
June in figures
- The amount of spam in email traffic increased by 0.4 percentage points compared to May and averaged 83.3%.
- The amount of phishing emails remained unchanged compared to May’s figure and accounted for 0.02% of all mail traffic.
- Malicious files were found in 3.8% of all emails, a decrease of 0.3 percentage points compared to May’s figure.
Spam in spotlight
Spam and the law
Microsoft still fighting Rustock
The recent joint effort between Microsoft and US law enforcement agencies has resulted in the death knell of the Rustock spam botnet.
We previously wrote about this in our spam report for March. To recap, the botnet command centers were closed on 16 March and for the next few days there was a significant decrease in spam.
However, Microsoft decided to take things further. The company’s blog dated 6 June reads that Microsoft published advertisements in the Russian newspapers Delevoy Petersburg and The Moscow News addressed to the Russian Federation citizens suspected of creating and administrating Rustock. The ad states that Microsoft has initiated a legal case in the USA against the unidentified defendants that went by the online name of Cosma2k. The text goes on to state that, using specified IP addresses and domains, the defendants created a botnet that was used to gain unauthorized access to the computers of third parties, to violate intellectual property rights, to distribute unwanted correspondence via mass mailings resulting in damage being caused to Microsoft and other undefined entities. Microsoft demands that access to the IP addresses and domains be blocked and the botnet be closed. In addition, the plaintiffs asked the court to take other appropriate measures.
Microsoft did not name any people suspected of being connected to Rustock in its advert. However, the names can be found at noticeofpleadings.com, a site created by Microsoft as a platform for Rustock-related publications.
The advertisement says that in case of the defendant’s failure to appear in court the decision will automatically be taken in favor of the plaintiff. The blog also states that the company will continue the case against the organizers of the botnet if they do not appear in court, including legal proceedings in Russia.
We wish our Microsoft colleagues every success. There’s nothing to stop the bot herders who remain at large from creating another major botnet. In this respect Microsoft’s steps are logical – simply closing the command centers is not enough to eradicate botnets. It is important to take all possible measures to prevent the cybercriminals from creating a new botnet.
Legislation in Japan
We regularly bring you news in our monthly spam reports about spam-related legislative initiatives in various countries. Each law that is adopted becomes a significant landmark in the fight against spam.
In June, the Japanese parliament passed an important law that makes the creation, distribution, purchase and storage of malicious programs as well as the distribution of pornographic spam a criminal offence.
There was widespread media coverage of the initiative.
High-profile cases in Russia
There are no anti-spam laws in Russia as yet, despite the fact that some of the world’s major spammers are resident in the country.
However, the lack of legislation has not prevented Russian law enforcement agencies doing their best to catch those sending mass mailings and bring charges against them…for other crimes.
In 2007, the Russian programmer Leonid Kuvayev was recognized as the world’s No.1 spammer, accounting for a significant amount of unsolicited emails distributed via the Internet. He is also considered the ‘inventor’ of image spam. In 2005, a court in the USA, where he lived for 14 years, named Leonid Kuvayev as the ringleader of a gang of spammers and placed him on the wanted list. By that time, however, Leonid had left the USA and was living in Russia beyond the reach of US law enforcement agencies.
Kuvayev most probably went into hiding in Russia in the hope that the lack of anti-spam laws would mean he could avoid punishment. This may have been the case if he hadn’t been suspected of another crime. On 7 June the first hearing of Leonid Kuvayev’s case took place in which he was accused of sexual crimes against minors. He has been in police custody since late 2009.
However, the fact that Kuvayev is in prison does not mean his business is dead. One of the biggest pharmaceutical spammer programs Mailien, which is believed to belong to him, continued to spread unsolicited emails via the Internet and earn him money long after he had been arrested.
