
August in figures
- The share of spam in mail traffic fell 0.9 percentage points from July and averaged 80%.
- The amount of phishing emails in all mail traffic increased by just 0.1 percentage points from July and totaled 0.03%.
- In August, malicious files were found in 5.9% of all email traffic – 1.2 percentage points more than the previous month.
Spam in the spotlight
Spam with malicious attachments: tactics old and new
In August, the percentage of spam with malicious attachments increased once again and accounted for 5.9% of all unwanted correspondence. Furthermore, malicious users used a number of different techniques to send emails with malicious attachments — both tried and true methods and some new tactics.
Since the end of June and all throughout August, we saw emails that were made to look like official notifications from mail delivery services such as UPS, FedEx, and DHL. This wave of spam was the most active during 8-11 August.
The spam emails stated that the delivery service was unable to deliver a package and that the recipient would need to pick it up from the office immediately, or that the recipient’s address was filled out incorrectly, or that a package was on the way to the recipient. All of these messages contained a ZIP archive file, which allegedly contained the forms required to successfully send or receive the package referred to in the email.
However, the ZIP files actually contained malicious files. For example, a rather large mailing made to look as though it were from UPS contained a variety of modifications of the FraudLoad Trojan (Trojan-Downloader.Win32.FraudLoad). Equally prominent were mailings with a number of modifications of Backdoor.Win32.Agobot. This threat was spread in emails designed to look like official notifications from all three mail delivery services: UPS, FedEx, and DHL. Less frequently, Kaspersky Lab registered different modifications of Trojan.Win32.Yakes.cap. These threats, once on a computer, would then download other malicious programs.
Making emails look like notifications from the aforementioned delivery services is an old trick that malicious users have been employing for at least two years now. However, judging by how frequently spammers use it, it appears to be an effective method.
In August we also noted several new tricks used to spread malicious code, although they were all based on the same idea: the more mysterious an email is, and the less text there is, the greater the chances of piquing the recipient’s curiosity. We saw three different kinds of spam using this technique:
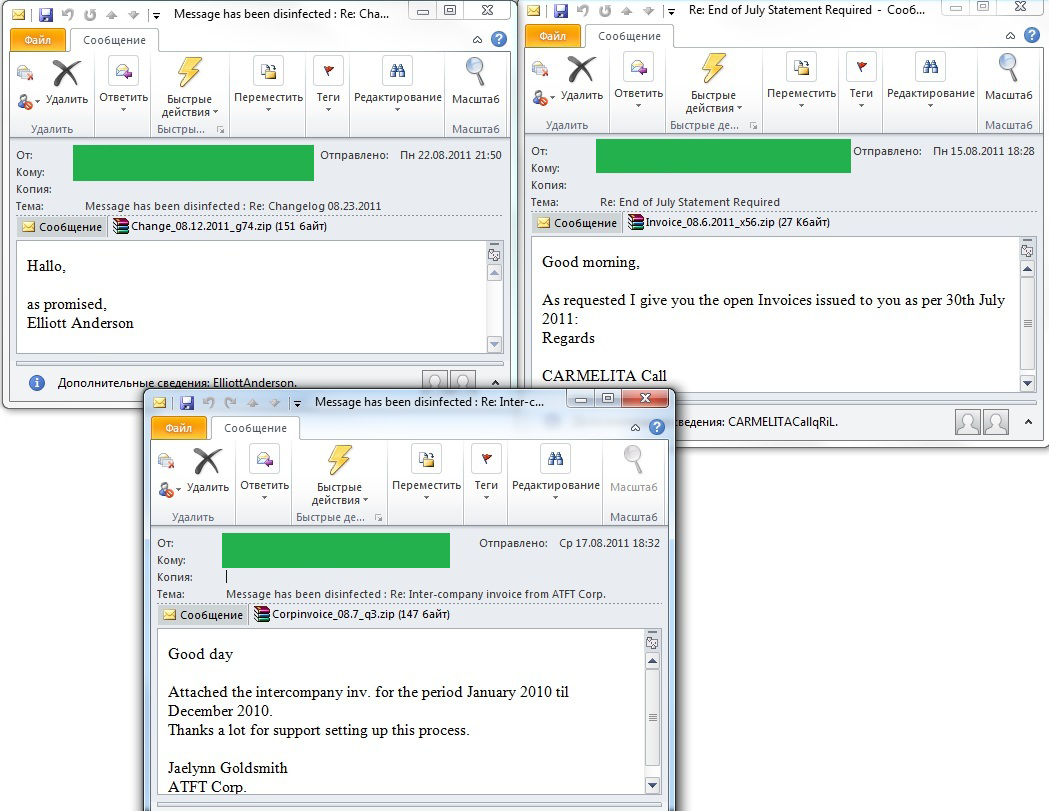
- the first group contained the word ‘Changelog’ and the date in the subject line. The body of the email had only a couple of words, such as “As promised” or “See attachments”;
- the second group had a subject line that read either “End of July Statement required” or “End of July Statement”. The body of the email explained that, as requested, the sender would be transferring unsettled accounts for a particular date that was usually specified;
- the third group featured the subject line “Internal accounts from ATFT Corporation” and contained a message stating that internal 2010 accounts were in the attachments, and expressed gratitude for the support in “setting up this process”.
