
Kaspersky Lab presents its malware rankings for September.
There are relatively few new malicious programs in either ranking. It is, however, worth highlighting a new ‘bundle’: Trojan-Dropper.Win32.Sality.cx which installs Virus.Win32.Sality.bh to an infected computer. The dropper spreads using a vulnerability in WinLNK files (i.e., Windows shortcuts). It’s also worth noting that in September the number of exploits targeting CVE-2010-1885 (the Windows Help and Support Center vulnerability) was significantly lower than in August. Another September trait is that the number of exploits – 7 – in the Top 20 was equal to that of adware programs.
Note that neither ranking includes data for heuristic detections, which currently account for as much as 25 – 30% of all the malware detected. We are planning to provide more detailed data on heuristic detections in the future.
Malicious programs detected on users’ computers
The first Top Twenty ranking shown below lists malware, adware and potentially unwanted programs that were detected and neutralized by the on-access scanner when they were accessed for the first time.
| Position | Change in position | Name | Number of infected computers |
| 1 |  0 0 |
Net-Worm.Win32.Kido.ir | 371564 |
| 2 |  0 0 |
Virus.Win32.Sality.aa | 166100 |
| 3 |  0 0 |
Net-Worm.Win32.Kido.ih | 150399 |
| 4 |  1 1 |
Trojan.JS.Agent.bhr | 95226 |
| 5 |  1 1 |
Exploit.JS.Agent.bab | 81681 |
| 6 |  1 1 |
Worm.Win32.FlyStudio.cu | 80829 |
| 7 |  1 1 |
Virus.Win32.Virut.ce | 76155 |
| 8 |  -4 -4 |
Net-Worm.Win32.Kido.iq | 65730 |
| 9 |  0 0 |
Exploit.Win32.CVE-2010-2568.d | 59562 |
| 10 |  0 0 |
Trojan-Downloader.Win32.VB.eql | 53782 |
| 11 |  new new |
Virus.Win32.Sality.bh | 44614 |
| 12 |  0 0 |
Exploit.Win32.CVE-2010-2568.b | 43665 |
| 13 |  return return |
Worm.Win32.Autoit.xl | 40065 |
| 14 |  -1 -1 |
Worm.Win32.Mabezat.b | 39239 |
| 15 |  new new |
Packed.Win32.Katusha.o | 39051 |
| 16 |  new new |
Trojan-Dropper.Win32.Sality.cx | 38150 |
| 17 |  -3 -3 |
Worm.Win32.VBNA.b | 37236 |
| 18 |  new new |
P2P-Worm.Win32.Palevo.avag | 36503 |
| 19 |  -4 -4 |
AdWare.WinLNK.Agent.a | 32935 |
| 20 |  return return |
Trojan-Downloader.Win32.Geral.cnh | 31997 |
There were four newcomers to the Top Twenty in September. Two other malicious programs returned after a period of absence.
The top ten positions of the ranking remained almost stationary, with only Kido.iq sliding down four positions.
Two exploits, Exploit.Win32.CVE-2010-2568.d (9th position) and Exploit.Win32.CVE-2010-2568.b (12th position), both of which exploit CVE-2010-2568, a vulnerability in Windows shortcuts, have kept their positions. However, the malicious program targeting the vulnerability has changed. In the August ranking this was Trojan-Dropper.Win32.Sality.r, which has now been succeeded by Sality.cx, malware from the same family (16th position). Sality.cx is similar in structure to the .r modification, but installs Sality.bh (11th position) rather than Virus.Win32.Sality.ag, an older modification of the same virus which was installed in August. In other words, exploits targeting CVE-2010-2568 are now being used to distribute a new variant of the Sality polymorphic virus. The Sality.cx dropper includes a URL which contains Russian words. This could mean that the native language of the malware writers who created it is Russian.
![]()
Fragment of Trojan-Dropper.Win32.Sality.cx, which includes a link containing Russian words
The geographical distribution of the new dropper Sality.cx is identical to that of Trojan-Dropper.Win32.Sality.r in August. It is most common, (in terms of number of times this malware has been detected) in India, Vietnam and Russia, in that order. Apparently, the distribution of the dropper is very similar to the distribution of the CVE-2010-2568 exploit, which is shown below.
