
IT security professionals have predicted that 2007 will be a watershed year in the battle against computer viruses, which would have an effect on computing and computer users as a whole.
In 2007 virus writers will continue to be active in creating and using Trojans which are designed to steal user data. The main targets will be users of a range of banking and e-payment systems, and online gamers. Virus writers and spammers will continue to work more and more closing together, with infected machines being used not only to organize new virus epidemics and attacks, but also as spamming platforms.
As for infection vectors, Kaspersky Lab analysts believe that email and browser vulnerabilities will continue to be widely used. Although malicious programs will continue to use P2P networks and IRC channels to spread, this is unlikely to be on a large scale. Generally, this tactic will be used locally – for instance, Winy, a P2P client which is very popular in Japan, may start to cause serious headaches for Asian users. Instant messaging clients will remain in the top three methods for conducting attacks: however, this infection vector is unlikely to see a big increase in popularity.
Epidemics, virus outbreaks and attacks will become even more markedly linked to specific geographical territories. For instance, Trojans which steal online gaming data and worms with virus functionality are likely to dominate in Asia, whereas Trojan spy programs and backdoors will have the lion’s share in Europe and the USA. Latin America will continue to suffer from a large number of Trojan banking programs.
There’s no question that Vista, and vulnerabilities associated with this new operating system, will be the main security event of 2007.
It’s also likely that there will be a significant increase in the number of malicious programs for other operating systems, primarily for MacOS, and for other *nix systems. Gaming consoles such as PlayStation and Nintendo are also likely to be targeted, as the increasing number of such devices and their ability to connect to each other and the Internet will make them a juicy potential target for virus writers. It’s true that at the moment, malicious code for these devices has been confined to the proof of concept/ vandal category. However, 2007 may be the year when viruses for ‘non-computers’ take a quantum leap and start to evolve actively, although the likelihood of this happening is small.
Malicious programs will continue to become more sophisticated technologically, and will use new methods in order to mask their presence in the system. Polymorphism, garbage code and rootkit technologies will be even more widely used and will become the de facto standard for the majority of new malicious programs.
There will also be an increase in the number of targeted attacks on medium business and large companies. In addition to traditional information theft, such attacks will be designed to extort money from the organizations under attack, including payment for decrypting data. One of the main infection vectors which will be used will be MS Office files by exploiting vulnerabilities in this software package.
The Internet battlefield
The end of 2006 was difficult for antivirus companies around the world. Virus researchers around the world were in a state of high alert, mobilizing all their resources throughout the final quarter of the year.
This was caused by the unprecedented long and widespread attacks on the Internet caused by the unknown authors of the Warezov family of email worms. The first examples of this worm appeared on the Internet in October 2006, and were most active towards the end of the month, when up to 20 new variants appeared in the space of 24 hours.
In many ways, Warezov is extremely similar to the notorious Bagle. Although Warezov is based on Mydoom.a source code, and Bagle was a completely original program created by an unknown group of virus writers, we are inclined to view these two worms as being related. Firstly, the way in which the epidemics were organized are extremely similar, with a large number of variants being mass mailed within a short period of time, which differ according to geographical region (e.g. the variants mailed in Russia differed to those mailed in Europe). Secondly, their functionality – installing other worm modules from Trojanized sites and collecting email addresses which are then sent to a remote malicious user – is identical. Bagle was the first to use this virus technology in order to provide fresh material for spammers address databases – Warezov did exactly the same.
These characteristics, and the appearance of Warezov and the cessation of new variants of Bagle coincided in the same week. It’s difficult to believe that the authors of Bagle suddenly decided to go out of business, with someone else taking over the reins. It’s possible that both worms are the creation of one and the same group.
By the end of 2006 we had detected more than 400 variants of Warezov. The authors of this worm organized a large number of short-lived mass mailings, sending out the latest variants, which led to a gigantic botnet being created. If we take into account that Warezov also harvests email addresses, it was clear that a wave of spam and phishing attacks was coming. Warezov was created and spread with one aim in mind – to use infected machines as mail proxy servers in the future.
To all intents and purposes, the worm’s authors and their clients had annexed a large part of the mass mailing black market. This was likely to lead to a reaction from competitors, with an answering blow being only a matter of time.
