
March in figures
- The share of spam in email traffic decreased by 3.5 percentage points compared to February and averaged 75%
- The share of phishing emails fell by half compared with February’s figure, accounting for 0.01% of all mail traffic
- Malicious files were found in 2.8% of all emails, the same as in the previous month.
Spam in the spotlight
Hlux/Kelihos closure has immediate impact on proportion of spam
In March the proportion of spam in mail traffic decreased by 3.5 percentage points. This is a pretty impressive figure, given that we are talking about relative values. In absolute terms, this means that the amount of spam fell 20% compared to the previous month.
We believe this was caused by the closure of the new version of the Hlux/Kelihos botnet. The week the anti-botnet campaign started (19-25 March) saw the lowest spam distribution rate of the month – 73.4%. When the campaign was successfully completed in the last week of the month, the share of spam crept up to 74.1% – most probably because the spammers began to reallocate their capacities.
New malicious tricks
In recent years, spammers sending out malicious attachments or links to malicious code have regularly altered their tactics. Their primary aim is to get users to open attachments or click links, otherwise they make no profit. That is why malicious spam always imitates harmless emails. But it’s a law of diminishing returns: the more often the same mask is used, the more likely users are to recognize the scam and deprive the fraudsters of any ill-gotten gains.
Often when spammers have invented a new trick they launch quick mass mailings over a few of days, trying to ‘hook’ as many users as possible before their new trick is discovered. Generally, spammers play on people’s curiosity, sending emails that appear to come from legitimate sites.
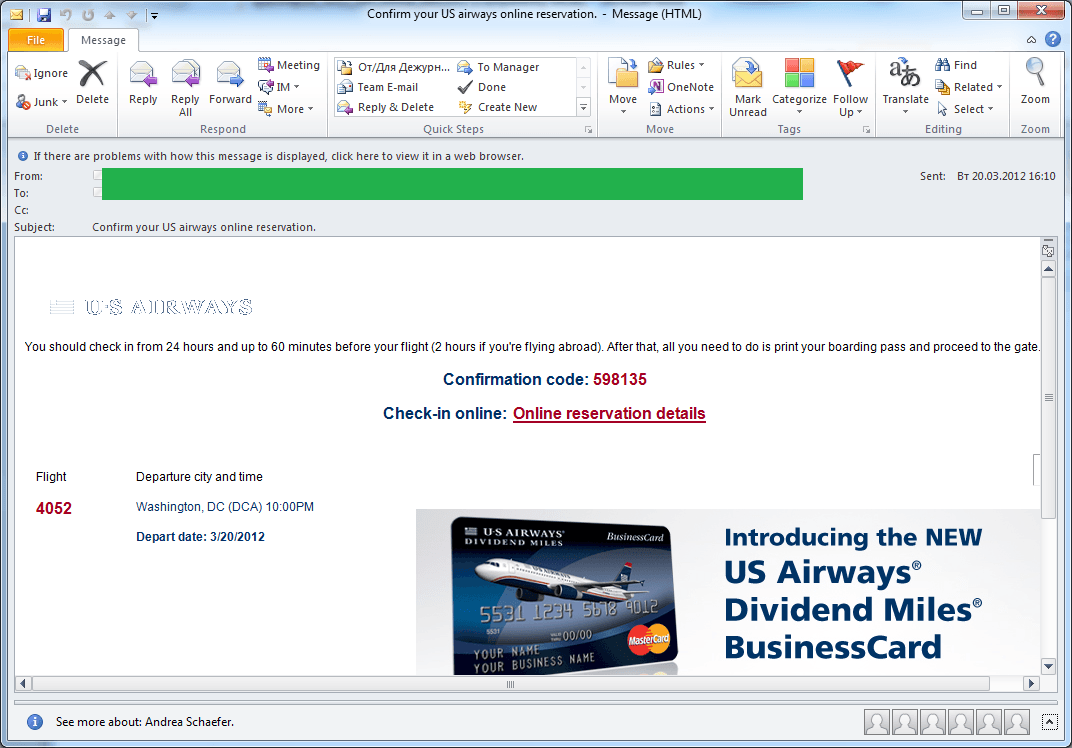
For example, a mass mailing that took place on 20-23 March mimicked a confirmation message from an airline’s online ticket reservation system.