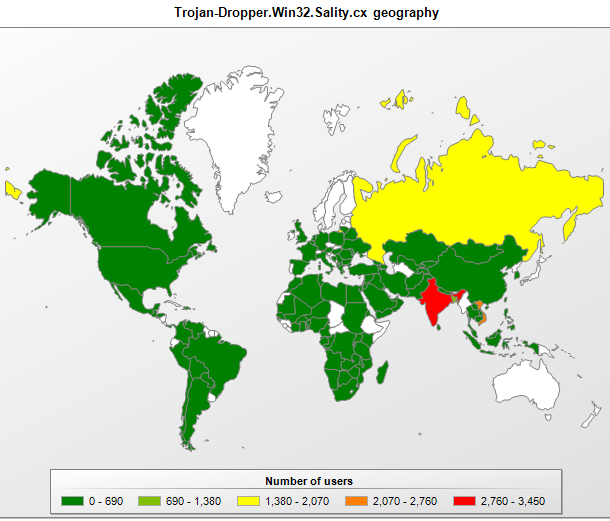
Geographical distribution of Trojan-Dropper.Win32.Sality.cx
A new malicious packer appeared in the ranking in September – Packed.Win32.Katusha.o (15th position). We have seen other members of the Katusha family in our previous rankings, but malware writers are actively working on modifying the packer to prevent it from being detected by antivirus software. Another packer, Worm.Win32.VBNA.b (17th position), has lost some ground but has nevertheless remained in September’s Top Twenty.
Starting in May, a new modification of P2P-Worm.Win32.Palevo has made an appearance in every ranking. The worm spreads mostly via peer-to-peer networks. September’s modification goes under the name Palevo.avag (18th position). Two malicious programs – Worm.Win32.AutoIt.xl (13th position) and Trojan-Downloader.Win32.Geral.cnh (20th position) – have returned to the Top 20. They last appeared in the ranking in July and May respectively. Two other programs that we have seen in previous rankings – Worm.Win32.Mabezat.b (14th position) and AdWare.WinLNK.Agent.a (19th position) – have lost a little ground.
Malicious programs on the Internet
The second Top Twenty list below shows data generated by the web antivirus component and reflects the online threat landscape. This table includes malware and potentially unwanted programs which are detected on web pages or downloaded to victim machines from web pages.
| Position | Change in position | Name | Number of attempted downloads |
| 1 |  1 1 |
Exploit.JS.Agent.bab | 127123 |
| 2 |  -1 -1 |
Trojan-Downloader.Java.Agent.ft | 122752 |
| 3 |  14 14 |
Exploit.HTML.CVE-2010-1885.d | 75422 |
| 4 |  3 3 |
AdWare.Win32.FunWeb.di | 61515 |
| 5 |  0 0 |
AdWare.Win32.FunWeb.ds | 56754 |
| 6 |  -2 -2 |
Trojan.JS.Agent.bhr | 51398 |
| 7 |  new new |
Exploit.SWF.Agent.du | 43076 |
| 8 |  3 3 |
Trojan-Downloader.VBS.Agent.zs | 42021 |
| 9 |  new new |
AdWare.Win32.FunWeb.ge | 41986 |
| 10 |  9 9 |
AdWare.Win32.FunWeb.fb | 37992 |
| 11 |  -1 -1 |
Exploit.Java.CVE-2010-0886.a | 37707 |
| 12 |  new new |
Trojan-Downloader.Java.Agent.gr | 36726 |
| 13 |  -5 -5 |
AdWare.Win32.FunWeb.q | 31886 |
| 14 |  2 2 |
Exploit.JS.Pdfka.cop | 29025 |
| 15 |  3 3 |
Exploit.JS.CVE-2010-0806.b | 28366 |
| 16 |  -2 -2 |
AdWare.Win32.FunWeb.ci | 26254 |
| 17 |  new new |
Trojan-Downloader.Java.OpenStream.ap | 21592 |
| 18 |  return return |
AdWare.Win32.Boran.z | 20639 |
| 19 |  new new |
Trojan-Clicker.HTML.IFrame.fh | 19799 |
| 20 |  new new |
Exploit.Win32.Pidief.ddd | 19167 |
Unlike in previous months, September’s Top Twenty showing malware prevalent on the Internet has only six newcomers. There are usually many more.
