
News Overview
Without doubt, 2016 was the year of Distributed Denial of Service (DDoS) with major disruptions in terms of technology, attack scale and impact on our daily life. In fact, the year ended with massive DDoS attacks unseen before, leveraging Mirai botnet technology, whose first appearance was covered in our last DDoS Intelligence Report.
Since then, we have published several other detailed reports dedicated to major attacks on Dyn’s Domain Name System (DNS) infrastructure, on Deutsche Telekom, which knocked 900K Germans offline in November. Additionally, we tracked similar attacks on Internet service providers (ISPs) in Ireland, the United Kingdom and Liberia all leveraging IoT devices controlled by Mirai technology and partly targeting home routers in an attempt to create new botnets.
Although ‘Rise of the Machines‘, as the Institute for Critical Infrastructure Technology (ICIT) titled its analysis, sounds quite blatant, it clearly shows that stakeholders worldwide, in particular in the United States and the European Union, recognize the lack of security inherent in the functional design of IoT devices and the need to set up a common IoT security ecosystem. And not before time, as we expect to see the emergence of further Mirai botnet modifications and a general increase in IoT botnet activity in 2017.
Altogether, the DDoS attacks we have seen so far are just a starting point initiated by various actors to draw up IoT devices into the actors’ own botnets, test drive Mirai technology and develop attack vectors. The DDoS attacks on five major Russian banks in November are a very good example of this.
First, they demonstrate once again that financial services like the bitcoin trading and blockchain platforms CoinSecure of India and BTC-e of Bulgaria, or William Hill, one of Britain’s biggest betting sites, which took days to come back to full service, were at the highest risk in the fourth quarter and are likely to remain so throughout 2017.
Second, cybercriminals have learnt to manage and launch very sophisticated, carefully planned, and constantly changing multi-vector DDoS attacks adapted to the mitigation policy and capacity of the attacked organization. As per our analysis, the cybercriminals in several other cases we tracked in 2016 started with a combination of various attack vectors gradually checking out a bank’s network and web services to find a point of service failure. Once DDoS mitigation and other countermeasures were initiated, the attack vectors changed over a period of several days.
Overall, these attacks show that the DDoS landscape entered the next stage of its evolution in 2016 with new technology, massive attack power, as well as highly skilled and professional cybercriminals. Unfortunately, this tendency has not yet found its way into the cybersecurity policies of many organizations that are still not ready or are unclear about the necessary investments in DDoS protection services.
Four main trends of the year
In 2016, the DDoS attack market saw a number of significant changes and developments. We have identified the four major trends:
-
The demise of amplification-type attacks. These attacks have been around for a while and the methods for combating them are well-known and have been perfected over time. They remained quite popular in the first half of 2016, but it was clear their number and volume were gradually declining. By the end of 2016, cybercriminals had almost completely given up using malicious amplification-type attacks, ending a downward trend that had lasted several years. First of all, this is the result of countermeasures being developed for these attacks. It’s also down to a reduction in the number of vulnerable amplification hosts available to the attackers (DNS Amplification attacks are the best illustration of this) as their owners react to the performance problems and losses associated with these attacks and look for ways to patch vulnerabilities.
-
Rising popularity of attacks on applications and the growth in their use of encryption. For the last few years UDP-based amplification attacks have remained the undisputed leader on the DDoS attack market, while attacks on applications have been relatively rare. In the second half of the year, and particularly in Q4, there was a dramatic increase in the popularity of attacks on applications, which gradually filled the niche previously occupied by amplification attacks. To organize such attacks, time-tested tools (Pandora, Drive, LOIC/HOIC) and new developments are used. Along with the growing popularity of attacks on applications, the number of these attacks using encryption is also growing. The use of encryption in most cases dramatically increases the efficiency of attacks and makes filtering them more difficult. In addition, cybercriminals continue to use an integrated approach, masking a small but effective attack on applications behind a simultaneous large-scale attack, for example, an attack involving a large number of short network packets (short-packet TCP flood).
-
The rise in popularity of WordPress Pingback attacks. WordPress Pingback-type attacks, which were extremely rare at the start of 2016, had by the fourth quarter occupied a substantial amount of the DDoS attack market. This is currently one of the most popular attack methods targeting applications, and we consider them separately from the overall mass of attacks at the application level. Relatively simple to organize, the “fingerprint” of these attacks is very specific, and the corresponding traffic can be easily separated from the general traffic flow. However, carrying out such an attack using encryption (something that was observed by Kaspersky Lab experts in Q4 2016) greatly complicates filtering and increases the malicious potential of this type of attack.
