
In late 2016, the Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT) reported on phishing attacks that were primarily targeting industrial companies from the metallurgy, electric power, construction, engineering and other sectors. As further research demonstrated, this was just part of a bigger story that began much earlier and is unlikely to end any time soon.
Targeted Attack
In October 2016, Kaspersky Lab products detected a surge in malware infection attempts on the computers of our customers who had industrial control systems installed. The malware used in these attacks was a specific modification of an exploit for a vulnerability dating back to 2015.
Further analysis of the incident led us to phishing messages disguised as business correspondence that were used to distribute the exploit.
Phishers have long since discovered the advantages of attacking companies (they obviously have much more money in their accounts than ordinary users and they usually conduct much larger transactions than individuals). The emails used in such attacks are made to look as legitimate as possible so that the employees who receive them open the accompanying malicious attachments without giving them much thought.
In this case, we were dealing with well crafted phishing messages that targeted not only commercial organizations but, in most cases, industrial enterprises. All in all, we discovered over 500 attacked companies in more than 50 countries. Most of these companies are industrial enterprises and large transportation and logistics corporations.
The Emails
The emails were sent on behalf of various companies that did business with potential victims: suppliers, customers, commercial organizations and delivery services. The emails asked recipients to check information in an invoice as soon as possible, clarify product pricing or receive goods specified in the delivery note attached.
Examples of phishing emails
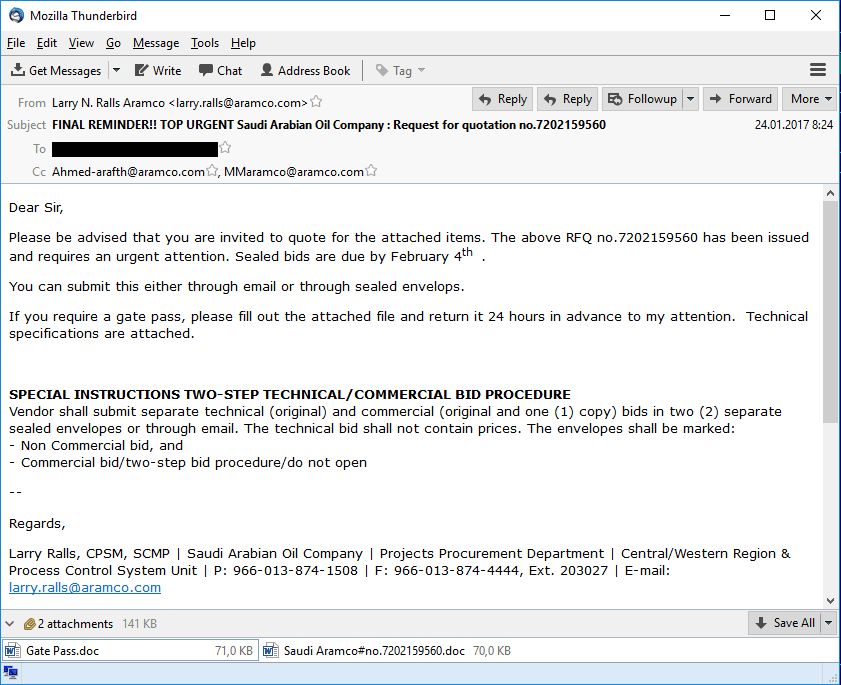
The phishers clearly tried hard to make their fake messages look very convincing to the employees of targeted companies. We have seen attachments with names such as “Energy & Industrial Solutions W.L.L_pdf”, “Woodeck Specifications best Prices Quote.uue” and “Saudi Aramco Quotation Request for October 2016”.
Malicious Files
All the emails had malicious attachments: RTF files with an exploit for the CVE-2015-1641 vulnerability, archives of different formats containing malicious executable files, as well as documents with macros and OLE objects designed to download malicious executable files.
In late 2016, our mail antivirus solutions detected between several hundred and several thousand emails per day containing given exploit for CVE-2015-1641.
Number of daily mail antivirus detections
of the exploit for CVE-2015-1641 (Exploit.MSWord.Agent.hp)
A characteristic feature of such phishing campaigns is that the number of emails sent varies depending on the day of the week: fewer emails are sent on weekends than weekdays.
