
Spam by category
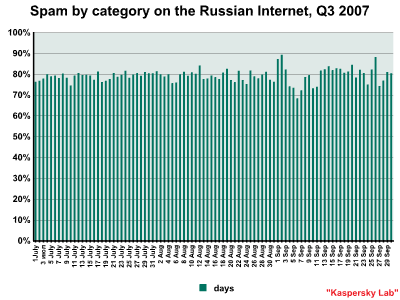
In the third quarter of 2007, the share of spam steadily approached 80% of all mail traffic on the Russian Internet: the average over the quarter came to 79%. The low in the third quarter was recorded on 6th September at 68.1% and the quarterly high occurred on 2nd September with 89%. An increase in spammer activity was noticeable early this autumn; a regular occurrence at this time of year.
The leading spam categories in the third quarter of 2007 were:
- Medications, health related goods and services (28.5%).
- Computers and the Internet (10.5%).
- Education (9.6%).
- Travel and tourism (7.8%).
- Electronic advertising services (6.6%).
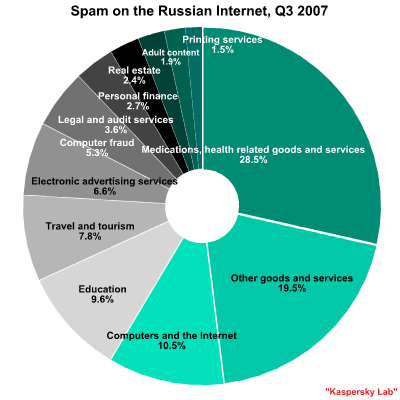
The composition of the top five spam categories remains the same except for one detail: the computer fraud and electronic advertising services categories switched places, putting the latter in fifth place with 6.6%.
First place in the top five went to the medications, health related goods and services category. This category increased 8% from the second quarter of 2007 and has now doubled the figures shown by this type of spam in the first quarter of the year. This rapid growth was triggered by mass mailings advertising Viagra, which currently represent the overwhelming majority of emails in this category.
In contrast, the personal finance category continued its decline through the third quarter and now stands at just 2.7%. This drop has been continuous since the beginning of the year, in spite of spammer attempts to implement new techniques and revive old methods in an attempt to get financial spam past spam filters.
Pump-and-dump stock spam: spammer techniques
For more than a year now, spammers have been trying to master new ways of evading spam filters in order to deliver spam that promotes stocks (so-called ‘stock spam’ or ‘pump-and-dump’ spam). The third quarter of 2007 was no exception – spammers applied the entire gamut of their new tactics to this type of spam.
Readers may recall that in June, spammers came up with a new way of delivering spam images – attaching them as PDF files. As Kaspersky Lab analysts predicted, the use of PDF-format spam petered out rather quickly; by late June, spam messages with PDF attachments accounted for just 0.1% – 1% of all spam.
Spammers continued to experiment with attachments in spam messages last quarter. In July we saw the arrival of investment spam messages with ZIP archive attachments, and in August spammers began sending messages with FDF format attachments. There was no text in the body of emails sent with these attachments. Recipients could view the contents of the FDF file by opening it with Acrobat Reader (and the contents were typical graphical spam, using random images, different colored backgrounds, and fonts in a variety of colors and sizes).
In September, spammers once again attempted to revive a tactic that became well known in 2003: sending simple email messages in plain text in which certain letters are replaced with non alpha-numeric symbols, and letters in keywords are separated by non alpha-numeric symbols. As has happened more than once already, these experiments resulted in unreadable messages, such as:

Flash mailings
Spammers are traditionally more active in early autumn. This year, their increased activity resulted in a wider variety of spam and the active usage of technologies which, although they had previously been used, were not particularly common. One such technology is flash mailings: while a standard mass mailing lasts for approximately 2 days (and in some cases, up to two weeks), flash mailings take just 15 – 30 minutes with an identical number of messages being sent in each mailing. Spammers are clearly counting on spam filters not being able to detect and combat threats within such a short space of time.
Flash mailings have specific characteristics which result from the need to complete the mailing quickly:
- as a rule, the messages in such mailings are small and often in plain text; if the message contains an image, it will be a small image of poor quality;
- spammers specifically use tactics that will not increase the size of the message e.g. they may vary the message body and any URL, but they will not include random fragments of text or use other techniques to create background ‘noise’ within the email.
Spammers began implementing such flash mailings in mid-September, and this type of mailing is on the increase, albeit slowly. By late September, flash mailings represented up to 10% of all spam on some days.
Why is it that so many spammers are now using this type of mailing technique? This choice is likely to do with the fact that the number of computers and computer users is on the rise, which means that botnets are also increasing in size. Moreover, access to the Internet is becoming faster all the time, with dial-up connections being replaced by dedicated lines and ADSL.
Most flash mailings are English language advertising for a variety of Viagra-type medications. Russian-language spam advertising other goods and services is also sent using this technique, but is much less common. Unlike their counterparts in other countries, Russian spammers try to send relatively large messages in flash mailings. There have so far been only a few isolated cases, but it’s possible that spammers will, in the future, work out how to send any size of message in flash mailings.
Continued criminalization of spam
Despite an official drop in the number of fraudulent emails in all spam (from 9% in 2Q2007 to 5.3% in 3Q2007), the criminalization of spam continues. Such spam typically advertises counterfeit and unlicensed goods. Spammers have no compunction about selling obvious fakes. However, while watches are clearly described as being “copies” of leading brands, spammers do not mention the dubious origins of most of the medications they offer. In the best case scenario, the people who purchase these medicines receive harmless sugar pills; in the worst, they can fall victim to drugs that are harmful to their health.
