
Many people have had a run-in with subscriptions to mobile content providers. They appear out of the blue, and get discovered only when account funds run dry. It might seem that the obvious solution is not to visit dubious sites and not to install apps from third-party sources. But, alas, these days such advice is clearly not enough. We recently discovered several apps in Play Market directly related to such intrusive services.
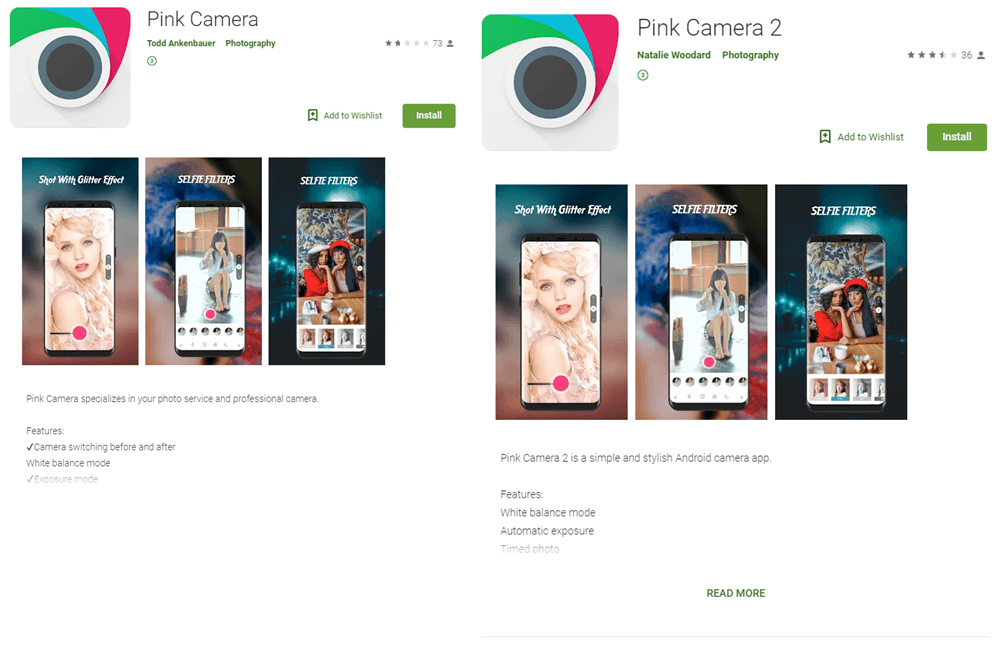
Pink Camera (com.paint.oil) and Pink Camera 2 (com.psbo.forand) are identical save for the numeral in the name; each has been installed more than 10,000 times
On the face of it, they are ordinary photo editors, but suspicions start to creep in on perusing the list of permissions. For example, the apps request access to Wi-Fi controls, which is rather unusual for this type of software. What’s more, when run, the editors request access to notifications — and keep doing it till the user says “yes.” Next, while the user is trying to embellish a photo (using the meager functionality), the app collects information in the background about the device and sends it to the server ps.okyesmobi[.]com.
Example of a request received after decrypting app traffic:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
{ "q1":"201905211050", // app ID "y":1184, // screen height "sign":"308F03D2E9173D9A1A43DFA15FDAF47D" "z":"PUSH", "e":"201905211050", "pl":"25011", // network operator code "cf":"111,108", "s1":"104870", "a":"862921000707889", // imei "i":720, // screen width "b":"250110201713837", // imsi "c":"unknown", "j":"ru", "d":"S10", // phone model "e1":1 // Wi-Fi status } |
As can be seen, information is transmitted about the device and network operator. In response, the software receives a set of links (depending on the country and network operator) to the pages:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
{ "sts":200, "ph":"", "js":[], "list": [ { "sta":0, "cf":"111", "dy":0, "tl":"http://of.okyesmobi[.]com/redirect?uid=F867D2329F195671825571419DB5B7FA67880B4E99583D6B&sourceid=2300&clickid=104870_112672190_250110201713837_862921000707889_201905211050_0.31_94.25.169.249", "id":0, "oid":112672190 } ], "cr": [ { "tl":"http://of.okyesmobi[.]com/redirect?uid=35092271DFB564AE09748A8CF282E15D089A4800D04DE5FE&sourceid=2300&clickid=104870_155608136_250110201713837_862921000707889_201905211050_0.36_94.25.169.249&p=1", "oid":155608136 }, { "tl":"http://of.okyesmobi[.]com/redirect?uid=71CBD61E0439CE5B6B6EF0BC46C140A842767CC39AC9A56E&sourceid=2300&clickid=104870_130581973_250110201713837_862921000707889_201905211050_0.24_94.25.169.249&p=1", "oid":130581973 } ], "wf":true } |
After several redirects, the addresses take the user to a subscription page. Our technologies detect these pages as not-a-virus:HEUR:AdWare.Script.Linkury.gen.
On receiving the addresses of the malicious pages, the program loads them in a window unseen by the user. Before doing so, the app turns off Wi-Fi in the user’s phone, thereby activating mobile data to simplify the subscription process.
The app then decrypts a Java helper script stored in the app resources, and performs the actions required to activate the subscription:
- It substitutes the user’s phone number (obtained while harvesting information) into the relevant field.
- If the subscription page is CAPTCHA-protected, the app uses the image recognition service chaojiying[.] and automatically inserts the result into the relevant field on the page.
- If an SMS code is required, the app gets it through access to notifications.
- It clicks the “subscribe” button.
How to protect yourself
Analysis of pages loaded by the malware revealed the targets to be users from different countries, while its distribution through an official app store helped the authors to spread it far and wide. To avoid the hook and save money on your mobile phone account, we recommend carefully studying the list of requested permissions during app installation and installing a security solution on your smartphone capable of detecting this type of threat. Additionally, you can enable content-blocking options, or open a “content account” — a free service offered by some carriers for managing subscription payments.
IOCs
SHA256
- 7F5C5A5F57650A44C10948926E107BA9E69B98D1CD1AD47AF0696B6CCCC08D13
- E706EB74BAD44D2AF4DAA0C07E4D4FD8FFC2FC165B50ED34C7A25565E310C33B
- 796A72004FAE62C43B1F02AA1ED48139DA7975B0BB416708BA8271573C462E79
- C5CA6AA73FDCB523B5E63B52197F134F229792046CBAC525D46985AD72880395
- B9038DC32DE0EA3619631B54585C247ECFD304B72532E193DED722084C4A7D1C
- D4406DEE2C0E3E38A851CEA6FD5C4283E98497A894CA14A58B27D33A89B5ED5F
- 59D64FBFF1E5A9AC1F8E29660ED9A76E5546CA07C2FF99FE56242FA43B5ABEC3
- C5B6146D7C126774E5BB299E732F10655139056B72C28AA7AD478BD876D0537E
C&C
- ps.okyesmobi[.]com:8802























Not-so-dear subscribers