-
Use of IoT botnets to carry out DDoS attacks. After the publication of code on the GitHub resource on 24 October, Kaspersky Lab experts noticed a surge in interest in IoT devices among criminals, especially their use in botnets to perform DDoS attacks. The concepts and methods demonstrated by the creators of the Mirai botnet were used as the basis for a large number of new malicious codes and botnets consisting of IoT devices. These kinds of botnets were used in numerous attacks on Russian banks in Q4 2016. Unlike classic botnets, IoT-based botnets are huge in terms of both their volume and potential, something that was proved by the high-profile attack on the DNS DYN provider, which indirectly affected the work of many major web resources (e.g., Twitter, Airbnb, CNN and many others).
Statistics for botnet-assisted DDoS attacks
Methodology
Kaspersky Lab has extensive experience in combating cyber threats, including DDoS attacks of various types and levels of complexity. The company’s experts monitor botnet activity with the help of the DDoS Intelligence system.
DDoS Intelligence (part of Kaspersky DDoS Protection) is designed to intercept and analyze commands sent to bots from command and control (C&C) servers, and does not have to wait until user devices are infected or cybercriminal commands are executed in order to gather data.
This report contains the DDoS Intelligence statistics for the fourth quarter of 2016.
In the context of this report, a single (separate) DDoS attack is defined as an incident during which any break in botnet activity lasts less than 24 hours. If the same web resource was attacked by the same botnet after a break of more than 24 hours, this is regarded as a separate DDoS attack. Attacks on the same web resource from two different botnets are also regarded as separate attacks.
The geographic distribution of DDoS victims and C&C servers is determined according to their IP addresses. In this report, the number of DDoS targets is calculated based on the number of unique IP addresses reported in the quarterly statistics.
It is important to note that DDoS Intelligence statistics are limited to those botnets detected and analyzed by Kaspersky Lab. It should also be noted that botnets are just one of the tools used to carry out DDoS attacks; therefore, the data presented in this report does not cover every DDoS attack that has occurred within the specified time period.
Q4 Summary
- Resources in 80 countries (vs. 67 in Q3) were targeted by DDoS attacks in Q4 2016.
- 71.6% of targeted resources were located in China.
- South Korea, China and the US remained leaders in terms of both the number of targets and number of detected C&C servers.
- The longest DDoS attack in Q4 2016 lasted for 292 hours (or 12.2 days) – significantly longer than the previous quarter’s maximum (184 hours, or 7.7 days) and set a record for 2016.
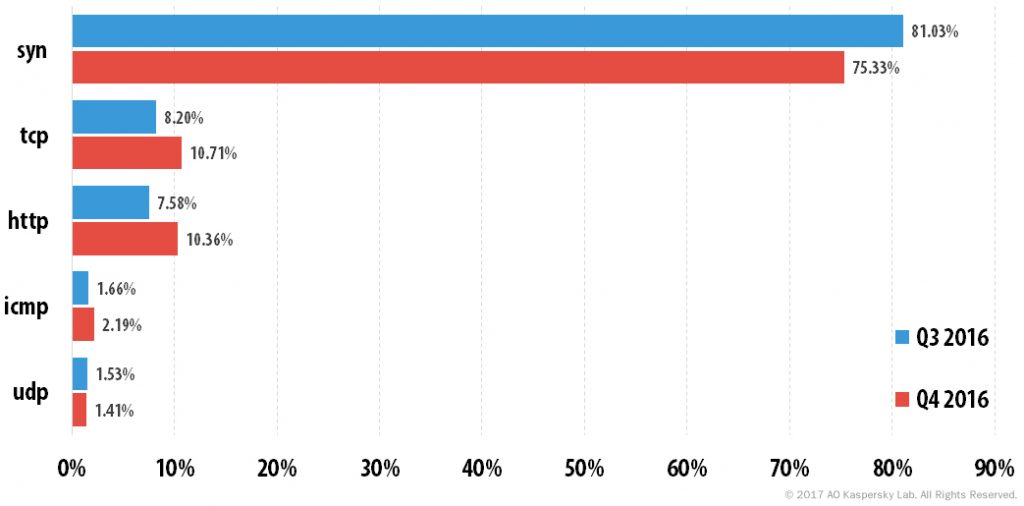
- SYN DDoS, TCP DDoS and HTTP DDoS remain the most common DDoS attack scenarios. The proportion of attacks using the SYN DDoS method decreased by 5.7 p.p., while the shares of both TCP DDoS and HTTP DDoS grew considerably.
