
The year in figures
According to Kaspersky Lab, in 2014
- The proportion of spam in email flows was 66.76%, which is 2.84 percentage points lower than in 2013
- 74.5% of spam emails were no more than 1 KB in size
- 16.71% of spam was sent from the USA
- Users in the USA were targeted by 9.8% of malicious emails, the largest share of any country
- 260, 403,422 instances that triggered the “Antiphishing” system were recorded.
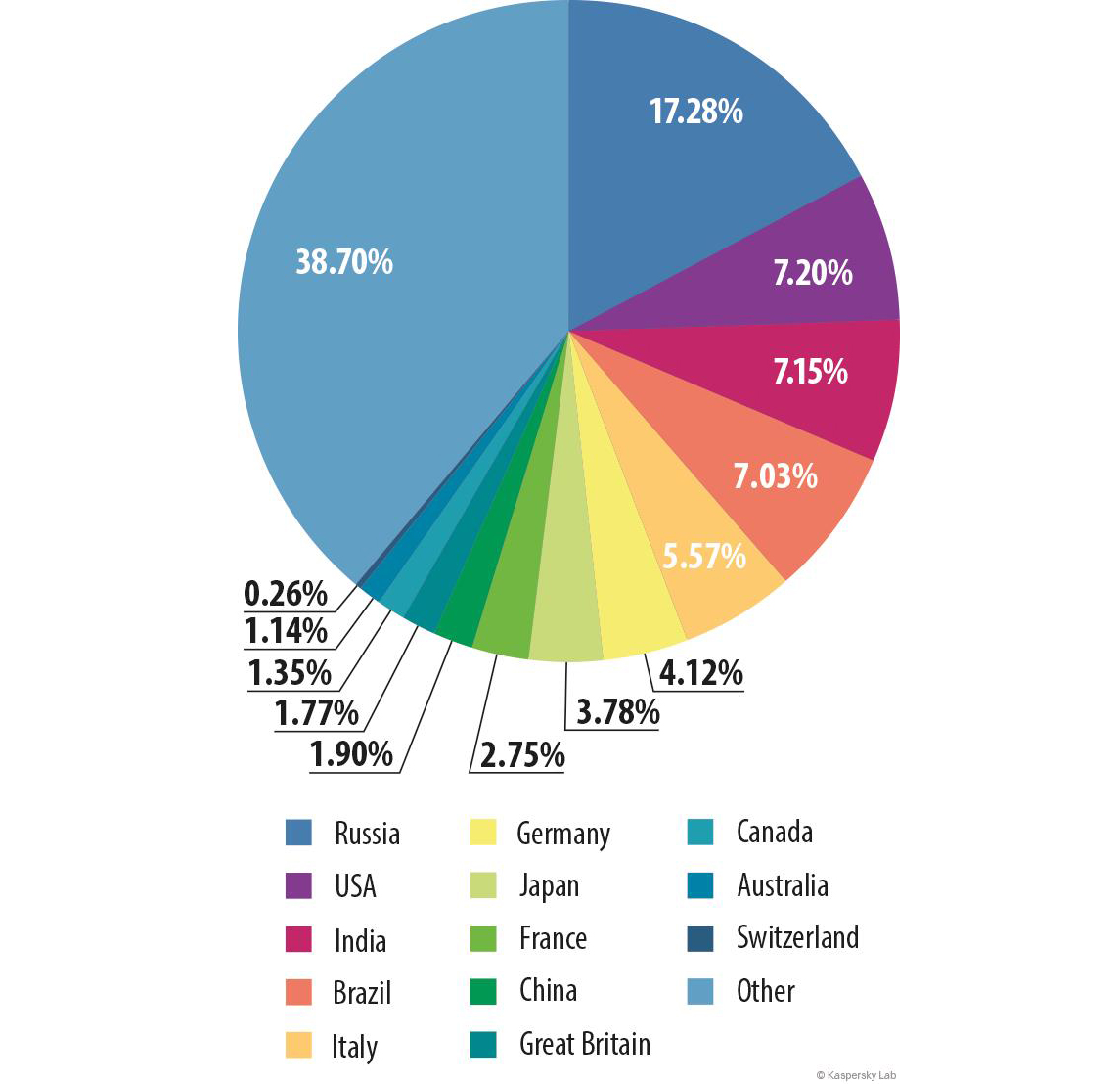
- Brazil had the highest proportion of people attacked by phishers – 27.47% of all Kaspersky Lab users in the country faced at least one attack
- Russia suffered the highest number of total phishing attacks, with 17.28% of the global total
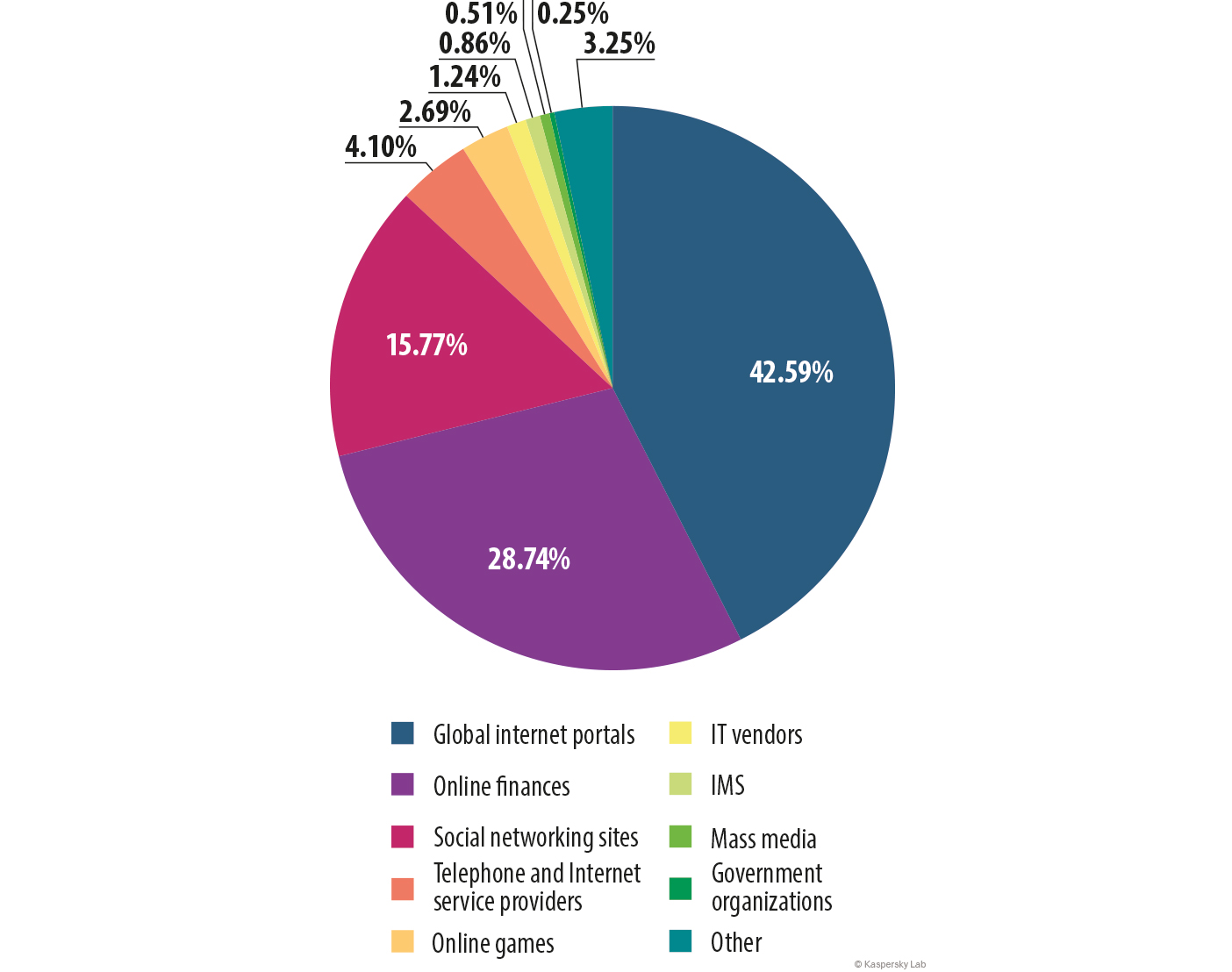
- 42.59% of phishing attacks targeted global portals that integrate many services accessed from a single account.
Popularity of mobile devices and spam
The popularity of mobile devices continues to grow, and this is affecting spam in email traffic: the number of advertising services that will spread spam on mobile devices is increasing, as are the number of offers addressed to the spammers who profit from these mailings. The popularity of mobile devices also makes them a valid vector for cyber-attack: email traffic now includes malicious imitations of emails sent from smartphones as well as fake notifications from popular mobile applications.
Adverts from/for “mobile” spammers
In 2014, spammers intensified their offers to distribute ads via SMS and popular IM services (WhatsApp, Viber, etc.). They use traditional spam mailings to help search for new customers, and the number of these adverts is also increasing.
Current email traffic also includes adverts addressed to “mobile” spammers: they are offered ready-made databases of phone numbers and other contact information that is designed to attract a specific target audience. These databases, in turn, are often generated with the help of mass mailings: the spammers send phishing emails which they use to collect personal data from victims.
Imitations of emails sent from mobile devices
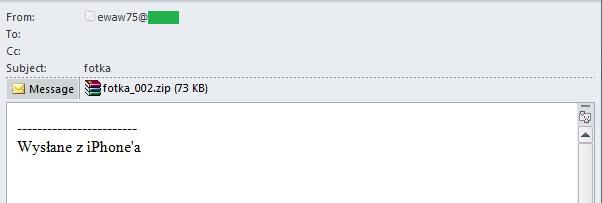
Spam mailings simulating emails sent from mobile devices have become very popular. We came across such emails written in several languages; they mentioned iPad, iPhone, Samsung Galaxy and other models. These messages had one thing in common – short (sometimes non-existent) text and a signature reading “Sent from my iPhone”. Typically, they contain links to phishing sites or malicious attachments.
Apparently, spammers think that an email with the attached file and a signature allegedly sent from the iPhone looks reliable. Indeed, the emails sent from mobile devices rarely use a complex template. And the senders often prefer to attach a file or insert a link rather than write a long text on the smartphone.
In some cases, the emails included an archive named to suggest it contained a photo. In fact, this was yet another way to distribute malware.
The emails sent allegedly from mobile devices often contained advertising links – most often to the sites illegally selling medications. Below is the example of one of these emails where the spammers used a few key words as the text of the message.
In order to bypass filtering, spammers often try to forge technical headers of the emails (Data, X-Mailer, Message-ID) to make them look like they were sent from mobile devices. However, when checked, the content of these headers is defined as incorrect.
Fake notifications from mobile applications
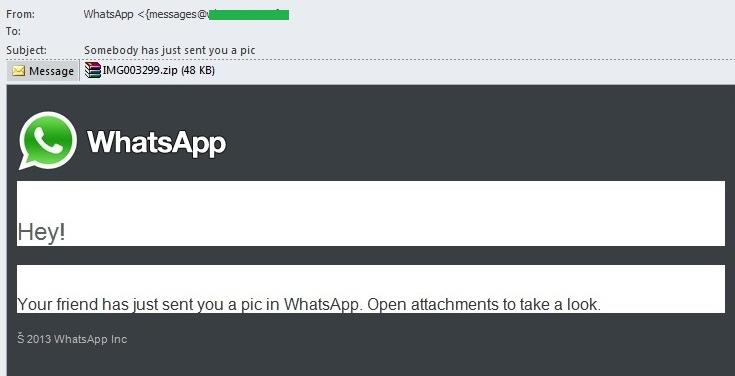
The widespread use of mobile devices has given rise to yet another phenomenon – spam that imitates notifications from different mobile applications such as WhatsApp and Viber. Users are accustomed to the synchronization of cross-platform applications, to the synchronization of contact data between applications and to different notifications from them, so many mobile device owners don’t think twice about an email saying a message has allegedly arrived on their mobile messenger. This is a mistake: these mobile applications are not related to the user’s email account in any way, which means that these emails are obviously fake.