Let’s start with the exploits that have made it to the ranking. Exploit.JS.Agent.bab (1st position), Trojan.JS.Agent.bhr (6th position) and Exploit.JS.CVE-2010-0806.b (15th position) exploit the CVE-2010-0806 vulnerability and have been prevalent for several months. It looks as though cybercriminals are set to exploit this vulnerability for a long time to come. The number of exploits targeting CVE-2010-1885 dropped from five in August to one -Exploit.HTML.CVE-2010-1885.d (3rd position) – in September. Two more exploits – Trojan-Downloader.Java.Agent.ft (2nd position) and Trojan-Downloader.Java.Agent.gr (12th position) – target the CVE-2009-3867, an old vulnerability in the getSoundBank() function. Finally, Exploit.Java.CVE-2010-0886.a (11th position) has featured in every ranking since May.
In September the number of exploits in the ranking was the same as that of adware programs. There are seven AdWare.Win32 programs in the Top Twenty, of which only FunWeb.ge (9th position) is a newcomer. Others have made the Top Twenty before: FunWeb.di (4th position), FunWeb.ds (5th position), FunWeb.fb (10th position), FunWeb.q (13th position), FunWeb.ci (16th position) and Boran.z (18th position), which was in the Top Twenty in July.
Now to September’s newcomers. Exploit.SWF.Agent.du (7th position), which is a Flash file, is something of a curiosity – up until now, it’s been relatively rare to see vulnerabilities in the Flash technology being exploited. A new Trojan-Downloader – Trojan-Downloader.Java.OpenStream.ap (17th position) – uses standard Java classes to download a malicious object. The malware writers have used obfuscation, as shown in the screenshot below:

Fragment of Trojan-Downloader.Java.OpenStream.ap
The repeated characters have no useful function and are included to prevent the program from being detected by antivirus software.
Another newcomer – Trojan-Clicker.HTML.IFrame.fh (19th position) – is a simple HTML page designed to redirect users..
The last piece of malware in the ranking – Exploit.Win32.Pidief.ddd (20th position) is another novelty. It’s a PDF file with an embedded script which launches the command prompt, writes a VBS script to the hard drive and displays the message “This file is encrypted. If you want to decrypt and read this file press “Open”?”. The Visual Basic script then launches and starts downloading another malicious script. The screenshot below shows a fragment of the malicious PDF file with part of the script and thphrase message displayed by the malware.
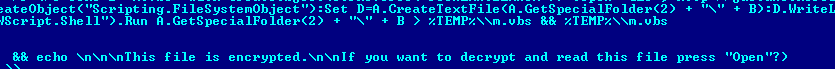
Fragment of Exploit.Win32.Pidief.ddd
Stuxnet
The month’s summary wouldn’t be complete without mentioning the Stuxnet worm; this is in spite of the fact that as the malware is highly specialized, it didn’t make the Top Twenty.
The mass media discussed Stuxnet extensively in September, although the worm was first identified as far back as early July. The worm exploits four different zero-day vulnerabilities; it also used two valid certificates belonging to Realtek and JMicron. However, the most important feature of Stuxnet is its payload, and this is why the worm received so much attention. The main purpose of this piece of malware is not to send spam or steal confidential user data: it’s designed to gain control over industrial systems. This is essentially a new-generation malicious program, and its appearance has led to talk of cyber-terrorism and cyber-warfare.
This malicious program has primarily infected India, Indonesia and Iran. A map of its geographical distribution is shown below:




















Monthly Malware Statistics, September 2010