The malware used in these attacks belonged to families that are popular among cybercriminals, such as ZeuS, Pony/FareIT, LokiBot, Luminosity RAT, NetWire RAT, HawkEye, ISR Stealer, and iSpy keylogger. The phishers selected a toolset that included the functionality they needed, choosing from malware available on cybercriminal forums. At the same time, the malware was packed using VB and .NET packers – a distinct feature of this campaign. To evade detection by security tools, the malicious files were regularly repacked using new modifications of the same packers.
The attackers used malware belonging to at least eight different Trojan-Spy and Backdoor families. All malicious programs selected for these attacks are designed primarily to steal confidential data and install stealthy remote administration tools on infected systems.
Domains Used by the Attackers
When we extracted C&C addresses from the detected malicious files, it turned out that in some cases the same resources were used as command-and-control servers for malware from different families. From this, it can be concluded that either there is one cybercriminal group behind these attacks, using different malware families, or different groups are cooperating closely with each other and using the same C&C to communicate to “their” malware.
The domain names of some of the malware command-and-control servers used by the attackers mimicked domain names used by industrial companies – more proof that the attacks were primarily targeting industrial companies.
An analysis of these domain names sheds light on the tactics used by the phishers. They try to register the same domain name as the targeted company’s legitimate resource, but in a different top-level domain. If this is impossible, the attackers register a domain with a name that looks very similar to the legitimate domain’s name (a standard technique is to replace one or more characters). We have also seen another technique used in these attacks: the domain name is made up of the legitimate site’s name and the name of its top-level domain.
| Malware CnC | Real industrial company site |
| hi***quil-ar.com | hi***quil.com.ar |
| em***uae.com | em***u.ae |
| lus***lt.com | lus***lt.pt |
Phishing domain names mimicking legitimate domain names
In some cases, the attackers gained unauthorized access to the legitimate websites of industrial companies and used them as a platform for hosting malware and C&C servers. The websites were accessed using credentials stolen earlier from infected computers used by the companies’ employees.
Compromised legitimate site
In the course of our investigation we found that, according to the publicly available information provided by Whois services, most domains used for malware C&C servers were registered to residents of Nigeria. All indications are that these were business email compromise (BEC) attacks that have come to be associated with Nigerian cybercriminals.
Attack Scenario
Business email compromise attacks are well-known. Several scenarios for these attacks have been described to date. Some of these scenarios were used in the targeted attacks we have been investigating.
Attack outline
In the first stage, phishers send emails with malicious attachments – Trojan-Spies or Backdoors. All malware used is available on the black market. It is worth noting that a complete set of malware for carrying out this type of attack usually costs no more than US$200.
Among other things, we have discovered messages sent using compromised email accounts of company employees, in which cybercriminals sent malicious attachments to corporate addresses at other companies.
After infecting a corporate computer, the attackers are able to make screenshots of the correspondence using malware or set up hidden redirection of messages from the attacked computer’s mailbox to their own mailbox. This enables them to track which transactions are being prepared in the company.
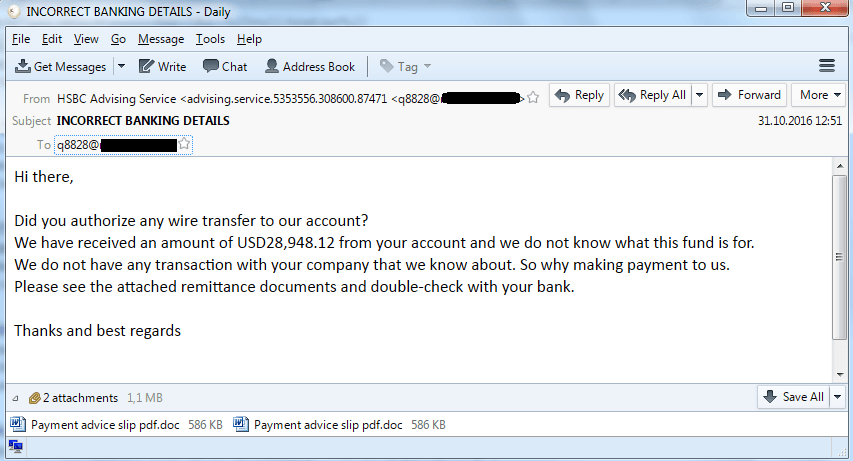
After selecting the most promising transaction among those in the pipeline, the attackers register domain names that are very similar to the names of the seller companies. Using the newly registered domains, the cybercriminals are able to carry out a man-in-the-middle attack: they intercept the email with the seller’s invoice and forward it to the buyer after replacing the seller’s account details with the details of an account belonging to the attackers. Alternatively, they can send a request on behalf of the seller for an urgent change of bank details in addition to the seller’s legitimate email containing the invoice.
