
- January in figures
- Spam in the spotlight
- The geographical distribution of spam sources
- Malicious attachments in email
- Phishing
- Conclusion
January in figures
- The percentage of spam in email traffic was down 7.7 percentage points compared with December and averaged 58.3%
- The percentage of phishing emails halved compared with December, falling to 0.003%
- In January, malicious files were found in 3% of all emails, a decrease of 0.15 percentage points
Spam in the spotlight
Holidays
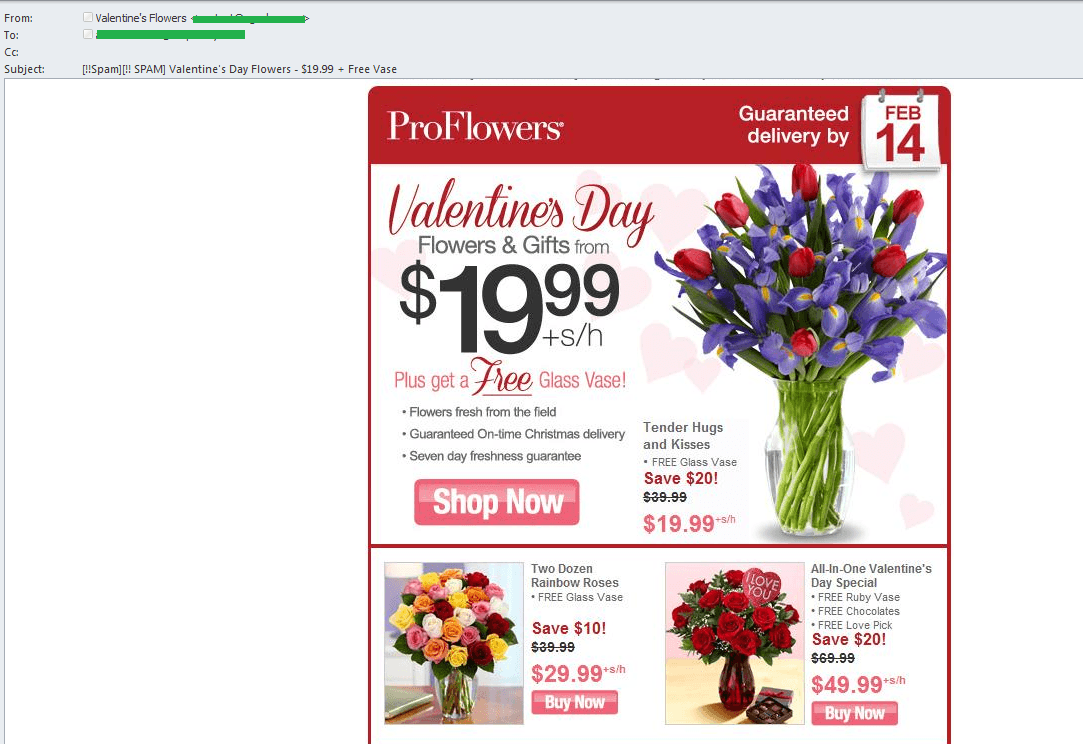
In the run-up to St. Valentine’s Day, English-language partner programs started distributing traditional offers of flowers.
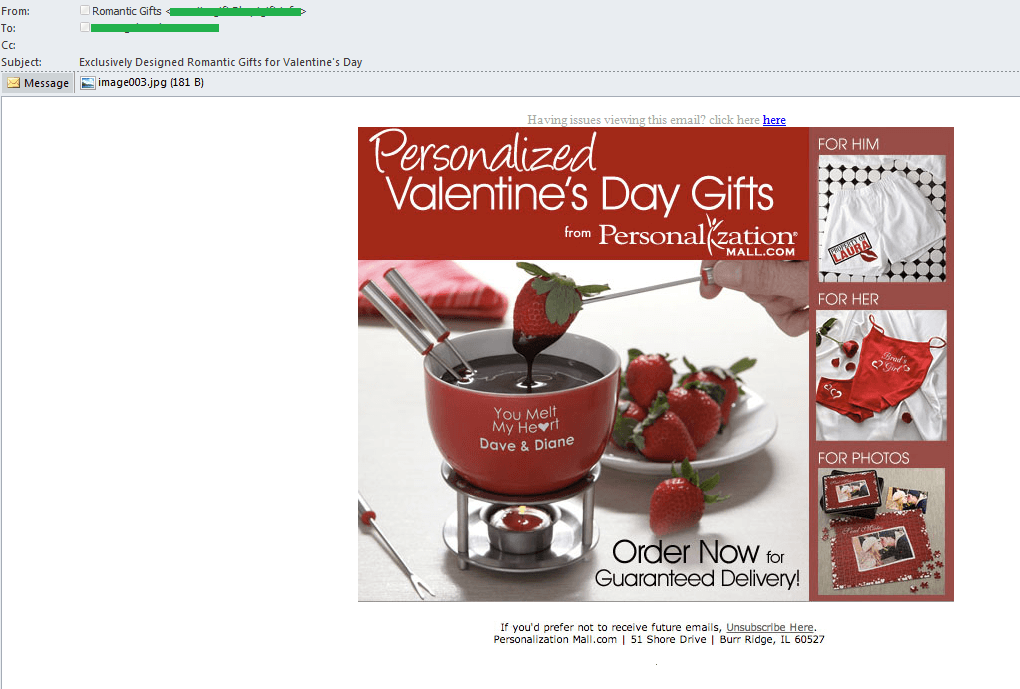
Personalized gifts, which have recently made up a big part of spam mailings, took on a Valentine’s theme in January.
