Recently, a new Remote Administration Tool has been discovered that started appearing here and there in targeted attacks. This tool is “PlugX”. Researchers have even tracked someone suspected of creating that malware – one of the members of the Chinese hacking group NCPH, which is allegedly in the service of PLA. Among others, this group has been accused of attacking high-profile US organizations.
But PlugX has been detected in targeted attacks not only against military, government or political organizations, but also against more or less ordinary companies. And this is quite a strange situation. No matter whether penetrators have been hired or they work for themselves, if they tend to attack “serious” organizations/persons how come we’ve also seen very different types of targets – absolutely peaceful companies – hit by the same group? We could not locate any site where this tool (or rather its kit or builder) has been offered for use, so we can’t confirm that PlugX has been shared between cybercriminal communities or other potential attackers (although we can’t deny that possibility).
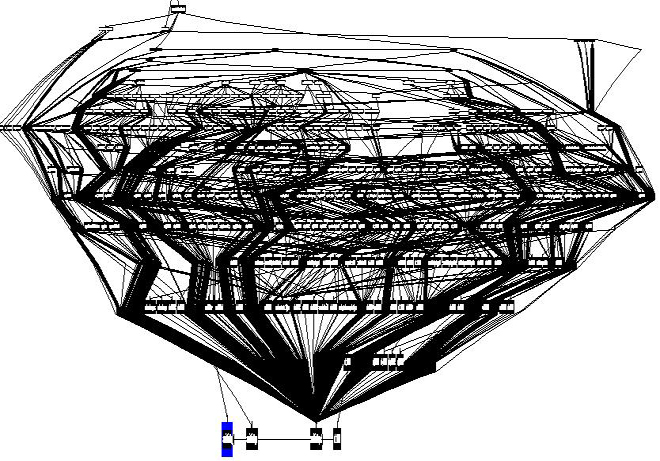
On our side we have detected attacks using this infamous tool against a company which is far from military, politics, critical infrastructure and so on. This company has been bombarded for a month with spear-phishing emails with attachments containing exactly this PlugX program. The first samples were of the same type that had been already described, i.e. some sort of debug version with plenty of logging of potential errors in a bug.log file. But several days ago attackers sent a bunch of emails with a new version of PlugX. This version differs from the previous one in terms of logging activity. The virus writer has removed almost all the lines of code for processing potential errors that were present in the old version. The following awful picture represents where the logging function has been invoked in the old version of PlugX code:
IDA calls graph of logging function: old versionAnd this is what left:
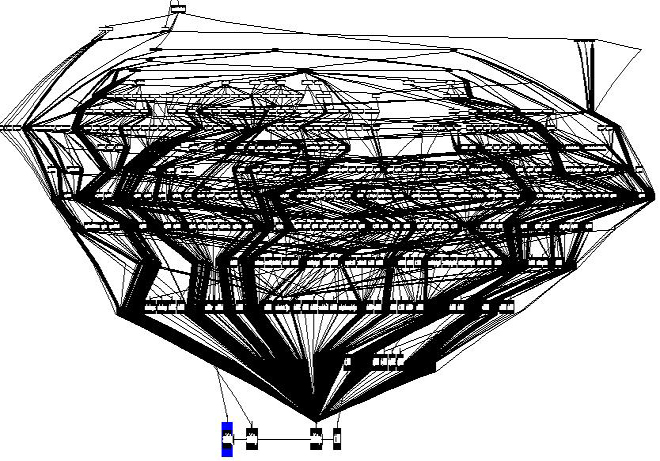
IDA calls graph of logging function: new versionThe nature of the changes shows that where previously the author was not sure that execution would proceed without errors, now he already trusts that the code flow runs successfully:
 |
|
| Old variant | New variant |
 |
|
| Old variant | New variant |
So all the strings related to the module’s source code in the form of “.cpp” have disappeared from the binaries. And the text referring to the project path, e.g.
“d:workplug4.0(nvsmart)(sxl)shellcodeshellcodeXSetting.h”, has been removed as well.
Earlier a part of the PlugX code spotted in previous samples specifies in some way that the program is a ‘demo’ version. Interestingly, this code is still there in the new version. But this means nothing: PlugX samples found ITW are not that ‘demonstrative’ even if this part of the code ‘claims’ so: they are malicious, fully-functional and highly offensive Remote Administration Tools.
We conclude that the PlugX project is a work in progress. And, this progress has just reached a milestone. Although the attackers did not hesitate to use the debug version in previous targeted campaigns, the debug version is now complete and a major version production release is being circulated. Also, we can assume that the attackers have been successfully infecting victims, adequately testing the new version of their tool to enable a move forward in development. But to tell the truth, we are not looking forward to another follow-up version.




















PlugX is Becoming Mature