On 18th January 2007, hurricane Kyrill swept Europe. The snowstorm took the lives of more than 30 people. Tens of thousands of Europeans were left without light, mobile connections or normal transport. The world’s attention was focused on the events which were covered by the mass media around the clock.
On 20th January, another storm hit, but this time the victim was email. The gigantic mass mailing contained messages with some of the subjects included below. The subjects were, naturally, designed to make the user launch the file within the message:
- 230 dead as storm batters Europe.
- Russian missle shot down Chinese satellite
- Chinese missile shot down USA aircraft
- Sadam Hussein alive!
- Venezuelan leader: “Let’s the War beginning”.
- Fidel Castro dead.
- President of Russia Putin dead
- Third World War just have started!
The attached files were actually a Trojan program, which got classified as Trojan-Download.Win32.Small.dam and Trojan-Downloader.Win32.Small.bet. This Trojan would download other components to the victim machine with the result being a new, extremely aggressive, network worm which utilized rootkit technologies. Unofficially it was christened ‘the Storm worm’. The official name given to it in our antivirus databases was Email-Worm.Win32.Zhelatin.a.
War had been declared in cyberspace between the groups producing Warezov and Zhelatin. Taking into account the size of the botnets used by both groups, and their clear aim to conduct a large number of attacks, the situations was clear: this was threatening to become one of the most serious problems on the Internet in recent years.
Until now, the best known cyber conflict was that between Mydoom, Bagle and NetSky, back in spring 2004. The network was flooded with dozens of variants of these worms: they scanned victim machines for their competitors and took their place, deleting the original worm. The war was brought to an end by the arrest of 18 year old Sven Jaschan, the author of NetSky, in Germany. However, his creations remain one of the most widespread worms in mail traffic. Out of all the malware authors involved, only the authors of Bagle have remained active. It’s true that they disappeared into the shadows for a while, and didn’t react in any way to the appearance of Warezov, which is why we thought that they might have been involved in creating this worm. However, in January Bagle suddenly reappeared, and one variant of this worm became the most widespread malicious program in mail traffic.
The situation was becoming more and more interesting. Three groups, from different countries, who were all busy with the same thing – creating botnets to send spam and harvest email addresses. All these groups are dependent on money from spammers, who will pay good money for the biggest botnet and the largest database. This brought the three groups into conflict with each other, and they are willing to use everything at their disposal to gain an advantage. The result was an unending cycle of attacks on users. In order to infect machines, the virus writers had come up with newer and newer methods to evade antivirus filters.
The authors of Warezov began responding to Zhelatin attacks in March, and Bagle started periodically putting its head above the ramparts several times a month from March onwards. At the end of last year, antivirus companies were only having to combat attacks from a single groups, but now the complexity and volume of the task had increased three times. And all of this was accompanied by an increase in spam and phishing.
Almost 32% of all malicious code in mail traffic in March 2007 was made up of Trojan-Spy.HTML.Bankfraud.ra. This was clearly a result of the epidemics caused by Bagle, Zhelatin and Warezov. This malicious program is a typical phishing email, and millions of copies were sent around the world. We also detected repeat sendings of this Trojan, which was initially detected on 27th February 2007. The Trojan targets Branch Banking and Trust Company clients, luring them to fake sites which are registered by malicious users in Croatia and the Cocos (Keeling) Islands.
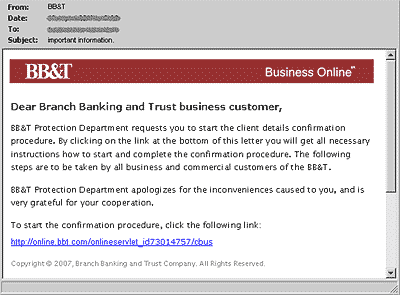
We can only guess which group is responsible for making this phishing attack a reality. Personally, my money would be on Zhelatin
Big trouble in little China
Kaspersky Lab analysts detected the first variants of Viking, a network worm, at the beginning of 2005. Initially, it was an unsophisticated program, and didn’t stand out from the crowd of other, similar programs. The worm copied itself to accessible network resources, infected files, attempted to download files from the Internet, and harvest user names and passwords for some online games.
Throughout 2005 Viking’s author wasn’t very active, releasing only one new variant of the worm approximately every two months. However, in April, with the release of Viking.h he became much more animated, and by September 2006 the number of known variants of this worm was more than 30. Then an epidemic which was comparable to those caused by Warezov in terms of scale broke out in China.
