
Recent trends
- The amount of spam in email traffic increased by 2.1 percentage points compared to April’s figure and averaged 85.1%.
- The number of links to phishing sites remained unchanged compared to April’s figure, accounting for 0.02% of all emails.
- Malicious files were found in 1.69% of all emails, an increase of 0.45 percentage points compared with the previous month.
Spam in mail traffic
The amount of spam detected in mail traffic averaged 85.1% in May 2010. A low of 79.8% was recorded on 31 May with a peak value of 89.8% being reached on 9 May.
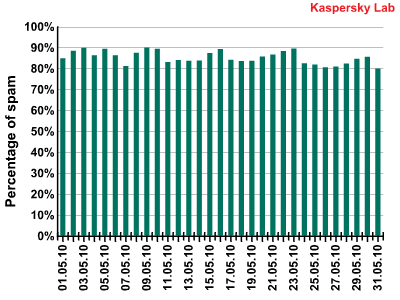
Spam in mail traffic in May 2010
Sources of spam
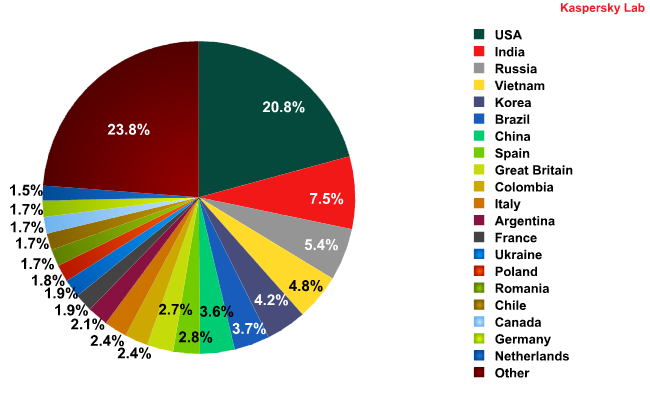
In April, India and Vietnam were hot on the heels of the USA for spam distribution. However, in May the amount of spam that originated from India and Vietnam decreased by 4.1 and 7 percentage points respectively. At the same time the quantity of spam coming from the USA increased by 8.5 percentage points, having returned to its usual level of 20.7%.
The amount of spam distributed from Russia increased by 1.2 percentage points. Though the growth was negligible, Russia reentered the Top 3 countries considered as prime sources of spam.
May saw major shifts involving China and Brazil – these countries have started to slowly win back their positions. They are not in the Top 5 yet, but could be soon. The amount of spam distributed from China increased by 2 percentage points when compared to April’s figure, while the quantity of spam that originated from Brazil nearly doubled (an increase of 1.2 percentage points), which put these two countries in 6th and 7th positions respectively.
In May, noticeable changes happened to spam flows coming from Germany and Italy, they dropped out of the Top 10 having distributed 2 percentage points less spam each compared with the previous month.
Interestingly, there is a “newcomer” in May’s Top 20 – Argentina distributed 2.1% of the total volume of spam.
The amount of spam distributed from the UK increased by 0.4 percentage points, accounting for 2.7% overall, which put this country in 9th place.
Phishing
The number of links to phishing sites remained unchanged compared to April’s figure, accounting for 0.02% of all emails.
PayPal, eBay, HSBC and Facebook remain the most popular targets for phishers, with 50.4% (-4.2 percentage points) for PayPal, 13.4% (+1.9 percentage points) for eBay, 8.5% (-1.1 percentage points) for HSBC and 6.9% (-1.8 percentage points) for Facebook. The list of the other six Top 10 members is fairly stable, except for the Habbo social networking website and the IRS which were replaced by NatWest and Bank of America respectively.
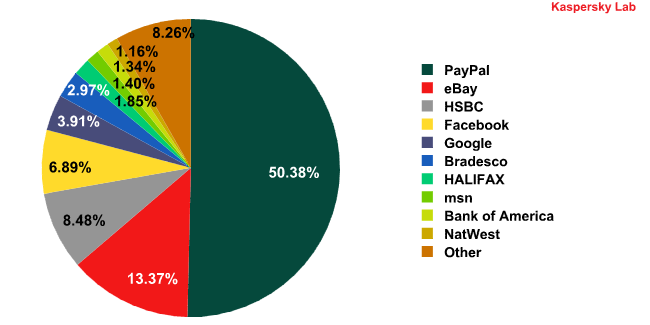
Organizations targeted by phishing attacks in May 2010
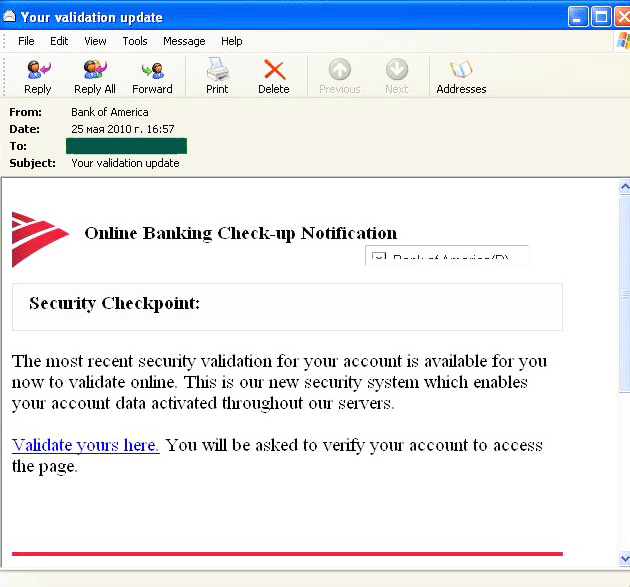
One of the major attacks targeted Bank of America. However the phishers did not even bother to think of something new:
As can be seen from the screenshot, the trick is typical for this type of fraud: a user must validate their account after a new security system has been enabled. Of course, their credentials will very soon fall into the fraudsters’ hands.