For example, there can’t be emails telling users that they’ve received an image via WhatsApp because registration on WhatsApp does not require an email address.
Moreover, the “picture” is packaged in an archive, which should also arouse suspicion: packaging an image does not offer any advantage while archives are often used to hide malicious attachments. And this is what we see in this case: the archive contains a malicious program.
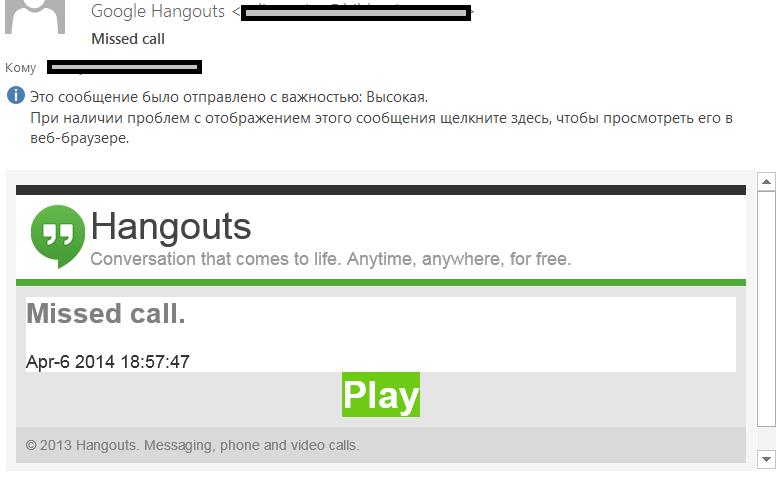
Yet another example: a notification about a voice message allegedly sent via Hangouts contains a hyperlink disguised as the “Play” button. After clicking “Play”, instead of hearing the voice message the user is sent to a compromised legitimate site from which integrated JavaScript redirects him to an advertising page.
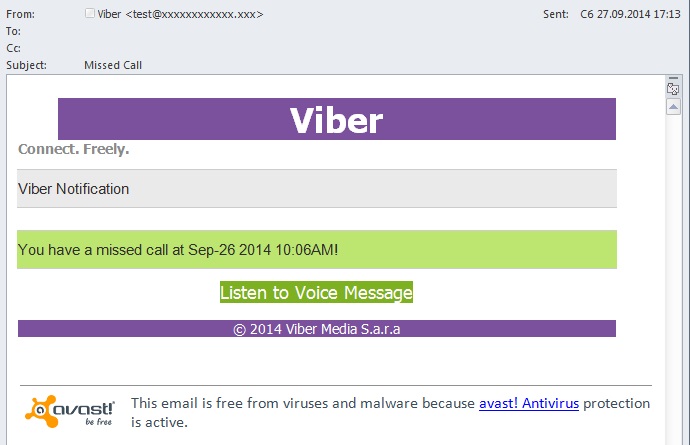
The notification of the voice message supposedly sent via Viber contains a “Listen to Voice Message” button that initiates the download of a malicious archive.
World events in spam
2014 was rich in global events: the crisis in Ukraine, the Ebola epidemic, the Olympics in Sochi and the FIFA World Cup in Brazil. Each of them was used by the spammers to draw attention to their mass mailings.
The Olympic games and the World Cup
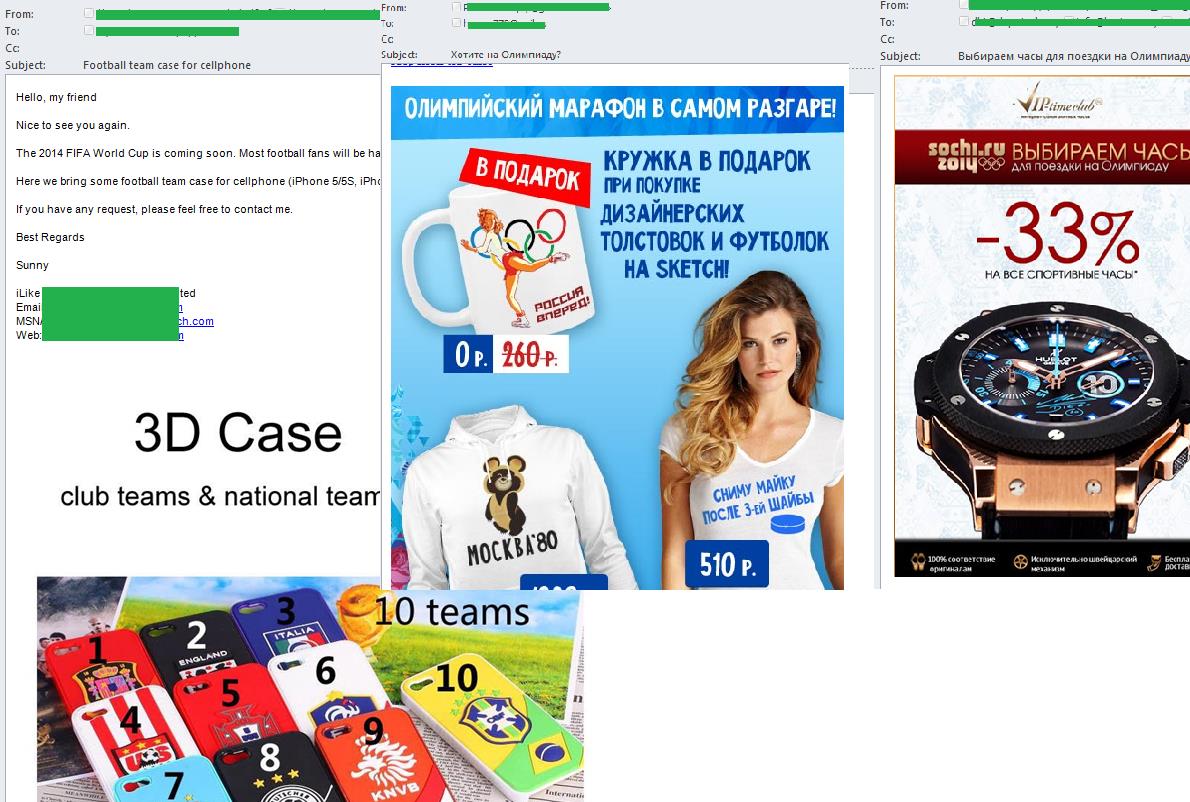
The Sochi Olympics and the FIFA World Cup in Brazil were the only sporting events that featured in spam flow. In both cases the majority of spam emails were written in the language of the country where the event took place, suggesting that the fraudsters’ main targets were the locals.
The spam sent out shortly before these events contained a lot of mass mailing advertising products with the symbols of the tournament. In the case of the Olympic Games, in addition to Sochi merchandise the adverts offered products harking back to the 1980 Moscow Olympics.
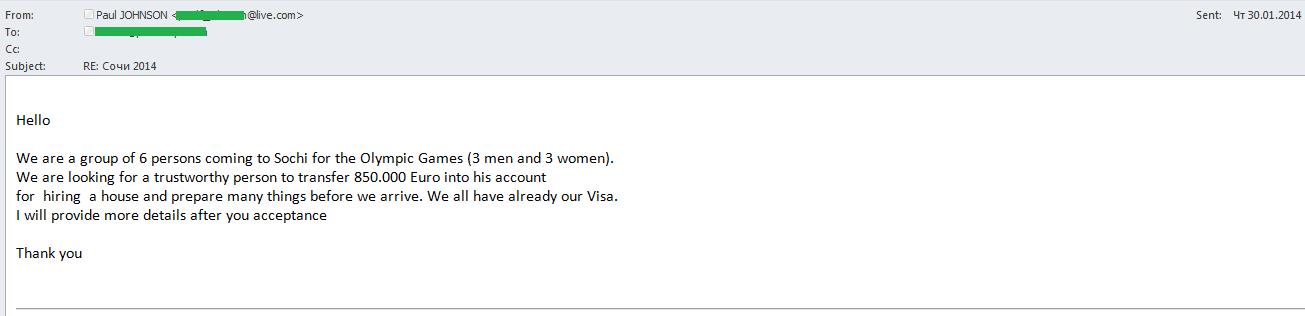
“Nigerian” scammers also got involved. Before the Olympics they sent emails on behalf of the fans who asked for assistance in renting accommodation in Sochi or paying for various services. The “sports fans” were allegedly ready to transfer 850,000 euro to a person who would help them. The promise of a big reward was designed to encourage victims to overlook a few preliminary costs, but once the requested money was transferred the fraudsters disappeared without delivering the promised cash and rewards.
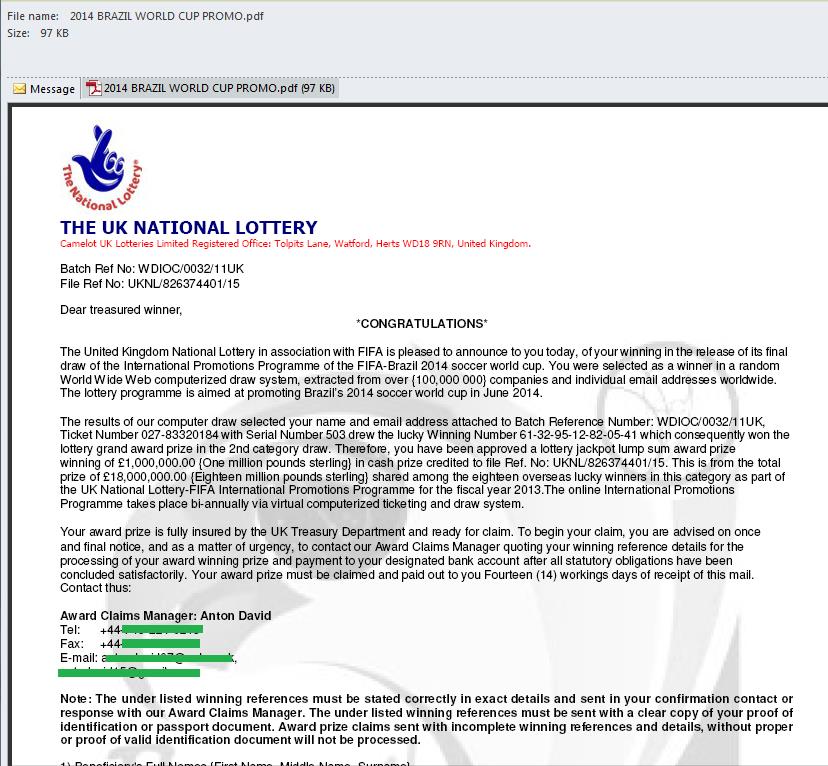
We also saw many fraudulent emails informing recipients that they had won an official FIFA World Cup lottery. Of course, to get his money, the ‘winner’ faced a few minor preliminary expenses. But, of course, these so-called winners would never see any money from a competition that they had never entered in the first place.
Similar emails are constantly sent out in the run-up to the big football championships.
Besides real adverts and fraudulent messages the pre-World Cup spam also contained malicious emails with links that allegedly led to websites where fans could buy tickets to the games.