The holiday theme even found its way into the ‘Subject’ fields of mass mailings offering credit, slimming aids and replicas of designer goods.
From China with spam
China has long been a leading source of spam. Junk emails from China offering business partnerships have spread all over the Internet. Chinese companies sell toys, flashlights and computer equipment, or offer transportation services. These emails usually contain a warm greeting, but one that doesn’t address the recipient personally.
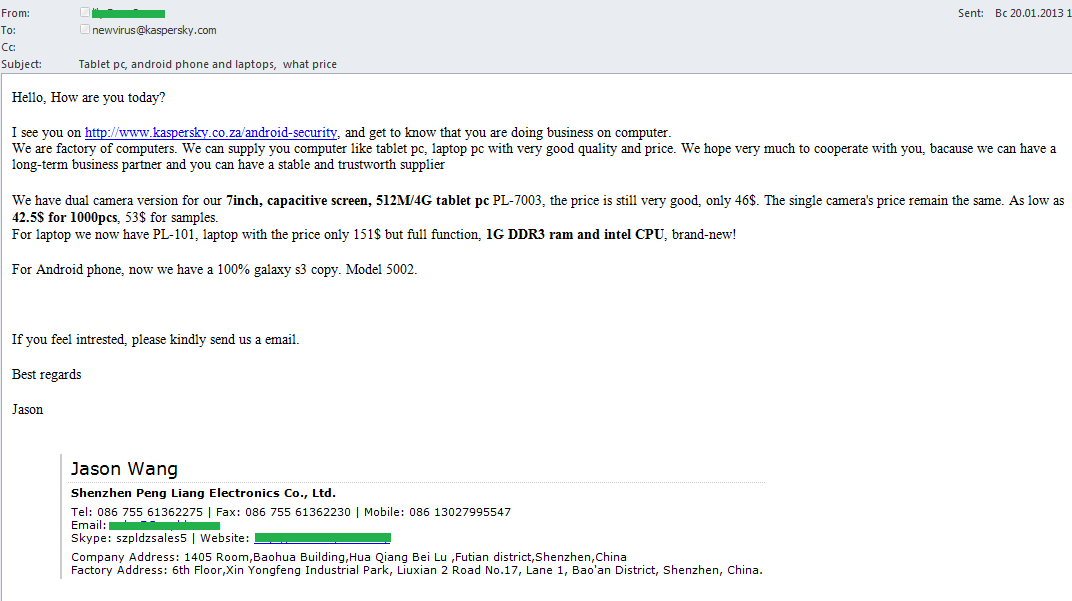
In January, an email offering computer equipment arrived from China to the Kaspersky Lab address. The sender included a link to the company’s official website (and specifically a link to our antivirus product for Android). The message also contained all the sender’s contacts.
This email looks like a well-designed template where the sender changes the addressee and the link to the recipient’s official site.
The geographical distribution of spam sources
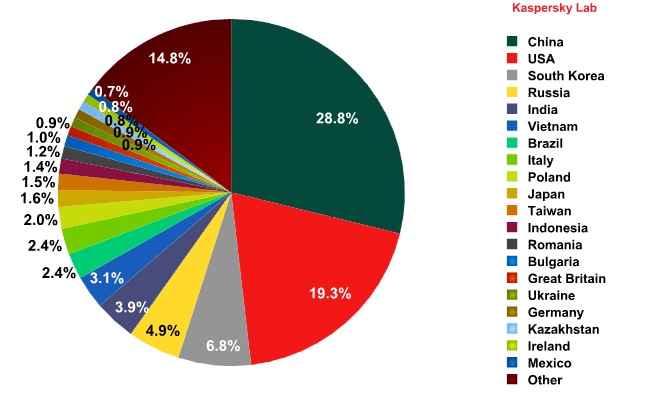
In January, China (28.8%) and the US (19.3%) remained the leading sources of spam worldwide. The amount of spam sent from China decreased by 5.4 percentage points, while the percentage of spam originating in the US grew by 3.7 points. Overall, these two countries produced 48.1% of global spam.
