
Recent trends
- The amount of spam in email traffic increased by 3.5% compared to December’s figure. The overall average being 86.1% for January.
- Links to phishing sites were found in 0.81% of all emails, a decrease of 0.03% compared to December.
- Malicious files were found in 0.07% of all emails, a decrease of 0.09% compared with the previous month.
Spam in mail traffic
The amount of spam detected in mail traffic averaged 86.1% in January 2010. A low of 78.9% was recorded on 8 January, with a peak of 89.5% on 24 January.
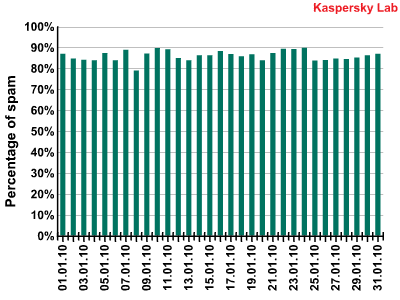
Percentage of spam in mail traffic in January 2010
Malware in mail traffic
Malicious files were found in 0.07% of all emails, a decrease of 0.09% compared with the previous month.
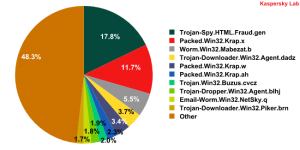
Malware found in spam messages during January 2010
The amount of emails containing files packed using Packed.Win32.Krap.x has decreased considerably when compared with December’s figure, but still makes up a significant part of the average at 11.66% of all infected mail traffic. This put the packer at No.2 in the Top 10 of the most popular malicious mail traffic programs. Just to remind you, this Krap modification is used for packing Zbot, FraudTools and Iksmas.
Another modified version of Krap – Packed.Win32.Krap.ah – was also to be found in the Top 10 due to its use in packing files found in 2.35% of all emails.
The leader of January’s Top 10 was Trojan-Spy.HTML.Fraud.gen, the only representative of the HTML platform in the Top 10 over the last few months; the rest of the malicious programs run under that most popular of platforms, Win32.
Fourth and eighth place was taken by Trojan-Downloader.Win32.Agent.dadz and its ‘brother in arms’ Trojan-Dropper.Win32.Agent.blhj. Though these Trojans belong to different families (one of them is a Trojan-Downloader, the other is a Trojan-Dropper) they both secretly install the same malicious program detected as Trojan.Win32.Fregee.h on an infected computer. The only difference is that after installation, Trojan-Downloader.Win32.Agent.dadz tries to connect to the Internet and download other programs.
Third place was occupied by Worm.Win32.Mabezat.b.
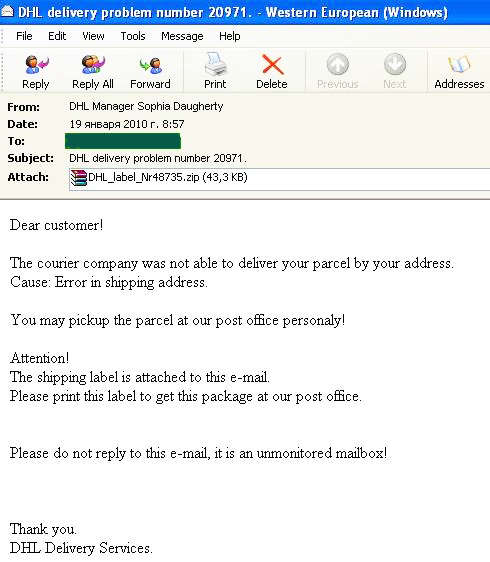
Interestingly, three of the Top 10’s programs were present in a mass mailing sent out in the guise of messages originating from DHL (see below). They were Packed.Win32.Krap.x, Trojan-Downloader.Win32.Piker.brn, which downloaded several unwanted files to the system, and Trojan-Downloader.Win32.Agent.dadz. Some fake notifications also contained an archived Backdoor.Win32.Bredolab.bvb.
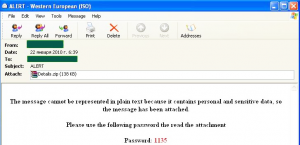
Additionally, January saw a mass mailing which carried a password-protected archive. The emails bore the header ‘ALERT!’ and contained a notification saying that in order to prevent the disclosure of confidential information, all the necessary data was contained within the attached archive, the archive’s password being sent along with the archive itself.