There is nothing new about using airline tickets in malicious emails. Earlier a zipped malicious program was attached to emails notifying the recipient of a successful payment. However, this time the emails did not contain any attachments. Instead the user was prompted to go through the online check-in process by clicking a link in the email.
By doing so the user installed a Trojan program on his computer which, in turn, downloaded our old friend – ZeuS/Zbot. The technical details are available here.
The attack was over by about 9 p.m. Moscow time on 23 March. It should be noted that all the emails in this scam dated 20-23 March invited users to check in for a flight leaving on 20 March. This fact once again demonstrates that user vigilance is the first line of defense when it comes to computer safety.
Spam of the day
The most popular themes exploited in spam throughout March were St. Patrick’s Day, Easter and the launch of iPad 3 .
Among the St. Patrick’s Day scams, we noted that in order to get the users’ attention, partner programs exploit all sorts of holidays, festivals and similar events. In this instance it was Leprechaun-festooned spam sites offering fake designer watches – but there was no pot of gold awaiting users here.
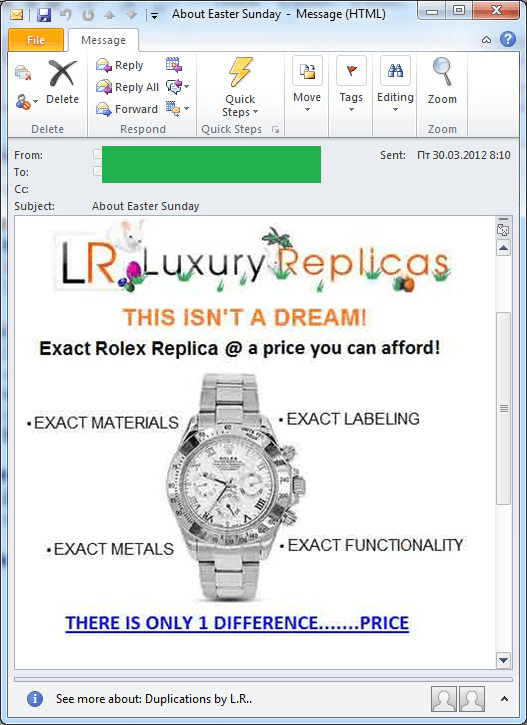
As expected, Easter was actively exploited by spammers. Similar fake designer goods were advertised in emails imitating Easter cards.
Unlike the St. Patrick’s Day mass mailings, Easter messages not only redirected users to a festively decorated site but contained Easter symbols and references in the original emails.
In addition to the adverts for Easter gifts and fake designer goods, English-language Easter spam also contained “Nigerian” letters congratulating the recipients on Easter lottery wins and offering various Easter presents.
Russian-language Easter spam also offered holiday presents for loved ones as well as Easter tours and excursions. Unlike the English-language messages, the emails distributed on the RuNet were not partner spam – these mass mailings were ordered from the spammers by small and medium-sized business as a means of advertising.
The release of the new Apple gadget – iPad 3 – could not escape the spammers’ attention. But just like Easter mass mailings there were obvious differences between English- and Russian-language messages.
For example, English-language spam primarily targeting a US audience makes use of Apple’s latest products as bait. Promising a free iPad or iPhone is an old, well-known trick which is obviously still effective because the fraudsters continue to utilize it to drag users into pyramid schemes or trick them into clicking on phishing or malicious links. A month ago the recipients of these mailings were mainly offered iPad 2 or iPhone 4S, whereas now they are promised iPad 3.
