
According to Wikipedia QR code is a type of matrix barcode (or two-dimensional code) first designed for the automotive industry. QR codes are becoming more and more popular today and are used in banners, magazines, transport and badges in order to provide quick and easy access to particular information. A QR code has a pretty big capacity (compared to a simple barcode) and is able to store 7089 numeric characters or 4296 alphanumeric characters; and it is more than enough to store text or URL.
But about the malicious QR codes? Yes, you scan a QR code with the help of your smartphone and it redirects you to a URL with a malicious file (APK or JAR). Such QR codes exist and are gaining in popularity.
Today people who use smartphones often look for new software for their devices with the help of desktop PCs. If a user finds something interesting he or she must retype the application URL in the smartphone browser for downloading it. It’s not very convenient so that’s why such websites have QR codes which can be easily scanned.
It is known that today a lot of mobile malware (especially SMS Trojans) is spread via sinister websites where all software is malicious. And cybercriminals have started to use malicious QR codes for users’ ‘convenience’. Here is an example of such a website:

Part of the website with malicious QR code
It is interesting to mention that the blurred URL is working but there is no ‘jimm.apk’ file associated with this link. But if a user scans the QR code he will be redirected to another URL that does have a ‘jimm.apk’ file. This file is detected by us as Trojan-SMS.AndroidOS.Jifake.f:
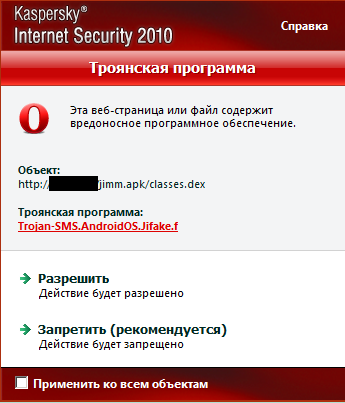
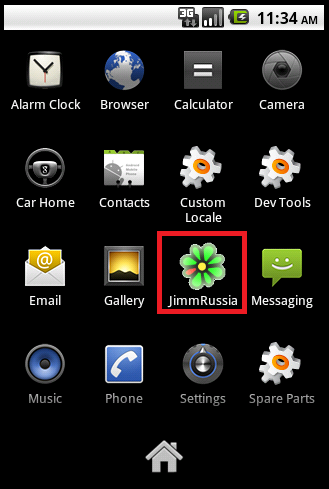
The malware itself is a Trojanized Jimm application (mobile ICQ client) which sends several SMS messages to premium rate number 2476 (6 USD each). After the installation an icon named ‘JimmRussia’ will appear in the phone menu.
Trojan-SMS.AndroidOS.Jifake.f
At the same time other websites also contain malicious QR codes with the links to various J2ME SMS Trojans:

Another website with malicious QR code
Usage of QR codes for malware spreading was predictable. And as long as this technology is popular cybercriminals will use it. These two examples illustrate the very beginning of such usage and in the nearest future likely we will see more pieces of mobile malware which is spread via QR codes.





















Malicious QR codes pushing Android malware