
There were no major malware incidents to talk about in December. However, throughout the month:
- 209064328 network attacks were blocked;
- 67408107 attempted infections via the web were prevented;
- 196651049 malicious programs were detected on users’ computers and neutralized;
- 70951950 heuristic verdicts were registered.
The tactics used by the cybercriminals remained the same. Surfing the web is still a dangerous pastime, while social engineering is routinely used to entice users into opening malicious links or downloading malicious or fraudulent programs.
Scammers in the .рф domain
November 2010 saw the beginning of domain name registration in the .рф (Cyrillic abbreviation for the Russian Federation) zone of the Internet. We decided to monitor how the cybercriminals would react to the new domain and we found that their malware of choice in this new area of the Internet was predominantly of a fraudulent nature.
Three types of malware are detected most of all on malicious sites in the .рф zone. The first is fake archives, which we have covered in quite a lot of detail recently, including in last month’s review. The second is the primitive script redirector Trojan.JS.Redirector.ki which simply redirects users to a malicious page using the command “document.location”.
The third – Hoax.Win32.OdnoklAgent.a – is quite an unusual sample. The program opens a window that closely resembles a login page for the Russian-language social networking site Odnoklassniki. The window even contains links to the social network and the site’s copyright information. But the program doesn’t actually do anything, even if the correct login and password are entered.

The window opened by Hoax.Win32.OdnoklAgent.a
So why would someone go to the trouble of creating a program like Hoax.Win32.OdnoklAgent.a? The thing is, the .рф zone is awash with lots of very similar sites offering “free communication services”. But these so-called services are anything but free: in order to access them the user has to send an SMS to a premium-rate number. After sending an SMS you receive a “service” that turns out to be the stub program Hoax.Win32.OdnoklAgent.a.
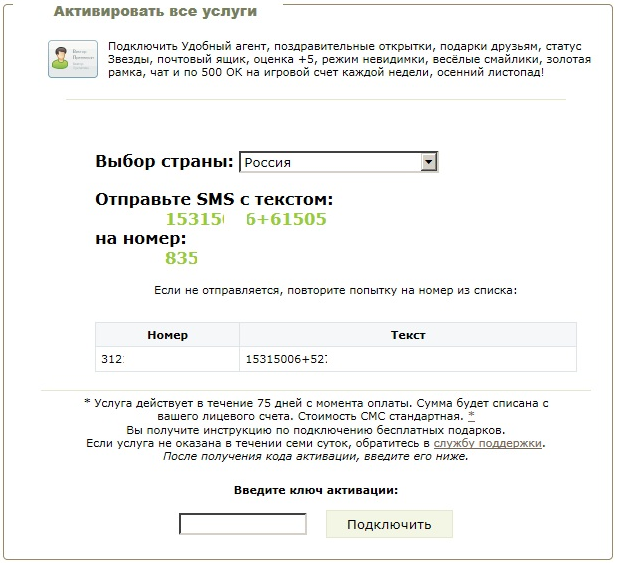
A page displaying an offer for a “service”
On all these sites there is a section at the bottom of the main page that states that the site has nothing to do with the Odnoklassniki social network and the software that can be accessed is only intended as a joke.
This is the site owners’ way of protecting themselves against any claims of fraud. But in this case the joke is on those inattentive users who don’t notice the disclaimer and end up paying the cost of an SMS.
Fake antivirus programs go online
The amount of fake antivirus programs has decreased recently as the real McCoy successfully stems their spread to users’ computers. But the scammers behind these rogue programs have started using the Internet as an alternative. In this scenario the program doesn’t need to be downloaded to a computer; the cybercriminals just have to get the user to visit a specific page, which is a lot easier than bypassing real antivirus protection. Several of these new ‘Internet antivirus programs’ were among the leading malicious programs detected online in December, with two samples making it into our Top 20 at 18th and 20th places.
The screenshot below was generated by Trojan.HTML.Fraud.ct and gives an insight into how these fake antivirus programs work.

Screenshot generated by Trojan.HTML.Fraud.ct
As you can see from the screenshot, the fake antivirus program generates an Internet page that closely resembles the My Computer window in a Windows operating system. The subsequent scenario is already a familiar one: it starts to simulate a scan of the computer and almost immediately claims it has detected malware. If the user agrees to clean up the system, a fake antivirus program is downloaded which then tells the user to purchase a license in order to remove the “malware”.