Another Russian citizen suspected of contacts with pharmaceutical spammer programs, Pavel Vrubelevsky, was arrested on 23 June at Sheremetyevo airport. The arrest was not attributed to his spamming activity, however. A day earlier, several reports appeared on the Internet stating that a criminal case had been opened at the end of May into DDoS attacks on the major Russian e-pay system Assist that took place in July 2010. There was also a confession from someone called Igor Artimovich who admitted his part in the attacks and who named Pavel Vrubelevsky, the head of ChronoPay, as the person who ordered the attack.
Pavel Vrubelevsky is considered the founder of the large pharmaceutical affiliate program rx-promotion.
In autumn 2010, a criminal case was initiated against Igor Gusev, the founder of another affiliate program called Glavmed with links to SpamIt, yet another spammer affiliate program. Gusev is accused of illegal business practices.
Themes of the month
In our spam reports and blogs we regularly mention world events that spammers use to grab our attention. The reason we do so is to remind users that any news can be exploited by the fraudsters for their nefarious schemes.
In June, spammers exploited the last Harry Potter movie by offering free cinema tickets. The death of Osama bin Laden still featured prominently in fraudulent emails too.
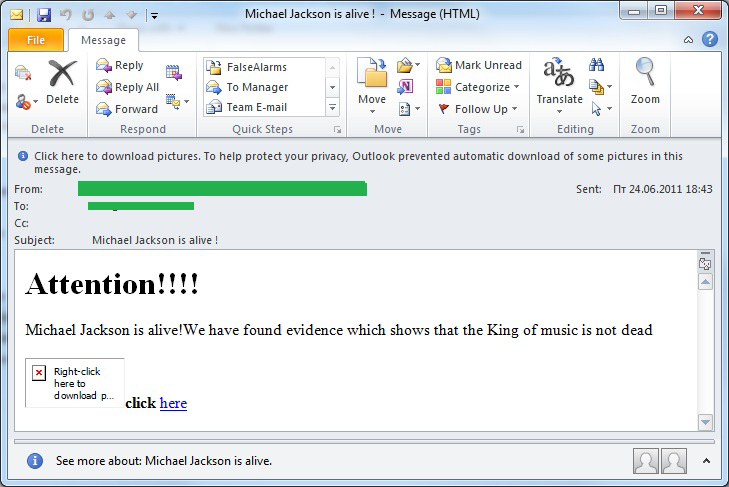
However, the most numerous mass mailings were associated with the anniversary of Michael Jackson’s death.
Spammers remember Michael Jackson
Michael Jackson died on 25 June 2009 and ever since we have seen a number of mass mailings claiming he is still alive.
Last month the whole world, including spammers, remembered the artist on the second anniversary of his death.
Chinese spammers, for instance, advertised collections of Michael Jackson’s songs, something that was assured to be popular with his fans.
An example of English-language spam contained the same sort of sensational claims that have appeared over the last two years:
The text in this message was followed by a link to sites containing the malicious file Backdoor.Win32.mIRC-based which allows cybercriminals to control an infected computer remotely.
Once again we would like to remind users of the necessity to be especially careful and not to trust emails exploiting news items that are sent from dubious sources.
Statistical summary
Sources of spam
In June, India remained the most popular source of spam, accounting for 16.35% of the total volume of spam (an increase of 5 percentage points).
Russia came 7th in the rating of the most popular spam sources, with the amount of spam originating from the country decreasing by 0.7 percentage points compared with May’s figure.
In June, Brazil demonstrated the most noticeable growth, occupying 2nd place in the rating with 11.22% of the total volume of spam (an increase of 4.36 percentage points). The volume of spam originating from South Korea decreased by 2.63 percentage points which saw it drop one position to 3rd.
Malware in mail traffic
In June, malicious files were found in 3.8% of all emails, a decrease of 0.3 percentage points compared with the previous month.
Russia and the USA maintained their status as the countries where malware was detected most frequently in mail traffic. Russia was the overall leader, with the amount of blocked emails with malicious attachments decreasing slightly. In the case of the USA, there was also a decrease of less than 0.3 percentage points.