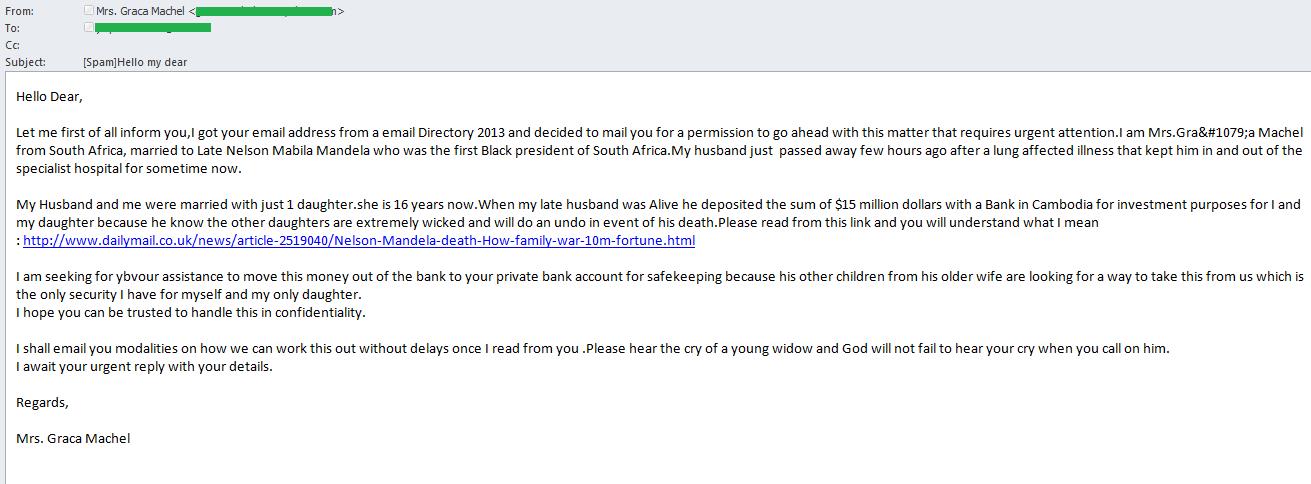
Nelson Mandela’s demise
Obviously, “Nigerian” scammers do not grieve for the demise of political leaders; for them these events are the ideal pretext to spin stories of a multi-million dollar will. Nelson Mandela’s death in late 2013 unleashed a wave of “Nigerian” spam. The attackers introduced themselves as representatives of different funds and informed the recipient that he had been awarded a Mandela prize; the “bankers” offered to secretly divide the Mandela family’s money, etc. In some cases, the emails contained the links to real news releases, hoping that this would make the message look more reliable.
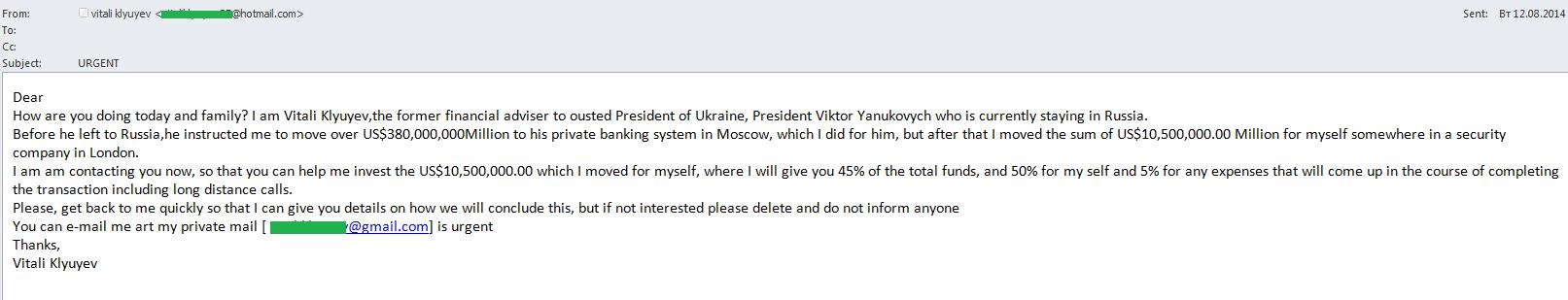
Political events in Ukraine
Unstable political situations and military conflict is yet another source of inspiration for “Nigerian” spammers. We regularly come across mass mailings exploiting conflicts in different countries, mostly in the Middle East, but in 2014 the “Nigerian” scammers focused on Ukraine. The authors of fraudulent emails posed as the disgraced Ukrainian politicians and entrepreneurs looking for a way to smuggle their millions out of the country. There were also mass mailings written on behalf of Russian businessmen who had suffered due to sanctions.
Traditionally, “Nigerian” letters offered the recipients huge money for their help. Meanwhile, if victims entered into correspondence, the scammers conned money from them to cover different alleged expenses – duties, taxes, air tickets, hotel rooms and so on.
The Ebola virus
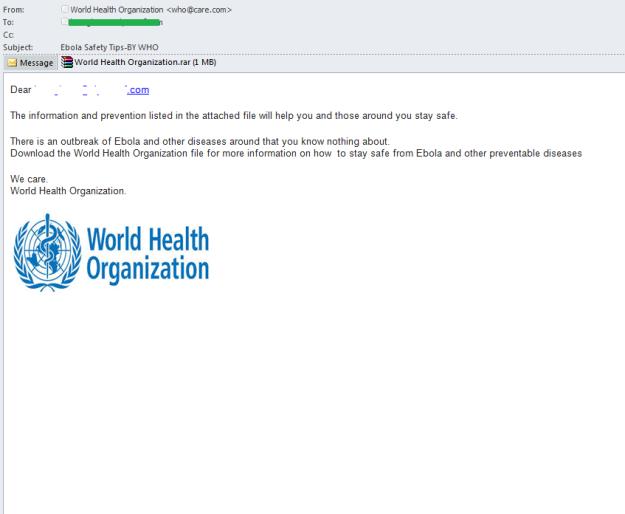
The Ebola epidemic also attracted the attention of spammers. “Nigerians” sent out emails on behalf of infected Africans who allegedly wanted to leave their fortune to charity. The fraudsters came up with a new twist on the story which invited recipients to participate as a guest at a World Health Organization conference. The proposed fee was 350,000 and a car for the job as a WHO representative in the UK.
Malware distributors exploited people’s fear of this deadly disease and sent out emails on behalf of the WHO which contained a link to information on the measures to prevent Ebola infection. Later, the emails with the similar content appeared but this time the “information from the WHO” was packed in an attached archive.
In reality both the link and the attached archive contained a malicious program designed to steal the victim’s data. In the above email it was Backdoor.Win32.DarkKomet.dtzn.
Spammer tricks
The techniques that have been actively used by the spammers in recent years can be called “classic”.
One well-known spammer trick is the stock spam advertising shares of small companies. These emails are part of a stock fraud scheme, the so-called pump and dump spam. The idea is simple: the fraudsters buy cheap stock then send out email mailings advertising the chance to buy stock in a certain company at super low prices, taking advantage of the sharp rise in value expected in the near future. As a result, demand for the stock in the company rises, the prices are artificially inflated and the scammers sell off their stock in the company at a tidy profit. This fraud peaked in 2006-2007 but stock spam is still in use today.
According to Kaspersky Lab, 74.5% of #spam emails sent in 2014 were smaller than 1 KB in size #KLReport
Tweet
In 2013, stock spam only contained a brief text showing the current and expected share price of the company. Some mass mailings included an auto signature which promised that an anti-virus scan had been deployed. Moreover, the language of the signature matched the language of the geographical domain which hosted the recipient’s e-mail (this common technique seeks to persuade the recipient of the legitimacy and security of the email). To enhance the chances of bypassing spam filters, the name of the company in a mass mailing was usually “noised” with the “_” symbol or gaps, and the text fragments varied.
In 2014, the design of fraudulent mass mailings advertising company shares changed – the spammers made the messages look more reliable. To bypass spam filters, they used some well-known tricks:
- Graphic spam. The advertising text is located within the picture and company logos are used. In a single mass mailing the content, color, font size or background color of the picture can vary. (Note that modern spam filters have long used graphic analyzers that can easily detect graphic spam)
- Junk text is inserted at the end of each message and is designed in different colors which do not always match the background. Fragments from literary works and quotes from Wikipedia are used. It is assumed that this method will make each email unique and cause spam filters to detect them as fragments of a literary work rather than a spam message.
Apparently, spammers are trying to compensate for their archaic methods with large volumes – hundreds of millions of these fraudulent emails are sent out.
However, spammers often use more advanced techniques to create “background noise” in the text. For example, they can “noise” the main text of the message even without affecting the readability of the message. To do this, HTML tags are used. The opening and closing tags are inserted into the main text of the message in HTML code. As a result, the user sees no changes in the message but the spam filter detects each email as a unique.
Statistics
The proportion of spam in email traffic
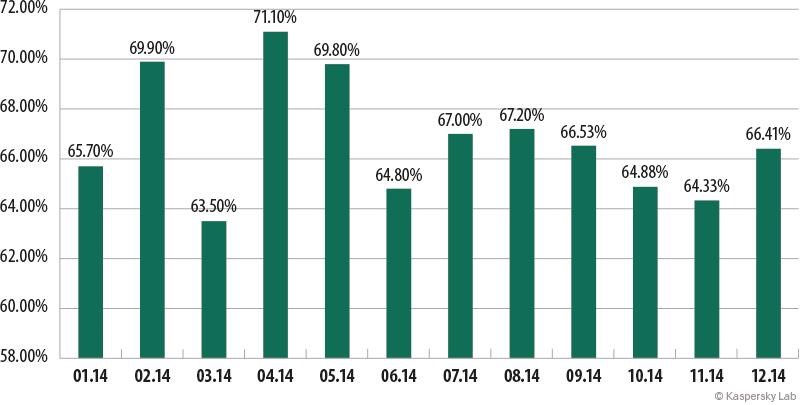
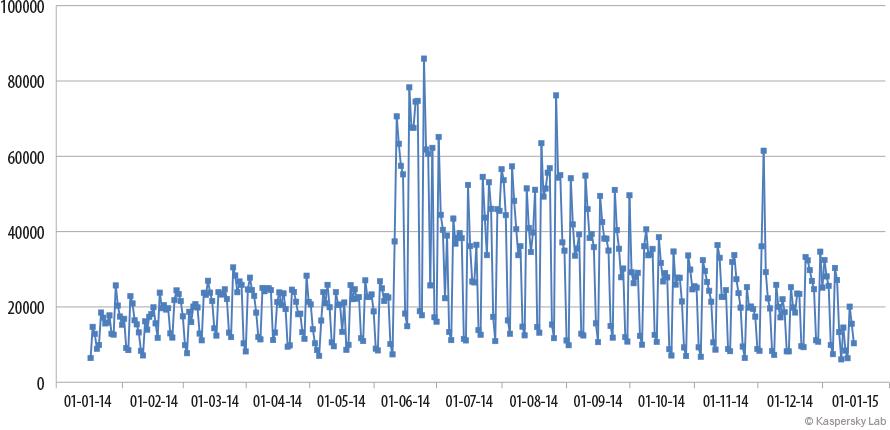
In 2014, the proportion of spam in email traffic was 66.76%, which is 2.84 percentage points lower than in the previous year. Spam levels have fallen consistently from a peak of 85.2% in 2009. This is due to the fact that adverts for legal goods and services are abandoning spam in favor of more effective legal advertising platforms.
The proportion of spam in email traffic, 2014
In 2013 the share of spam in email traffic showed almost no variation from month to month but in 2014 there were some noticeable fluctuations, especially in the first half of the year. The lowest value of the year (63.5%) was registered in March. However this was immediately followed by the highest monthly figure of 71.1% in April. The second half of the year was more stable.
