
Spam in the First Half of 2006
This report analyzes the volume and types of spam detected during the first half of 2006, and the new approaches and techniques used to send spam. Predictions regarding the future evolution of spam in the second half of the year are also included. The report is aimed at IT security professionals and users who are interested in the problem of spam.
- Malware Evolution
- Malware for non Win32 platforms
- Internet Attacks
- Malicious programs for mobile devices
- Spam Report
Kaspersky Labs receives and analyzes approximately 300,000 – 500,000 spam emails per day. The spam comes from several sources: dedicated spam traps, samples from email traffic, and samples provided by clients and partners. All incoming spam traffic is automatically classified, and a proportion is also analyzed manually. A unique spam classification system helps maintain detailed records of the volume and types of spam.
Sending Spam: The Technical Details
During the first half of 2006 technologies currently used to send spam continued to evolve steadily. The techniques used by contemporary spammers are multiple, and include the following:
- Viruses which target PCs
- Distributed management of zombie networks
- Systems that make it possible to control PCs and servers remotely
- Automatic template-based email generators
The interdependence of these techniques has reached such a level that new innovations in mass mailing will take more than several months to appear. However, at the same time, the methods currently being used to send spam are evolving.
The following are still being used to send spam:
- Networks of zombie computers, i.e. botnets.
- Web servers and vulnerabilities in popular server-based software.
Botnets
Most spam is sent via botnets. The number of botnets is increasing steadily, while the networks themselves are becoming ever larger. Last year, the Dutch police arrested the creators of a network of 1.5 million PCs – a record which has not yet been broken. This doesn’t mean that there aren’t other giant botnets out there – it just means that the authorities haven’t been able to pinpoint them or their owners yet.
Currently, the controllers of botnets are moving from using IRC to HTTP. Moreover, centralized networks (i.e., those that have several control nodes to which other zombie computers can connect) more and more often have a control center that is located on a dedicated “spam-resistant” server1. Thus the dedicated server serves a second purpose, not as a source of spam, but as a control center for botnets.
Decentralized botnets have also become more popular; these are made up of zombie computers that attempt to connect to as many other zombies as possible. Commands are then passed from one computer to another within the network. Such networks can be managed via any of the computers in the network.
In an effort to fight spam, Internet providers that provide services to end users have introduced the following restrictions:
- Prohibiting sending mail directly to mail relays other than that belonging to the provider. This is in order to monitor all outgoing mail.
- Restricting the number of outgoing messages sent by one user in a defined period of time. A user may be banned altogether or face stringent restrictions if s/he exceeds the limit.
- Filtering the content of outgoing emails with the same filters used for incoming mail.
These measures help limit mass mailings from botnets that either send spam directly, or that send large quantities of spam from the same computer, and do not cause problems for the average user. In response, spammers have begun to use a large number of zombie computers to produce spam, thus reducing the number of emails sent from a single machine. . Another method used for mass mailing is to send spam via the provider’s mail server, which is identified either by a network scan or via an analysis of the settings in the user’s mail client.
|
1 The term ‘”Spam-resistant” server’ refers to servers leased from a provider which will allow the server to be used to send spam and which will ignore complaints. Usually, such providers are located in countries where there is little or no anti-spam legislation.
|
Web Servers & Vulnerabilities in Popular Server Software
The main idea behind using web servers and vulnerabilities in server software to conduct mass mailings is similar to the idea of using botnets: malicious users have to get the server to do their dirty work for them. However, the search for vulnerabilities does not relate to personal computers, but to servers, usually those running under Unix. Furthermore, the methods used to infect and manage vulnerable servers differ from those used for PCs, as do the methods used to exploit the vulnerabilities detected.
Web servers can typically be infected in the following manner:
- The source code of popular software is examined to see if any errors can be found that would allow commands to be executed server side. PHP interpreters, popular forum engines and blogs are the main targets when searching for vulnerabilities.
- Search engines (like Google, Yandex, etc) are used to search for web pages that use software containing vulnerabilities.
- Vulnerabilities are used to install scripts on a server that will allow the spammer to remotely execute commands or modify data accessed by the web server.
Once a way of accessing the server has been found, it can be used to send spam or conduct DDoS attacks.
A system administrator will probably notice fairly quickly that a server is being used in the ways described above can be noticed. S/he will then be able to delete the malicious code and patch the vulnerability. Other methods of exploiting servers are less obvious and involve embedding malicious code in a website’s html code. The malicious code will then infect the browsers of users visiting the site; naturally, the more popular the resource is, the more PCs are at risk of being transformed into zombie machines via browser vulnerabilities.
Spam on Message Boards
Last year we wrote about spammers attempts to find channels other than email to deliver their information, such as instant messaging (ICQ, MSN), and mobile phones (SMS, MMS). But that’s not all. An increasing amount of spam now occurs in the form of posts on popular message boards and comments on blogs.
Previously, this type of spam was never actually meant to be read by people, but rather to trick search engines, i.e. to increase the rating of the site being advertised due to the large number of links to it. This type of spam was mainly found on dead forums, where the administrators did not perform any forum maintenance.