Hijacking the correspondence between the seller and the buyer using a phishing email address
Another option for the cybercriminals is to send the emails on behalf of a seller with spoofed email header in such a way that it points to the seller’s legitimate mailbox as a sender. It’s worth saying that this way of sending emails is less reliable as some programs and mail servers can reveal the replacement.
In any event the chances of the recipient never suspecting anything and the criminals getting the money are very high.
Nigerian Fishing
‘Nigerian letters’ (a.k.a. 419 scams) have become classics of online fraud. The creators of fascinating stories about heiresses/widows/secretaries/lawyers of deceased millionaires/disgraced dictators/other fat cats didn’t win the Ig Nobel Prize for literature in 2005 for nothing. They may not be very highly qualified, but they certainly have a talent for extortion, and may well have been profiting from the greed and gullibility of their victims for years.
Several years ago, Nigerian phishers appeared on the radar of researchers. They were the same scammers who specialized in so-called Nigerian letters, but at the same time they were mastering new techniques for stealing money – this time, from companies. They are usually the ones behind business email compromise attacks.
There have been a good many publications on phishing attacks by Nigerian fraudsters in the past three years. This is no coincidence: this relatively new type of criminal business is gaining momentum. According to FBI estimates, the damage from Nigerian phisher activity from October 2013 to May 2016 exceeded US$3 billion and the number of affected companies was as high as 22,143. Those companies are scattered across 79 countries of the world.
In 2013-2015, mostly small and medium-size companies were attacked. The phishers gathered the email addresses of potential victims on the Internet.
Cybercriminals exchanging addresses for phishing email distribution. Most addresses are on publicly available email services
Since the fraudsters are interested primarily in companies that buy and sell, they use resources such as Alibaba.
Message with spoofed header and replaced banking details allegedly sent from Alibaba seller’s legitimate email
Phishers also buy databases of email addresses that are of interest to them. Addresses belonging to different categories of company are available on the black market. Relatively small industrial companies are among those targeted by phishers.
An offer to buy categorized email addresses sent to a Nigerian phisher
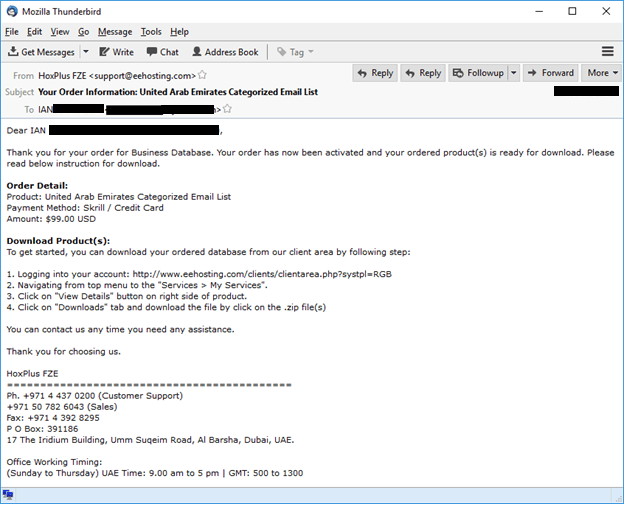
Clearly, targeted attacks focusing on specific regions already took place in 2015. The screenshot below shows a message that confirms the purchase of a database of UAE company addresses by a Nigerian phisher. This purchase set the cybercriminal back $99.
Purchase of an email address database for attacks on UAE companies by a Nigerian phisher
Some cybercriminals are prepared to pay a small fortune for email addresses:
Purchase of corporate data by a Nigerian phisher for $995
Hunting the Big Phish
Cybercriminals want to steal as much money as possible in one go. As a result, the companies attacked in 2016 included some major corporations.