Remarkably, all of these messages are clearly coming from the same source. Not only did they use the same tricks and text style but the way the ZIP archives were named was also the same: a real word was followed by an underscore and then the date, another underscore, and a letter or one or two numbers.
Furthermore, we also identified a link between these messages and the fake emails claiming to come from the aforementioned delivery companies. In particular, the attachments that were spread in the emails were different modifications of Trojan.Win32.Yakes and Backdoor.Win32.Agobot.
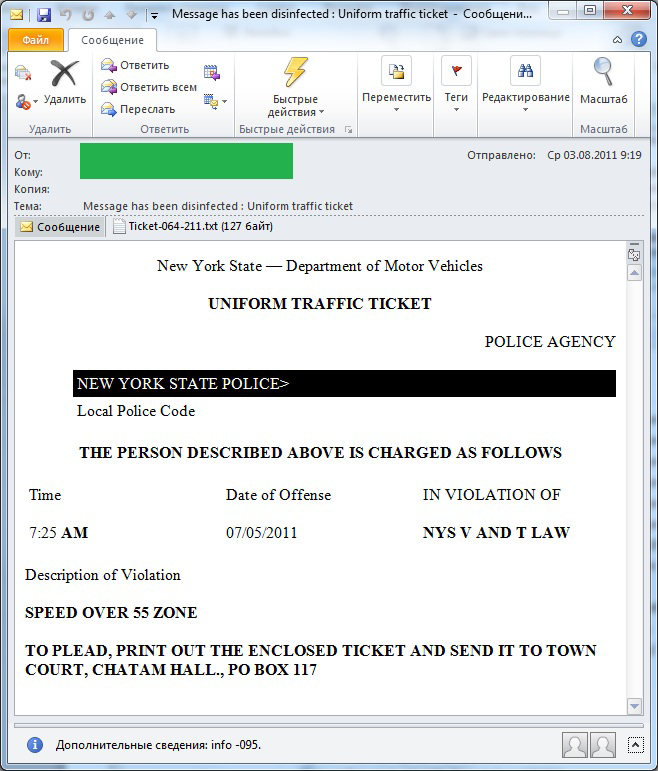
In order to spread the different modifications of Trojan-Downloader.Win32.FraudLoad, another tactic — social engineering — was used. The emails were designed to look like notifications from the US police stating that the recipient should print out the attached letter that allegedly contained the details of a fine for driving offences and send it to a municipal court.
Malicious users have started looking for new methods to get a user’s attention. This is most likely happening because the old tried and true methods are quickly recognized by most people today as fradulent and are no longer as lucrative for malicious users.
It is also remarkable that previously, many different types of malicious attachments were spread in emails that appeared to be from adult content websites where users could “meet girls” or view “scandalous photos” of celebrities. Today, malicous users are trying to copy the style of official notifications and business correspondence. This is because most users do not expect to find malicious attachments in random business emails. Furthermore, adult content and “girls waiting to meet you now” can be found all over the Internet, while a company’s internal documents are more likely to pique an Internet user’s interest.
Hot topics: Ramadan
There are also mass mailings that specifically target Muslims, as spammers adopt a kind of ‘equal-opportunity’ policy and operate on an international, multicultural basis. In August this year, Muslims celebrated the month of Ramadan, and just like every year, spam emails focused on this theme.
This year, Kaspersky Lab registered several different mass mailings at once, all promoting a proper diet during Ramadan. We received one email with offers of food delivery to one’s home at a special Ramadan discount. There was another email advertising a restaurant with nighttime hours, i.e., when Muslims can eat during the holy month.