Phishing
In January 2010, links to phishing sites were found in 0.81% of all emails. PayPal (+21.68%) and eBay (-6.81%) remained the most popular targets for phishers.
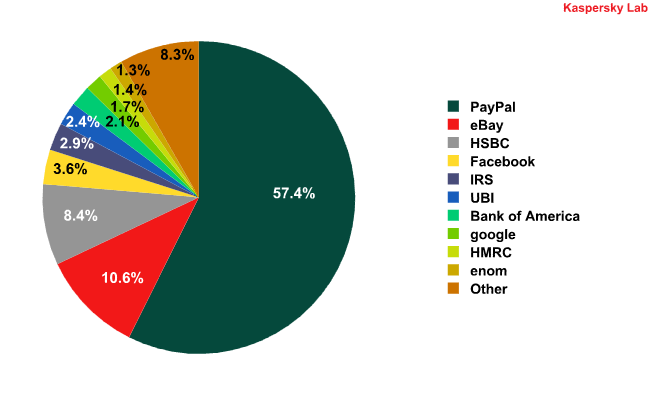
Organizations targeted by phishing attacks in January 2010
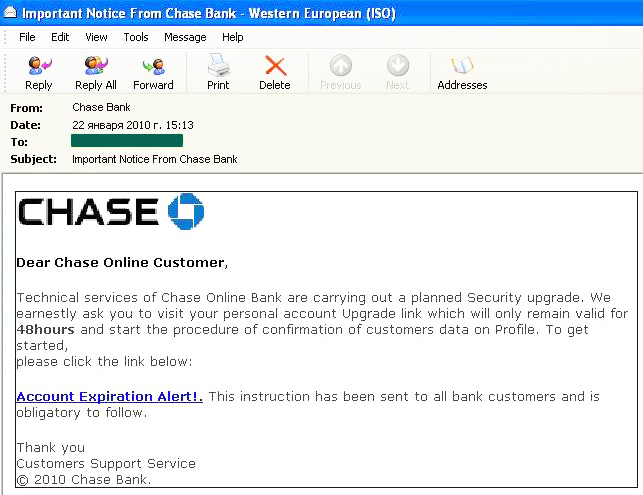
The number of attacks on Facebook decreased considerably (-6.58%) compared to the previous month, seeing this popular social networking site drop to fourth position in the Top 10, making way for HSBC to take the lead. This bank was attacked twice as often as in December (+4.5%). One of the phishing mass mailings targeting HSBC customers asked users to reset their online banking session by using a link. In order to ‘reset’ they had to enter their personal data and password into a form provided by the phishers.
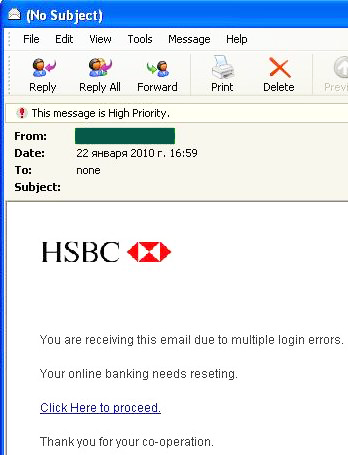
The same scam was used by phishers targeting clients of Chase Bank.
Sources of spam
In January, the US maintained its position at the top with a slight decrease of 2.3% compared to December’s figure. Brazil and Russia swapped positions, occupying second and third places respectively. We expected Russian spam to decrease a little because the majority of the botnets located in the Russian Federation would be offline during the long holidays at the beginning of January. Contrary to these expectations, the quantity of spam originating from Russia increased by 0.1%, which means spammers made up for lost time in the second half of the month.
China moved up to the sixth place with an increase of 0.5% compared to December.
Ukraine’s offering was only 1.63% of the total spam figure, which was 2.5% less than that of the previous month.
Interestingly, in January, Columbia entered the Top 10 with an increase of 1.2% on December’s figure.
The UK occupied thirteenth place with 1.84% of the total volume of spam distributed from there.
Spam by category
The medication and health-related goods and services category retained its lead among English-language spam with over 35% of the total volume of spam. Closer to the end of January spammers started exploiting the theme of Valentine’s Day, sending out advertisements for their favorite ‘Love Drug’ in the process.
