
My colleagues Fabio Assolini and Vicente Diaz wrote two blog posts recently regarding the Rogue AVs for MAC OSX. After executing it on a test machine, and playing with it, I noticed there was some hidden information in the About Window as can be seen below:
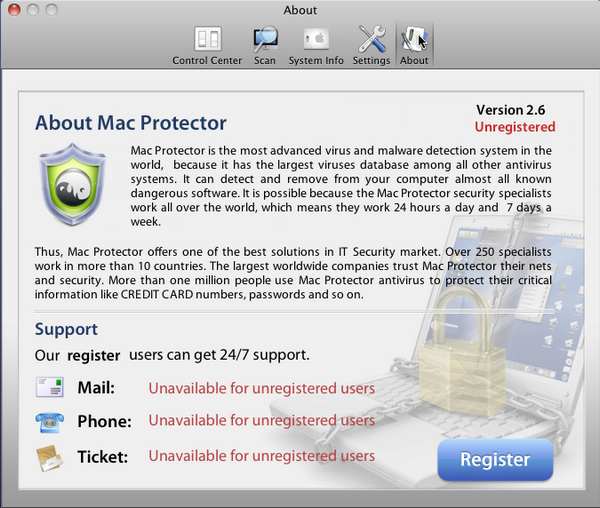
I was interested by the “Support” information, but it’s only available to registered customers.
I also wanted to confirm a few things such as the “cleaning” of the fake threats once registered, and to see if the “infected” popups would stop.
I decided to start examining the Rogue AV binary under IDA Pro. The malware is a MAC OS file, uses intel assembly and Objective-C.
After a quick look in the function names, I found something interesting: __RegEngine_CheckKey__.
This function name was the first one I checked, and I found the following code:
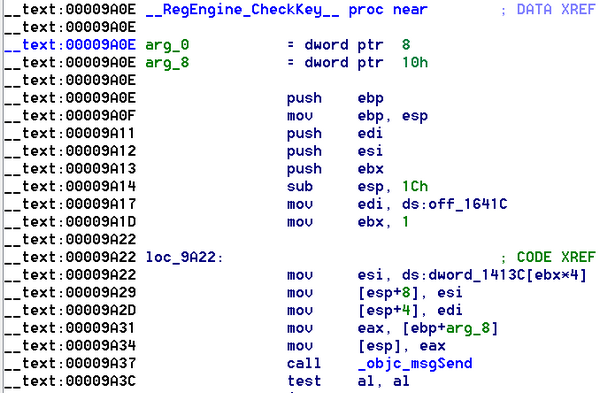
The first thing I noticed is an array starting at Dword_1413C. I moved my mouse over within IDA and the first value is 0 and nothing else was showing up. However, the index is set to one (EBX) which made me realize I should have a look onto that array to see the real interesting content. Here is what I had:
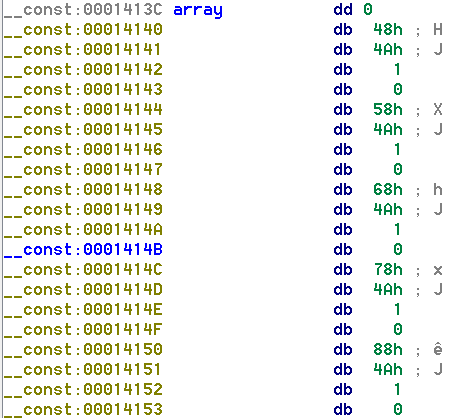
As you can see, the first dword is set to 0, hence IDA only showing that. Trained eyes however, quickly realize the other dwords are in fact addresses within the program. (All start with 0x14 like the current array address for instance).
Within IDA, it’s possible to make offsets out of those dwords , which I did, and here is what appeared:
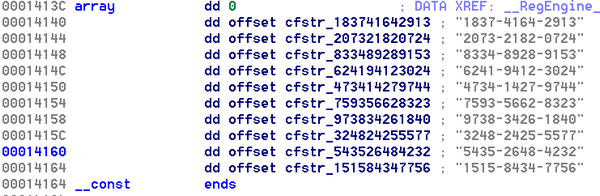
The full hardcoded list of serials showed up.
I had a look into the About window in order to see if they really provide Support information to registered customers and indeed they do:
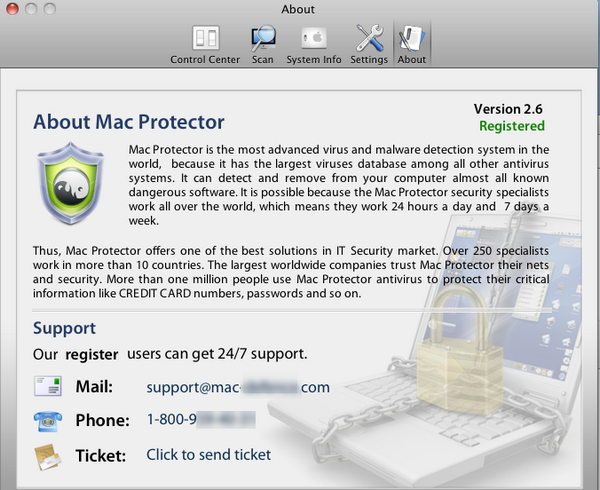
I decided to try to “clean” my infected system now that I registered it, and it started deleting the discovered threats (fake ones obviously). The Fake product indeed looks like it works as expected; tricking the users into thinking it is a real AV Program:
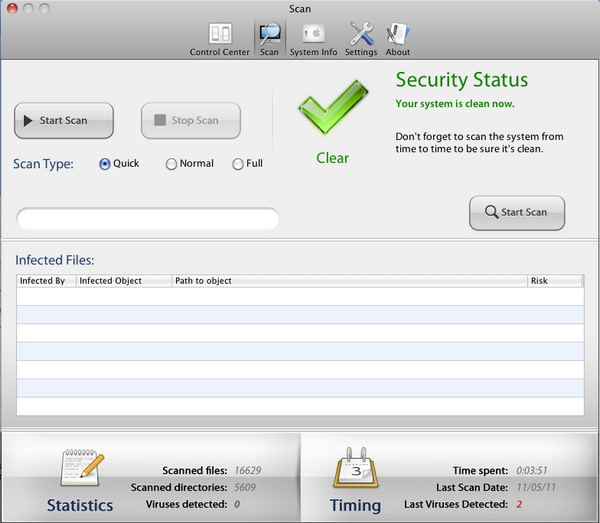
You can use any of those serials to register the Rogue AV Product in order to stop the Warnings that get flooded on your screen, which is really annoying. Once this is done, you are free to install an Anti Virus solution for your Mac and clean it properly.
For your convenience, here are the serials you can copy paste into their Fake Product:
|
1 2 3 4 5 6 7 8 9 10 |
1837-4164-2913 2073-2182-0724 8334-8928-9153 6241-9412-3024 4734-1427-9744 7593-5662-8323 9738-3426-1840 3248-2425-5577 5435-2648-4232 1515-8434-7756 |
As a conclusion, I want to say that this Rogue AV is actually well designed and all the usual “Clean after payment” process is actually implemented and working.
They really want the victim to think the product is working in order to get them to renew their solution in the future.






















Mac Protector: Register your copy now!