
Promises to marry a potential groom if he covers his bride-to-be’s travel expenses to his hometown are a fairly common feature of fraudulent spam. Less common are more ‘noble’ offers of help, though even these charitable offers usually come at a price.
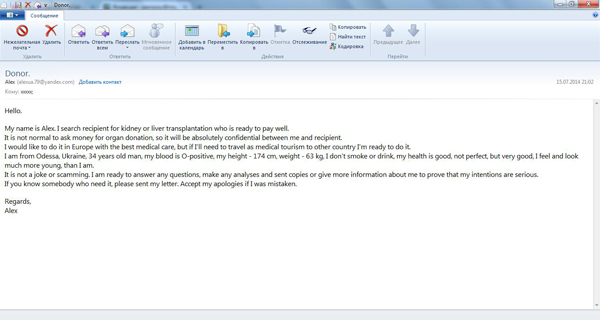
In a recent mailing, a resident from the Ukrainian city of Odessa expressed his wish to become an organ donor, but for a considerable fee. In the email, he provided an overview of his current state of health – “good, not perfect” – his biometric data (height – 1.74 m, weight – 63 kg) and even his blood type. The price for which he was willing to sell a kidney or his liver was not specified; the main condition was that the operation had to be done in a European clinic.
It is obvious that anyone who decides to take him up on his offer will have to pay a considerable sum of money. It is highly likely that our “man from Odessa” will also want money to pay for his trip to Europe or to carry out tests in a good laboratory, before disappearing once he receives a money transfer. Honesty and offers made in spam are just incompatible. Moreover, no one should ever enter into negotiations with people who send unsolicited emails, especially when it concerns health issues.



















Organ donation: home delivery