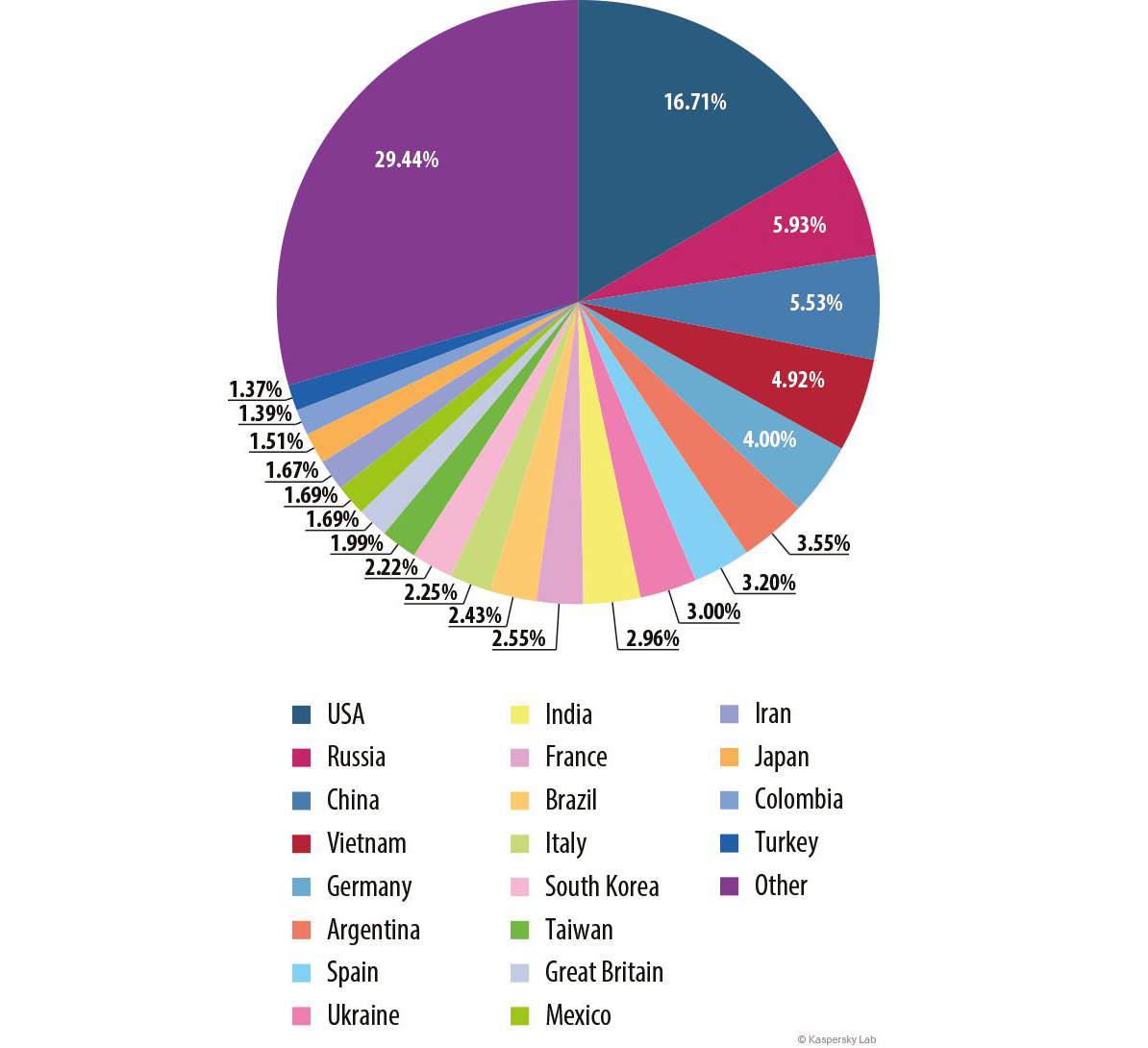
Sources of spam by country
Sources of spam by country, 2014
In 2013 China was the undisputed leader among the spam source countries. However in 2014, the percentage of unwanted mail originated from this country dropped by 17.44 pp. As a result, China fell to 3rd in the annual rating, overtaken by the USA (-1.08 pp) and Russia (+1.98 pp).
The Top 10 sources of spam include three western European countries: Germany (+2.79 pp), Spain (+2.56 pp) and France (+2.33 pp). Two Asian countries – South Korea (-10.45 pp) and Taiwan (-3.59 pp) – which occupied 3rd and 4th positions in 2013 moved down to 13th and 14th places respectively in 2014.
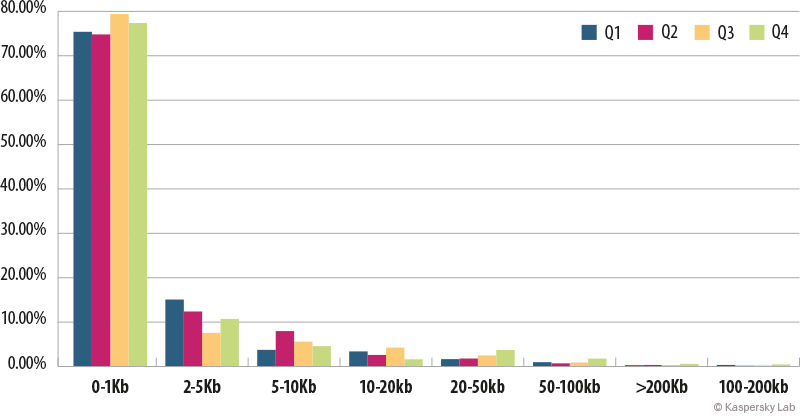
The size of spam emails
The size of spam emails in 2014
The number of super-short spam emails is growing: in 2014 77.26% of spam emails weighed in at under 1 KB, 2.76pp more than in 2013.
These emails usually contain links to advertising websites. To generate the text of the email the spammers use robots that combine short phrases from several words taken from thematic dictionaries, or change the words in the message for synonyms. In the end they get unique messages, making the task of spam filters more difficult. The small size of the emails also helps spammers to reduce traffic costs.
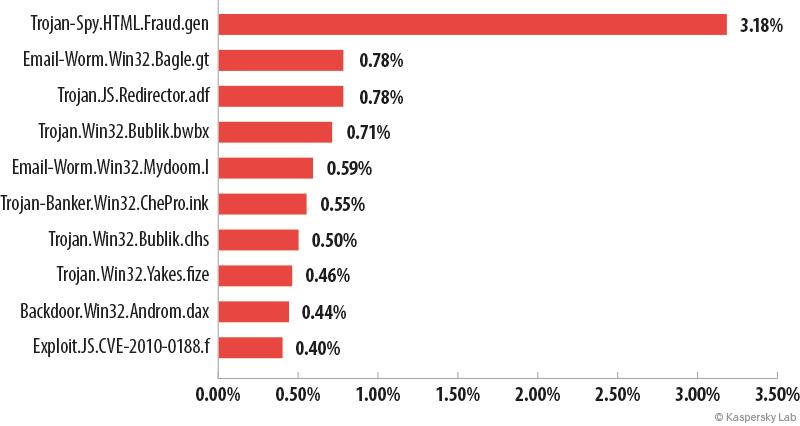
Malicious attachments in email
For the fourth year in a row the most widespread malware in emails were programs that attempted to steal confidential data, usually logins and passwords for Internet banking systems.
The Top 10 malicious programs spread by email in 2014
Trojan-Spy.HTML.Fraud.gen topped the rating again. It is generally distributed using phishing emails and is designed to look like an html page where users are invited to enter their confidential data.
Email-Worm.Win32.Bagle.gt is in second place. The main functionality of all email worms, including Bagle, is to collect electronic addresses from compromised computers and to send copies of itself to all email addresses found on an infected computer. Bagle email worms can also receive remote commands to integrate with other malicious applications.
#Spam levels have fallen consistently from a peak of 85.2% in 2009 to 66.76% in 2014 #KLReport
Tweet
Third came Trojan.JS.Redirector.adf, which was the most widespread malware in Q3. The malware spreads via email in a passwordless ZIP archive. It appears as an HTML page with an integrated script which, when opened by users, redirects them to an infected site. There it usually offers to load Binbot — a service for the automatic trading of binary options, which are currently popular on the net.
Representatives of the Bublic family occupy 4th and 7th positions in the Top 10. Their main functionality is the unauthorized download and installation of new versions of malware onto victim computers. They often download a ZeuS/Zbot modification. The Trojans of the Bublic family appear as EXE files but use the Adobe document icon to mislead the victim.
Email-Worm.Win32.Mydoom.l is in 5th place. This network worm with a backdoor functionality is spread as an email attachment via file sharing services and writable network resources. It harvests email addresses from infected computers so they can be used for further mass mailings. The worm also enables attackers to remotely control the infected computer.
In 2014, the proportion of spam in email traffic was 66.76% #KLReport
Tweet
Trojan-Banker.Win32.ChePro.ilc. ended the year in sixth position. This downloader appears as a CPL applet (a component of the control panel) and, as is typical for this type of malware, it downloads Trojans developed to steal bank information and passwords. These banking Trojans mainly target online customers of Brazilian and Portuguese banks.
Eighth isTrojan-Downloader.Win32.Dofoil.ea. This Trojan downloads other malicious programs onto the victim computer to steal various user information (mainly passwords) and send it to the fraudsters.
Backdoor.Win32.Androm.daxcame 9th. This malicious program belongs to the Andromeda/Gamarue family of universal bot modules. The main features of these malware programs are the ability to download, store and run executable files, downloading and loading DLL (without saving on disk), downloading plugins and the ability to update and delete themselves. The bot’s functionality is enhanced with a system of plugins that can be downloaded by the cybercriminals whenever necessary.
Exploit.JS.CVE-2010-0188.f rounds off the Top 10. This particular exploit appears as a PDF file and uses a vulnerability in version 9.3 and lower of Adobe Reader. This vulnerability has been known for a long time and poses no danger to users who update their software regularly. However, when it encounters an old version of Adobe the exploit downloads and runs the executable file Trojan-Dropper.Win32.Agent.lcqs. The dropper installs and runs the malicious script Backdoor.JS.Agent.h, which collects information about the system, sends it to the attackers’ server and receives various commands in response. The commands and the results of their execution are transmitted in an encrypted form.
The Andromeda family remains the most widespread malware family. It accounted for 11.49% of all malware detected in malicious attachments. These programs allow the attackers to secretly control infected computers, which often become part of a botnet.
Second came ZeuS/Zbot (9.52%), one of the most popular and widely-available programs designed to steal banking information and, as a consequence, users’ money. This program is often downloaded on to a victim computer by loader programs distributed via spam mailings.
Bublik (8.53%) completes the Top 3. This is a family of malicious loader programs that downloads modifications of the Zeus/Zbot family onto a compromised computer.
