
Today we’ve seen a new variant of Net-Worm.JS.Twettir going around on Twitter. Kaspersky products detect it as Net-Worm.JS.Twettir.h.
This worm appeared right after an announcement that a security firm has hired the author of the original worm. Not wanting to stray too much from the intended topic of this blog post I’ll only say that we feel very strongly that this is an extremely bad move.
This new variant selects a message to tweet from a pool of choices. Some of them reference big twitter names, others simply talking about “Mikeyy”, the original author.
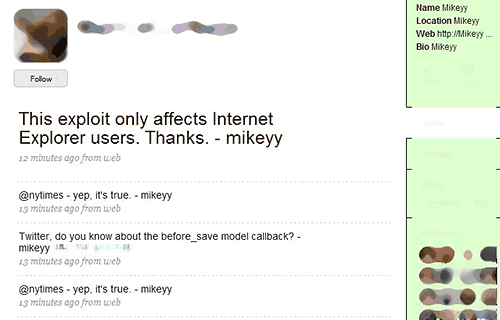
One of the messages also asserts that this XSS vulnerability only affects Internet Explorer users. At the time of writing, we can confirm only that the latest version of Firefox (3.0.8) is indeed not vulnerable to this exploit.
What’s interesting about this is that the XSS script is hosted on the same domain as the original worm. That would imply that Mikeyy has been at it yet again. Rather odd for someone who just landed a security job, isn’t it?
On the other hand, there are rumors floating about that “Mikeyy’s” machine along with his passwords is compromised. So it might be someone else after all.
For all of you tweeters out there who love to click on profiles and URL – your best bet is to use the latest version of Firefox with the noscript plugin available at noscript.net. This should provide reasonable protection from new XSS-worms which Twitter may be facing at this point in time.
We’ll keep monitoring the situation and keep you posted.




















New Twitter XSS-Worm going around