Over the past six months, the amount of spam that contains advertising material and that is meant to actually be read by people has increased. These messages usually mimic standard forum posts. Spammers choose forums and blogs with the highest hit rates and subjects most relevant to the service or product being advertised for this type of spam.
Graphical Spam
Graphical spam topped the charts in the first half of 2006. Graphical spam is a term used for the mass mailings where the spam includes the main information in an attachment to the email, rather than in the body of the message itself. This type of spam is on the rise. Spammers modify software in order to create and send graphical spam. The following innovations have appeared on the scene:
- Rotating source images at random angles.
- Dividing images into pieces and reconstructing the original whole image from the pieces using HTML.
- Graphical representations of individual letters; these will be represented differently in individual mails which are part of the same mass mailing.
New tricks currently being developed by spammers share the same goals as older methods used to evade spam filters: to include ‘noise’ in the image to prevent the filtration module from using checksumming to establish that the graphical attachments in a single spam attack are identical.
Any innovation requires modification of the software spammers use – and that means time, money and human resources. If spammers have started working on a specific technique or technology, it means that this technique or technology is currently effective in terms of helping spam get past anti-spam filters.
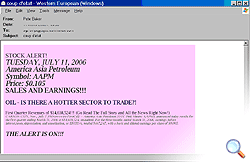
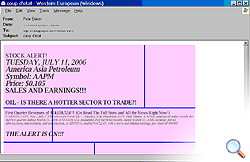
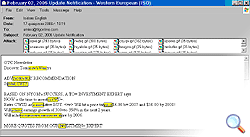
Today’s graphical spam is in English and aimed predominantly at Western users. Frequently, graphical spam offers deals on medicines, cheap software, Swiss watches and hot stock market opportunities.
About two years ago, Russia was hit by a wave of graphical spam experimentation. However, Russian spammers then more or less stopped their investigations, confining themselves to the technologies and approaches that they created in 2004.
Below are some examples of new trends in graphical spam seen in the first six months of 2006.
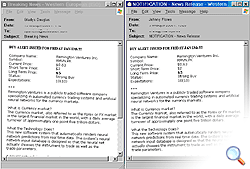
1. Two examples of a spam attack using skewed text.
2. “Fragmented” Images:
A user will see this message:
But actually the image consists of several smaller images, like this one:

Here is the same message, showing the image fragments:
3. Graphical images of individual letters
Strictly speaking, this isn’t so much a new trend as an attempt to revive an oldie but goodie. This graphical trick hasn’t been seem for more than 1.5 years, which is why we decided to place this back in the ‘new trends’ category for the first half of 2006.
Below is one typical example of this kind of message:
This is the same email, but with the graphical text fragments highlighted:
Despite such innovations, no major new mass spamming technologies have been detected in the past six months; instead, current technologies are being developed further.
Spam Volume
Starting in March 2006, Kaspersky Lab analysts have noted that spam has a steady, large share of email traffic, between 75-78% of all email.
 |
Kaspersky Lab analyst data suggest that this high percentage is valid both throughout the Russian and the Western segment of the Internet.
If we were to compare the figures from the first half of 2006 with those from 2004-2005, we could note that the lower end of the percentage range has risen from 73% to 75%. Meanwhile, the graph depicting the volume of spam shows a smoother, more gradual increase without any sharp rises or falls, which is actually rather unusual. In 2003-2005 the Russian Internet saw two ‘seasonal’ declines in spam volume, linked with the traditional New Year and May holidays. There was no decline in May 2006. It appears that currently spam has reached a saturation point in email traffic. The volume of spam has stabilized at a relatively high level, and this level is only slightly influenced by factors such as regional holidays.
Overall, the trends in terms of spam volume in the first half of 2006 can be outlined as follows:
- In January, spam fell to a low of 44% of the total volume of email traffic (4-5 January);
- Spam then climbed steadily to a peak at 86.4% in February (14-17 February);
- A few more sharp fluctuations were seen, from 63.8% to 81.2%;
- Finally, spam volume stabilized within the range of 75%-78%.
Over the last four months of the first half of this year, the volume of spam in mail traffic did fluctuate slightly, although a jump to 89.7% was recorded on 13 April. Towards the end of the first six months of this year, Kaspersky Labs noted a gradual increase in spam, while June closed at 82.2%, which is also unusual. Mid-summer is typically “dead season” for spam advertising. The next few months will reveal whether or not spam volume will revert to average figures, i.e. below 80%.
Spam Topics
During the first six months of this year, the top three spam categories in the Russian Internet were:
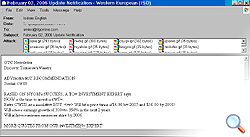
- “Computer fraud” spam2
- Spam offering medications and other medicinal and “semi-medicinal” products / services.
- “Educational” spam, offering special courses, seminars and training.
 |
Computer fraud spam has once again increased; while this type of spam accounted for 11% of all spam in 2005, it comprised 18.8% of all spam in the first six months of 2006. For more details, see the section on criminalized spam.