Statistical summary
Sources of spam
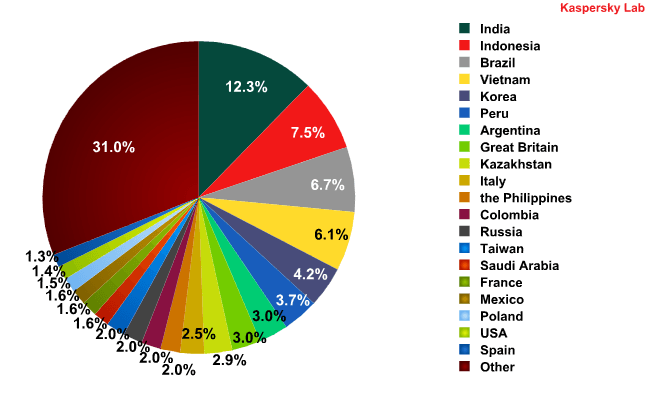
Top 20 sources of spam in March 2012
The top 20 most popular sources of spam remained largely unchanged from the previous month: the first 6 places were occupied by the same countries, though Vietnam and South Korea swapped places, coming fourth and fifth respectively. The share of spam distributed from South Korea decreased by 2.3 percentage points. The shares of the other countries in the rating did not change significantly, with all fluctuations within a range of 1.5 percentage points. India maintained its lead with 12.3% (+0.4 percentage points) of all distributed spam.
Malware in mail traffic
In March, the share of malicious files found in all emails remained unchanged compared with February’s figure and amounted to 2.8%.
Distribution of email antivirus detections, by country
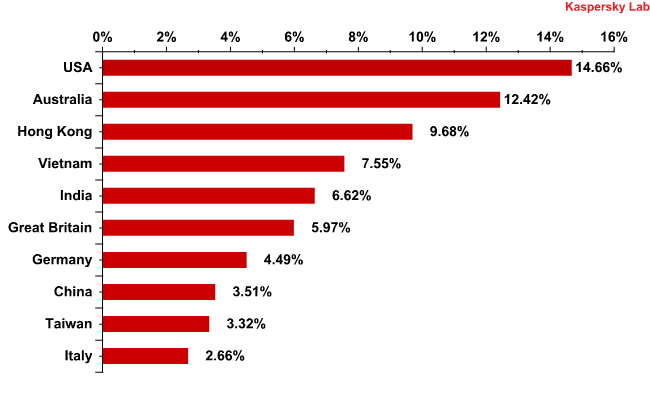
Distribution of email antivirus detections, by country: March 2012
For the third month in a row the US topped the rating of email antivirus detections: the share of Kaspersky Mail Anti-Virus detections increased by 1.7 percentage points in the US compared to February and accounted for 14.7% of the overall total.
Unexpectedly, Australia came second with 12.4% of all email antivirus detections having doubled its February’s result (+6.9 percentage points). As in February, Hong Kong was in third place.
Germany’s share dropped by 2.5 percentage points compared with the previous month.
The contribution of the other countries fluctuated within a range of 2 percentage points.
Top 10 malicious programs spread via email in March 2012
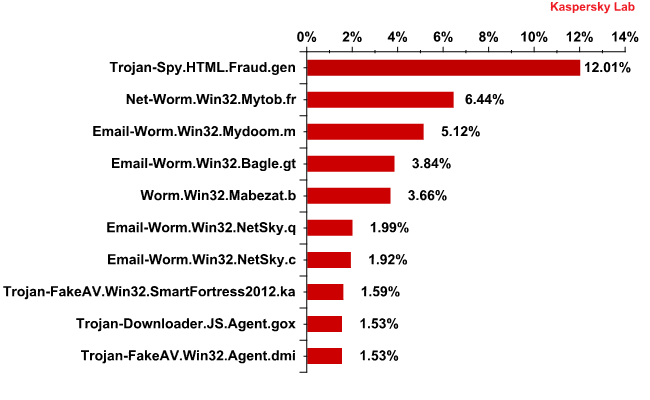
Top 10 malicious programs spread via email in March 2012
Rating leader Trojan-Spy.HTML.Fraud.gen accounted for 12% of all detections, a decrease of 2 percentage points compared with the previous month. This Trojan uses spoofing technology and appears in the form of an HTML page. It comes with a phishing email containing a link to a fake site resembling that of a well-known bank or e-pay system where the user is asked to enter a login and a password.