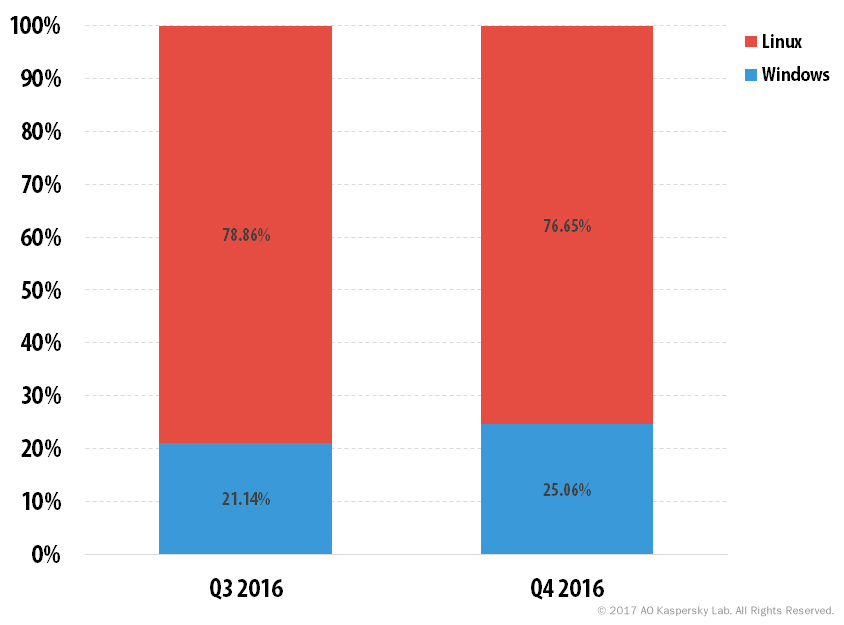
- In Q4 2016, the percentage of attacks launched from Linux botnets decreased slightly and accounted for 76.7% of all detected attacks.
Geography of attacks
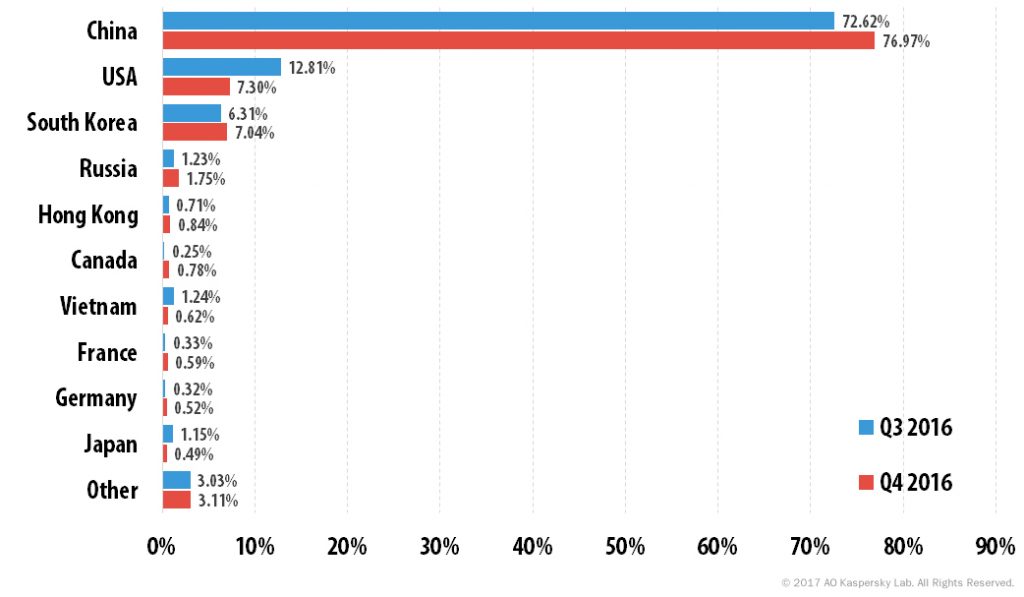
In Q4 2016, the geography of DDoS attacks expanded to 80 countries, with China accounting for 76.97% (4.4 p.p. more than the previous quarter). The US (7.3%) and South Korea (7%) were once again second and third respectively.