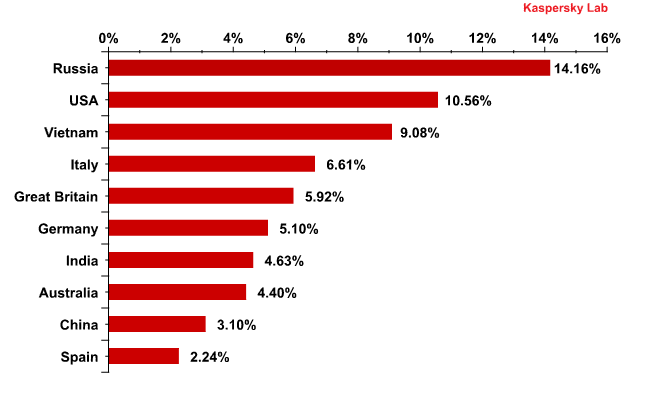
Countries where mail antivirus detected malware most frequently in June 2011
Vietnam was a non-mover in June and remained in 3rd place with an increase of nearly 1 percentage point compared with the previous month.
The biggest shifts in the amount of blocked emails with malicious attachments were witnessed in Italy which occupied 4th position in the rating. Malicious files were found in 6.6% of all emails, an increase of 1.5 percentage points compared with May.
There were no other considerable changes in the Top 10 countries where mail antivirus detected malware most frequently in June 2011.
The Top 10 malicious programs distributed via mail traffic in June 2011 were as follows:
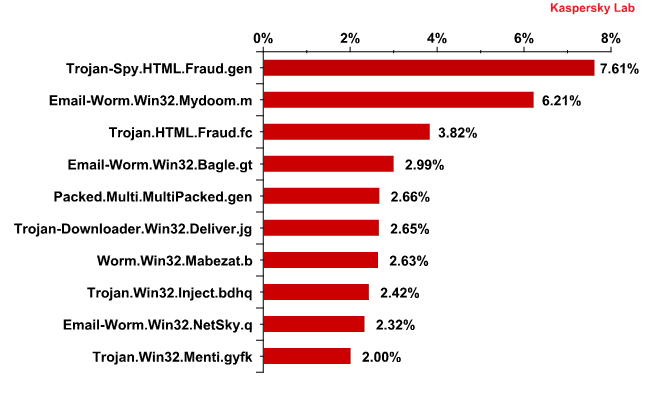
The Top 10 malicious programs distributed via mail traffic in June 2011
The four most popular malicious programs remained unchanged.
7.6% of malicious files found in blocked emails belonged to Trojan-Spy.HTML.Fraud.gen, the long-standing leader of this rating.
Email-Worm.Win32.Mydoom.m, Email-Worm.Win32.Bagle.gt and Email-Worm.Win32.NetSky.q mail worms occupy 2nd, 4th and 9th positions respectively. These malicious programs have also become long-term residents in the rating. As we have already mentioned in previous reports, Mydoom.m and NetSky.q are malicious programs whose only functions are to harvest email addresses and to send copies of themselves to these addresses. Bagle.gt is yet another mail worm, but with more sophisticated functionality: it not only collects email addresses and sends a copy of itself to all email addresses harvested from the victim’s machine but downloads malicious programs itself from Internet resources.
Trojan.HTML.Fraud.fc, a new entry in April’s Top 10 rating of malicious programs distributed via mail traffic, came 3rd in June again. It appears in the form of a phishing HTML page designed to steal confidential financial information from Brazilian users.
Phishing
In June, the amount of phishing emails remained unchanged and accounted for 0.02% of all mail traffic.