There were dozens of new Viking modifications being detected every week, with tens of thousands of Chinese Internet sites which were involved in spreading the worm, and multiple requests for help from Asian users. It very quickly became clear that we were dealing with a national epidemic.
It was Viking which caused China to take first place in terms of the number of malicious programs created by the country. And it was due to Viking that the class of network worms, programs which spread via local area networks, infect files, and which are normally small in number, experienced a significant increase in numbers (see the annual report for further details).
We encountered the next Chinese puzzle in winter 2007. A number of the new Viking variants differed so significantly from the original variant that we started classifying them as a new family: Fujack. This decision coincided with another outbreak. In January and February Fujack was the main problem for Chinese users, and information about the “panda virus” (so called because the icon for infected files would be changed to an icon showing a panda with a stick of bamboo) could be found on all major Asian news sites.
We need to take a short diversion, and ask the question: how did a non-email and non-network worm manage to spread in such huge quantities, and why exactly did this happen in China?
The main factors are as follows:
- In comparison to other countries, the Chinese segment of the Internet has a relatively high amount of file sharing.
There are thousands of servers in China which act as an enormous file storage. There’s no question that if piracy is the only way in which users are able to get hold of the programs that they want, such servers will be extremely popular. It’s likely that it’s possible to find any program that has ever been written on these servers. And if users are exchanging files, then one infected file on such a server would be enough to ensure tens of thousands of victims. The sites which we identified as being sites spread Viking and Fujack were, unsurprisingly, file sharing sites.
- The virus was spread by more than one person. Virus writers were involved in selling exclusive variants of Fujack designed to steal user data to online games. This contributed to the enormous number of variants and the several sources by which the worm was spread.
- The enormous size of local area networks, above all in Chinese universities. Once a virus gets into such a network, it would be able to very quickly infect thousands of computers with open network resources.
I think that this was an example of a very particular type of epidemic, which couldn’t have happened anywhere except China. And in spite of the number of infections, the virus wasn’t able to transcend national borders, and there was no significant number of infections in Europe or the US.
The result was one that we had hoped for, but not expected. On 12th February, the Chinese news agency Xinhua announced that the police had arrested several people who were suspected of being involved in the creation of Fujack. In total, 8 suspects were arrested, including the 25 year old Li Jun, who goes by the pseudonym WhBoy. Li Jun admitted that he had made approximately $12,500 from creating and selling the worm to other hackers, and that he started writing viruses because he could not find work in the IT sector.
According to some sources, this was the first case of a virus writer being arrested in China. I am not certain that it was the first case, but it’s certain that it was the first high profile arrest of a virus writer in China.
I searched our virus collection for malicious programs which contain the word WhBoy in their code – Li Jun’s signature. The resulting list is as follows:
- several dozen variants of Trojan-PSW.Win32.Lmir, a Trojan which steals accounts for Legend of Mir, an online game;
- several dozen variants of Trojan-Downloader.Win32.Leodon;
- all worms in the Email-Worm.Win32.Lewor family;
- a number of variants of Backdoor.Win32.WinterLove;
- several dozen variants of Trojan-PSW.Win32.Nilage, which steals user accounts to the online game Lineage;
- several dozen variants of Trojan-PSW.Win32.QQRob, a Trojan which steals QQ accounts (a Chinese instant messaging system);
- the Viking and Fujack worms.
If WhBoy is really the author of all these malicious programs, he could be seen as being one of the most active virus writers of the past decade.
There’s an interesting twist to all of this. The Chinese police demanded that Li write an antivirus which would clean computers infected by Fujack. He tried. But what he came up with wasn’t capable of restoring infected systems. The author of the virus couldn’t control his own creation – can you think of a more ironic situation?
The highs and lows of Vista
There’s no doubt that the release of Microsoft’s new operating system, Vista, onto the market at the end of January 2007 was a major event, not just for the antivirus industry but for the computer world as a whole. Microsoft announced that this latest version of its operating system would be the most secure in the history of Windows, and that many security issues which had caused virus epidemics in the past had been solved.
Questions about how secure the new operating system would actually be started circulating long before the release of the beta version. What exactly would the security functions be, and how effective would they be? Would it be true that Vista would make antivirus solutions redundant?
