
The following statistics were compiled in June using data from computers running Kaspersky Lab products:
- 249,345,057 network attacks blocked;
- 68,894,639 attempted web-borne infections prevented;
- 216,177,223 malicious programs detected and neutralized on users’ computers;
- 83,601,457 heuristic verdicts registered.
Overview of June’s main events
Fortunately, the first summer month was relatively uneventful with no major incidents to report and nothing out of the ordinary about cybercriminal activity. In developing countries, attackers took advantage of users’ ignorance of IT security to spread their malware. In developed countries, malware targeting users’ data and money was prevalent. In Brazil, it was ‘bankers’ as usual, while in Russia, as ever, malware was used in a variety of scams.
There has been much talk of cloud services offered by various companies lately. In June, cybercriminals used Amazon’s cloud to host and distribute malware that targeted Brazilian users and was designed to steal data from customers of 9 Brazilian banks. To improve its chances of success, the malware blocks the normal operation of AV programs and special plugins that are supposed to make online banking secure. The malware also steals digital certificates and Microsoft Live Messenger credentials.
As well as the standard fake archives and Trojan Blockers that demand ransoms for unblocking computers, Russian attackers tried to make money out of thin air using the BitCoins virtual money system. All that was required was to take over the resources of a victim machine for some time. Kaspersky Lab experts detected a piece of malware that launched bcm.exe, a legitimate BitCoins file, on the victim computer in an attempt to generate the cyber currency. The file is embedded in the malicious program and is copied to the hard drive after the malware is launched. The BitCoins site administration quickly blocked the attacker’s account, so apparently the cybercriminal did not make much money.
The interest that black hats have shown in Mac OS X has not abated. While rogue antivirus programs for that platform were detected in May, June saw cybercriminals distributing a backdoor – Backdoor.OSX.Olyx.a. This piece of malware is designed to provide attackers with remote control of victim machines, enabling them to use infected computers for their malicious purposes: download other malware, launch programs and send commands to an interpreter for execution.
June brought some notable successes for various law enforcement agencies in the war on cybercrime, with several successful operations resulting from joint efforts. In the US, the criminal activities of two international groups that made money from fake antivirus programs were terminated. According to preliminary estimates, the damage caused by these groups amounts to $74 million. In addition to US agencies, the operation to shut down these groups involved law enforcement agencies from Germany, France, Holland, Sweden, the UK, Romania, Canada, Ukraine, Lithuania, Latvia and Cyprus. About 600 people suspected of implementing online fraud schemes were arrested in several Southeast Asian countries. Participants of the operation also included police units in China, Taiwan, Cambodia, Indonesia, Malaysia and Thailand. In Russia, Pavel Vrublevsky, the owner of ChronoPay, Russia’s major payment processing center, was arrested on charges of organizing a DDoS attack on a competing service. It is worth mentioning another important development in combating cybercrime at the legislative level: in June, the Japanese parliament passed a number of amendments to existing laws, introducing jail terms for creating and distributing malware.
Malware rating
As was the case in the previous month, the Top 20 malicious programs on the Internet in June included a large number of new entries, while the Top 20 threats detected on users’ computers remained virtually unchanged.
Malicious programs on the Internet
The Top 20 malicious programs on the Internet are once again dominated by malware that make use of drive-by attacks: redirectors, script downloaders and exploits. These made up 14 of the 20 places in this rating.
Redirectors
Four redirectors appeared in this rating: Trojan-Downloader.JS.Agent.fzn (12th place), Trojan-Downloader.JS.Agent.gay (13th place), Trojan-Downloader.JS.IFrame.cfw (14the place) and Trojan.JS.IFrame.tm (15th place).
The latter two simply redirect users to a malicious site using an tag and can be described as primitive compared to the other two entries which make use of more sophisticated technology. As well as infecting legitimate .js files they also invoke the download of another JavaScript, albeit only when the cursor moves within the confines of the active window. This technology appears to be used in order to circumvent certain types of ‘sandboxes’ and emulators.