The Top 10 most targeted countries accounted for 96.9% of all attacks. Canada (0.8%) appeared in the rating, replacing Italy. Russia (1.75%) moved from fifth to fourth thanks to a 0.6 p.p. decline in Vietnam’s share.
Distribution of DDoS attacks by country, Q3 2016 vs. Q4 2016
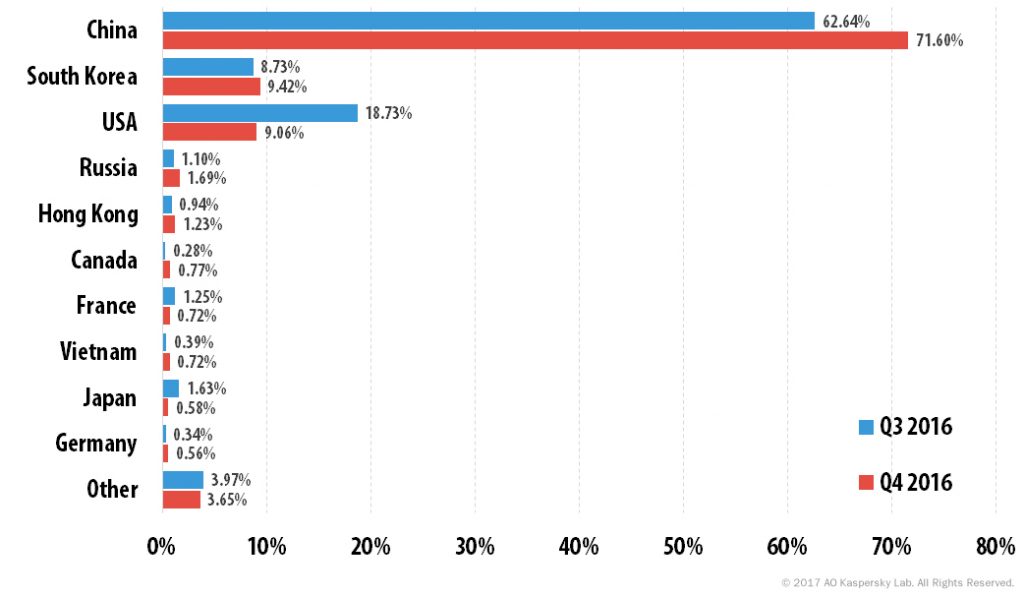
Statistics for the fourth quarter show that the 10 most targeted countries accounted for 96.3% of all DDoS attacks.
Distribution of unique DDoS attack targets by country, Q3 2016 vs. Q4 2016
71.6% of attacks targeted resources located in China, which was 9 p.p. more than the previous quarter. There was a small increase in the number of targets in South Korea (+0.7 p.p.). The US rounded off the top three, even though its share decreased by 9.7 p.p. (9% vs.18.7% in Q3).
The shares of the other countries in the Top 10 remained almost unchanged, with the exception of Japan which saw a fall of 1 p.p. Italy and the Netherlands left the rating and were replaced by Germany (0.56%) and Canada (0.77%).