Sources of spam around the world by country
In January, South Korea unexpectedly entered the top three sources of spam (+4.1 percentage points). India fell to 5th place, down 1.7 points from December.
Russia moved up one place to 4th (+ 1.8 percentage points).
Germany dropped from December’s 7th place to 17th with 0.9% of all distributed spam, though the percentage of unsolicited emails originating from this country only slightly changed (-1.5 percentage points).
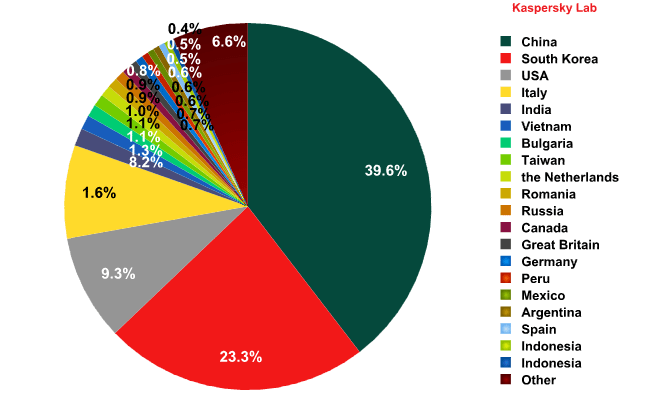
The first month of 2013 also saw China maintain its leading position as the main source of spam sent to European users despite the noticeable drop in the volume of junk email (-18.6 percentage points) originating from this country. South Korea came 2nd with an increase of 18.7 percentage points. The USA was 3rd having distributed 0.6 points less spam compared to December.
Sources of spam in Europe by country
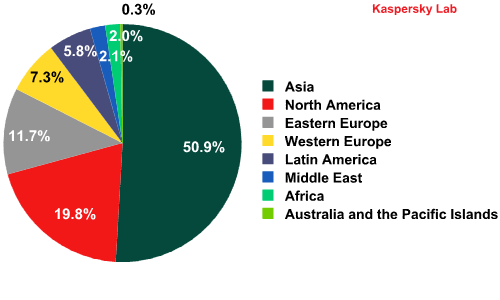
Asia remained the leading regional source of spam (50.9%). As in December, the Top 3 also included North America and Western Europe.
Sources of spam by region
Malicious attachments in email
Although the share of spam in mail traffic decreased, the percentage of mass mailings that contain malware remains quite high. In January, malicious attachments were detected in 3% of emails, a drop of 0.15 percentage points from December.
Top 10 malicious programs spread by email
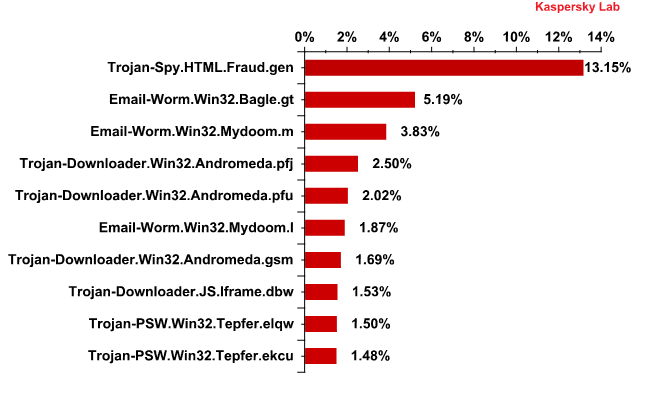
Trojan-Spy.HTML.Fraud.gen regained its position as the most widespread malicious program carried by email. In much of 2012 it was the leader of this rating but in September the amount of emails containing this malicious program decreased drastically and it fell out of the Top 10. This Trojan program is also designed to steal passwords – and not just for online banking but also for a broader range of online accounts.
The Top 10 includes two other malicious programs targeting user passwords. They both belong to the Tepfer family and occupy 9th and 10th places.
