
Earlier tonight I was on my balcony and noticed a very rare phenomenon, at least when it comes to seeing it from Moscow: the Aurora. It was so beautiful, especially since it was the first time for me to see it. I decided to write about it on Twitter and then decided to search for “северное сияние” (Aurora in Russian) to see if others have noticed it too.
I saw a number of tweets from people in Moscow who also saw the Aurora. Then, I noticed “Morgan Freeman” listed in the Twitter Trends.
Thinking that something has happened to him I checked the tag and found a number of suspicious messages. After checking the URL I found they were malicious – a new attack being carried through Twitter right now, live.
Further investigation revealed several trending topics –‘Morgan Freeman’, ‘Advent Calendar’, ‘Pastor Maldonado’, ‘Toivonen’, ‘Grinch’ and ‘Hannukah’ – with various messages with the shortened URLs. Various shortening services were used: tinyurl.com, urlcut.com, bit.ly, doiop.com, tiny.cc, alturl.com, shortlinks.co.uk, yep.it – all pointing to malicious websites.
All these links lead to br********.com/about.html which will redirect user to bestivideos****.it. Then user will be redirected to myb****.com/flash/ where user will see the following ‘offer’:
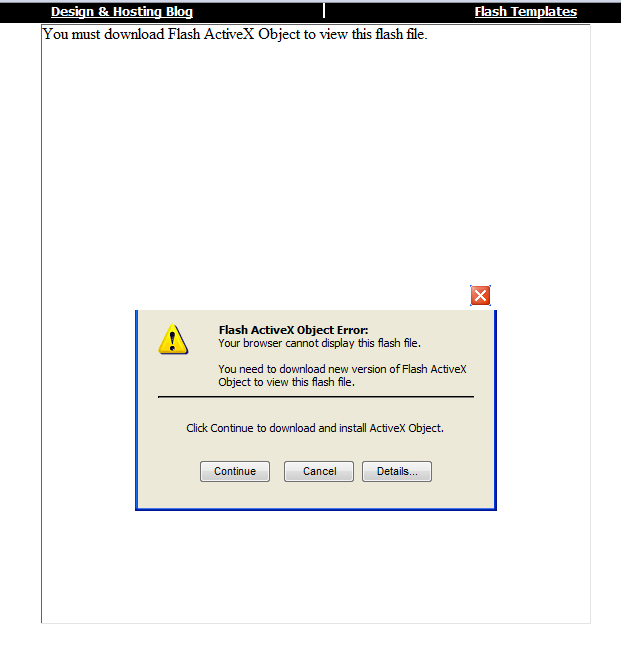
This ‘codec’ is actually is malicious and detected by us as Trojan-Dropper.Win32.Drooptroop.ipl.
Be careful with current twitter trends because other popular topics may also lead to malicious messages!
UPD: number of messages with each malicious trend has grown to almost 3000 in about 40 minutes





















Malicious Twitter trends