As far as computer fraud spam is concerned, Nigerian (a.k.a 419) scams still make up the vast majority of emails in this category. Although the amount of spam in this category has fallen overall, scammer attacks are becoming targeted and consequently more of a threat.
Targeted attacks by 419 scammers
Spammers who send 419 scam messages have turned their attention to Russian-language dating websites. Users who set up a profile on these websites risk receiving touching messages from alleged would-be partners – in some cases, such emails are sent mere minutes after a new profile is set up.
The scam is the same as ever: the sender of the email asks the recipient for assistance in releasing millions of dollars, with a generous amount in compensation being offered in return. This fools gullible victims into handing over thousands of dollars in initial expenses. However, the scammers have changed the theme of their emails. Internet users are no longer receiving emails from dictators’ widows, the secretaries of disgraced millionaires or philanthropic bank staff. Instead, the scammers are trying a different tactic, spinning a yarn of heirs and heiresses due to receive millions who have suddenly become overcome with love for the recipient of the email (who is, of course, the potential scam victim). The scammers are relatively subtle: the request for help in rescuing millions and a helpless, exotic beauty into the bargain isn’t generally voiced until the third or fourth email, by which time the potential victim has voiced sympathy for their new contact.
An example of a typical 419 scam is shown below. (Russian Internet users receive this type of messages both in English and in Russian. The Russian language variants are produced using machine translation).
Dearest Love,
I am more than happy of your reply to my mail. How is your day today, My name is Miss Andaline single and never been married, i am from Sudan in East Africa, 23 yrs, at earlier i was residing in Darfur s refugee camp in Chad on January 2005, at a time, there is a division and dispatch of some of the refugees due to the over population of the people in Chad, i was taken to Senegal West African on 10th August 2006 where I’m presently residing in N’dioum refugee camp here in Senegal where i am seeking political asylum due to the civil war in my country. I am in sufferings and pains here in this camp and i really need to have a man by my side to encourage me and give me good advice in life and help me to come out from this situation.
My late father Dr Col Nathaniel Mbarote was the Industrial Managing director of (MBAROTE AND INDUSTRIAL COMPANY LTD) in the federal capital of Sudan (KHARTOUM) the economy capital of my Country, and he was also the personal adviser to the former head of state, before the rebels attacked our house one early morning and killed my mother and father in a cold blood. It is only me that is alive now and i managed to serve my life here in Senegal where i am living now as a refugee. This Refugee Camp is headed by a Reverend Father, i used his office computer to send you this email and i only enter his office when he is less busy in his office.
I would like to know more about you, your likes and dislikes, your hobbies and what you are doing presently. i like to meet understanding, loyal, sincere, truthful, kindly and friendly and more to that, a man of vision and truth. I will tell you more about myself in my next mail. Attached here is my picture, Hoping to hear from you soonest.
Miss Andaline
Phishers testing the waters of the Russian Internet
Previously, phishers were not particularly interested in Russian Internet users, since electronic payment systems in Russia were not as widely used as in Western countries. However, in the third quarter of 2007, Russian-language phishers became more active.
n particular, in summer we saw attacks against users of Mail.ru email, WebMoney and Yandex.Dengi. In the latter case, scammers implemented a tactic commonly used by their counterparts in other countries, i.e. asking users to click on a link that looks very similar to a company’s real URL. Here are some examples of links received by users of the Yandex.Dengi service: http://www.passport-yandex.ru, http://yanclex.ru, http://yandcx.ru/.
Subject: New security measures
Dear User,
Due to instances of fraud stemming from unauthorized access to Yandex services, in accordance with point 9.1 of the user agreement, we must inform you of the introduction of new security measures which will enable you to receive messages about attempts to access your account from unregistered IP addresses and react promptly to counteract the theft of personal data (contact information, correspondence), funds held on the Yandex.Dengi system or data displayed on the Yandex.Direct sytem.
In line with point 9.1.1 of the user agreement, you must register your IP address in the system within three days of receiving this notification.
Click this link to register and follow the instructions: http://www.passport-yandex.ru/?mode=GETIP&sauth=retire&uid=O&retpath=http://yandex.ru
In late summer and early autumn, phishers conducted several targeted attacks on corporate users of the Russian Internet. The targets were clients of Alfa Bank. Clearly, the phishers were hoping that it would be easier to find potential victims among employees of major companies. This was the first recorded instance of such targeted phishing mailings.
Clearly, depending on the effectiveness of these attacks, the phishers will decide whether to continue with similar mailings or whether to wait for a better time. From a security point of view, the problem is that Russian-speaking users, unlike Western users, have not yet been widely exposed to phishing emails and may well swallow the bait. The less aware recipients are about the operation of companies from which phishing emails purportedly come , the more successful a phishing attack is likely to be. Certainly a large number of Internet users are unaware that major companies (including email providers, electronic payment systems, online banking systems and Internet auctions) never send their users email messages requesting confidential data.
It is likely that phishers will continue to target Russian Internet users, and that the share of Russian-language phishing emails in total email traffic will continue to rise.
Conclusion
In late summer and early autumn, spammers traditionally become more active and test new spamming tactics and technologies. As a rule, this is the period during which spamming trends for the next 12 months are defined.
The third quarter of 2007 was no exception. Based on these quarterly results, we can expect to see an increase in the volume of spam and in the speed at which mailings are sent, new spam experiments with graphical spam, and more activity by phishers and scammers on the Russian Internet.
Recent trends
- Spam accounted for an average of 79% of all mail traffic during the third quarter of 2007.
- Spammers are using a combination of old and new methods to push stocks.
- Spammers are increasing the usage of flash mailings.
- Phishers are testing the waters of the Russian Internet using targeted attacks.

















Spam evolution: July – September 2007