Changes in DDoS attack numbers
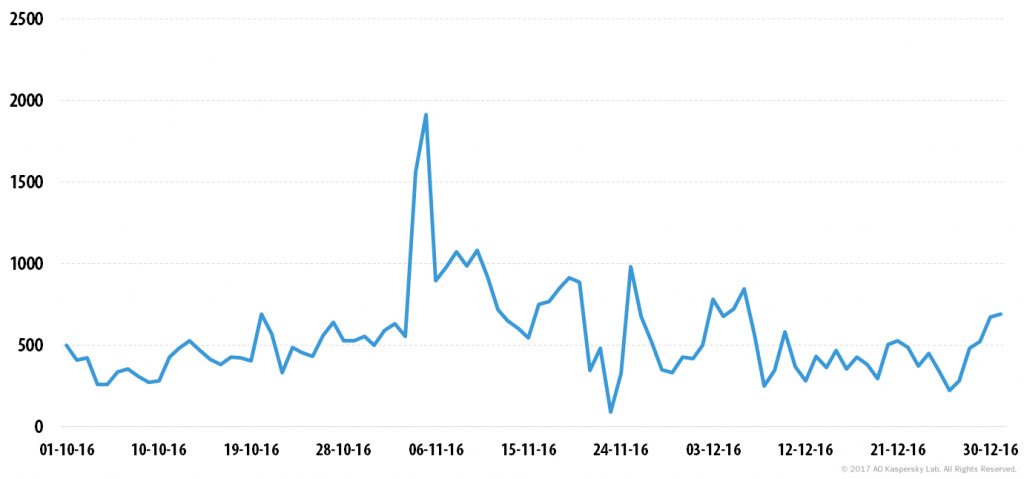
The distribution of DDoS activity was relatively even throughout Q4, with the exception of a sharp peak registered on 5 November when the largest number of attacks in 2016 – 1,915 – was recorded. The quietest day of Q4 was 23 November (90 attacks). However, by 25 November cybercriminal activity had increased to 981 attacks.
Number of DDoS attacks over time* in Q4 2016
*DDoS attacks may last for several days. In this timeline, the same attack may be counted several times, i.e. one time for each day of its duration.
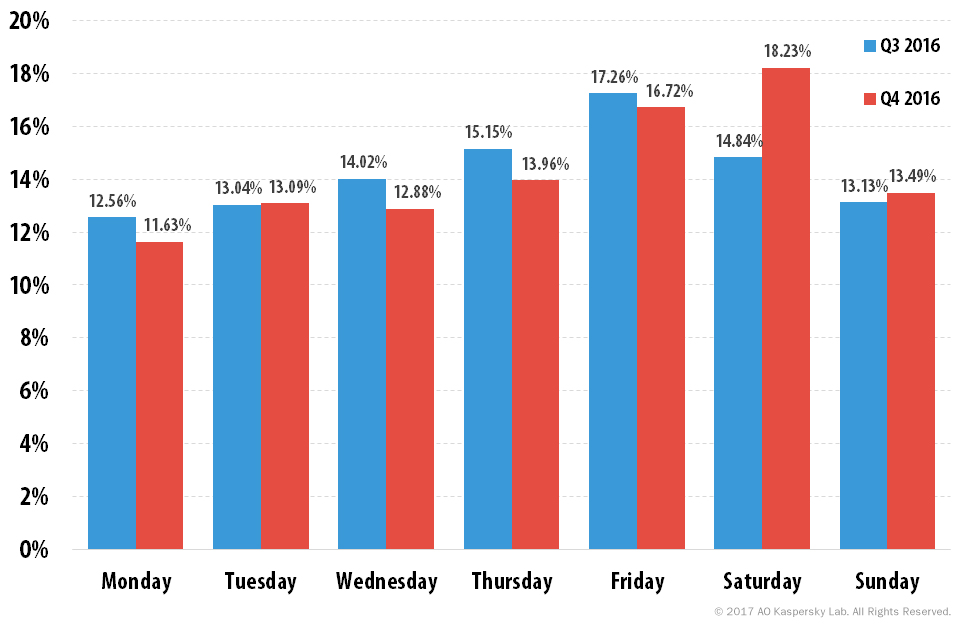
Saturday was the busiest day of the week in Q4 for DDoS attacks (18.2% of attacks), followed by Friday 1.7 p.p. behind. Monday became the quietest day of the week for DDoS attacks (11.6%).
Distribution of DDoS attack numbers by day of the week, Q3 and Q4 2016
Types and duration of DDoS attacks
The SYN DDoS method remained the most popular: its share accounted for 75.3% of attacks, although this figure is 5.7 p.p. less than in the previous quarter. The figures for other attack types increased slightly – TCP DDoS (from 8.2% to 10.7%) and ICMP DDoS (from 1.7% to 2.2%). UDP’s contribution remained almost unchanged.