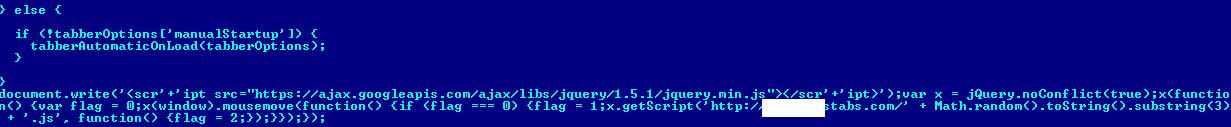
Fragment of script infected by Trojan-Downloader.JS.Agent.gay
Downloaders
Script downloaders appear in two groups in the rating. The first consists of: Trojan.JS.Redirector.pz (5th place), Trojan.JS.Redirector.qa (7th place) Trojan.JS.Redirector.py (8the place) and Trojan.JS.Redirector.qb (9th place). The second is made up of Trojan-Downloader.JS.Agent.gbj (11th place) and Trojan-Downloader.JS.Agent.gaf (19th place).
The main script data of all these downloaders is stored in HTML tags. The scripts in the first group use the alt parameter of the tag, while the second group uses the
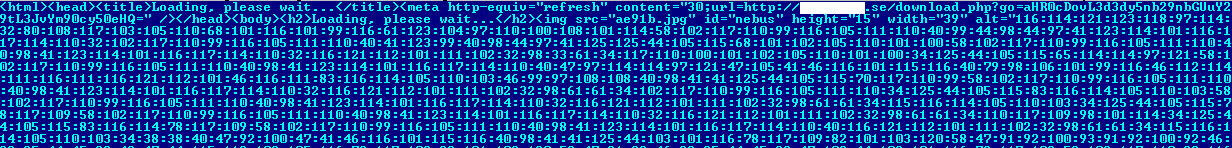
Fragment of the Trojan.JS.Redirector.qa malicious downloader
Exploits
It’s worth noting the appearance in SWF files of the exploit Trojan-Downloader.SWF.Small.dj (20th place). Its functionality consists of the hidden launch of another malicious SWF file from the same server folder.
Two exploits in PDF documents – Exploit.JS.Pdfka.dyi (16th place) and Exploit.JS.Pdfka.duj (17th place) – target a vulnerability (CVE-2010-1885) in tagged image file format (TIFF). To make analysis of PDF files more difficult, the cybercriminals spread the exploit code among several objects. The beginning of the JavaScript is located in one object, the second object contains the end of the script and the main data is in the third object. The code is somewhat obfuscated – all variable names are random and the names of objects and functions are made up as they go along.
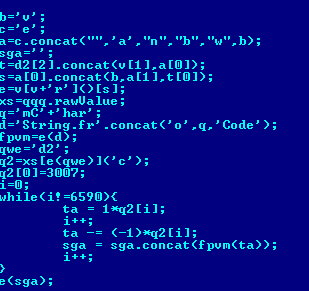
Fragment of the obfuscated Exploit.JS.Pdfka.duj JavaScript
The other new exploit to enter the top 20 was Exploit.HTML.CVE-2010-4452.bc (10th place). It uses a straightforward vulnerability (CVE-2010-4452) to download and launch a Java exploit, sending specific parameters to a Java applet via the tag. The cybercriminals decided to mask Exploit.HTML.CVE-2010-4452.bc – the majority of the symbols in the tags were modified to a sequence of ‘&#number’ while the case was changed in the remaining symbols.
Malicious programs on users’ computers
As has already been mentioned above, there were only minor changes to the Top 20 rating of malicious programs on users’ computers. However, along with all the usual suspects in this Top 20 there is a rather unusual specimen – the file virus Virus.Win32.Nimnul.a.
Nimnul infector
This malicious program first appeared in the Top 20 back in May and in the last two months has risen from 20th to 11th. This is very unusual considering that file infectors are gradually becoming obsolete. Cybercriminals now prefer malware protected by polymorphic packers (in order to ensure the uniqueness of packed malicious programs). It is hardly worth the bother of using file viruses, which are not easy to develop or maintain, and are fairly easy to detect on a system.
The Nimnul.a virus infects executable files by adding a .text section to the end of a file and modifying its entry point. After being launched, an infected file checks for the presence of a unique virus identifier (Mutex) on the OS. The presence of the Mutex object means that another infected file has been launched on the system. In that case, the virus only launches the original application. If Mutex is not found, it will be created and then the main Nimnul component will be dropped onto the disk. This component writes several other malicious libraries to the disk.
The malicious program steals personal configuration files for popular browsers, connects to a remote server and is then capable of substituting web pages.