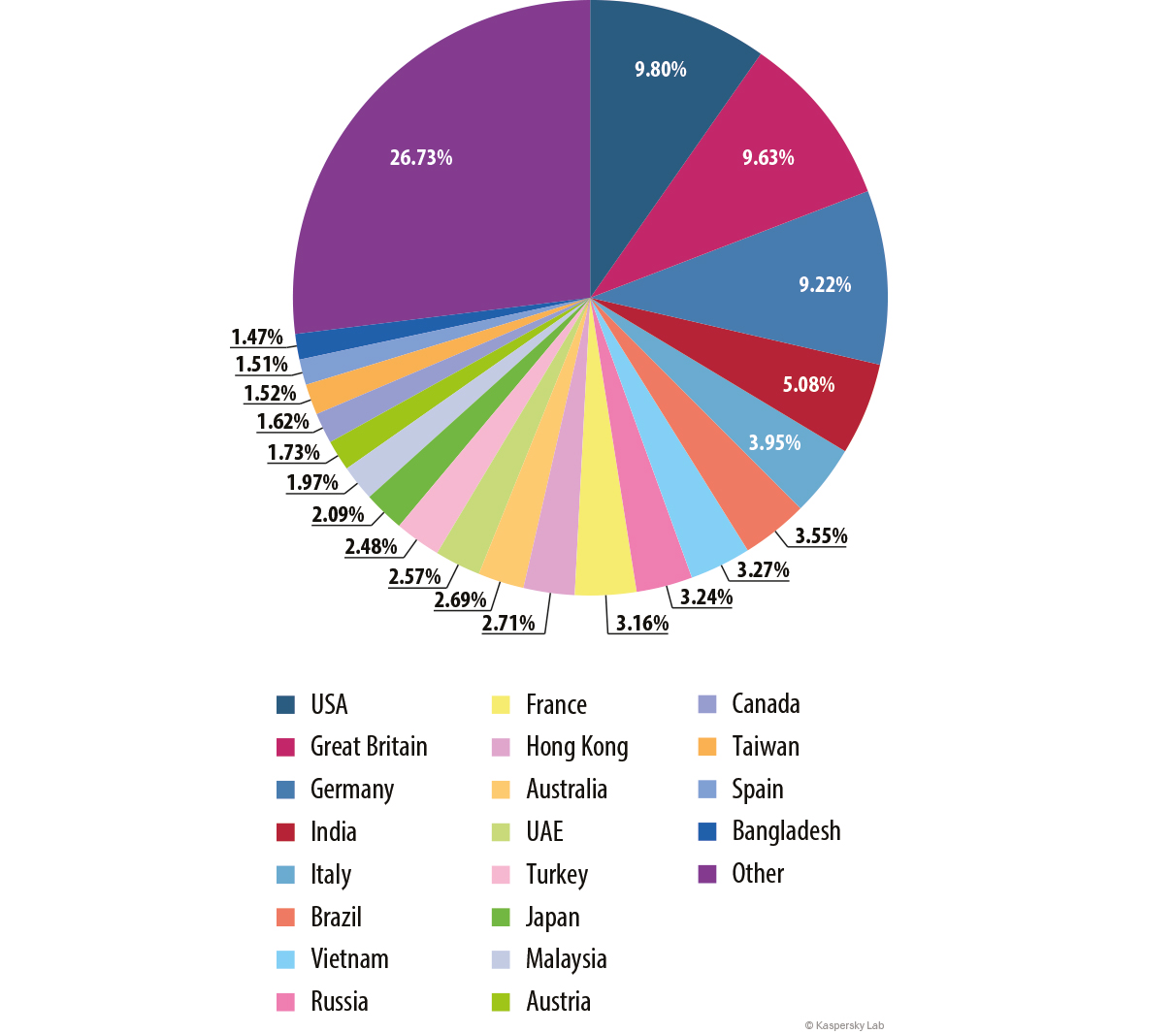
Countries targeted by malicious mailshots
Distribution of email antivirus activations by country, 2014
For the third year in a row the Top 3 countries most targeted by malicious mailshots remains unchanged: the US, the UK and Germany. The USA (9.80%) maintained its leading position despite the 2.22 pp decrease in the number of antivirus activations. Britain came second with 9.63% (-1.63 percentage points). Germany was third with 9.22%.
Of special note is France (3.16%) which climbed from 16th to 9th position in the rating.
Russia (3.24%) occupied 8th place, one position up from the previous year.
Spammers’ tricks
In 2014, spammers had a mix of old and new distribution tricks to lure in users.
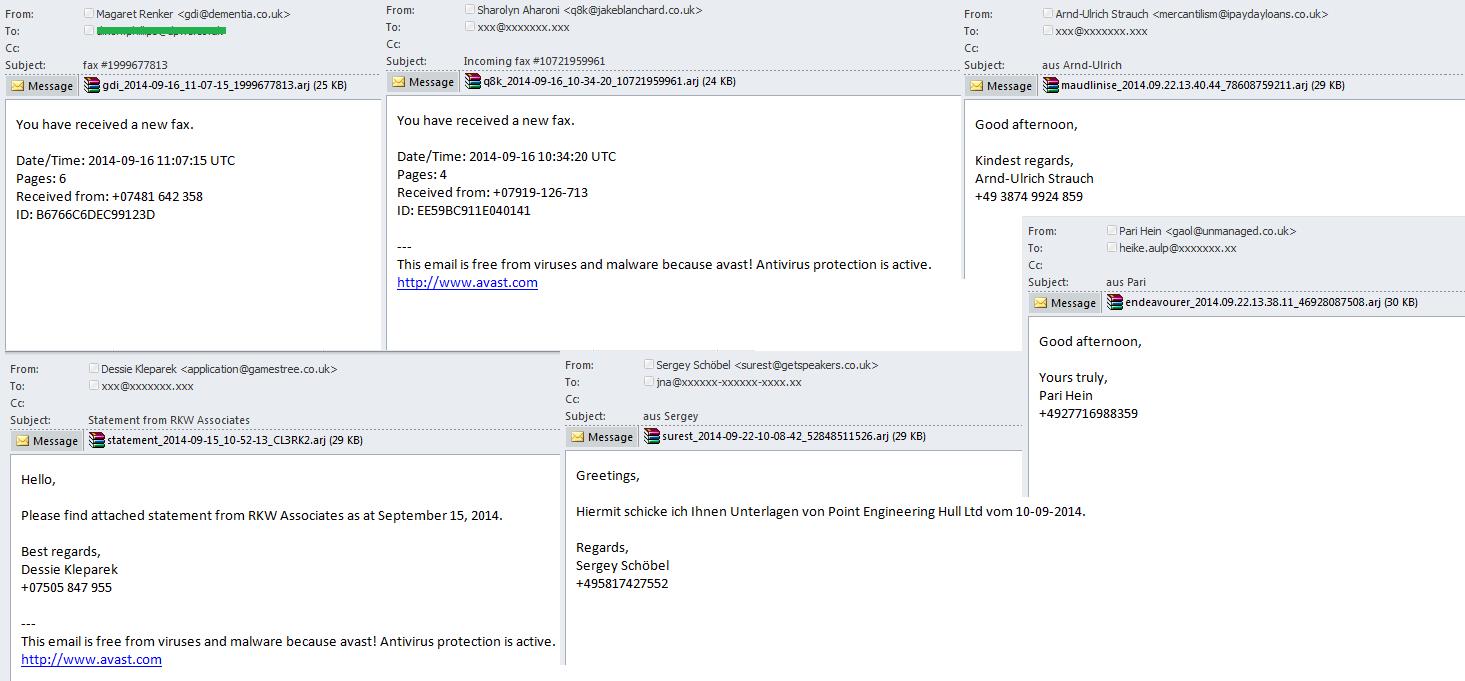
We came across emails containing attached archives with the .arj extension. This format was introduced long ago and is rarely used now. Therefore, even users who are wary of attached archives do not always recognize this attachment as potentially dangerous. The ARJ archiver has a further advantage as it can reduce file sizes to the minimum.
In addition to nonstandard archives, spammers also sent out malicious emails containing files with unusual extensions for attachments, such as .scr. This extension usually denotes a screensaver.
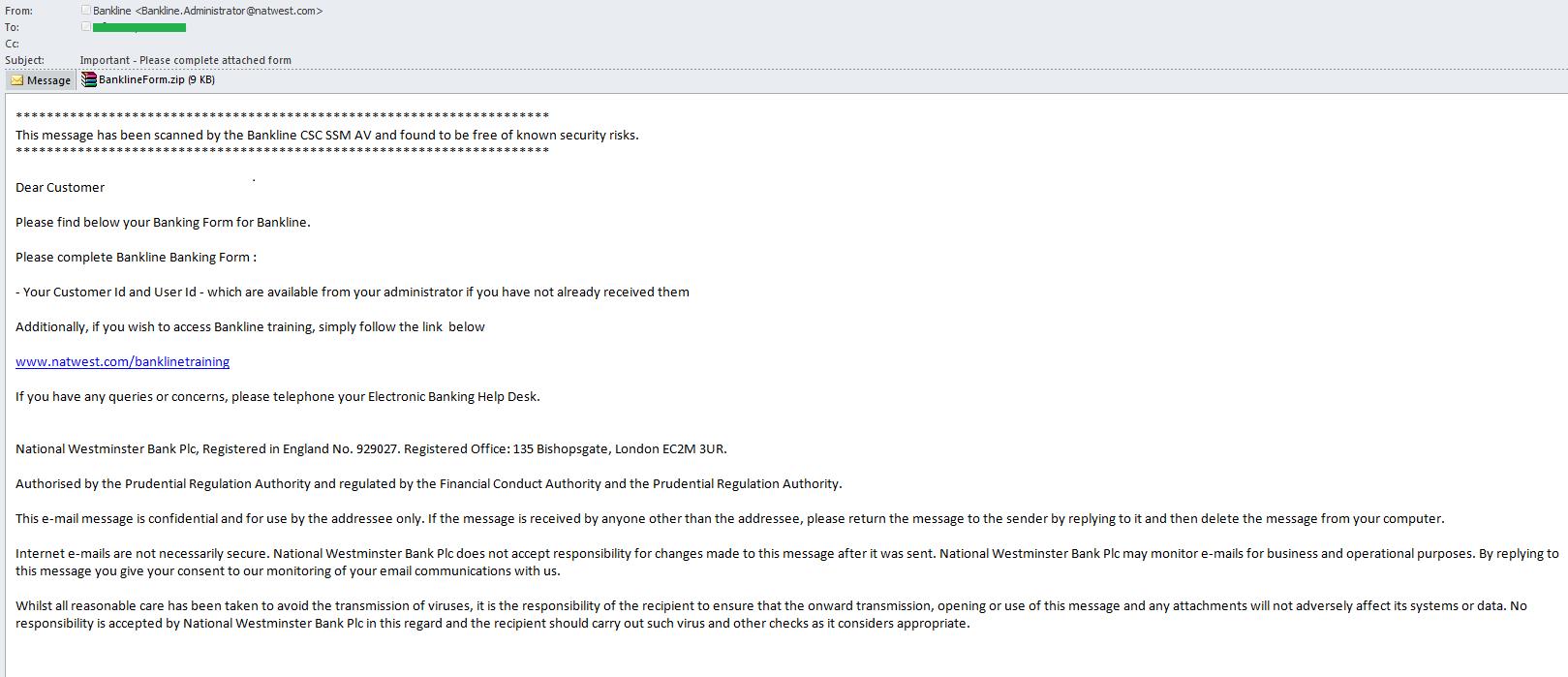
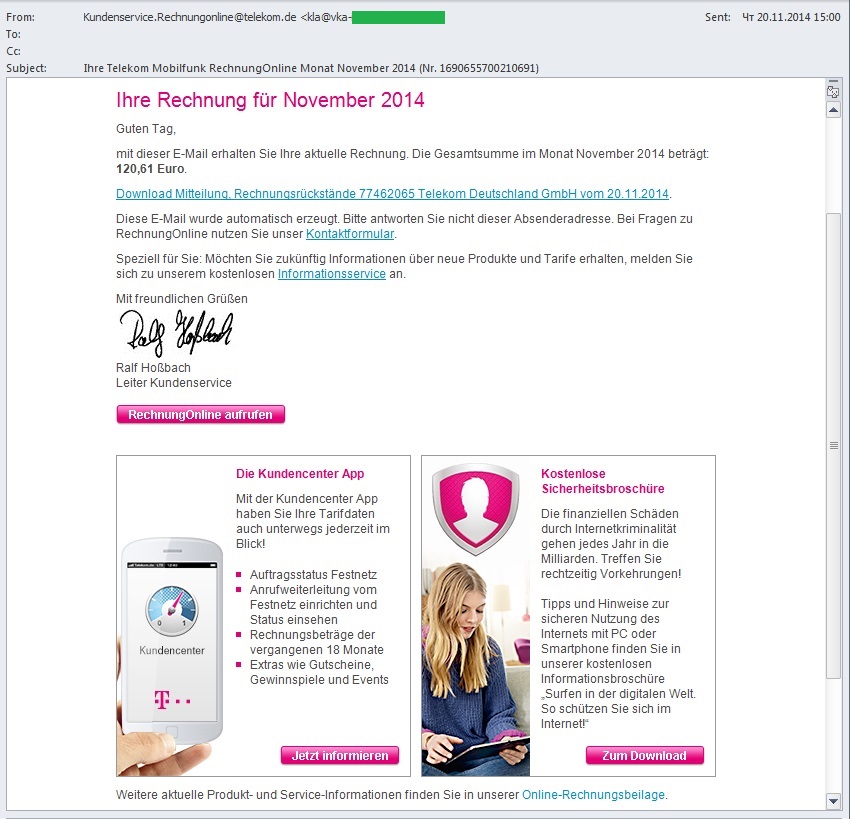
One of the most common types of malicious spam and phishing are fake bank notifications. In 2014, spammers began to complicate the design of fake messages by adding more links to official resources and services from the organizations that were mimicked in the fake notifications. Obviously, the attackers hoped that an email with a few legitimate links would be recognized as legitimate by users and spam filters alike. Meanwhile, the email contained a single fraudulent link; after clicking it an archive containing a malicious program was downloaded onto the victim computer.
