
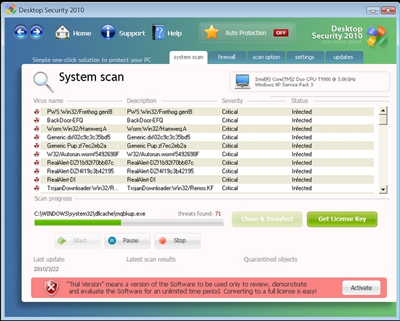
Rogue antivirus programs have been around for years now, trying to scare people into buying fake products.
This time, Desktop Security 2010 RogueAV comes with an interesting new trick to frighten users.
The main rogue component creates a remote thread in taskmgr.exe in order to call LoadLibrary from its dll component: taskmgr.dll.
This dll is part of the scare tactics.
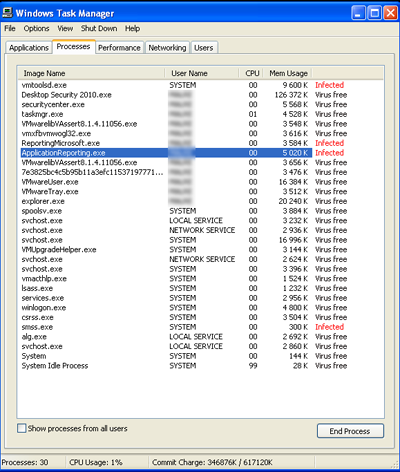
As you can see in the screenshot below, the words “virus free” and “infected” were inserted in front of process names:
The dll is packed with a custom packer. Once the dll has been unpacked, it’s easy to find out how it performs the modification.
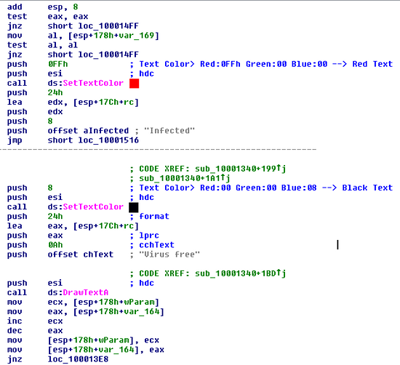
Here is a small snippet from the unpacked dll to understand how it manipulates Task Manager:
As you can see above, it uses the SetColorText API function to change the text color. A comment has been added to the color parameter on the screenshot.
Finally, the DrawTextA API function is used to add the text.
This is a simple but effective trick to scare those people who use Task Manager to detect and remove malware.



















Rogue Anti Virus: Scaring people with Task Manager