
Targeted attacks and malware campaigns
Back to the future: looking for a link between old and new APTs
This year’s Security Analyst Summit (SAS) included interesting research findings on several targeted attack campaigns. For example, researchers from Kaspersky Lab and King’s College London presented their findings on a possible link between Moonlight Maze, a 20 year old cyber-espionage attack that targeted the Pentagon, NASA and others, and Turla – a very modern APT group.
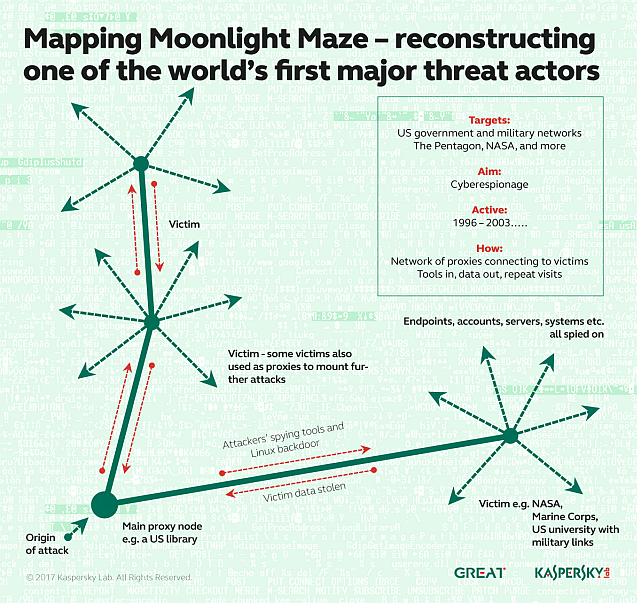
Contemporary reports on Moonlight Maze show how, starting from 1996, US military and government networks, as well as universities, research institutions and even the Department of Energy, began detecting breaches in their systems. The FBI and the Department of Defense launched a massive investigation in 1998. However, although the story became public the following year, much of the evidence has remained classified, leaving the details of Moonlight Maze shrouded in myth and secrecy. Nevertheless, over the years several investigators have stated that Moonlight Maze evolved into Turla.
In 2016, while researching his book Rise of the Machines, Thomas Rid of Kings College London tracked down a former system administrator whose organisation’s server had been hijacked as a proxy by the Moonlight Maze attackers. This server, ‘HRTest’, had been used to launch attacks on the US. The now-retired IT professional had kept the original server and copies of everything relating to the attacks, and handed it to Kings College and Kaspersky Lab for further analysis. Kaspersky Lab researchers, Juan Andres Guerrero-Saade and Costin Raiu, together with Thomas Rid and Danny Moore from Kings College, spent nine months undertaking a detailed technical analysis of these samples. They reconstructed the attackers’ operations, tools, and techniques, and conducted a parallel investigation to see if they could prove the claimed connection with Turla.
Moonlight Maze was an open-source Unix-based attack targeting Solaris systems, and the findings show that it made use of a backdoor based on LOKI2 (a program released in 1996 that enables users to extract data via covert channels). This led the researchers to take a second look at some rare Linux samples used by Turla that Kaspersky Lab had discovered in 2014. These samples, named Penguin Turla, are also based on LOKI2. Further, the re-analysis showed that all of them use code created between 1999 and 2004.
Remarkably, we’re still seeing attacks that use this code. It was seen in the wild in 2011 in an attack on defence contractor Ruag in Switzerland that has been attributed to Turla. Then, in March 2017, Kaspersky Lab researchers discovered a new sample of the Penguin Turla backdoor submitted from a system in Germany. It is possible that Turla uses the old code for attacks on highly secure victims that might be harder to breach using its more standard Windows toolset.
The newly unearthed Moonlight Maze samples reveal many fascinating details about how the attacks were conducted using a complex network of proxies, and the high level of skills and tools used by the attackers.
So did Moonlight Maze evolve into Turla? It is not possible to say at this time. The next step would focus on a little known operation called ‘Storm Cloud: the evolved toolkit used by the Moonlight Maze operators once the initial intrusions became public in 1999. The story of Storm Cloud leaked out in 2003 with little fanfare. However, a few prescient details led us to believe that this intrusion set might give a more definitive answer.