In some cases, cybercriminals used different URL shorteners to mask the real link. Eventually they redirected the user to a popular cloud storage where a malicious program was hosted under the disguise of an important document.
Phishing
When preparing statistics on phishing we applied the methodology that was first used in our report “Financial cyber threats in 2013” published in April 2014. As a result the data on phishing for 2014 should be compared with the data in that report (not with the report “Spam in 2013”).
The data source
The report is based on the data about Antiphishing system activations collected by Kaspersky Security Network. The Antiphishing system contains of three components:
2 deterministic:
- Offline phishing contains a database of the most relevant phishing wildcards* and is located on users’ devices. It is triggered when the system encounters a link that matches one of the phishing wildcards in the database
- Cloud anti-phishing contains all known phishing wildcards*. The system refers to the cloud if the user encounters a link that is not included in the local anti-phishing database. Cloud databases are updated much quicker than local databases.
Heuristic:
- The heuristic web component of the antiphishing system. This component is triggered when a user clicks on a link to a page with phishing content but information about this page is not yet available in the Kaspersky Lab databases.
* Phishing wildcards are a set of symbols to describe a group of links detected by the system as phishing. One phishing wildcard can help detect several thousand active links to phishing sites.
In 2014 the computers of users of Kaspersky Lab products recorded 260,403,422 instances that triggered the antiphishing system. Of these, 55% (143,827, 512) involved activation of the deterministic component, and 45% (116, 575, 910) came from the heuristic web component.
Phishing links: not only in email
The deterministic components of the antiphishing system (cloud and offline) check links in the user’s browser and messages received via IM or email. Only 6.4% of all the activations of these components come from links in emails. This suggests that today, instead of traditional phishing mass mailings, phishers are using other ways to spread links and new scams.
Kaspersky’s #antiphishing system was triggered 260,403,422 times in 2014 #KLReport
Tweet
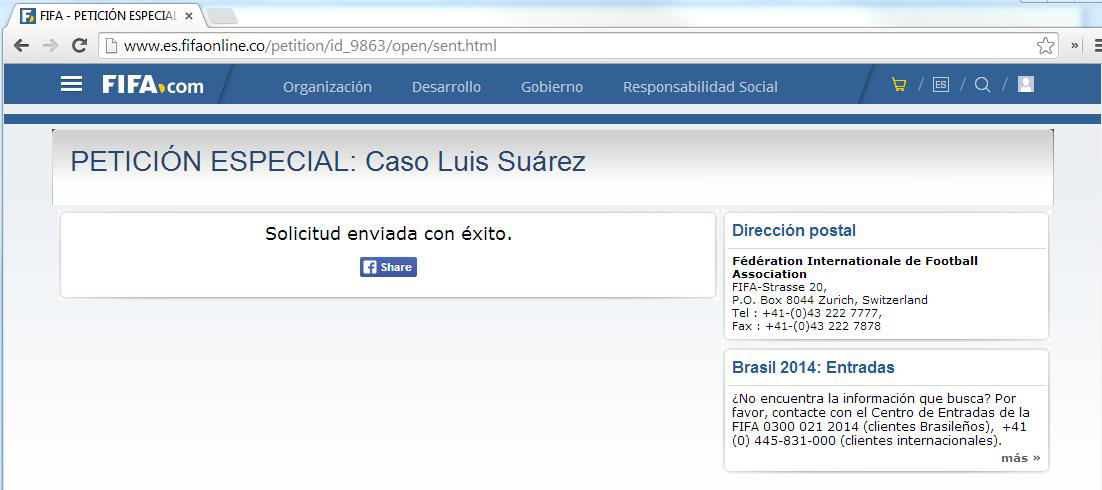
Currently links to phishing sites are more often distributed via social networks. It’s not just about using stolen accounts; fraudsters are also involving unwitting users in sending out phishing links to their friends in social networks.
For example, in July 2014 this particular trick was used to spread a link to the petition in support of Uruguayan footballer Luis Suárez via social networks. To sign the petition, users had to enter their personal data, which then went to the phishers. After that, the victim was invited to share the link with his friends on Facebook. As a result, the link to the phishing page spread quickly among football fans and their friends.
An example of a phishing page distributed with the help of social networks
Phishing emails
All this should not be taken as evidence that fraudsters have stopped spreading phishing links via email. It is still the most popular way of distributing links to fake pages of financial institutions. Perhaps that’s why scammers usually send out emails containing links to phishing sites on weekdays when the users check their e-mail \at work.
Activation of the deterministic components of the antiphishing system on the users’ mail clients
Fraudulent schemes utilizing phishing emails with malicious attachments, HTML files or HTML forms inserted in the body of the message are also popular with fraudsters.
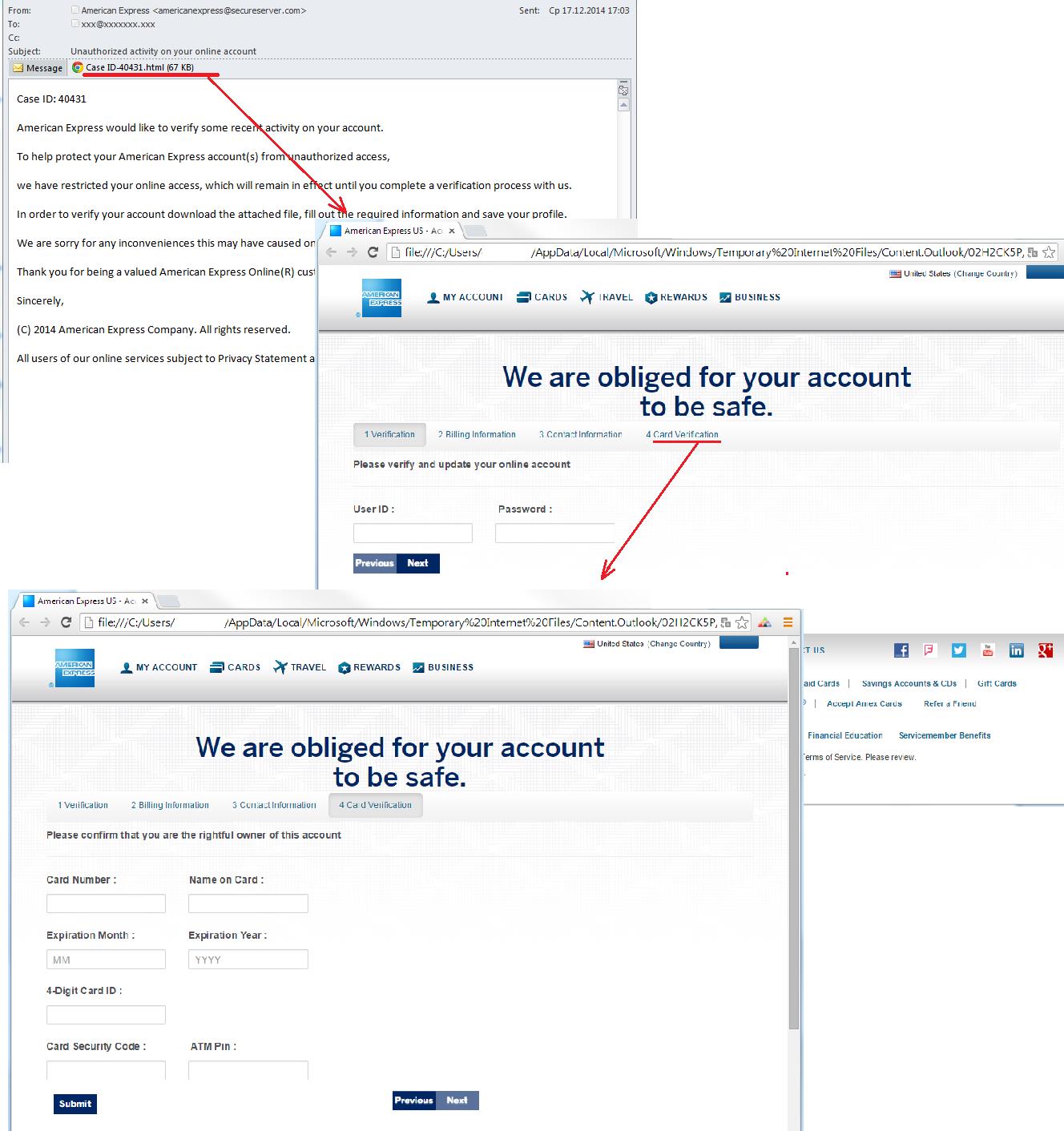
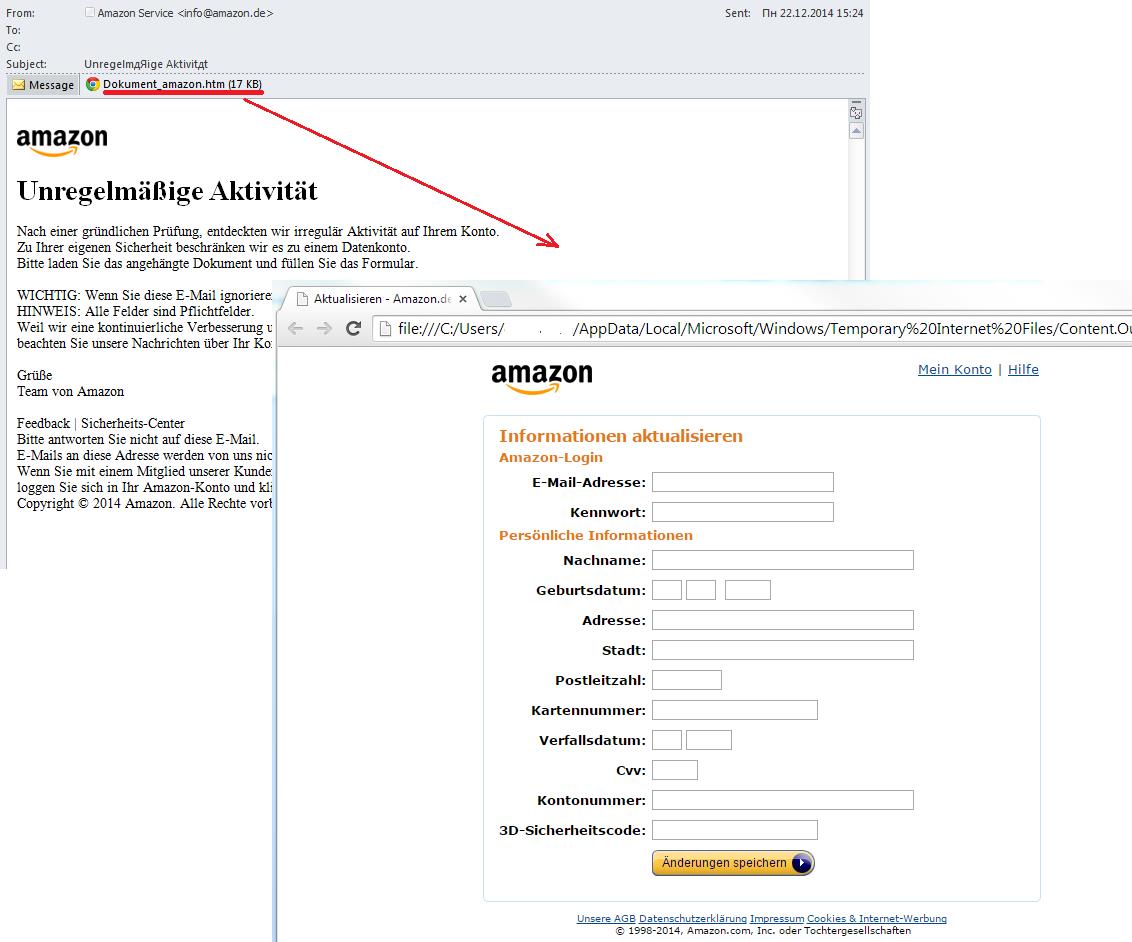
Attaching HTML files or HTML forms allows fraudsters to reduce the costs of maintaining the page on the Web. The standard scheme looks like this. User receive a fake notification from an organization that informs them their accounts have been blocked, their data has leaked or some suspicious activity was logged. To help solve the problem, users should update their personal information in the attached file or form. The data entered by the victims goes straight to the scammers. Over the past year we found dozens of mailings like this purporting to come from various financial institutions and other organizations.
