
In its second month of compiling data, the new Kaspersky Security Network (KSN) technology revealed some significant changes amongst the most widespread malicious programs.
The first table is based on statistics provided by our 2009 antivirus products. This table shows the malicious programs detected on users’ computers.
| Position | Change in position | Name |
| 1 | Trojan.Win32.DNSChanger.ech | |
| 2 |  New New |
Trojan.Win32.Pakes.kab |
| 3 |  New New |
Trojan-Downloader.Win32.Agent.xqz |
| 4 |  New New |
Trojan-Downloader.Win32.Agent.yaw |
| 5 |  New New |
Trojan-Downloader.Win32.Agent.xws |
| 6 |  New New |
Trojan-Downloader.Win32.Small.zie |
| 7 |  New New |
Trojan-Downloader.Win32.Agent.xna |
| 8 |  New New |
Trojan-Downloader.JS.Agent.chk |
| 9 |  New New |
Trojan.Win32.Agent.tfc |
| 10 |  6 6 |
not-a-virus:AdWare.Win32.BHO.ca |
| 11 |  New New |
not-a-virus:AdWare.Win32.Agent.cp |
| 12 |  -3 -3 |
Trojan.Win32.Agent.abt |
| 13 |  New New |
Trojan-Dropper.Win32.Agent.tbd |
| 14 |  New New |
not-a-virus:AdWare.Win32.BHO.sc |
| 15 |  New New |
not-a-virus:AdWare.Win32.BHO.vp |
| 16 |  New New |
Trojan-GameThief.Win32.OnLineGames.sjbb |
| 17 |  New New |
Trojan-Clicker.Win32.Agent.bkd |
| 18 |  1 1 |
Trojan.Win32.Chifrax.a |
| 19 |  New New |
Trojan.RAR.Qfavorites.a |
| 20 |  New New |
Trojan-GameThief.Win32.OnLineGames.sgpq |
Despite the changes, last month’s leader – Trojan DNSChanger.ech – remains at the top of this ranking. Overall, it is more than three times more widespread than the program which comes in second place. This indicates that there is quite a large-scale epidemic caused by DNSChanger which is affecting Western European countries in particular.
There were a total of 16 new entries to the rankings this month, all of which were added to our antivirus databases in August 2008. Prominent among the newcomers is a group of six Trojan-Downloaders that have occupied 3rd to 8th place. By preventing these Trojan-Downloaders from fulfilling their primary task of downloading the main body of a malicious program, our antivirus products have also blocked mass downloads of other malicious programs to users’ computers.
A number of Adware programs in the form of BHO (Browser Helper Object) also stand out. The large number of these programs is due to the fact that Internet Explorer – the browser such programs are designed to function on – is extremely popular.
Last month’s statistics contained four classes of malicious and potentially unwanted programs (TrojWare, AdWare, VirWare and other MalWare). In August only TrojWare and AdWare remained.
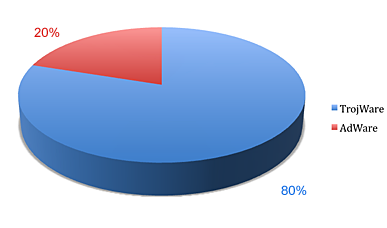
A total of 28940 different malicious and potentially unwanted programs were detected on users’ computers in August. That is an increase of more than 8000 on July’s figures and points to a significant increase in the number of in-the-wild threats.
The second table provides data about the most common malicious programs among all infected objects detected. The majority of the programs listed below have file-infection capabilities. The figures given are interesting as they indicate the spread of threats which need to be disinfected, rather than simply dealt with by deleting infected objects.
| Position | Change in position | Name |
| 1 |  3 3 |
Net-Worm.Win32.Nimda |
| 2 |  8 8 |
Virus.Win32.Xorer.du |
| 3 |  3 3 |
Virus.Win32.Parite.b |
| 4 |  5 5 |
Virus.Win32.Virut.n |
| 5 |  9 9 |
Virus.Win32.Parite.a |
| 6 |  2 2 |
Virus.Win32.Alman.b |
| 7 |  New New |
Trojan.Win32.DNSChanger.ech |
| 8 |  New New |
Email-Worm.Win32.Runouce.b |
| 9 |  4 4 |
Worm.Win32.Fujack.k |
| 10 |  9 9 |
Worm.VBS.Headtail.a |
| 11 |  4 4 |
Trojan-Downloader.WMA.GetCodec.d |
| 12 |  New New |
Virus.Win32.Downloader.ax |
| 13 |  New New |
Trojan-Clicker.HTML.IFrame.js |
| 14 |  -13 -13 |
Virus.Win32.Virut.q |
| 15 |  New New |
Virus.Win32.Small.l |
| 16 |  -12 -12 |
Virus.Win32.Hidrag.a |
| 17 |  -5 -5 |
Worm.Win32.Otwycal.g |
| 18 |  New New |
Virus.Win32.Virut.b |
| 19 |  -14 -14 |
Virus.Win32.Neshta.a |
| 20 |  New New |
Virus.Win32.Tenga.a |
The changes in this list are less dramatic – only 7 new entries. However, there was some significant movement, with last month’s leader – Virut.q – falling 13 places and Fujack.ap dropping out of the rankings altogether after a second place finish last month.
The surprise leader turned out to be a worm that dates back to 2001. You could have been forgiven for thinking that such a worm would have disappeared from the Internet long ago, but the facts suggest otherwise: Nimda is still active and it’s likely that it’s still present in files that were infected during the epidemics of 2001-2002.
The appearance of Trojan.Win32.DNSChanger.ech in the second table also deserves a mention. This shows that it is constantly modifying itself and can exist in various guises on different computers.

















Monthly Malware Statistics for August 2008