Email-Worm.Win32.Mydoom.m, Email-Worm.Win32.Bagle.gt, Email-Worm.Win32.NetSky.q and Email-Worm.Win32.NetSky.c were non-movers in March as well, occupying third, fourth, sixth and seventh places respectively. These mail worms have only two functions – to harvest email addresses and send copies of themselves to these addresses. Bagle.gt, yet another mail worm in the Top 10, also downloads malicious programs from the Internet. This type of malware is not used for targeted attacks – its functionality cannot be controlled.
Two malicious programs in March’s rating are fake AV programs. We haven’t seen any of these in the Top 10 for some time. To recap, their main function is to extort money from the user of an infected computer.
Phishing
The amount of phishing emails fell by half compared with February’s figure, accounting for 0.01% of all mail traffic.
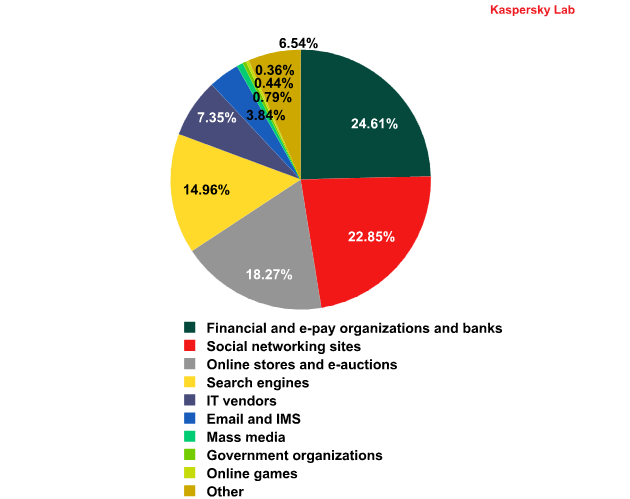
Top 100 organizations, by sphere of activity, targeted by phishers in March 2012
(based on anti-phishing component detections*)
*This rating is based on our anti-phishing component detections activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
Financial organizations are still the most attractive target for the phishers: almost a quarter of our anti-phishing detections came from phishing sites designed to steal from bank and e-pay accounts. In fact, this category seems fairly stable – since January its share has remained practically unchanged. In general, the phishers’ interests do not vary much: the most noticeable shift compared to February was the increase of 1 percentage point in the proportion of phishing attacks targeting online stores.
The shares of the other categories changed insignificantly – within a range of 1 percentage point.
Spam by category
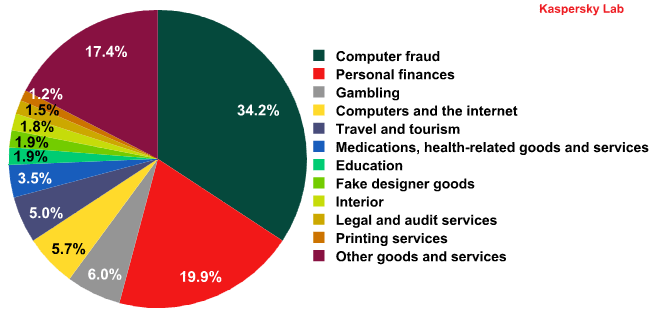
Spam by category in March 2012
Although the computer fraud and personal finance categories maintained their leading positions for a fourth successive month, their share of the market in March dropped by 9.5 and 4.4 percentage points respectively. The amount of spam advertising casino services grew by 4 percentage points. This type of spam, along with Personal finance spam, aims to part users with their cash in the hope of a generous reward.
March saw an increase in the amount of mass mailings offering educational services (+3 percentage points) which may be linked to the approaching summer holidays.
The share of the other categories changed insignificantly – within a range of 1.5 percentage points.
Conclusion
In March, the proportion of spam in email traffic dropped by 3.5 percentage points. We believe this was caused by the successful anti-Hlux/Kelihos campaign which was carried out with the help of Kaspersky Lab experts.
In March, spammers enriched their malicious arsenal with several new tricks. Spam is still dangerous though the share of malicious attachments in mail traffic decreased slightly.
The most popular themes exploited in March’s spam were St. Patrick’s Day, Easter and iPad 3. The first two were used to advertise different goods while the new Apple device became the latest bait to be used in various fraudulent mass mailings.






















Spam report: March 2012