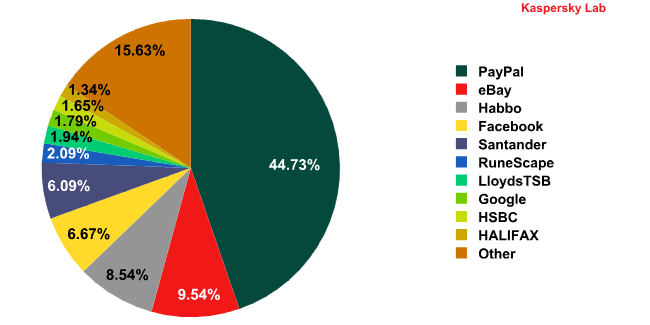
Top 10 organizations targeted by phishing attacks in June 2011*
* The rating is based on the number of phishing URLs on the Internet that attempt to obtain user logins and passwords for various online services. The rating is not demonstrative of the security level of the organizations named above, but rather the popularity of the services among users, which in turn explains their popularity among phishers.
In June, spammers seemed to lose interest in online games. Only May’s Top 10 newcomer RuneScape managed to hold out in the rating, occupying 6th place: 2.1% of all phishing attacks targeted its users (a decrease of 2.57 percentage points). World of Warcraft did not appear in the rating at all. As we have already mentioned this is most likely the result of the Blizzard team’s efforts to protect their users.
The number of attacks targeting Habbo (+6.25 percentage points) and Facebook (+4.07 percentage points) increased considerably. These two social networks regained 3rd and 4th positions in the rating respectively.
In June, phishers once again focused in on Google. It should be noted that the figure for Google did not include statistics for its Orkut social networking service. The amount of attacks targeting this social network accounted for 0.8% which, together with the attacks on the company’s other services, brings the total for Google to over 2.5% of all phishing attacks.
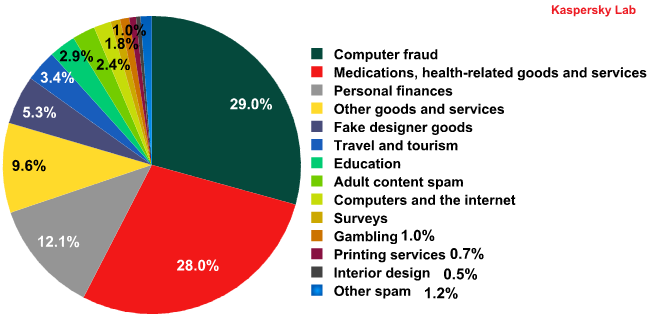
Spam by category
The fact that almost one third of all English-language spam messages (29%) fell into the Computer Fraud category should act as a warning for all users to be careful when online. It means that a significant amount of spam that reached inboxes was sent with the intention of extorting money from users (e.g. ‘Nigerian’ spam or phishing messages) or else contained a malicious attachment or link to malicious code.
More than a quarter of all English-language spam messages contained ‘pharmaceutical’ spam. Such proposals give rise to demand: billions of messages are sent every day offering recipients generic Viagra implying the product still has its customers despite warnings from both large IT security companies and health professionals. Users should most definitely not trust pharmaceutical mass mailings: counterfeit medication is very unlikely to improve your health. We would also like to remind those who take up the offers of cheap ‘Canadian’ drugstores that cybercriminals often spread malicious code along with their medications. A user can easily end up with an infected computer when visiting sites that claim to sell medications.
Besides the most popular spam categories mentioned above the Top 5 also includes Personal Finance (12.1%) offering quick earnings and dubious loans, Other Goods and Services (9.6%) and Fake Designer Goods (5.3%).
Conclusion
Contrary to our expectations, rogue antivirus programs did not return to mail traffic for long. Not a single representative of this family made it into the Top 10 malicious programs detected by our mail antivirus in June.
In the near future we expect to see phishing emails exploiting the new Google social network Google+. The social network is currently invitation-only, which is all the more reason for cybercriminals to take advantage of people’s desire to get into the closed community by offering fake invitations that include both phishing links and malicious code.























Spam report: June 2011