
Recent trends
- The amount of spam in email traffic decreased by 0.9% compared to October’s figure. The overall average being 84.8% for November.
- Links to phishing sites were found in 0.97% of all emails, an increase of 0.06% compared to October.
Malicious files were found in 0.83% of all emails, a decrease of 1.12% compared with the previous month. - The amount of festive season spam is growing very fast.
- In order to evade filtering, spammers are actively using HTML code.
Spam in mail traffic
The amount of spam detected in mail traffic averaged 84.9% in November 2009. A low of 78.3% was recorded on 18 November with a peak value of 89.6% being reached on 16 November.
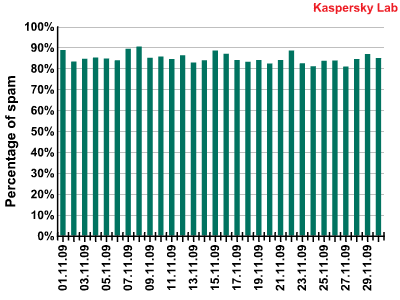
Percentage of spam in mail traffic in November 2009
Malware in mail traffic
Malicious files were found in 0.83% of all emails, a decrease of 1.12% compared with the previous month.
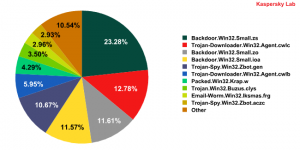
Malware found in spam messages during November 2009
This month’s clear leader in the malicious programs Top 10 is the Backdoor.Win32.Small family. The previous month saw one representative of this family in the Top 10 but in November the total quantity of these malicious programs exceeded 45%. All in all, the Top 10 includes three versions of the ‘small’ Backdoor – Small.zs, Small.zo and Small.ioa. Once installed, these versions collect information about the infected computer and send it to the command server. They can also download additional components.
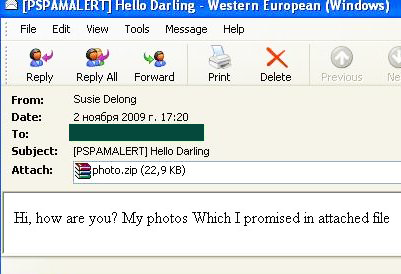
In order to spread Backdoors of this type, spammers used the old social engineering trick of attaching a zip archive with the title ‘Photos’ to a message stating that the attachment contained some photos that were promised a while ago. In fact, the attachment contains a malicious program.
Two Trojan-Downloader.Win32.Agent versions, Agent.cwlc and Agent.cwlb, occupy second and sixth places respectively in November’s Top 10. After installation, these programs connect to the system resources in order to access the URL list which is then used to download other malicious programs.
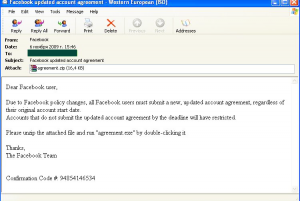
In order to distribute these pieces of malware, fraudsters used fake notifications from the popular social networking site Facebook. The messages said that according to Facebook’s new security policy, all users had to accept the agreement regardless of the date that their accounts had been registered. The users were also warned that account holders that did not agree to the terms would have their accounts canceled. To accept the agreement a user had to unpack the attached archive, which turned out to be Trojan-Downloader.Win32.Agent.cwlb.
Two changes in November’s Top 10 are particularly noticeable compared to the previous month. First of all, two Zbot versions have appeared at fifth and tenth places, though one of them, Trojan-Spy.Win32.Zbot.gen, was also recorded in September. Just to remind you, Trojan-Spy.Win32.Zbot is Trojan spyware designed to steal confidential data. A more detailed description of the program is available at https://threats.kaspersky.com/. The second important change was the return of Iksmas, a mail worm that is designed to steal a user’s confidential data and to distribute spam.
Phishing
PayPal and eBay remain the most popular targets for phishers, with 44.53% (+5.61%) for Paypal and 19.42% (+12.29%) for Ebay. There was a sharp rise (6.9%) in the number of attacks on Facebook during November, with the social networking site targeted by 9.03% of all phishing attacks.
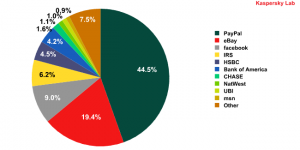
Organizations targeted by phishing attacks in November 2009
Bank of America (4.22%), one the phishers’ ‘favorite’ targets, was subjected to a well-organized attack in November. The messages that users received very closely resembled legitimate notifications from the bank.