Remember, spam is first and foremost a threat that needs to be counteracted, which is why spam that promotes something should not be perceived as a mere advertisement. Even the most harmless-looking email could contain malicious script, and spammers have no problems making money from advertising and from users who unwittingly install malicious code.
Statistical summary
Sources of spam
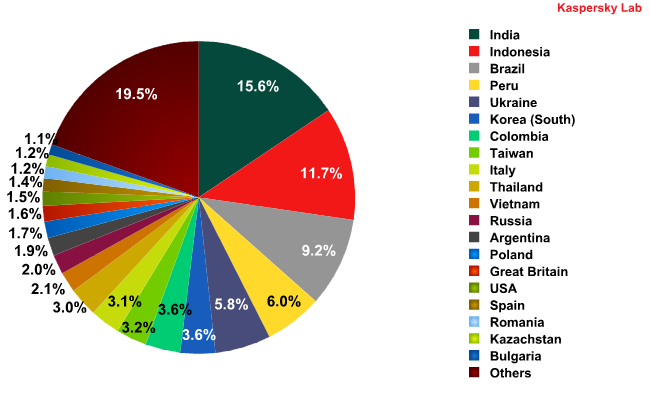
Sources of spam in August 2011
In August, the top four sources of spam remained the same as in the previous month: India (15.6%), Indonesia (11.7%), Brazil (9.24%), and Peru (6%).
Among the most substantial changes in the Top 10 sources of spam it is worth mentioning that Italy, the last western European country in the Top 10, slipped down to 12th place in August. Poland is now in the Top 10, with an increase of 1.3 percentage points compared to July. As a result, the Top 10 sources of spam in August are now comprised exclusively of countries in Asia, Latin America, and eastern Europe.
Russia is still in 11th place in the ratings. The percentage of spam spread from Russia compared to July did not change significantly. Meanwhile, the amount of spam originating from Ukraine fell by nearly 1 percentage point.
Spam traffic from the two groups of countries that were featured in July (India-Brazil and Indonesia-Ukraine-Thailand-Peru) continues to spread in sync with one another.
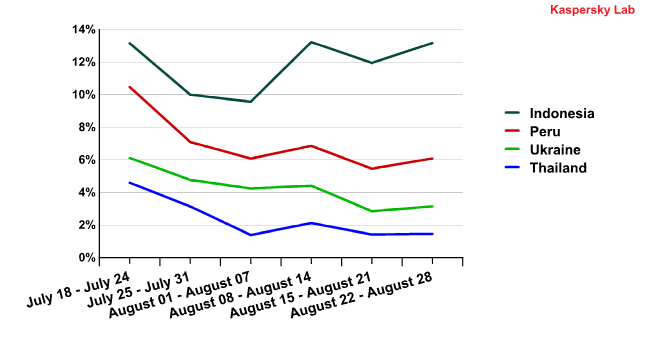
The correlation between Indonesia, Ukraine, Thailand, and Peru is still in effect, despite the fact that the percentage of spam originating from Indonesia has increased over the past month, and the percentage of spam coming from the other three in this group has decreased. Nevertheless, the local highs and lows among these four countries are still aligned with one another. See for yourself:
The percentage of spam originating from Indonesia, Peru,
Ukraine and Thailand from 18 July to 28 August
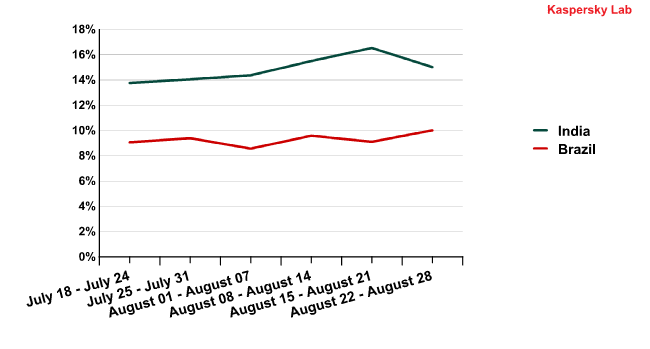
The curves illustrating the dynamics of spam traffic from India and Brazil grew slightly farther apart over the last two weeks of August, but the change in the indicators from these countries is so negligible that the gap can most likely be explained by local factors, such as the existence of other spam botnets managed by other malicious users.