An email with an attached HTML file
A phishing attack using HTML attachments to target the customers of a specific organization is often a means of extracting a wide range of financial information from victims, not of all of which necessarily relates to the company used in the scam.
An email with an attached HTML file
The examples above show the tricks that fraudsters use trying to get not only credentials to access online accounts, but also other personal information including bank card data.
Big game hunting
As mentioned above, when attacking customers of various organizations, fraudsters often try to get not only the victim’s account data but also the bank card details and other confidential information. In this way, some scammers collect valid e-mail address, perhaps to sell them to spammers. Others pose as a bank or similar organization that is concerned about security and use that mask to steal the user’s financial information and then his money.
The increased danger of phishing schemes consists of this: no matter what anti-fraud schemes are in place to protect customers (double, triple verification, one-time passwords, etc), they can only protect the account. If the user passes personal data to fraudsters there is little that can be done to stop that information being used to access the account.
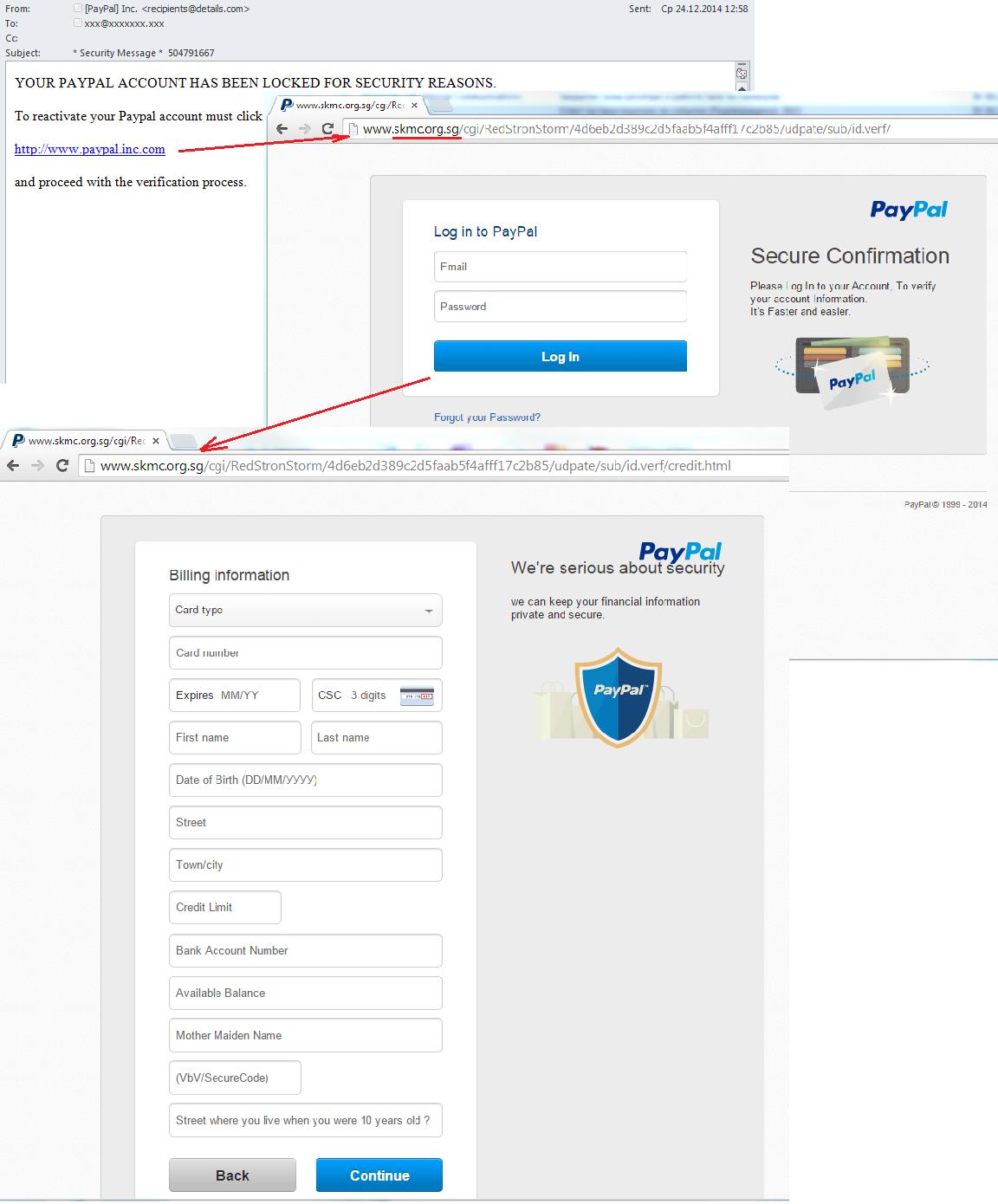
We have already given examples of an “extended” phishing attack that utilizes HTML attachments. Yet another example is this phishing attack on PayPal. The traditional scam directs victims to a phishing page that mimics the site of the payment system. Unwary users input their usernames and passwords, sending them to the fraudsters. A further page opens and request bank card data and other information. The users believe they are safely logged onto PayPal and enter the information without a second thought. Once the scammers have that info, they redirect users to the official PayPal site leaving their victims none the wiser about the data theft.
A phishing attack on PayPal
The attackers may not be able to get into the victim’s PayPal account because the company has additional protection measures. But they will have enough information to be able to steal money in other ways.
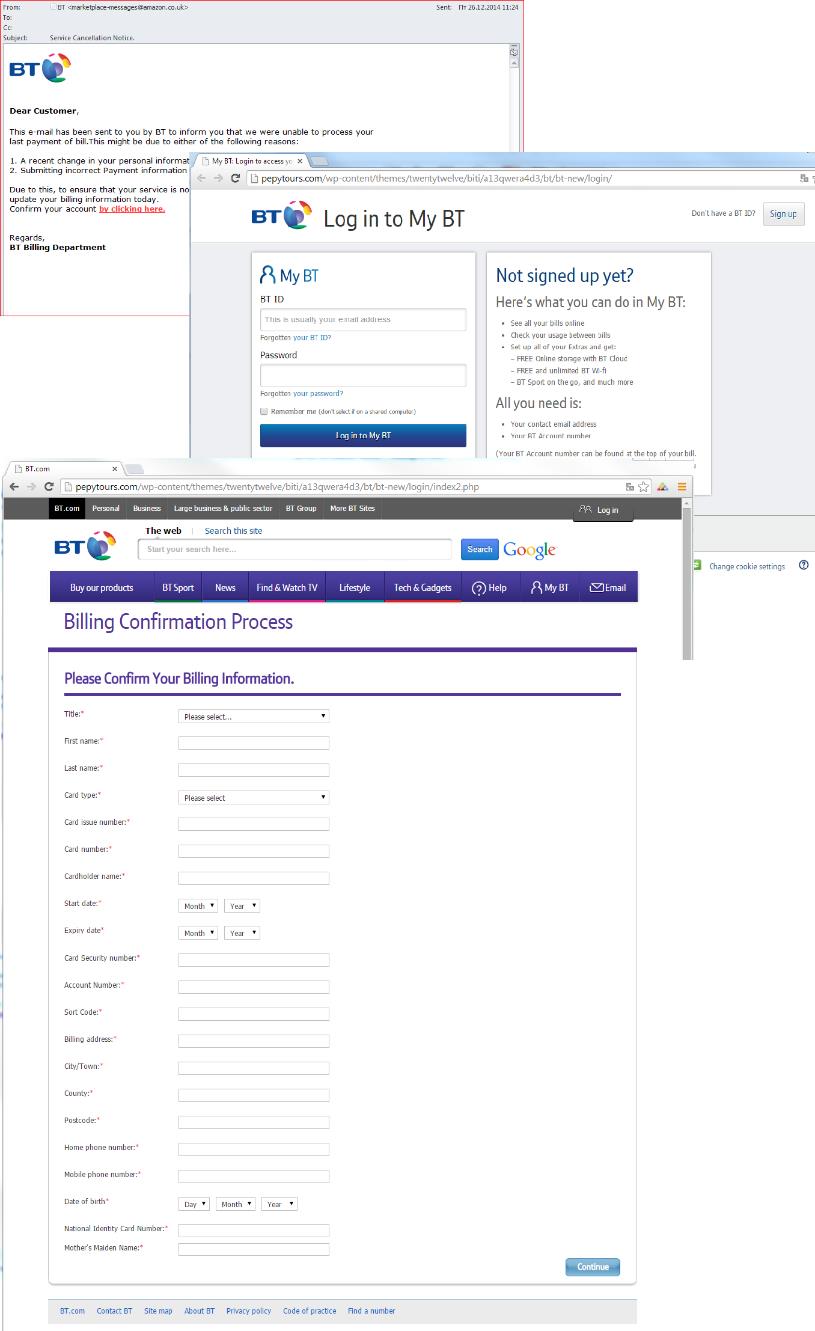
A phishing attack on one of the largest organizations in the telecommunications industry is another good example. At first glance, the fraudsters need a login and password to access the user’s personal account. However, once the victim enters a fake account, the scammers not only ask for the card data but also for all other information that may be useful for them to manipulate the victim’s money.
A phishing attack targeting the victim’s personal information
The geography of attacks
In 2014 phishing attacks were registered in almost all countries worldwide.
Top 10 countries by percentage of attacked users
Brazil had the highest proportion of users subjected to phishing attacks (27.47%).
The percentage of users on whose computers the antiphishing system was triggered out of the total number of users of Kaspersky Lab products in the country, 2014
Top 10 countries by percentage of attacked users
| Country | % of users | |
| 1 | Brazil | 27.45 |
| 2 | Australia | 23.76 |
| 3 | India | 23.08 |
| 4 | France | 22.92 |
| 5 | Ecuador | 22.82 |
| 6 | Russia | 22.61 |
| 7 | Kazakhstan | 22.18 |
| 8 | Canada | 21.78 |
| 9 | Ukraine | 20.11 |
| 10 | Japan | 19.51 |
In 2014, the percentage of attacked users in Brazil grew by 13.81 percentage points compared with 2013 (when Brazil was 23th in the rating). This intense burst of phishing activity in Brazil is probably connected to the 2014 World Cup, which brought thousands of fans from around the world to the South American country.