Request for payment from a fake antivirus program
The majority of computers where this malicious program was detected were located in developed countries: the USA, Canada, the UK, Germany and France, with India most probably making it into the list due to the high number of English-speaking users in that country.
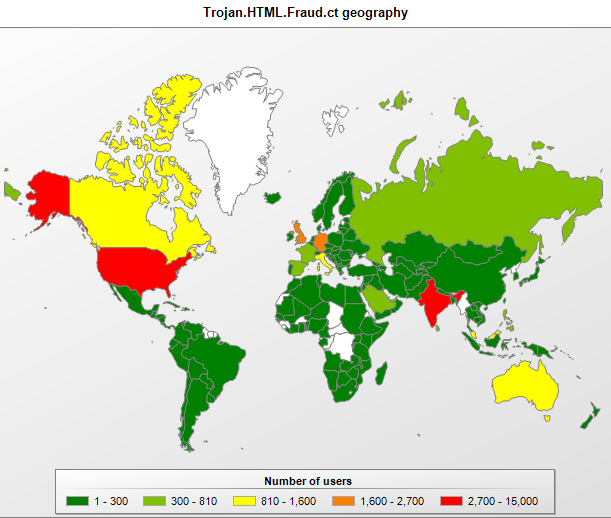
The geographical spread of Trojan.HTML.Fraud.ct
Malicious links in disguise
Services that shorten URLs have only just recently become popular. This may well be down to Twitter’s 140 character limit, but cybercriminals have been quick to make use of the services to mask malicious links.
During an attack on Twitter in December the top trends on the site’s main page included a number of entries that had made it into the list with the help of malicious programs. All the trends contained links that had been shortened using services such as bit.ly and alturl.com. After several redirects the links led to an infected web page that downloaded a malicious program to users’ computers without their knowledge. Google’s goo.gl service was also used by cybercriminals to spread malicious links on Twitter at the start of the month.
Another method used to mask malicious links was detected at the end of the month in an instant messenger mass mailing that contained links to a Facebook page warning users they were navigating away from the social networking site. The link had been crafted in such a way that after users clicked the ‘Continue’ button that appeared on the Facebook page they ended up on a malicious site.
TDSS flexes its muscles
Apart from organizing online attacks and relatively straightforward attacks via social networks, cybercriminals are still working on the “heavy artillery” in their arsenal. The authors of one of today’s most complex malicious programs – the TDSS rootkit – continue to perfect their creation. In December, the latest modification of the rootkit, TDL-4, started exploiting the vulnerability CVE-2010-3338 that was discovered in June 2010 while analyzing the Stuxnet worm.
More than just vulnerabilities
In our November review we wrote about the explosive growth of the Trojan-Downloader.Java.OpenConnection family. Instead of using vulnerabilities to download malware to victims’ computers, these programs employ the OpenConnection method of a URL class.
Two representatives of Trojan-Downloader.Java.OpenConnection (2nd and 7th places) were among the Top 20 malicious programs detected on the Internet in December. At the height of their activity the number of computers on which these programs were detected in a 24-hour period exceeded 40,000.

The number of cases of Trojan-Downloader.Java.OpenConnection
detected for the period October-December 2010
As we just mentioned, all the representatives of the Trojan-Downloader.Java.OpenConnection family, instead of exploiting vulnerabilities, use standard Java functionality to download and run files from the web. This is currently one of the prime download methods for malicious programs written in Java. It appears that until Oracle closes the functionality this family uses to download files its popularity will continue to grow.
Adobe XML Forms in PDF exploits
The Top 20 malicious programs detected on the Internet in December included Exploit.Win32.Pidief.ddl (11th place) which is a PDF document based on Adobe XML Forms. The payload of Pidief.ddl is in a JavaScript script which is embedded in XML-stream. The Adobe XML Forms object model contains an ‘event’ object that invokes a script when a certain event occurs. The object’s ‘activity’ property is responsible for executing the script. This property contains a string that tells the parser when to invoke the script. The string in this particular file contains the word ‘initialize’, meaning the launch of the malicious script is initialized when a user opens the PDF document. The script is an exploit which downloads and runs another malicious program.