The email above informed recipients that representatives of the bank had already contacted the account holder in order to verify their account and that the verification process must now be completed by clicking a link. The link contained in the email had nothing to do with the bank and leads to a phishing site.
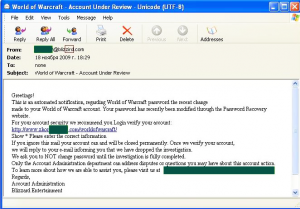
Additionally, fraudsters continue to be especially persistent in their attacks on users of the popular online game World of Warсraft. Their messages closely resemble genuine notifications from Blizzard Entertainment. The address in the ‘From’ field looks very much like the company’s real address and only a vigilant user will notice the difference. As per the email above, the message requires that the user verifies their account and in so doing they are directed to a phishing site.
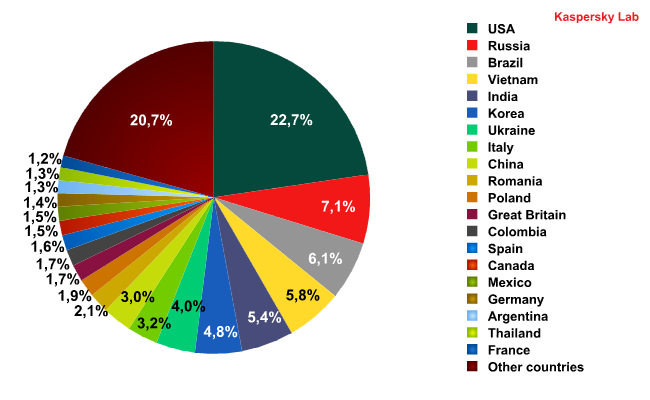
Sources of spam
In November, the USA maintained its position as the prime distributor of spam, though the quantity of spam originating from there decreased by 10% when compared to October’s figure. Brazil, which used to be in second place, fell two places to fourth, even though the amount of spam originating there increased by 0.7% compared to the previous month. Russia jumped to second place with just over 8% of spam distribution worldwide (+2.8%). India came third having distributed nearly twice as much spam as in previous months (7.2%). Fifth, sixth and eighth places were occupied by those resident favourites – Vietnam, Korea and Poland, whose October’s figures remained largely unchanged. Italy’s ‘contribution’ increased by 1.2%, placing it in seventh. The UK fell from twelfth to fifteenth position, with 1.7% of November’s spam total originating from there.
Spam by category
The Medications and health-related goods and services category retained the lead among English-language spam. However, the Christmas theme is even more popular, especially with spammers offering fake designer goods.
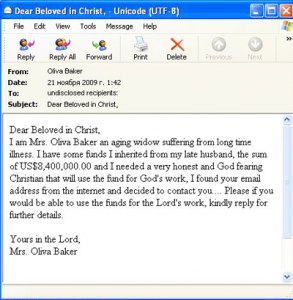
Two English-language spam themes that occur frequently are Christmas-style messages that can be included in the computer fraud category, and offers of cheap software which spammers promote heavily over the Christmas period. In the run-up to Christmas, Nigerian letters try to appeal to the users’ religious feelings. For example, we received a letter from an inconsolable widow who had just inherited a multi-million dollar fortune from her deceased husband. In the letter, the widow expressed her willingness to share a modest portion of her money with a pious Christian.
This year Christmas seems to have affected the content of messages from spammers of fake designer goods and those behind the various Nigerian letters. Every year spammers spread emails offering Christmas-related goods and services. This year’s mass mailings got underway with spam messages offering personal letters from Santa Clause to users’ children.
Spammer methods and tricks
In November, spammers continued to distribute emails containing HTML code which included random symbols and blocks of dashes in different numbers and positions. The email itself looked quite ordinary however.
Conclusion
The amount of fraud in spam continued to grow in November. We foresee things becoming even worse in December due to the perception that the festive season will catch users off their guard, and fraudsters rarely miss an opportunity to take full advantage of such lapses.
The decrease in the number of malicious programs in November does not mean the trend will continue in December. Christmas and New Year is traditionally a time when e-cards are sent and received. Thus, it is most likely that malware will be hidden within Christmas and New Year e-cards.
No doubt December will see an increase in the amount of spam relating to the forthcoming Christmas and New Year period in some way or other.
























Spam evolution: November 2009