Distribution of DDoS attacks by type, Q3 and Q4 2016
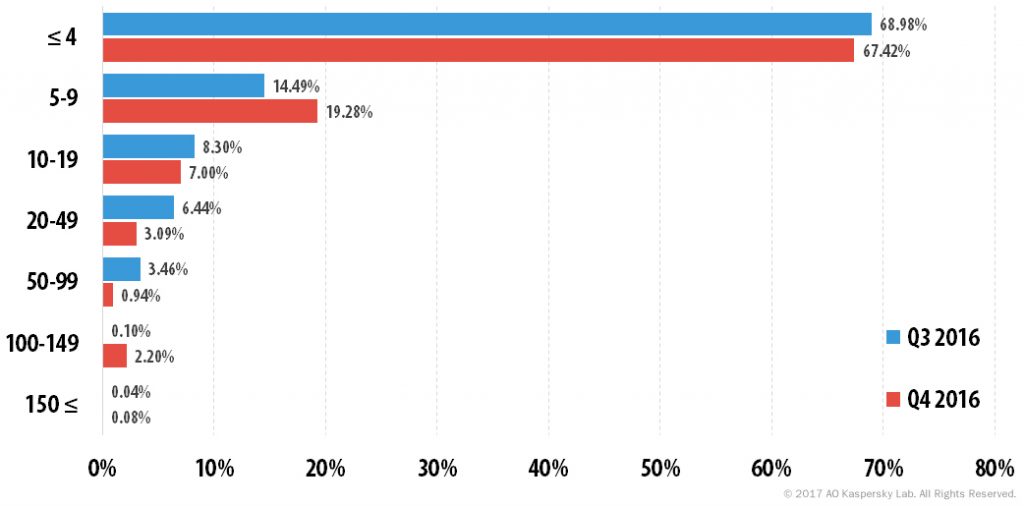
Distribution of DDoS attacks by duration (hours) in Q4 2016 was distinctly uneven. While the share of attacks that lasted no more than four hours remained almost the same as the previous quarter (it decreased by just 1.56 p.p.), the figures for the other time periods changed significantly.
The share of attacks that lasted 5-9 hours increased from 14.49% to 19.28%. Attacks lasting 10-19 hours fell by 1.3 p.p., while the proportion of attacks that lasted 20-49 hours fell by even more – minus 3.35 p.p. The percentage of even longer attacks decreased considerably – the share of attacks lasting 50–99 hours accounted for 0.94%, compared to 3.46% in the previous quarter. The share of attacks that lasted 100-150 hours grew and reached 2.2%, which meant that Q4 saw twice as many of these attacks than those lasting 50-99 hours. There were very few cases of attacks lasting longer than 150 hours.
The longest DDoS attack in the fourth quarter lasted for 292 hours, 8 hours longer than the Q3 maximum. This was also the longest attack of 2016.
Distribution of DDoS attacks by duration (hours), Q3 and Q4 2016
C&C servers and botnet types
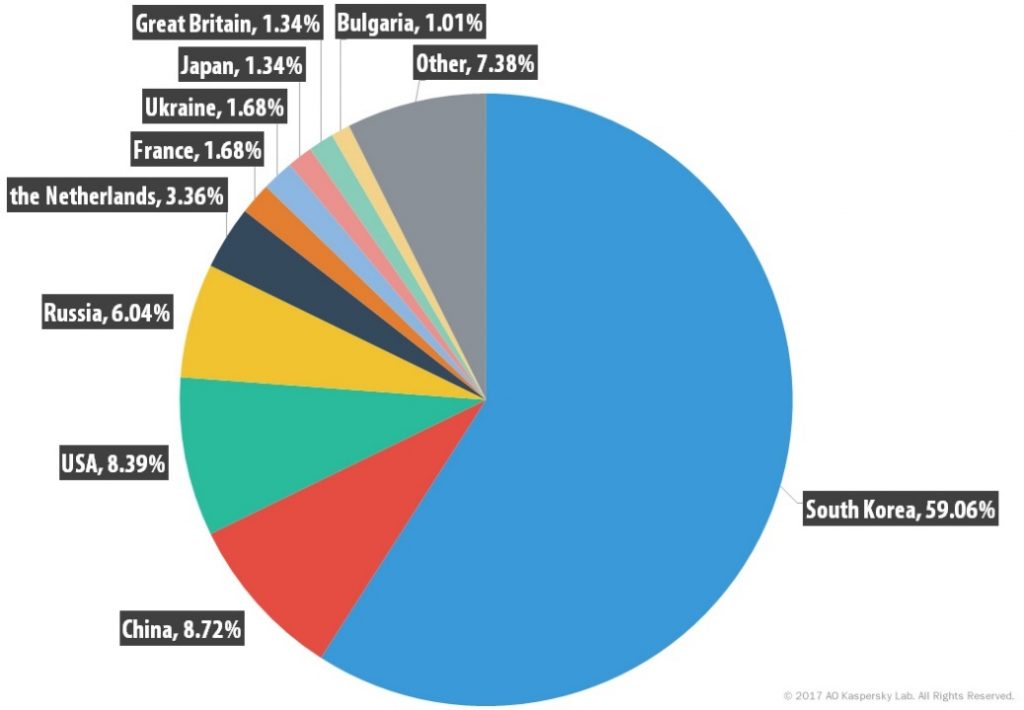
In Q4, the highest number of C&C servers (59.06%) was detected in South Korea. Although the country’s contribution increased by 13.3 p.p. from the previous quarter, it is much less than in Q2 2016 (69.6%). The top three countries hosting the most C&C servers remained unchanged – South Korea, China (8.72%) and the US (8.39%). Their total share accounted for 76.1%, which is an increase of 8.4 p.p. compared to Q3.
