
In the past few days several Brazilian ISPs have fallen victim to a series of DNS cache poisoning attacks. These attacks see users being redirected to install malware before connecting to popular sites. Some incidents have also featured attacks on network devices, where routers or modems are compromised remotely.
Brazil has some big ISPs. Official statistics suggest the country has 73 million computers connected to the Internet, and the major ISPs average 3 or 4 million customers each. If a cybercriminal can change the DNS cache in just one server, the number of potential victims is huge.
Last week Brazil’s web forums were alive with desperate cries for help from users who faced malicious redirections when trying to access websites such as YouTube, Gmail and Hotmail, as well as local market leaders including Uol, Terra and Globo. In all cases, users were asked to run a malicious file as soon as the website opened.
We monitored one attack which saw a clean machine displaying this warning when opening Google:
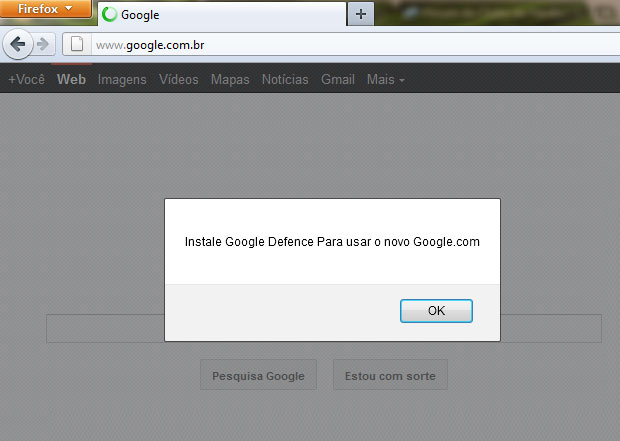
“To access the new Google.com you need to install Google Defence”
It asks the customer to download and install the so-called “Google Defence” software required to use the search engine. In reality, though, this file is a Trojan banker detected by Kaspersky’s heuristic engine. Research into this IP highlighted several malicious files and exploits hosted there:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
80.XX.XX.198/Google_setup.exe 80.XX.XX.198/google_setup.exe 80.XX.XX.198/Google_Setup.exe 80.XX.XX.198/ad2.html 80.XX.XX.198/flash.jar 80.XX.XX.198/FaceBook_Complemento.exe 80.XX.XX.198/ad.html 134XX69350/AppletX.class 80.XX.XX.198/YouTube_Setup.exe 80.XX.XX.198/FlashPlayer.class 80.XX.XX.198/google2.exe 80.XX.XX.198/crossdomain.xml 80.XX.XX.198/favicon.ico |
In fact the file ad.html is an encrypted script, exploiting CVE-2010-4452 and running arbitrary code in an old installation of JRE. The exploit detected by us as Exploit.Java.CVE-2010-4452.a calls up one of the files in this list. According to statistics in KSN (Kaspersky Security Network) all the infected users are from Brazil; we registered more than 800 attempts to access this site which were thwarted by our web antivirus.
In related news, last week Brazil’s Federal Police arrested a 27-year-old employee of a medium-sized ISP in the south of the country. He was accused of participating in this malicious scheme. Over a 10-month period he had changed the DNS cache of the ISP, redirecting all users to phishing websites. We strongly suspect similar security breaches will be happening in other small and medium ISPs in the country.
Attacks in network devices
In another related incident some companies reported attacks in their network devices, where an attacker remotely accessed the company’s router or modem and changed all the DNS configurations of the devices. In those cases, when employees of the affected companies tried to open any website they were requested to execute a malicious Java applet:
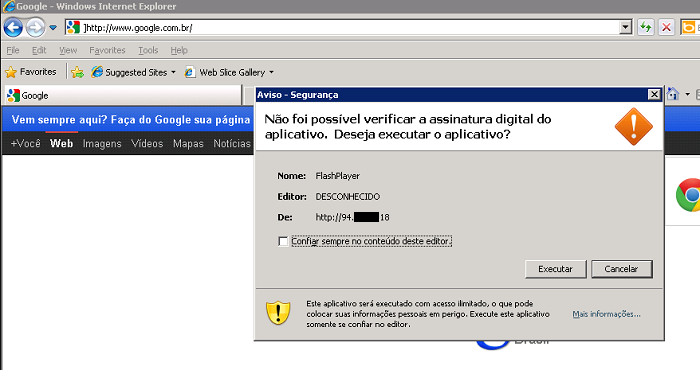
Not surprisingly the malicious applet goes on to install a Trojan banker, spotted by our heuristic detection.
As described by my colleague Marta in this analysis, several routers and modems have security flaws that enable an external attacker to access and change the configuration of the device. They are able to exploit security failures and vulnerable configurations such as default passwords.
We advise all affected users to update antivirus and all software in the computer, also change the DNS configuration to other providers (such as Google DNS). In attacks against network devices we also recommend updating the firmware of the router and changing the default passwords.





















Massive DNS poisoning attacks in Brazil