The average value of a sales transaction can be quite high for a large company. Apparently, Nigerian hackers took note of this in 2016. We believe that a group of Nigerian phishers (or several groups working together) chose industrial and transportation companies as their main targets in 2016.
For example, Palo Alto Networks published two reports in June 2015 and February 2016 based on their analysis of phishing attacks against companies. These reports painted a familiar picture: Nigerian attackers targeted phishing emails and malware that steals confidential data – a Trojan-Spy called KeyBase was used in those attacks. Remarkably, unlike the 2015 attack, the 2016 attack targeted primarily industrial companies.
In August 2016, our colleague studied a series of phishing attacks that he dubbed Operation Ghoul. Operation Ghoul also made use of targeted phishing emails that contained malware designed to steal authentication credentials from different applications, including KeyBase. That operation in fact had much in common with the targeted attacks that we detected in the fall of 2016. In both cases, the attacks targeted mostly industrial companies and the texts of phishing emails and attached files were very similar. We also noticed fake emails sent in both campaigns on behalf of the same sender – Emirates NDB Bank. Finally, in the Operation Ghoul attacks we found files packed with a specific .NET packer (sold on hacker forums as Data Protector) that was one of the markers of the attacks we uncovered.
In the attacks analyzed by Kaspersky Lab, industrial companies account for over 80% of potential victims.
Potential Losses
Nigerian phishing attacks are particularly dangerous for industrial companies. In the event of a successful attack, the company making a purchase not only loses money but also fails to receive the goods they need on time. This can be critical for industrial companies: if the goods are raw materials used in manufacturing or spare parts needed to repair equipment, their non-delivery can result in downtime or failure to perform scheduled maintenance or commissioning and start-up work.
However, there are other possible consequences, as well. The spyware programs used by phishers send a variety of information from infected machines to their command-and-control servers.
We analyzed data from some command-and-control servers used in 2017 attacks. The amount and contents of data obtained by Nigerian phishers is truly disturbing. Cybercriminals have gained access to information on industrial companies’ operations and main assets, including information on contracts and projects.
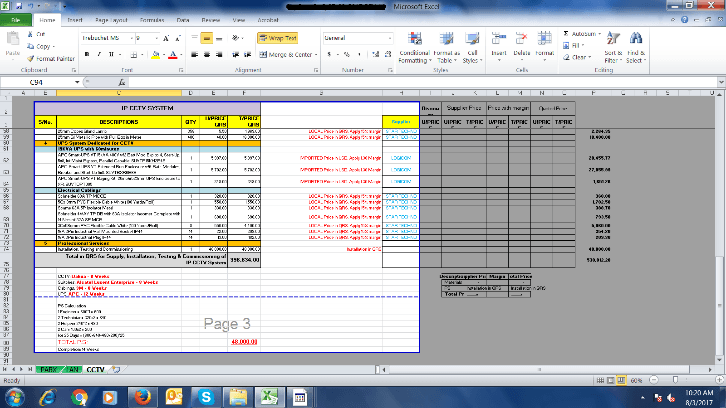
For example, screenshots found on malware command-and-control servers included various cost estimates and project plans for some of the current projects at victim enterprises.
 |
 |
Screenshots from infected computers
We also found screenshots that were clearly not made on the computers of project managers or procurement managers, but rather on the workstations of operators, engineers, designers and architects. They show, among other things, technical drawings, floor plans, diagrams showing the structure of electrical and information networks.
 |
 |
 |
 |
 |
|
Screenshots from infected computers
Clearly, this is not needed to carry out the cybercriminals’ Nigerian scams. What do they do with this information? Do they destroy it after completing an attack? Could someone order the theft of data from a specific company?
So far, we have not seen any of the information stolen by Nigerian cybercriminals on the black market. However, it is clear that, for the companies being attacked, in addition to the direct financial loss a Nigerian phishing attack poses other, possibly more serious, threats.
This malicious phishing campaign is ongoing and is unlikely to cease in the foreseeable future.