Mail worms came 2nd and 3rd in the rating. Mydoom’s main functionality is to self-proliferate to addresses in the victim’s address book, while Bagle can also download other malicious programs onto a user’s computer.
The Andromeda family malware took 4th , 5th and 7th places in the Top 10. Once installed on victim computers, these threats download other malicious programs onto the system, after which it deletes itself.
Email antivirus detections by country
There were no major changes in January to the list of countries that are most heavily targeted by malicious emails.
Not surprisingly the USA, with more Internet users than anywhere else, remains the most widely targeted. In addition, many malicious programs were designed to steal passwords for online banking services which are very popular and highly developed in the USA.
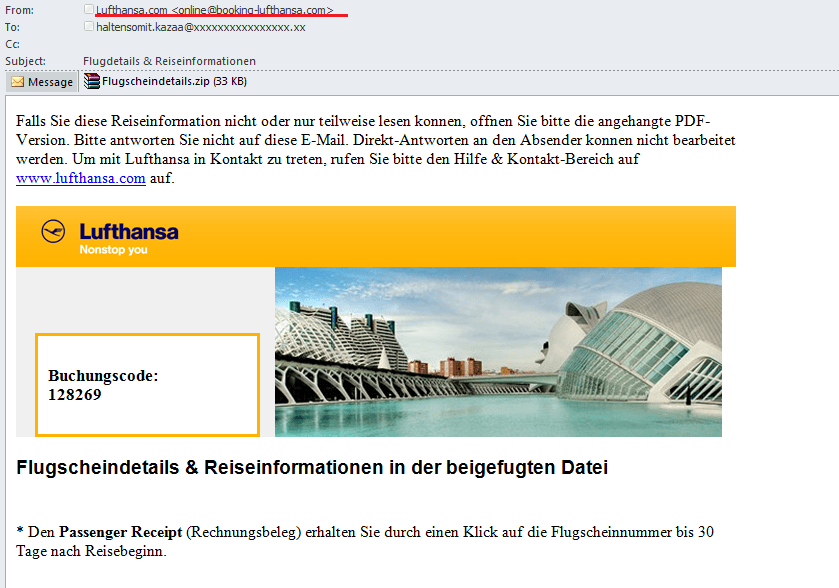
Spammers continued to spread fake notifications from various services. In January, their attention was again focused on the popular online booking service Lufthansa.com. Notifications which allegedly arrived from online@booking-lufthansa.com contained the malicious zip archive with Flugscheindetails.PDF.exe detected by Kaspersky Lab as Trojan-Downloader.Win32.Andromeda.ply. This Trojan took 12th place in the programs distributed via email in January.
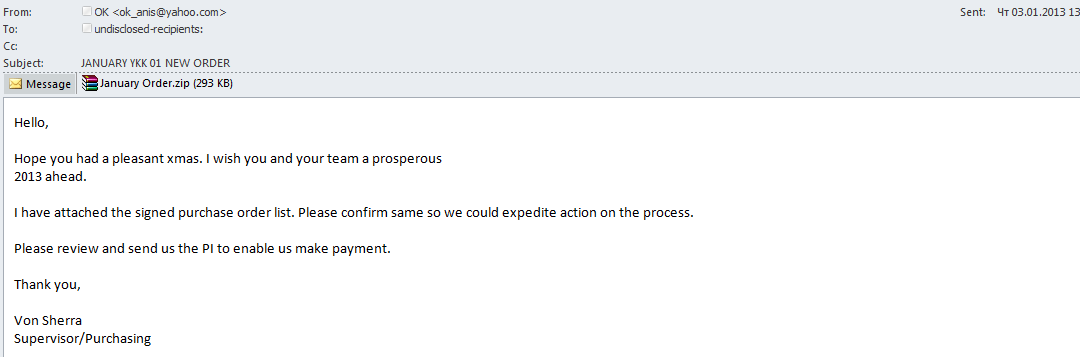
However, spammers did not confine themselves to sending fake notifications from popular online services. For example, one email supposedly contained a signed list of ordered goods which was in fact a malicious zip archive containing a file named January Order.scr that is detected by Kaspersky Lab as Trojan-Spy.Win32.Zbot.hviq.
Phishing
The percentage of phishing emails in total email traffic halved in January and settled at 0.003%.
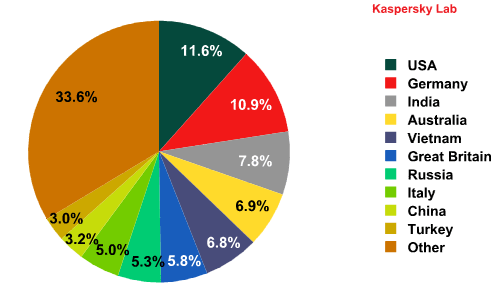
The distribution of the Top 100 organizations targeted by phishers, by category*
*This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
The Top 5 organizations targeted by phishers underwent some major changes in January.