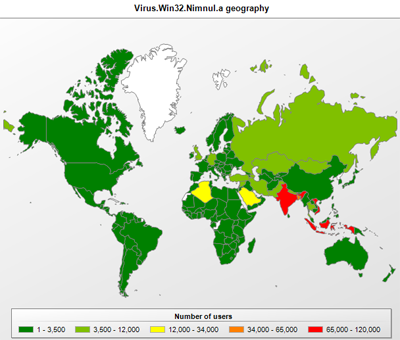
The virus spreads via removable media using autorun.inf and its own infection files. Interestingly, the virus has been recorded in India, Indonesia, Bangladesh and Vietnam. These were the countries where malware was detected on the highest percentage of Kaspersky Security Network participants: Bangladesh (85.76%), India (65.27%), Indonesia (59.51%) and Vietnam (54.16%). The users in these countries are obviously not careful enough when it comes to IT security and are using unpatched versions of Windows OSs. Microsoft released an update that disables autorun from removable media on 8 February 2011.
Top 20 malicious programs on the Internet
| Current rank | Delta | Verdict |
| 1 |  2 2 |
AdWare.Win32.FunWeb.kd |
| 2 |  4 4 |
Trojan-Downloader.JS.Agent.fxq |
| 3 |  2 2 |
AdWare.Win32.FunWeb.jp |
| 4 |  -2 -2 |
Trojan.JS.Popupper.aw |
| 5 |  New New |
Trojan.JS.Redirector.pz |
| 6 |  5 5 |
Trojan.HTML.Iframe.dl |
| 7 |  New New |
Trojan.JS.Redirector.qa |
| 8 |  New New |
Trojan.JS.Redirector.py |
| 9 |  New New |
Trojan.JS.Redirector.qb |
| 10 |  New New |
Exploit.HTML.CVE-2010-4452.bc |
| 11 |  New New |
Trojan-Downloader.JS.Agent.gbj |
| 12 |  New New |
Trojan-Downloader.JS.Agent.fzn |
| 13 |  New New |
Trojan-Downloader.JS.Agent.gay |
| 14 |  New New |
Trojan-Downloader.JS.Iframe.cfw |
| 15 |  New New |
Trojan.JS.Iframe.tm |
| 16 |  New New |
Exploit.JS.Pdfka.dyi |
| 17 |  New New |
Exploit.JS.Pdfka.duj |
| 18 |  New New |
Trojan-Ransom.JS.SMSer.id |
| 19 |  New New |
Trojan-Downloader.JS.Agent.gaf |
| 20 |  -1 -1 |
Hoax.Win32.Screensaver.b |
Top 20 malicious programs detected on users’ computers
| Current rank | Delta | Verdict |
| 1 |  0 0 |
Net-Worm.Win32.Kido.ir |
| 2 |  2 2 |
AdWare.Win32.FunWeb.kd |
| 3 |  -1 -1 |
Virus.Win32.Sality.aa |
| 4 |  -1 -1 |
Net-Worm.Win32.Kido.ih |
| 5 |  0 0 |
Trojan.Win32.Starter.yy |
| 6 |  0 0 |
Virus.Win32.Sality.bh |
| 7 |  1 1 |
Virus.Win32.Sality.ag |
| 8 |  -1 -1 |
Trojan-Downloader.Win32.Geral.cnh |
| 9 |  0 0 |
HackTool.Win32.Kiser.il |
| 10 |  Return Return |
AdWare.Win32.HotBar.dh |
| 11 |  1 1 |
Virus.Win32.Nimnul.a |
| 12 |  -2 -2 |
Trojan-Downloader.Win32.FlyStudio.kx |
| 13 |  5 5 |
Trojan.JS.Agent.bhr |
| 14 |  0 0 |
Worm.Win32.FlyStudio.cu |
| 15 |  1 1 |
Worm.Win32.Mabezat.b |
| 16 |  -3 -3 |
HackTool.Win32.Kiser.zv |
| 17 |  0 0 |
Hoax.Win32.Screensaver.b |
| 18 |  1 1 |
Trojan-Downloader.Win32.VB.eql |
| 19 |  -4 -4 |
Hoax.Win32.ArchSMS.pxm |
| 20 |  New New |
Trojan-Downloader.SWF.Small.dj |

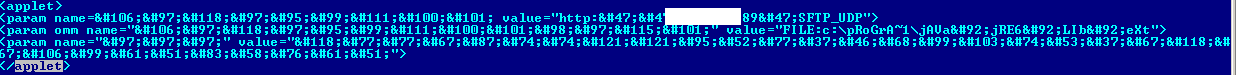

















Monthly Malware Statistics, June 2011