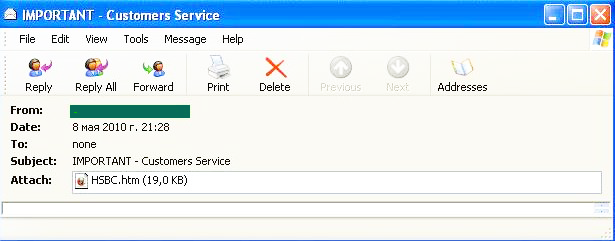
HSBC’s clients are also among the most attractive targets for phishers. In May we registered emails which requested that the bank’s clients open an attached file. There were no explanations or comments in the body of the message, and the subject of the email was particularly laconic in nature – IMPORTANT.
An unwary user was in fact redirected to a phishing site where they had to enter their login and password to purportedly access the online banking system.
Malware in mail traffic
Malicious files were found in 1.69% of all emails, an increase of 0.45 percentage points compared with the previous month.
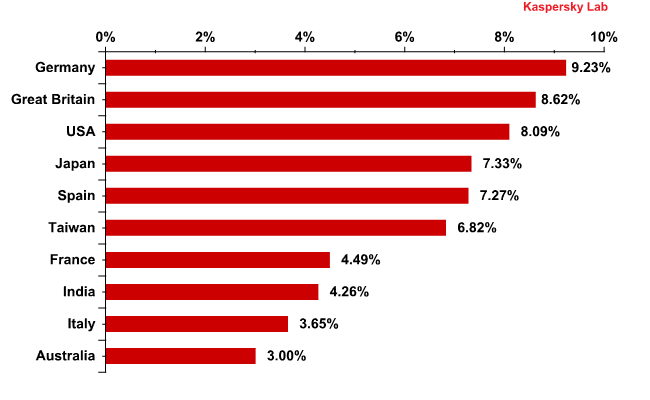
The Top 10 list of countries from which malware was distributed via email remained practically unchanged compared to April: the developed countries are still more attractive targets for fraudsters who have much more chance to obtain profit by attacking users from wealthier countries where each user has a credit card and an online banking or an e-pay system account.
The most noticeable changes in the rating happened to Spain which moved four steps upward to take fifth position. The amount of malware detected by our mail antivirus solution in this country doubled compared to the previous month.
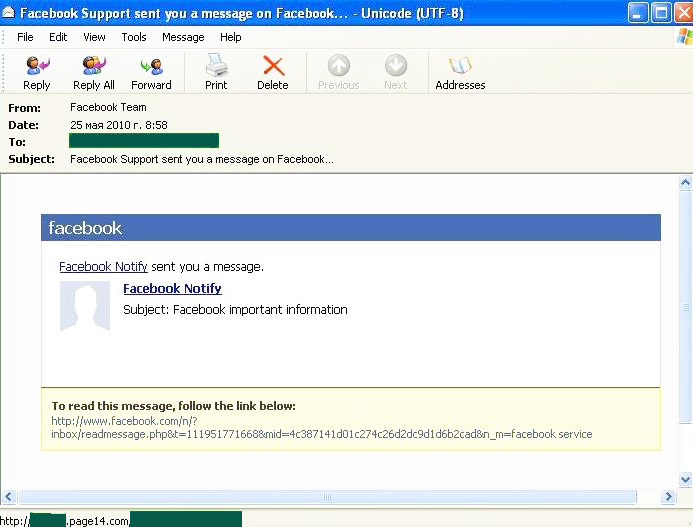
Social networks are again the focus of the fraudsters’ attention. In May, we registered emails which used Facebook and YouTube to distribute malicious code. Emails distributed via Facebook were designed in line with the phishers and spammers usual practice: the user being asked to read some very important information allegedly received from the social networks’ administration. In order to read it the user had to follow the link.
