
The experts at Kaspersky Lab present their monthly report about malicious activity on users’ computers and on the Internet.
July in figures. The following statistics were compiled in July using data from computers running Kaspersky Lab products:
- 182,045,667 network attacks blocked;
- 75,604,730 attempted web-borne infections prevented;
- 221,278,929 malicious programs detected and neutralized on users’ computers;
- 94,004,507 heuristic verdicts registered.
This is how the situation looks when compared to June:
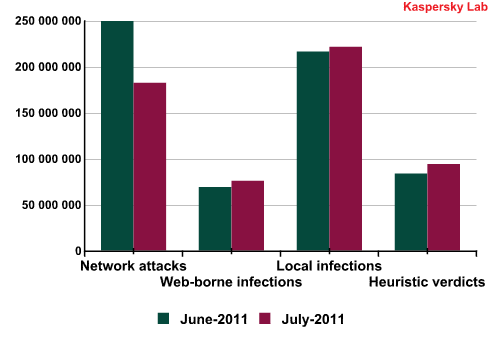
Number of threats detected in various categories. Source: KSN data
Google vs. the co.cc Domain Zone
One of the month’s most remarkable events was Google excluding 11 million+ URLs with *.co.cc addresses from its search results. The ‘blocked’ domain zone is among the largest globally, ranking fourth after .com, .de and .net in terms of registered domain names.
The reason for such drastic measures was due to the domain’s URLs regularly being used by cybercriminals to spread rogue antivirus programs or conduct drive-by attacks. It should be noted that the .cc zone belongs to the Cocos Islands, while the domain .co.cc belongs to a private South Korean company. The popularity of .co.cc among cybercriminals is explained by the fact that the domain registrar allows third-level domain names to be registered for free or for a very low price.
Our research shows that Google’s offensive has indeed resulted in cybercriminals using the .co.cc domains less frequently; however, they have merely started using the services of other domain zone registrars. Therefore, it is difficult to say how successful Google’s campaign has been. There is also the chance that legitimate, law-abiding domain owners have been inadvertently affected by Google’s actions.
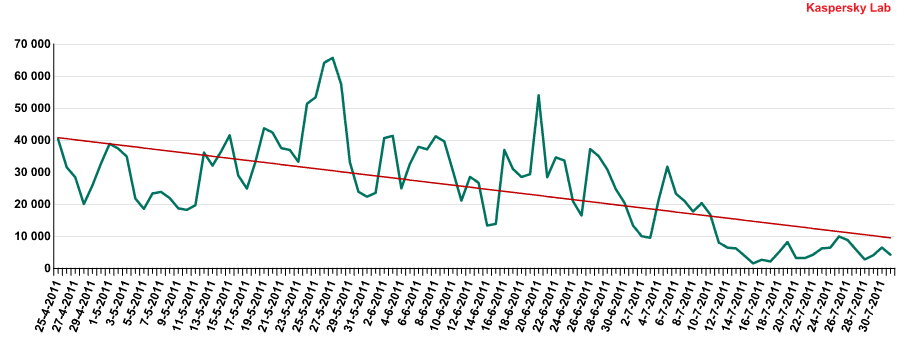
Number of unique users protected from attacks employing .co.cc domain names. Source: KSN data
ZeuS for Android
In July, a mobile version of the notorious ZeuS Trojan was detected – this is the fourth representative of the ZitMo spying Trojan. We have already encountered versions of ZitMo running on Symbian, Windows Mobile and BlackBerry platforms, but this time ZitMo has been modified to attack Android devices.
ZitMo (classified by Kaspersky Lab as Trojan-Spy.AndroidOS.Zbot) is designed to steal mTAN codes, one-time passwords used to conduct a remote transaction. Bank clients receive the code in an SMS and it ensures Protection Level 2 when conducting online banking.
Users themselves install the malicious program on their smartphones following a prompt from a ZeuS backdoor to install an alleged security application. If a user’s computer is infected with ZeuS, and the mobile phone is infected with ZitMo, the cybercriminals gain access to the victim’s bank account and can intercept the one-time transaction password sent by the bank to the user. In this case, even authentication using mTAN codes cannot prevent the victim’s money from being stolen from their bank account.
As protection of online banking security continues to develop, cybercriminals will increasingly supplement spy Trojans operating on users’ computers with mobile modules so they have a better chance of accessing the victims’ bank accounts. Users should be very careful when installing programs on their smartphones.
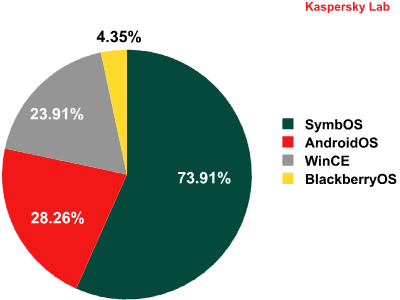
Occurrences of ZitMo across mobile platforms. Source: KSN data
Flying phishers
In July, the experts at Kaspersky Lab uncovered an interesting development: Brazilian phishers, in addition to bank account details, have started stealing the ‘miles’ accrued by frequent flyers. Not only are they using them to buy tickets but also as a form of currency. In one IRC message, a cybercriminal was selling access to a Brazilian botnet that sends spam in exchange for 60,000 miles, while in another message air miles were offered for stolen credit cards. This coincides with our predictions for 2011 in which we stated that cybercriminals would be interested in all kinds of information and ready to steal absolutely everything.