In the fourth quarter, three Western European countries – the Netherlands (7.4%), the UK (1.3%), and France (1.7%) – remained in the Top 10 after entering it back in Q3. Among the newcomers to the C&C rating were Bulgaria (6%) and Japan (1.3%).
Distribution of botnet C&C servers by country in Q4 2016
When it came to the distribution of operating systems in Q4, Linux-based DDoS bots remained the clear leader, although their share decreased by 2.2 p.p., accounting for 76.7%. This correlates with the decline in popularity of SYN DDoS for which Linux bots are the most appropriate tool.
The growing popularity of IoT devices used for DDoS attacks suggests that in 2017 the balance will shift further towards Linux, since most Internet-connected devices are based on this operating system.
Correlation between attacks launched from Windows and Linux botnets, Q3 and Q4 2016
The majority of attacks – 99.7% – were carried out by bots belonging to a single family. Cybercriminals launched attacks using bots from two different families in just 0.3% of cases.
Conclusions and forecasts
We expect the share of amplification-type attacks in 2017 to continue to decrease, especially the most popular types (DNS, NTP). However, considering the simplicity and low organizational costs, the technique may be used in some less popular protocols suitable for amplification (RIP, SSDP, LDAP and so on), though it is unlikely that such attacks will be very effective.
The number and complexity of attacks on applications will continue to grow. Considering the renewed interest in this type of attack among cybercriminals and the stagnation in this segment over the last few years, we can assume that older botnets will gradually fall out of use and something new will appear, for example, botnets capable of more sophisticated attacks. The trend for encryption in attacks on applications will remain.
WordPress Pingback attacks will remain popular. Although in the newer versions of the WordPress CMS the vulnerability used for organizing such attacks (namely, the default Pingback function in older CMS versions) has long since been patched by the developers, there are still many vulnerable hosts on the Internet. Of course, their number will decline over time, reducing the number and power of WordPress Pingback attacks. But the relative simplicity and low cost of organizing such attacks, as well as the possibility of using encryption, makes WordPress Pingback-type attacks attractive to unpretentious cybercriminals.
Botnets based on IoT devices will continue to grow. This is largely due to both the novelty of the IoT concept in general and exploitation of IoT devices by cybercriminals. We can assume that in the fourth quarter of 2016 we only saw the emergence of this new market segment, and in 2017 it will continue to grow and develop. The potential growth is difficult to estimate: until now IoT-device manufacturers were not particularly concerned about protecting their products. Even if we assume that all new IoT devices entering the market are perfectly protected from malicious attacks (which in itself is quite doubtful), the current volume of vulnerable IoT devices with Internet access is considerable. Just a few months after the initial appearance of the concept, attackers were able to demonstrate the use of botnets of unprecedented size and conduct attacks whose power was previously only considered possible in theory. Moreover, these devices have the potential to launch attacks of any complexity – the current trend is attacks on applications, including the use of encryption. Considering the highly effective nature and huge potential of IoT-based attacks, we can predict an increase in the number of such attacks as well as their volume and complexity in 2017.
DDoS attacks in Q4 2016



















Cynthia Wells
This is a interesting Overview.
Michael
Excellent article. Really a problem of various types of attacks on websites fairly relevant. It affects not only the major sites such as the williamhill.com or pokerstars.com.
But smaller and not as a development resource like bet-list.com
Michael
excellent review