If you look carefully, at the bottom of the page you may see the address which leaves no doubt as to where a user is in fact going to be redirected to. If a user opens the page, a malicious code will immediately be downloaded to their computer. Particular notice should be paid to the fact that spammers have learned to imitate Facebook notifications perfectly. For example, the above message looks very much like an original email sent on behalf of the social network.
A link contained in some fake YouTube emails is much less professionally designed. It offers the user a chance to download a tool that allegedly provides easy searching of videos on a well-known portal.
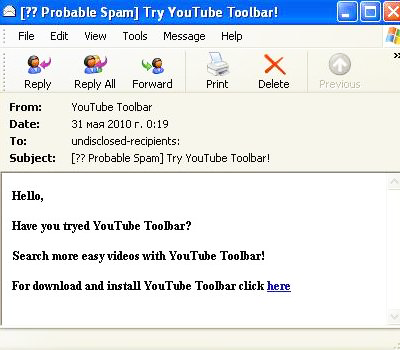
Of course, the “tool” is in fact a Trojan program.
Spam by category
The Medications and Health-Related Goods and Services category retained the lead for English-language spam. In May this category’s share averaged 30%, whilst for a time during the second half of the month it even exceeded 45-46% of the total amount of spam.
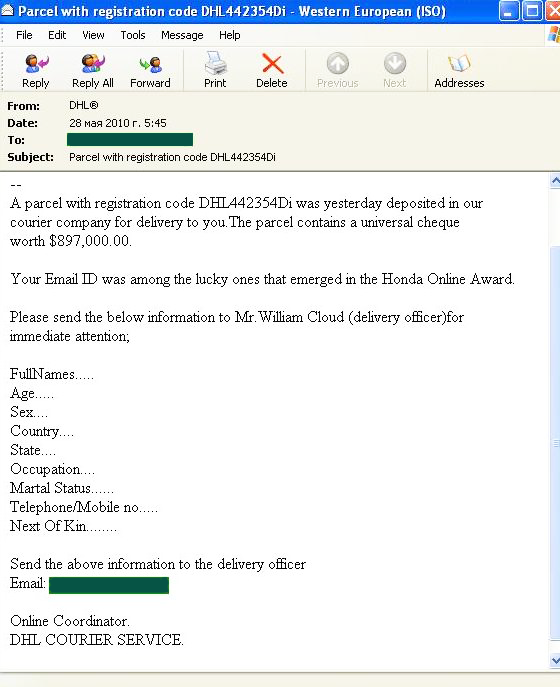
During May the Computer Fraud category again came second, though the amount of this type of spam decreased slightly compared to April’s figure (-3 percentage points). Interestingly, fake DHL notifications abandoned by malicious code distributors have been taken up by fraudulent spam authors. However, now users are not told to open the attached file in order to determine the parcel details, but are instead required to enter their personal data in order to receive a high value cheque with the help of DHL.
The share of the Personal Finance category increased considerably (+5 percentage points) compared to the previous month and occupied 3rd place in May’s Top 10 most popular spam categories. Emails contained offers of credit or encouraged recipients to determine their credit ratings.
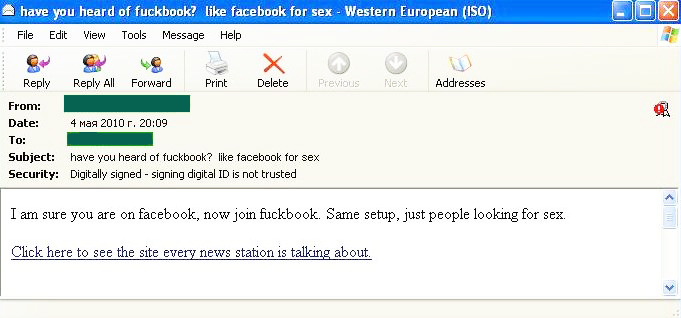
Interestingly, spammers who distribute adult content spam (the share of which is, by the way, very small) actively exploit social networks. Spam flows during May saw quite a few emails suggesting that users register with “porn Facebook” or “porn YouTube”.
Conclusion
In May, the number of links to phishing sites remained unchanged compared to April’s figure. Previously there were only two leaders – PayPal and eBay – in the list of organizations most often targeted by phishing attacks. A few months ago they were joined by two more organizations and the Top 4 “entry list” has been fairly stable ever since.
There was negligible growth in the amount of malicious emails in May. However, spammers are trying to compensate for the lack of quantity by introducing new malware distribution methods and abandoning the old ones. For example, some time ago their main trick was sending out fake DHL and UPS notifications, a practice which has decreased significantly of late.






















Spam Report: May 2010