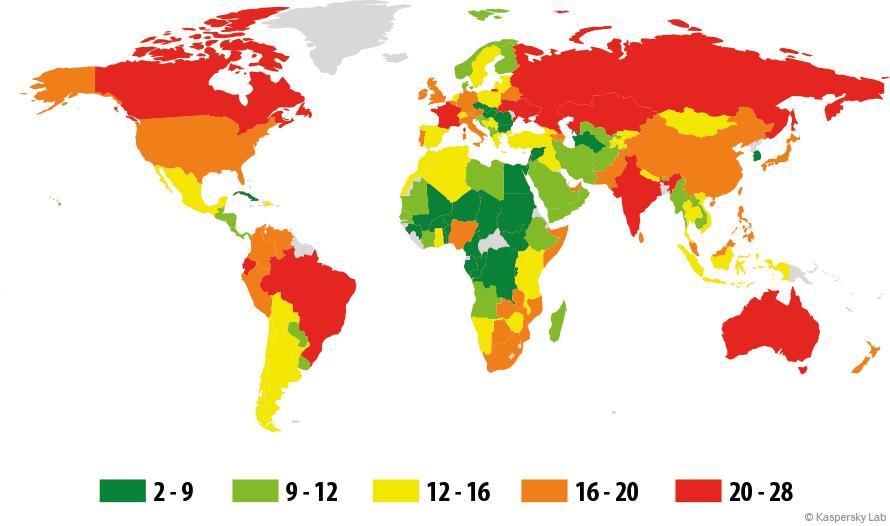
The distribution of attacks by country
Russia had the greatest share of phishing attacks, with 17.28% of the global total. The percentage of users in this country on whose computers the Kaspersky Lab antiphishing system was up 6.08pp from the previous year.
Distribution of phishing attacks by country in 2014
The increase in the number of attacks on the users in Russia is probably related to the deteriorating financial situation in the country in 2014. People are making more transactions as they try to invest their savings and make online purchases. At the same time many users are worried, giving scammers more opportunities to apply their social engineering techniques and play on those fears.
Last year’s leader – the US (7.2%) – moved down to second place, with a 23.6 percentage point drop in the number of attacked users. It is followed by India (7.15%) and Brazil (7.03%), where rates increased by 3.7 pp and 5.11 pp respectively.
Organizations under attack
These statistics on the organizations used in phishing attacks are based on the triggering of the heuristic component of the antiphishing system. The heuristic component is triggered when a user follows a link to a phishing page and there is no information about this page in the Kaspersky Lab databases.
Distribution of organizations subject to phishing attacks by category, 2014
In 2014 we saw changes in the organizations targeted by phishers. Last year’s leader, the ‘Social networking and blogs’ category dropped 19.62 pp to 15.77%, and was overtaken by ‘Global portals’, which gained 19.29 pp and reached 42.59%. Global Portals was previously described as ‘E-mail’ in earlier reports. The change is no big surprise: Google, Yahoo!, Yandex and similar companies are constantly developing their services and offering new options, from email and social networks to e-wallets. This is very convenient for users because everything is available under one account; it’s also a boon for scammers because one password can unlock a huge range of digital resources. That’s why Yahoo! and Google came into the top 3 most-frequently attacked organizations, sandwiching Facebook.
Top 3 attacked organizations
| Organisation | % of phishing links | |
| 1 | Yahoo! | 23.3 |
| 2 | 10.02 | |
| 3 | 8.73 |
In 2014 the numbers for Yahoo! (23.3%) grew by 13.3 percentage points compared with the previous year (partly due to a sharp increase in the number of fraudulent links to fake Yahoo! pages at the beginning of January 2014).
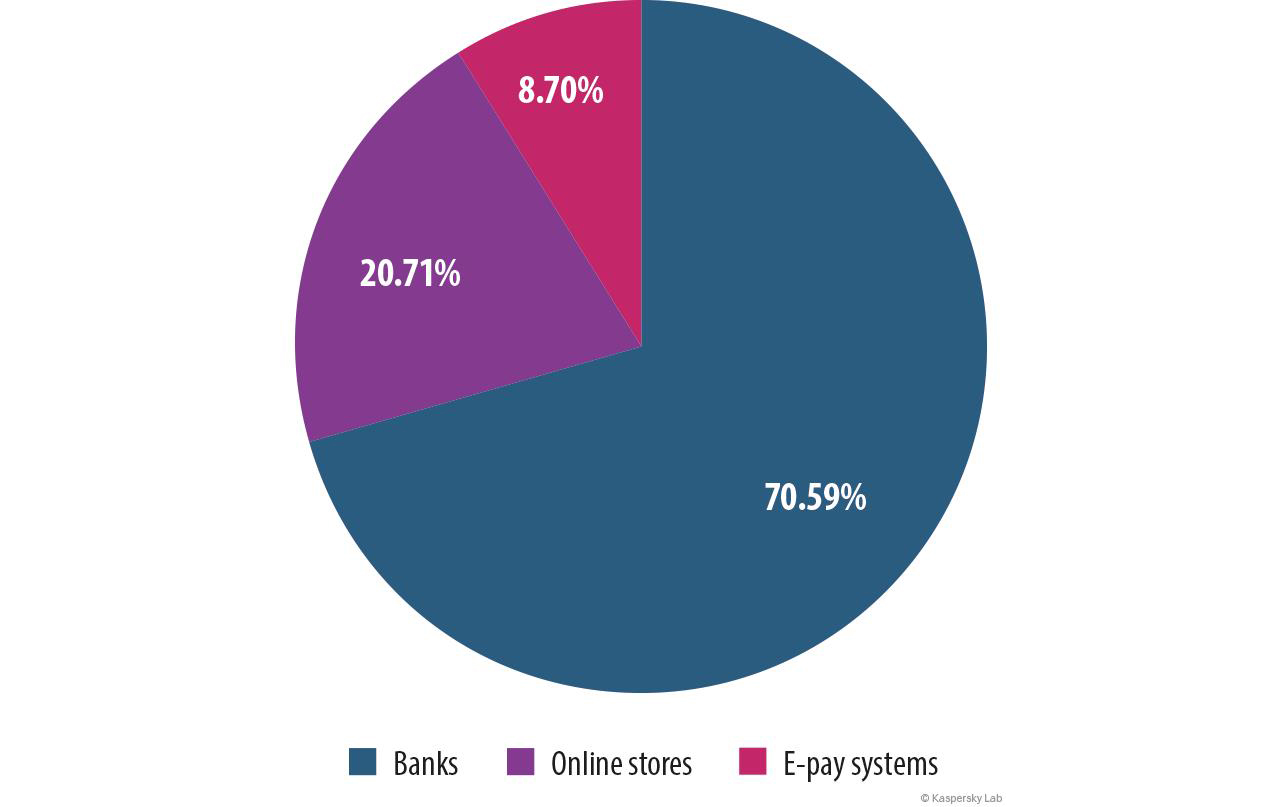
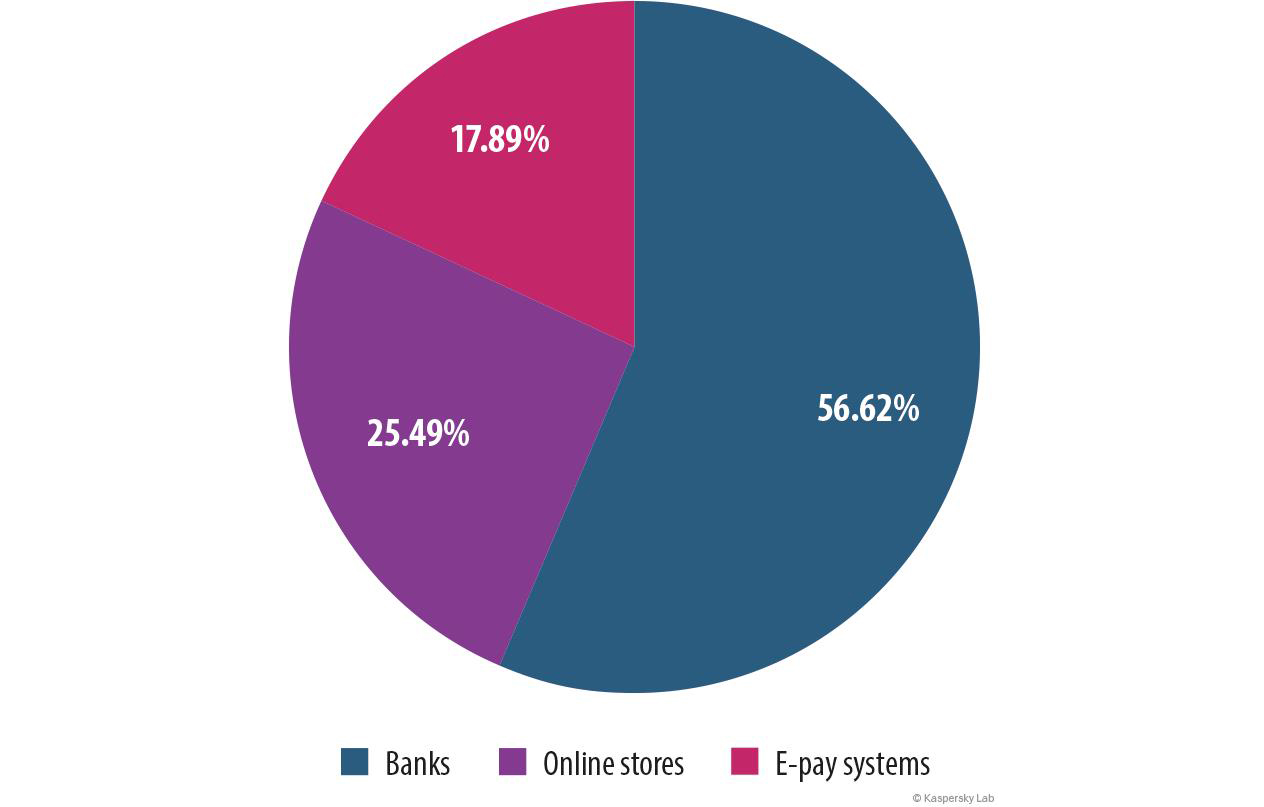
The share of phishing attacks on financial institutions was 28.74%, a 2.71 pp drop from 2013. Within this sector the percentage of attacks on the banking sector declined (down 13.79 pp from 2013). At the same time the numbers for “Online stores” and “Payment systems” rose by 4.78 pp and 9.19 pp respectively.
Distribution of financial phishing by the type of organization attacked, 2013
Distribution of financial phishing by the type of organization attacked, 2014
You can read more about financial phishing in our report “Financial cyber threats in 2014: times have changed“.
Conclusion
The percentage of spam in email traffic continues to decline; we do not expect a significant change in these numbers in 2015.
We expect a further reduction in the amount of advertising spam and an increase in the number of fraudulent and malicious emails. At the same time we will see more carefully designed fake messages, in which attackers will use even more elaborated tricks (such as malicious attachments with unusual extensions like .arj, .scr).
Fraudsters use a variety of methods to distribute phishing content. However, time-proven phishing mass mailings are still popular and are likely to remain so for a long time.
For their phishing attacks scammers choose the clients of the most popular organizations, thereby increasing the likelihood of a successful attack. At the same time, many attacks are conducted in order to get maximum personal, primarily financial, information from the victim. We assume that this trend will continue in the future.
Kaspersky Security Bulletin. Spam in 2014




















Jerry Chapman
I’ve been trying to install the new total security software for some time now. I can’t get it to load. I follow instructions but it seems to have a mind of it’s own. Something different pops up and I don’t know what to do. Would somebody please walk me through it?
thank you
Jerry