A fragment of the Exploit.Win32.Pidief.ddl code
This is the first time we have seen malicious PDF documents that use Adobe XML Forms being spread en masse.
Annoying advertising
Topping the list of web-based threats, well ahead of its nearest rival, was AdWare.Win32.HotBar.dh, an adware program that includes HotBar, Zango, and ClickPotato. It also claimed 5th place in the Top 20 malicious programs detected on users’ computers. As a rule, this type of software is installed along with legitimate applications and then annoys the user by displaying intrusive advertising.

Installation of ClickPotato adware along with VLC Media Plater
Malware on the Internet
| Position | Change in position | Name | Number of distinct users |
| 1 |  New New |
AdWare.Win32.HotBar.dh | 203975 |
| 2 |  New New |
Trojan-Downloader.Java.OpenConnection.cf | 140009 |
| 3 |  1 1 |
Trojan.HTML.Iframe.dl | 105544 |
| 4 |  8 8 |
Trojan.JS.Popupper.aw | 97315 |
| 5 |  13 13 |
Trojan.JS.Redirector.lc | 73571 |
| 6 |  Returned Returned |
AdWare.Win32.FunWeb.di | 70088 |
| 7 |  -6 -6 |
Trojan-Downloader.Java.OpenConnection.bu | 70006 |
| 8 |  -5 -5 |
Exploit.Java.CVE-2010-0886.a | 60166 |
| 9 |  -3 -3 |
Trojan.JS.Agent.bmx | 57539 |
| 10 |  -2 -2 |
Exploit.JS.Agent.bab | 54889 |
| 11 |  New New |
Exploit.Win32.Pidief.ddl | 53453 |
| 12 |  -5 -5 |
Trojan.JS.Agent.bhr | 49883 |
| 13 |  New New |
Trojan-Downloader.JS.Small.os | 40989 |
| 14 |  New New |
Trojan-Clicker.JS.Agent.op | 40705 |
| 15 |  Returned Returned |
Exploit.HTML.CVE-2010-1885.v | 40188 |
| 16 |  New New |
Packed.Win32.Krap.ao | 38998 |
| 17 |  New New |
AdWare.Win32.FunWeb.fq | 36187 |
| 18 |  New New |
Trojan.JS.Fraud.ba | 35770 |
| 19 |  -9 -9 |
Trojan.JS.Iframe.pg | 35293 |
| 20 |  New New |
Trojan.HTML.Fraud.ct | 33141 |
Malware detected on users’ computers
| Position | Change in position | Name | Number of distinct users |
| 1 |  0 0 |
Net-Worm.Win32.Kido.ir | 468580 |
| 2 |  0 0 |
Net-Worm.Win32.Kido.ih | 185533 |
| 3 |  0 0 |
Virus.Win32.Sality.aa | 182507 |
| 4 |  0 0 |
Trojan.JS.Agent.bhr | 131077 |
| 5 |  New New |
AdWare.Win32.HotBar.dh | 122204 |
| 6 |  1 1 |
Virus.Win32.Sality.bh | 110121 |
| 7 |  -2 -2 |
Virus.Win32.Virut.ce | 105298 |
| 8 |  0 0 |
Packed.Win32.Katusha.o | 100949 |
| 9 |  New New |
Porn-Tool.Win32.StripDance.b | 92270 |
| 10 |  -4 -4 |
Worm.Win32.FlyStudio.cu | 88566 |
| 11 |  -11 -11 |
Trojan.Win32.AutoRun.avp | 68970 |
| 12 |  -2 -2 |
Exploit.JS.Agent.bab | 65139 |
| 13 |  1 1 |
Trojan-Downloader.Win32.Geral.cnh | 63651 |
| 14 |  -3 -3 |
Trojan-Downloader.Win32.VB.eql | 57155 |
| 15 |  -3 -3 |
Exploit.Win32.CVE-2010-2568.b | 55578 |
| 16 |  -1 -1 |
Worm.Win32.Mabezat.b | 54994 |
| 17 |  -1 -1 |
Packed.Win32.Klone.bq | 53160 |
| 18 |  -5 -5 |
Exploit.Win32.CVE-2010-2568.d | 50405 |
| 19 |  -1 -1 |
AdWare.Win32.FunWeb.gq | 50272 |
| 20 |  New New |
Worm.VBS.VirusProtection.c | 46563 |



















Monthly Malware Statistics, December 2010