Questions about how secure the new operating system would actually be started circulating long before the release of the beta version. What exactly would the security functions be, and how effective would they be? Would it be true that Vista would make antivirus solutions redundant.
The list of key functions was impressive: User Account Control, Patch Guard (to protect the kernel) and security features in Internet Explorer 7, Address Space Layer Randomization, Network Access Protection, and Windows Service Hardening. In addition to all of this, Vista is equipped with Windows Defender, an integrated firewall and antivirus.
Information security professionals agreed that none of these innovations were likely to have a significant effect on computer viruses. Tests conducted by a number of antivirus companies showed that approximately 90% of malicious programs designed to run on Windows XP systems would be capable of functioning on Vista. And of course, the question of vulnerabilities in the new operating system would also be an issue.
In spite of Microsoft’s assurances that the new operating system would be developed almost from scratch, and that unprecedented steps would be taken to ensure security right from the start of the development process, and that a unique testing system had been successfully implemented, everyone was sure that there would be problems. It wasn’t so much a question of ‘Will critical vulnerabilities be identified in Vista?’ but rather, ‘When will they be identified?’
Vista was released for sale on 30th January 2007, and the race to find vulnerabilities was on. Hackers around the world focused their attention on Vista, searching for a zero-day exploit which could be used to create malicious programs.
Within two weeks, on 13th February, Microsoft released the latest bundle of patches. It included patches for six critical vulnerabilities and 6 important vulnerabilities, one of which was, as usual, vulnerability in Microsoft Excel. We’ve often written about the multiple vulnerabilities detected in Microsoft Office in 2006. In spite of all the patches which have been released, vulnerabilities continue to be identified and immediately exploited by malicious users.
However, the February patch bundle didn’t include a single vulnerability in Vista! This was a surprise, and could be viewed as confirmation that the new operating system is truly secure. However, there was one ‘but’. The vulnerabilities which were patched in February were detected prior to Vista’s release. Even if vulnerability had already been identified in Vista, it would not be patched in February. Consequently, we had to wait until March in order to get a true picture.
11th March came, and with it some surprising news. Microsoft announced that it would not be issuing any patches that month. This was the first time in several years that Microsoft did not release any patches – it could be seen as evidence that all problems in all versions of Windows had finally been fixed. However, the explanation that following the announcement showed that the situation was not quite that rosy. Microsoft was busy testing the patches which had been released the previous month. The software giant explained that it was continuing to invest both potential and already disclosed vulnerabilities in order to protect their customers. However, the statement continued, creating patches which fully resolve security issues is a long process made up of several steps. These words clearly meant one thing: there are known vulnerabilities, and it will take time to fix them. At the same time, eEye Digital Security announced that 5 unpatched vulnerabilities had been detected in Windows.
The situation was worrying. And after three weeks, the storm broke.
On 29th March 2007, antivirus companies noticed a strange program in among the flood of now-standard viruses. ANI format files (animated cursor files) had been found on a number of Chinese sites. When a user viewed these sites, a range of Trojan programs, mainly Trojan-Downloader programs, would be installed to his/ her machine.
In addition to that, email messages which contained the suspicious ANI files were also circulating. Analysis showed that they were connected to a new vulnerability in graphic files processing, which was present in Windows Vista.
This vulnerability was fought over for nearly two months. The struggle ended in the worst possible way – Chinese hackers used the vulnerability to spread viruses, and no patch was made available.
Even more worrying was the fact that two years ago there had already been issues connected to the processing of ANI files. Back in January 2005, hundreds of sites containing Exploit.Win32.IMG-ANI (this is the Kaspersky Lab classification) were detected. MS05-002 contained a patch for this hole; however, as time passed, it became clear that the patch had not been sufficiently tested. In addition to this, all the assertions that Vista had been written from scratch, that all the code had been repeatedly tested, and that such errors could not arise were negated by the appearance of these small vulnerable cursor files.
It only remained for Microsoft to release information about the new vulnerability, which was labeled CVE-2007-1765 and to provide a list of affected operating systems and applications. Meanwhile, antivirus companies were continuing to detect more infected sites and Trojan programs.
Websense detected more than 500 infected sites capable of infecting unsuspecting users in less than a week. The majority of incidents resulted in the victim machine being infected by several Trojan spy variants, which were designed to steal user data to online game accounts (World of Warcraft, Lineage).