The percentage of spam originating from India and Brazil from 18 July to 28 August
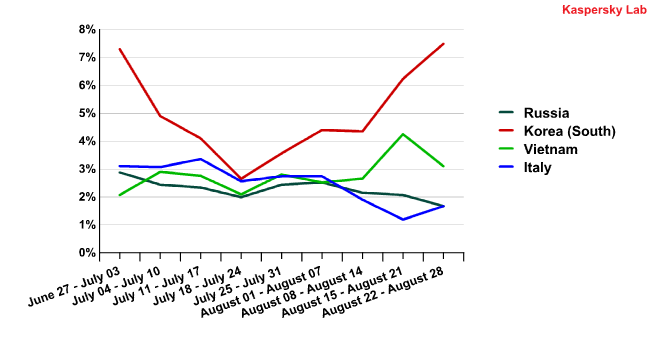
Statistics for the Vietnam-South Korea-Russia-Italy group of countries did not reveal any correlations among the fluctuations of spam traffic originating from these countries.
The percentage of spam originating from Russia, Korea,
Vietnam and Italy from 27 July to 28 August
Some similarities can be seen in the movements of the local highs and lows of Russia and Vietnam, and we will continue to track the spam traffic flows of these two countries.
Malicious attachments in mail traffic
In August, malicious files were found in 5.9% of all emails — 1.2 percentage points more than in July.
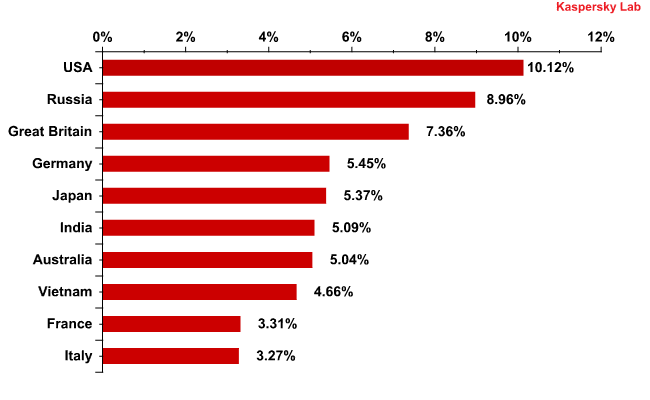
Country ratings based on the number of email antivirus detections show that Russia has fallen considerably, down 5.1 percentage points in August with a total of 8.96%. As a result, Russia is now in second place behind the US.
The number of detections in US email traffic was up 2.6 percentage points in August and came to 10.1%, returning to the levels registered in June.
A distribution of email antivirus detections, by country: August 2011
The number of email antivirus detections within Germany (5.45%) and India (5.1%) fell as sharply as they rose in July, by 3.8 and 2.8 percentage points respectively.
The percentage of email antivirus detections registered in Japan rose significantly (+3.7 percentage points). Interestingly, the Top 20 email malware detections in Japan are modifications of the aforementioned Trojan.Win32.Yakes, and Backdoor.Win32.Agobot.
The top two most frequently detected malicious programs in August came as no surprise:
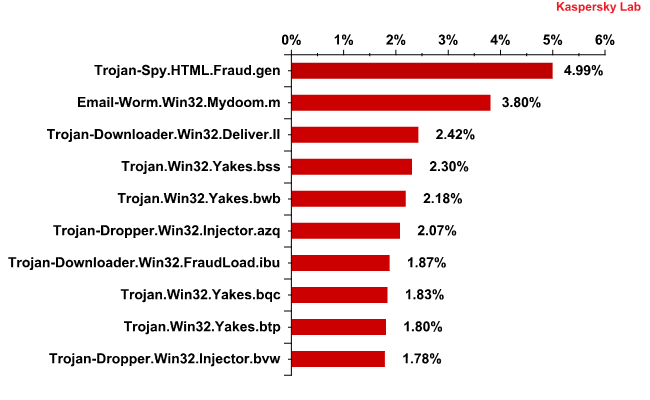
The Top 10 malicious programs spread via email in August 2011
Trojan-Spy.HTML.Fraud.gen – typically the number one troublemaker these days -accounted for 5% of malware detections in mail traffic in August (down 0.5 percentage points from July). Second place was taken by Email-Worm.Win32.Mydoom.m, the only mail worm to make the August ratings. This particular threat really only has two functions: to harvest electronic addresses on infected machines and send itself to those addresses.
The third-most detected malicious program in email in August was Trojan-Downloader.Win32.Deliver.ll. The Trojans in this family represented the majority of our Top 10 malicious programs in March. This program is a classic Downloader Trojan that installs other malicious programs on an infected computer without the user noticing.
Four of the Top 10 detections this month were modifications of previously mentioned Trojan.Win32.Yakes, which placed fourth, fifth, eighth, and ninth in August.
