
On 3 December, we noted a rapid growth in the number of detections for exploits targeting the vulnerability CVE-2011-3544 in Java virtual machine. The vulnerability was published on 18 October, but malicious users have only recently begun to make active use of it. It can be used by exploits in drive-by attacks to download and launch malicious programs.
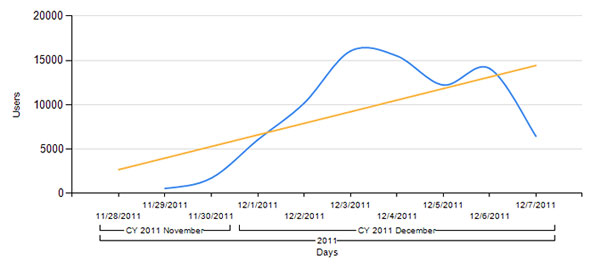
Number of unique detections of Exploit.Java.CVE-2011-3544
According to KSN data, most of the exploits targeting CVE-2011-3544 are used in the BlackHole Exploit Kit, which is currently the most popular exploit pack.
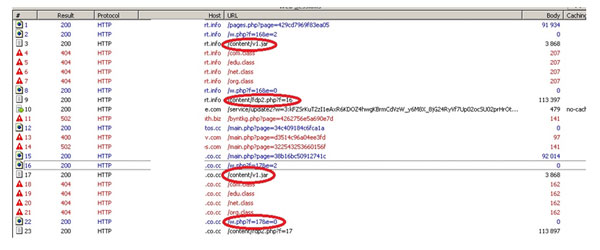
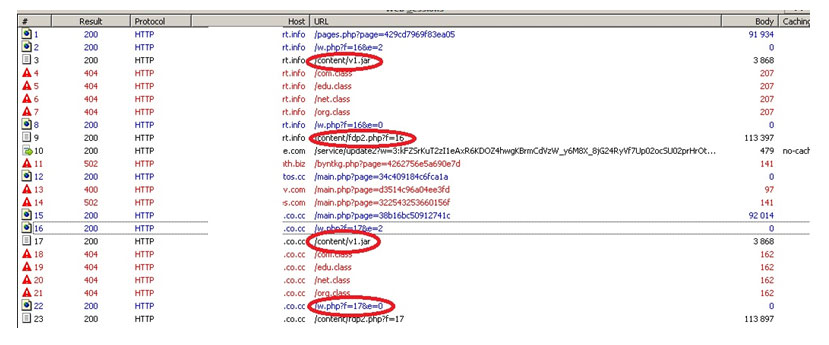
We analyzed the latest BlackHole kits. The sites that carry out drive-by attacks with the help of BlackHole turned up quite an old exploit – a PDF file that targets the vulnerability CVE-2010-0188, and a new Java exploit targeting the vulnerability CVE-2011-3544. The corresponding files are circled in red in the screenshot below.
A screenshot of the list of files intercepted when visiting websites where BlackHole is installed
Brian Krebs reports that the creators of BlackHole have successfully integrated the new exploit into their kit. According to KSN statistics, the new exploits attack users in Russia, the US, the UK and Germany. This appears to be related to the fact that new exploits that are integrated in BlackHole and target the vulnerability CVE-2011-3544, install the Trojan Carberp that steals banking data, as well as SMS blockers. SMS blockers are mostly used in Russia, while Trojan bankers attack users in developed countries.
Once again we see that malware writers are forging ahead and are continually improving their creations. It is, therefore, critical that all users install Java updates from Oracle in a timely manner. The patch for (among other things) the CVE-2011-3544 vulnerability can be downloaded here.




















New Exploit Targeting Java Vulnerability Found in BlackHole Arsenal