
October’s two Top Twenties were compiled from statistics received during the month from the Kaspersky Security Network.
The first Top Twenty ranks the most widespread malicious program, including adware and potentially unwanted programs. The programs are ranked according to the number of computers they were detected on.
| Position | Change in position | Name |
| 1 |  1 1 |
Trojan-Downloader.WMA.Wimad.n |
| 2 |  New New |
Packed.Win32.Krap.b |
| 3 |  New New |
Worm.Win32.AutoRun.dui |
| 4 |  New New |
Virus.Win32.Sality.aa |
| 5 |  2 2 |
Trojan-Downloader.JS.IstBar.cx |
| 6 |  6 6 |
Trojan.Win32.Obfuscated.gen |
| 7 |  -4 -4 |
Packed.Win32.Black.a |
| 8 |  -2 -2 |
Trojan-Downloader.Win32.VB.eql |
| 9 |  New New |
Virus.Win32.Alman.b |
| 10 |  -6 -6 |
Trojan.Win32.Agent.abt |
| 11 |  New New |
Worm.VBS.Autorun.r |
| 12 |  New New |
not-a-virus:AdWare.Win32.Ejik.sl |
| 13 |  New New |
Trojan.JS.Agent.df |
| 14 |  -9 -9 |
Trojan-Downloader.HTML.IFrame.sz |
| 15 |  New New |
Virus.Win32.VB.bu |
| 16 |  2 2 |
Email-Worm.Win32.Brontok.q |
| 17 |  New New |
Trojan.Win32.Agent.rzw |
| 18 |  New New |
Trojan-Clicker.HTML.IFrame.wq |
| 19 |  -10 -10 |
not-a-virus:AdWare.Win32.BHO.ca |
| 20 |  -12 -12 |
Trojan.Win32.Agent.tfc |
September’s leader, the Agent.cxv rootkit, vanished from the rankings as suddenly as it appeared. It hasn’t disappeared completely, but this month’s statistics show it hovering around seventieth place, rather than being one of the most common programs.
Trojan-Downloader.WMA.Wimad.n has taken first place. This is a non-standard piece of malicious code -a multimedia file which exploits a vulnerability in Windows Media Player to download other Trojan programs to the victim machine.
A cluster of three new entrants follow Wimad. The most interesting of these are the Autorun.dui worm, and the Sality.aa virus. Given that Sality.aa is something of a fixture in our second Top Twenty, the fact this virus is now among the top three most common malicious programs is something of a cause for concern. It seems as though the epidemic caused by this virus is reaching new levels. Alman.b, a complex polymorphic virus, is in a similar situation.
This month, the Top Twenty includes almost all kinds of malware and potentially unwanted programs: there’s a script worm, a couple of adware programs, and several Trojans of varying types.
The diagram below groups the programs in this ranking according to class. For the second month in a row, the overall share taken by Trojan programs is dropping. This month the share has decreased from 70% to 50% of the total.
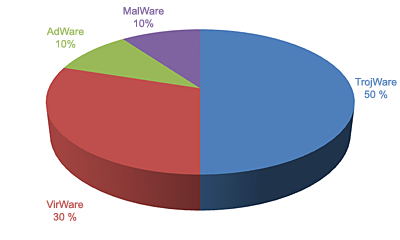
Overall, 39,240 unique malicious programs, adware programs, and potentially unwanted programs were detected on users’ computers in September. Clearly, the number of threats in the wild is increasing, and this month the increase was approximately 4,000 (35 103 programs were detected in September.)
The second Top Twenty presents statistics on the malicious programs which most often infect objects on victim machines. The majority of programs in this ranking are those which are capable of infecting files.
| Position | Change in position | Name |
| 1 |  3 3 |
Worm.Win32.Mabezat.b |
| 2 |  -1 -1 |
Virus.Win32.Xorer.du |
| 3 |  2 2 |
Virus.Win32.Sality.aa |
| 4 |  -2 -2 |
Net-Worm.Win32.Nimda |
| 5 |  -1 -1 |
Virus.Win32.Alman.b |
| 6 |  0 0 |
Virus.Win32.Parite.b |
| 7 |  0 0 |
Virus.Win32.Virut.n |
| 8 |  6 6 |
Virus.Win32.Sality.z |
| 9 |  0 0 |
Virus.Win32.Virut.q |
| 10 |  -2 -2 |
Virus.Win32.Small.l |
| 11 |  1 1 |
Virus.Win32.Sality.s |
| 12 |  -1 -1 |
Email-Worm.Win32.Runouce.b |
| 13 |  Return Return |
Worm.Win32.Otwycal.g |
| 14 |  -1 -1 |
Virus.Win32.Hidrag.a |
| 15 |  -5 -5 |
Virus.Win32.Parite.a |
| 16 |  -1 -1 |
Trojan.Win32.Obfuscated.gen |
| 17 |  -1 -1 |
Worm.Win32.Fujack.k |
| 18 |  0 0 |
Trojan-Downloader.WMA.GetCodec.b |
| 19 |  New New |
Worm.Win32.Fujack.bd |
| 20 |  Return Return |
Virus.Win32.Neshta.a |
The changes between this month’s and last month’s rankings are relatively small: there’s only one new malicious program, and two returns to the Top Twenty. Once again there’s been a change of leader – a relatively common occurrence. Nimda headed the August rankings, with Xorer.du taking its place in September, and the Mabezat.b worm moving into the top spot in October.
Mazebat.b was first detected in November of last year. In third place in September 2008, this program now seems to have gained a certain critical mass, enabling it to head the rankings this month. It seems it was premature to celebrate Otwical.g’s disappearance from the rankings. The worm has now returned, and although it’s only in 13th place, who knows what the future will bring? Some estimate that the botnet created by this worm is among the top ten largest botnets on the Internet.
Sality has also made itself felt this month, with Sality.aa taking first place, Sality.z rising six places, and Sality.s just falling outside the Top Ten.
Overall, it should be stressed that this second Top Twenty has achieved a certain stability in terms of the programs it contains. It’s unlikely that future changes and shifts in position will be caused by a large number of new programs entering the rankings.





















Monthly Malware Statistics: October 2008