The number of phishing attacks against social networking sites increased by 9.71 percentage points, accounting for 39.62% and keeping this category at the top of the ratings.
The share of attacks on search engines (+3.6 percentage points) and IT vendors (+ 1.2 percentage points) also grew, which placed these categories in 2nd and 4th positions respectively.
At the same time, the number of phishing attacks targeting online stores and e-auctions (-5.8 percentage points) and financial and e-pay organizations (-7 percentage points) fell considerably compared with the previous month.
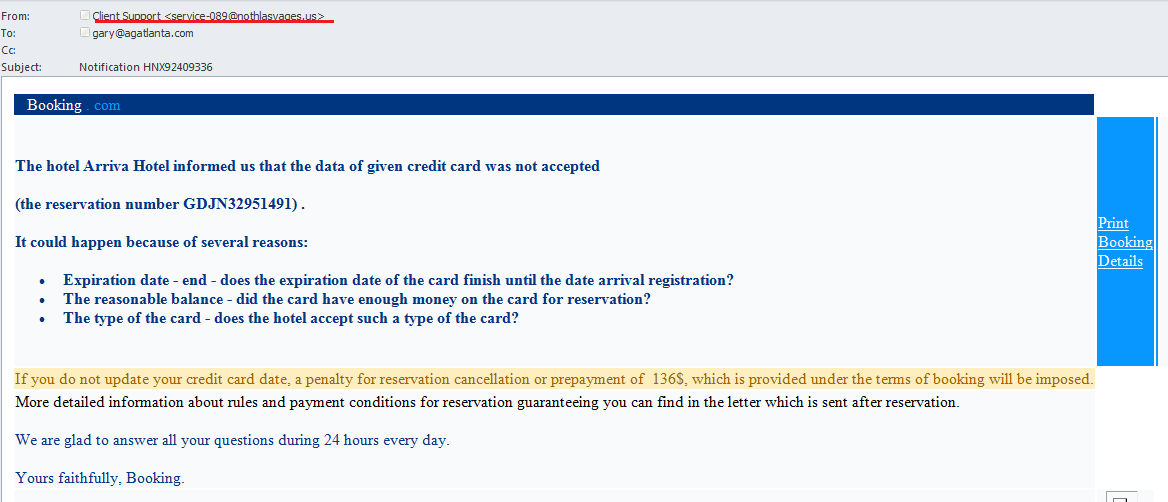
Phishers continue to distribute emails imitating mass mailings from popular services which, by all appearances, seem to be rather effective. In autumn, we wrote about fake notifications from Booking.com containing malicious attachments. In January, we registered a new wave of phishing mailings sent on behalf of a famous hotel booking site. This time the phishers tried to extort credit card data from users.
The message informed recipients that their credit card data had not been accepted. To avoid a penalty for cancelling the reservation, which could be imposed under the terms of booking, users were asked to update their credit card data. It was another example of the phishers using the time-tested method of threatening their potential victims. Booking.com’s regular customers could have been expected to spot the scam straight away, but many still fell into what turned out to be an effective trap.
An alert user would notice that the sender’s address in this email had nothing to do with the name of the company which allegedly sent the message.
Banking-related phishing is still very popular on the Internet. In order to redirect users to phishing pages and steal their credit card numbers and passwords, the fraudsters have resorted to their old trick of notifying users of a number of failed attempts to enter their account and warn them of the need to install extra protection. Below is one such email:
Unlike the previous message from Booking.com, this email had a real bank address Informationen@postbank.de in the ‘From’ field which could help convince recipients that it’s genuine.
Conclusion
As expected, the total amount of spam decreased in January due to the post-festive season lull.
In mid-January, the first mass mailings exploiting the theme of Valentine’s Day and International Women’s Day (March 8) appeared. These mailings were not as numerous as the Christmas and New Year ones, but the variety of products and services offered was no less impressive.
The annual Valentine’s Day spam – emails with malicious attachments imitating Valentine’s cards – did not materialize in January. Traditionally, Valentine’s offers peak at the beginning of February.
January saw a continued decline in the number of phishing and malicious emails in spam traffic. However, the popularity of booking services was still being actively exploited by fraudsters to steal credit card data.




















Spam in January 2013