
A new year has broken – a new peer-to-peer botnet is on the rise. It shares some commonalities with the infamous Waledac bot that was taken down in a exemplary effort by Microsoft early last year. Although this new bot has a different code base, it uses the same spreading strategy and also seems to maintain a multi-relay (or peer-to-peer) infrastructure just like its predecessor. Our friends over at ShadowServer have posted an excellent blog entry about this new threat and how it relates to earlier bots.
We are currently analyzing the new family and can confirm peer-to-peer-like behavior. When started, the bot loads a list of 20 hard-coded peers. Each entry contains a unique ID, the peer’s IP address and a TCP port it is listening on:
d9d04244-2f07-464c-b5c9-ad78e6319546 69.204.140.0:80
89787e02-6de4-4385-ae5f-5eaca64a3fe0 112.204.169.0:80
…
Every 10 minutes the bot connects to one of these hosts and downloads a list of another 10 peers that is merged into its own one. Each downloaded peer information contains the online time of the corresponding bot:
61410ab9-aa16-441c-84b9-6a8d1257b8da, 202.144.33.227:80 lst_act=03.01.201115:40:23 live_tm: d1.h23.m25.s59
085a9416-1a0b-403f-abb2-88b2600e9c51, 114.249.53.47:80 lst_act=03.01.2011 15:40:02 live_tm: d0.h0.m6.s49
…
The botnet is hosting a fast-flux network that constantly directs 12 domains that are advertised in spam campaigns to one of the infected machines. These machines then serve a copy of the malicious file. We have queried 5 of the domains for a period of 5 hours and counted the number of unique IP addresses we got back per minute (on the y-axis):
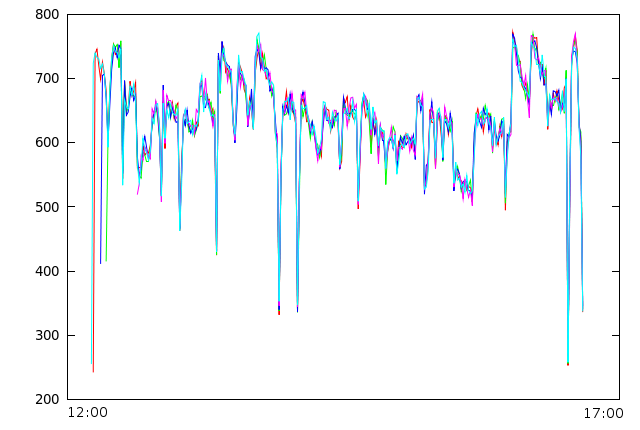
The resulting chart shows that the domains are strongly correlated, telling that the same set of machines is most likely serving all of the domains. The graphs also show the typical tendency to decrease as machines go offline and therefore are not part of the fast-flux collective any more, countered by adding new hosts through the controlling entity
The samples we are currently seeing spreading differ in their checksums but all have a size of 485888 bytes. We detect current versions as a version of Trojan-Downloader.Win32.FraudLoad.




















New P2P Botnet Arising