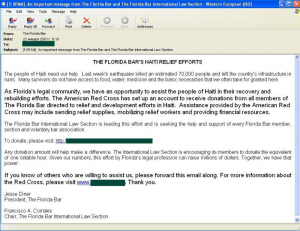
January saw a considerable increase in fraudulent spam, averaging some 22%. Some of this was dedicated to the 2010 Haitian earthquake, with fraudsters attempting to raise funds ‘for Haiti’s recovery’. There is little doubt that Haitians will never actually see the money that kind-hearted users sent to the spammer.
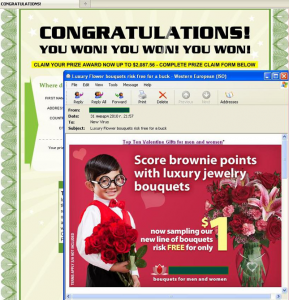
The number of emails advertising different goods and services decreased in January, accounting for 4%. This can be explained by the fact that the majority of emails from the Other Goods and Services category are seasonal in character. For example, in December they advertised Christmas presents and in January they switched to Valentine’s Day material.
The Top Ten Valentine Gifts for men and women link in the above email redirected users to an instant lottery site.
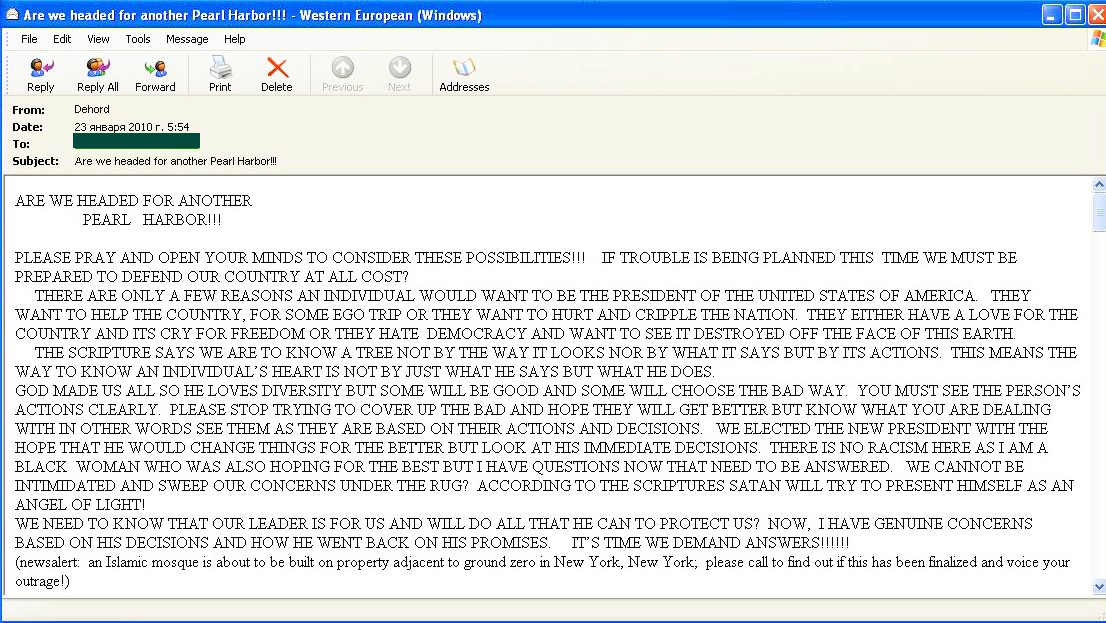
In addition, English-language spammers continued to send provocative, politically-themed emails attacking US President Barack Obama. These mailings were not exactly large-scale and usually contained a lot of text.
Conclusion
As we expected, the amount of malicious attachments remained rather low. Spammers used tried-and-tested methods to distribute malware such as fake notifications from DHL, rather than implementing anything new or different.
As anticipated, the amount of phishing seemed to stabilize. Most likely the situation will remain unchanged for the next couple of months.
The growth in the volume of fraudulent emails was the most noticeable feature of last month. This category includes phishing emails, Nigerian letters, fake notifications of lottery wins, etc. In January such emails accounted for more than 20% of the total volume of spam in mail traffic.























Spam evolution: January 2010