
I think I speak for just about the entire security industry when I say that I really value the work of the people who help out on security forums.
These people put in a lot of hard work and effectively it’s all voluntary.
Some of these people create tools to remove certain malware families/types, and these tools will be very popular within the communities that they belong too.
Recently the tools created by members of one community have proved so popular that someone decided to copy them. Most of these tools are scripts, which means that they can very easily be edited. Normally editing is done to update the scripts so that they can detect new malware. Sadly, in this case someone has basically copied the scripts and put his own name to them.
This copying and taking credit for other people’s work has been going on for quite a while now. Normally ignoring such people is the best course of action, so as not give them any (more) attention, but I think a line has been overstepped.
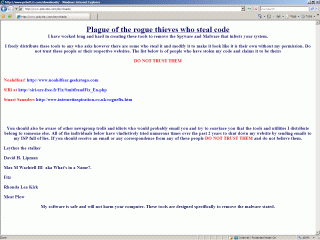
‘Pcbutts1’ is actively promoting ‘his’ anti-malware tools which remove a number of threats. This is what people see when they go to his very recently updated downloads page.
The people listed on this page are well respected within the security community and a number of them are actually Microsoft MVPs. It’s ‘pcbutts1’ who is the fraud, not them.
Let’s hope ‘pcbutts1’ grows up – and fast.



















No good deed goes unpunished