Phishing
The percentage of phishing emails in total mail traffic compared to July increased very slightly and stood at 0.03%.
The top four phishing targets have not changed since July.
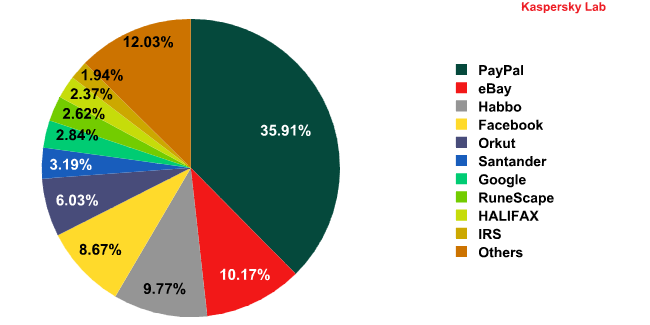
Top 10 organizations targeted by phishers*
* This rating is based on the number of phishing URLs on the Internet that attempt to obtain user logins and passwords for various online services. The rating is not demonstrative of the security level of the organizations named above, but rather the popularity of the services among users, which in turn explains their popularity among phishers.
One of the main changes in August was the rise of the social networking site Orkut (6%) from seventh to fifth place among the organizations most frequently targeted by phishers.
Also of note is the drop in phisher interest in online games: RuneScape, which was the number 6 target in July, dropped two places (-1.1 percentage points), and WoW, which brought up the rear of last month’s Top 10, was not even in the Top 10 phishing targets in August, even though its respective percentage of attacks did not change.
Kaspersky Lab is also monitoring the emergence of the IRS among top phishing targets. In the months to come, its position will rise as the US tax season approaches. This period always sees an increase in the percentage of attacks involving the IRS.
Spam by category
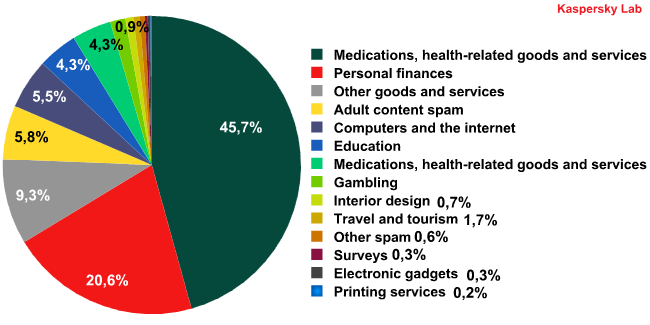
Categories of spam in August 2011
Nearly half of all English-language spam in August was comprised of fraudulent emails. As the percentage of malicious attachments in email rises, this serves as yet another reminder to take measures to ensure your security on the Internet.
The second-most prevalent category of spam this past month was financial spam, including emails with dubious credit offers and get-rich-quick schemes. The percentage of this spam category has risen 1.5 times since June.
The percentage of adult content spam doubled in August.
At the same time, the percentage of medical-themed spam, including advertisements for Viagra and weight-loss pills, fell considerably, from 28% in June to 4.5% in August. Equally striking was the drop in the percentage of spam advertising luxury item replicas.
Overall, in August we saw an increase in English-language spam among those categories of spam that are not primarily out to sell something, but rather designed to install malicious programs on a victim’s computer, steal personal data, and use that data in fraudulent schemes.
Conclusion
The percentage of malicious attachments in spam continues to rise steadily. Over the past two months, that indicator has grown by a third. Overall, this is a typical trend for the summer months, as spammers usually have fewer orders from their clients during the holiday season, and switch gears over to mailings with affiliate programs that will be more lucrative. Affiliates that pay spammers a percentage for installing malicious programs are always a popular choice among malicious users, and especially so during the summer. Furthermore, spammers are using both new as well as tried and true techniques to spread malicious programs. Scammers have updated their arsenal, and a rise in the percentage of malicious attachments gives us yet another good reason to remind users that computer security depends first and foremost on one’s own attentiveness and caution.
The distribution of English-language spam categories also reveals that during the holiday season, the goods advertised in spam are not in great demand. This forces malicious users to have to search out different methods of earning money that do not depend on the consumer power of Internet users.
In September we can expect the percentage of malicious and fraudulent spam to decrease, while medications and medical goods and services and replicas of luxury items gain back some of their lost ground.






















Spam report: August 2011