Personal data leaked on the Russian Internet
July saw the biggest ever leaks of personal data in the history of the Russian-language Internet. On 18 July, 8,000 text messages sent by subscribers of mobile phone operator MegaFon surfaced in the cache of Russian search engine Yandex and were in the public domain for several hours.
The incident appears to have been caused by an analytical tool, Yandex.Metrika, being installed incorrectly on the MegaFon site. The tool, which monitors web visitor behavior, passed on pages with the text messages to the search engine index.
A few days later there was more bad news: a query, albeit formulated with complex search syntax, entered into Google, Yandex and Mail.ru returned data about clients of online sex shops as well as the personal data of people who had bought railway tickets at two Russian websites.
It’s worth pointing out that in all these incidents there were problems with the robots.txt file that contains instructions for search engines when they index the contents of web pages. This suggests the administrators of the affected sites are also partially at fault.
Malware rating
For a number of months now the Top 20 malicious programs detected on users’ computers has remained virtually unchanged, while our other rating of online malicious programs has seen a regular turnover of new entries. July was no exception – 60% of the programs in the latter rating were new this month! This is due to the predominance on the Internet of malicious scripts that are not usually located on users’ machines but remote servers that are regularly updated by cybercriminals. Meanwhile, network worms such as Kido and viruses such as Sality dominate in the Top 20 rating of malicious programs on users’ computers. These programs can go undetected by antivirus solutions for a considerable length of time. They are also constantly trying to infect other machines via network folders or removable media which will trigger antivirus protection if installed.
In most cases, cybercriminals are very quick to update their malicious programs. The short-lived nature of each modification means they are difficult to detect using signatures and they rarely make it into our Top 20 ratings. To successfully combat such threats the antivirus industry not only uses signature-based detection methods but also heuristics and cloud technology.
Drive-by-download attacks remain one of the most popular methods of infecting users’ computers with malicious programs. Every month new entries that facilitate such attacks – redirectors, script downloaders and exploits – appear in the Top 20 malicious programs on the Internet. There were a total of 11 in July.
Top 20 malicious programs on the Internet
| Current Rank | Delta | Verdict |
| 1 |  0 0 |
AdWare.Win32.FunWeb.kd |
| 2 |  1 1 |
AdWare.Win32.FunWeb.jp |
| 3 |  1 1 |
Trojan.JS.Popupper.aw |
| 4 |  New New |
Trojan-Downloader.JS.Agent.gcv |
| 5 |  1 1 |
Trojan.HTML.Iframe.dl |
| 6 |  2 2 |
Trojan.JS.Redirector.py |
| 7 |  6 6 |
Trojan-Downloader.JS.Agent.gay |
| 8 |  New New |
Hoax.HTML.FraudLoad.a |
| 9 |  0 0 |
Trojan.JS.Redirector.qb |
| 10 |  New New |
Trojan-Downloader.JS.Agent.gdy |
| 11 |  New New |
Trojan-Downloader.Win32.Adload.ajek |
| 12 |  New New |
Trojan-Downloader.JS.Iframe.chf |
| 13 |  New New |
Hoax.HTML.BroUpdate.af |
| 14 |  New New |
Exploit.JS.Pdfka.efl |
| 15 |  New New |
Trojan-Downloader.JS.Agent.gdk |
| 16 |  New New |
Exploit.JS.CVE-2010-4452.t |
| 17 |  3 3 |
Hoax.Win32.Screensaver.b |
| 18 |  New New |
AdWare.Win32.Shopper.ds |
| 19 |  New New |
AdWare.Win32.Gamevance.hfti |
| 20 |  New New |
Trojan-Downloader.JS.Expack.as |
Top 20 malicious programs detected on users’ computers
| Current Rank | Delta | Verdict |
| 1 |  0 0 |
Net-Worm.Win32.Kido.ir |
| 2 |  0 0 |
AdWare.Win32.FunWeb.kd |
| 3 |  0 0 |
Virus.Win32.Sality.aa |
| 4 |  0 0 |
Net-Worm.Win32.Kido.ih |
| 5 |  0 0 |
Trojan.Win32.Starter.yy |
| 6 |  0 0 |
Virus.Win32.Sality.bh |
| 7 |  0 0 |
Virus.Win32.Sality.ag |
| 8 |  3 3 |
Virus.Win32.Nimnul.a |
| 9 |  0 0 |
HackTool.Win32.Kiser.il |
| 10 |  -2 -2 |
Trojan-Downloader.Win32.Geral.cnh |
| 11 |  -1 -1 |
AdWare.Win32.HotBar.dh |
| 12 |  0 0 |
Trojan-Downloader.Win32.FlyStudio.kx |
| 13 |  2 2 |
Worm.Win32.Mabezat.b |
| 14 |  New New |
Trojan.Win32.AutoRun.bhs |
| 15 |  -1 -1 |
Worm.Win32.FlyStudio.cu |
| 16 |  1 1 |
Hoax.Win32.Screensaver.b |
| 17 |  New New |
Trojan-Dropper.VBS.Agent.bp |
| 18 |  -2 -2 |
HackTool.Win32.Kiser.zv |
| 19 |  -1 -1 |
Trojan-Downloader.Win32.VB.eql |
| 20 |  Return Return |
Exploit.Win32.CVE-2010-2568.d |




















Monthly Malware Statistics: July 2011