Phishing attacks agains industrial companies continue
Nigerian phishing is clearly a profitable type of cybercrime that does not require significant financial investment or a high level of technical knowledge. It appears that Nigerian threat actors don’t face stiff competition, at least for now: they readily share information as well as command-and-control servers used by malware. However, as in the case of Nigerian letter scams, this type of cybercriminal activity, can easily be adopted by other criminals. That is if they haven’t already done so, of course.
P.S. The Hidden Threat
And last – though by no means least – it is very dangerous if as a result of an infection cybercriminals gain access to computers that are part of an industrial control system (ICS). In such cases, they can gain remote access to the ICS and unauthorized control over industrial processes.
Remote access to SCADA machines enables attackers to simply switch industrial equipment off or change its settings. There are known cases of hackers changing the parameters of an industrial process without any obvious malicious intent – simply out of curiosity. In 2016, Verizon published data breach digest describes several attacks investigated by the company, including one aimed at the systems of an unnamed US water utility. In the course of the attack, the cybercriminals managed to infiltrate the control system and change the amounts of chemicals used to treat tap water and the flow rate. At the same time, according to Verizon experts, the hackers didn’t understand what the results of the changes they were making would be and changed the settings randomly. In this context, it has to be hoped that the interests of Nigerian phishers will be limited to stealing money and that they won’t tamper with ICS controls.
Unfortunately, there is no guarantee that people who want to carry out acts of sabotage will not gain access to computers in industrial enterprises, including SCADA systems.
Protection Measures
The following measures are needed to mitigate attacks which involve social engineering techniques:
- Regularly brief employees on security rules when working with email and the Internet. Train employees in the basic rules of cyber-hygiene, such as not opening suspicious links and attachments, carefully checking sender and recipient addresses, company names and the actual domain names from which messages were sent.
- Inform employees not only about the tools that can be used by cybercriminals, but also about the fraudulent schemes they use.
- In the course of conducting a transaction, if an unexpected request is received from the seller to change the bank details, payment methods or other parameters of the transaction, it is best to contact the seller by phone or using other methods unrelated to email and ask for confirmation of the changes.
The following protection measures are recommended to minimize the risk of infection and any damage from attacks:
- Install a security solution on all workstations and servers where possible.
- Keep security software, signature databases, heuristic and decision rule databases up to date.
- Where possible, install operating system and software updates without delay.
- In the event of a system being compromised, change the passwords for all accounts used on that system.
- Promptly send suspicious emails, attachments and domain names for analysis to highly qualified experts, such as Kaspersky Lab ICS CERT experts.
On industrial information systems, whose composition and configuration cannot be changed quickly, the greatest effect can be achieved by using application startup control and device control technologies in allowlisting mode in combination with application behavior control technologies and protection against network attacks. We also recommend the following measures:
- Install tools that provide passive monitoring of network activity on the industrial network, capable of detecting newly connected devices, suspicious network connections, and malware network communication. These tools will help to detect and monitor attempts by threat actors to penetrate the enterprise’s network. Importantly, some of these tools are very easy to install and do not require the composition or configuration of the industrial control systems to be changed in any way.
- Install tools that provide deep analysis of network traffic on the industrial network and detection of commands that can potentially disrupt the industrial process. Using this class of system is absolutely necessary for the detection and timely prevention of advanced attacks designed to physically damage an enterprise’s systems and carried out by highly qualified external or internal threat actors. This type of technology can also be implemented passively, without any impact on the operation of industrial control systems.
- Minimize the range and quantity of software products used in ICS segments.
- Restrict the use of computers that are part of an ICS for purposes unrelated to the industrial processes. These measures can be implemented using application startup control tools included in endpoint security solutions.
High-quality and properly configured security solutions help to protect an enterprise against the vast majority of chance infections and many targeted attacks, especially those carried out using tools that are not particularly sophisticated.
Nigerian phishing: Industrial companies under attack
































ar
Very Good One.. Any known indicators?
Jorge Saenz
I gotta give it to you guys, this is a really neat article. Very concise. Do you have one in which you somehow quantify in detail the loss, in terms of money, for certain vulnerabilities or attacks? If not, you could use one, to complement this.