It seemed that this problem might grow into a global epidemic. eEye Digital Security released an unofficial patch for the vulnerability. This was reminiscent of other cases, where Microsoft refused to release an out of schedule patch: for instance, December 2005, and the vulnerability in processing WMF files. Almost three weeks passed between the problem being detected, and a solution being provided. On the other hand, in September 2006, Microsoft only needed 10 days to release MS06-055, which patched a dangerous vulnerability.
This time Microsoft moved rapidly, and on 3rd April MS07-017 was issued in an out of schedule release. This vulnerability was described as ‘Vulnerabilities in GDI Could Allow Remote Code Execution’, and the number of affected operating system versions certainly made an impression.
- Microsoft Windows 2000 Service Pack 4;
- Microsoft Windows XP Service Pack 2;
- Microsoft Windows XP Professional x64 Edition and Microsoft Windows XP Professional x64 Edition Service Pack 2;
- Microsoft Windows Server 2003, Microsoft Windows Server 2003 Service Pack 1, and Microsoft Windows Server 2003 Service Pack 2;
- Microsoft Windows Server 2003 for Itanium-based Systems, Microsoft Windows Server 2003 with SP1 for Itanium-based Systems, and Microsoft Windows Server 2003 with SP2 for Itanium-based Systems;
- Microsoft Windows Server 2003 x64 Edition and Microsoft Windows Server 2003 x64 Edition Service Pack 2;
- Windows Vista;
- Windows Vista x64 Edition.
The list of vulnerabilities corrected by this patch was also impressive:
- GDI Local Elevation of Privilege Vulnerability (CVE-2006-5758);
- WMF Denial of Service Vulnerability (CVE-2007-1211);
- EMF Elevation of Privilege Vulnerability (CVE-2007-1212);
- GDI Invalid Window Size Elevation of Privilege Vulnerability (CVE-2006-5586);
- Windows Animated Cursor Remote Code Execution Vulnerability (CVE-2007-0038);
- GDI Incorrect Parameter Local Elevation of Privilege Vulnerability (CVE-2007-1215);
- Font Rasterizer Vulnerability (CVE-2007-1213).
Three of these vulnerabilities were present in Vista: EMF Elevation of Privilege Vulnerability, Windows Animated Cursor Remote Code Execution Vulnerability, GDI Incorrect Parameter Local Elevation of Privilege Vulnerability. Two of them had been identified back in 2006, but were only closed with the release of this patch!
Microsoft did, to some extent, explain how the company had been able to develop and release a patch which covered such a large number of vulnerabilities on the Microsoft Security Response Center Blog:
“I’m sure one question in people’s minds is how we’re able to release an update for this issue so quickly. I mentioned on Friday that this issue was first brought to us in late December 2006 and we’ve been working on our investigation and a security update since then. This update was previously scheduled for release as part of the April monthly release on April 10, 2007. Due to the increased risk to customers from these latest attacks, we were able to expedite our testing to ensure an update is ready for broad distribution sooner than April 10.”
So: Microsoft had known about the problem since December the previous year, and had spent the intervening period testing; it decided not to release the patch as part of the March cycle, but to wait until April, although the patch was actually released prior to the scheduled date. The vulnerability had been known about, both by Microsoft and the computer underground, for more than three months…We can only guess how many hacker attacks took place during this period.
This case clearly showed that Windows Vista is no different from previous version of Windows as far as vulnerabilities go. It also showed that all of Microsoft’s innovations, both in terms of program security and in terms of flawless code were not all that they were cracked up to be. And finally, it showed that zero-day vulnerabilities, which are exploited by virus writers before an official patch can be released, are still a serious issue.
Conclusion
The events of the first three months of 2007 confirmed our worst fears. Virus writers are still continuing to organize multiple short term epidemics by releasing numerous variants of a single malicious program onto the Internet in a short space of time. Naturally, this makes life more difficult for antivirus companies. Vista became a target for hackers, who were not only searching for vulnerabilities, but also for ways to evade some of the security features such as UAC, Patch Guard, and protection against buffer overflows.
The second quarter of the year will undoubtedly confirm trends. It will also give clear pointers as to how secure contemporary operating systems actually are, and which new methods malicious users are choosing to conduct their attacks.



















Malware Evolution: January – March 2007