Some computer fraud spam stands out due to its enviable longevity: such emails are repeatedly sent out at regular intervals to millions of addresses.
The top 3 most widespread, long-lasting and repetitive spam attacks are as follows:
- Offers for Viagra and other means of improving virility (the message feature jumbled spellings of the medicine in question, such as ouxomVjlAGRA).
- Financial spam – i.e. an attempt to influence the value of a stock on the stock market (the subject of the mail will offer a stock, for example Stock Promo Mover: SGXI.PK).
- Offering courses, training and seminars for managers on improving employee motivation, issues relating to accounting or taxation.
|
2 This includes spam categories such as phishing, 419 emails, false notification of lottery winnings, counterfeit and contraband goods, fraudulent invitiations to send text messages to a paid number, etc. |
Criminalized Spam
The following factors demonstrate that criminalized spam process is still going strong:
- continued growth of the amount of ‘computer fraud’ spam;
- the appearance of new kinds of fraud which use spam;
- improvements in the types of spam in this category that have already been identified.
The numbers prove that criminalized spam is on the rise – in the first six months of 2006, 18.8% of all spam was criminalized spam.
 |
The diagram shows that the share of criminalized spam in the Russian segment of the Internet during the first six months of the year fluctuated a good deal. During “peak” periods, which lasted for as long as 1-3 days, as much as 25% of all spam fell into this category. During the remainder of the time, criminalized attacks accounted for 13-16% of all spam. Detailed figures for this category demonstrate that phishing incidents may comprise up to half of all ‘computer fraud’-type spam attacks.
Certain types of criminalized spam are distributed around the world. First and foremost, this is true for phishing, 419 spam, financial spam, offers for pirated software, etc. But there are other types of spam that are specific to certain regions. For example, participation in disguised money-laundering schemes (presented by spammers as legal business) is offered exclusively to users of the Western segment of the Internet.
Good day, Sir/Madam!
Let me introduce myself: my name is Sergey Rubinshtein and I am a financial analyst in Moscow. My specialization is analysis of Russian economics and financial markets. I frequently perform consulting projects for US financial firms. My American client’s Human Resources Dept manager advised me to find an American resident to serve as an intermediary because it is easier to receive payment this way than filling out all the required paperwork to become a 1099 employee.
That’s why I ask you for help in transferring consulting payments received from the US firms and will gladly compensate you with a percentage of my wages which I expect to be about $2,000 – $4,000 per week. This will become a small but recurring source of income for you for very little effort. Please contact me via e-mail if you are interested and would like to know the details.
In Russia, users experienced a new type of spam in the first half of 2006: spam which in one way or another invited the user to send free text messages to a paid service number. There are all kinds of different offers, but the spammers’ objective is always the same: earning money at the expense of the user.
For example, Kaspersky Lab analysts have detected spam containing an offer to unsubscribe from a spam mailing list by sending a text message to the number shown in the text. The spammers promise that this mythical ‘un-subscription from the spam database’ is free of charge, but actually sending a text message to the number used by the spammers can cost the sender $0.30 – $0.50. The unsuspecting user will lose a certain amount of money, and they will continue to receive spam as before.
A certain proportion of criminalized spam is mass mailed in European languages: English, French and German. For example, fake notice of lottery winnings are usually in English, while 419ers typically write in English and French, and counterfeit watches and popular brand name bags are also advertised in English.
This is partly due to the differences in day to day life for Russian speakers and Western Internet users – there are some offers that just aren’t currently relevant to Russian users. For example, online financial systems in Russia are less developed than in the West, which explains the lack of any Russian-language offers to conduct cash transactions; moreover, counterfeit and pirated goods can be purchased much more cheaply in Russia than at the prices spammers offer.
Attempts to translate some popular variants of English-language spam have been seen over the years and in the first half of 2006. Currently these are no more than sporadic attempts to adapt typical English-language spam for the Russian market. If these attempts are successful – if the spammers receive a sufficient response for them to gain financially – then the spam in question may become a regular nuisance in the mail boxes of Russian users.
Conclusions
- The volume of spam remains high, at 75%-78% of total mail traffic. An unexpected rise in spam hit the Internet in mid-summer. June closed with 82.2% of all mail traffic being spam.
- The most frequent types of spam were: computer fraud, pharmaceuticals (mainly Viagra and similar medications) and educational services.
- A new type of fraudulent spam has appeared on In Russia. This new type of spam invites the recipient to send a certain type of text message (containing a code word and/or number) to a paid service number. The spammers’ goal is to have funds transferred to their own personal accounts.
- The methods currently used for mass spamming are evolving.
- Spammers are gaining footholds on message boards and blogs.
- Graphical spam is a new development in spammer technology.
Predictions
- During the second half of the year, the percentage of spam in the total volume of mail traffic will not decline.
- Spam will feature more criminal aspects as the amount of criminalized spam in Russian increases.
- The top three spam categories are unlikely to change during the second half of the year.
- Spammers will continue to investigate and use other channels for distributing spam.





















Kaspersky Security Bulletin, January – June 2006: Spam Report