You can find details of the research here.
Lazarus uncovered
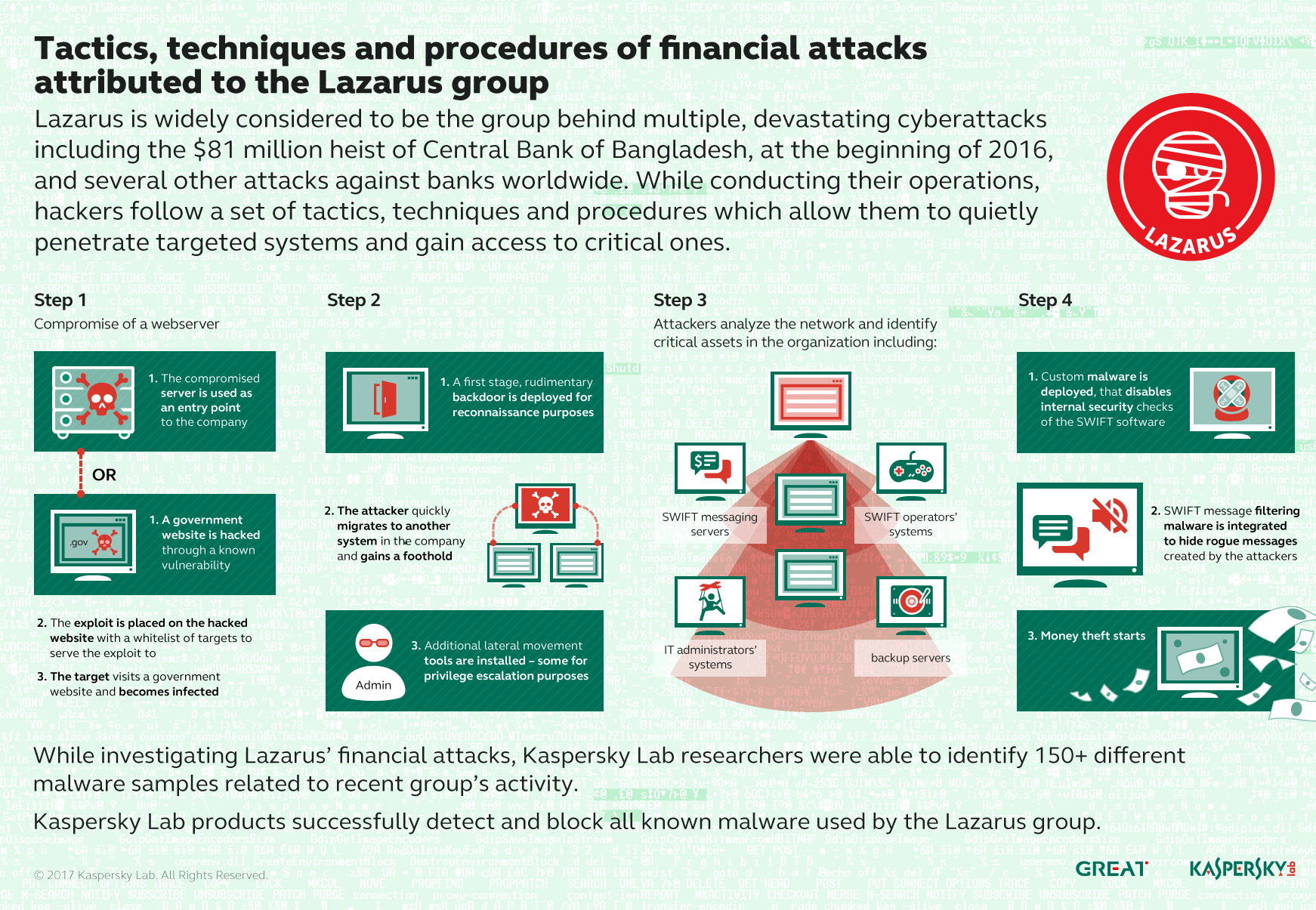
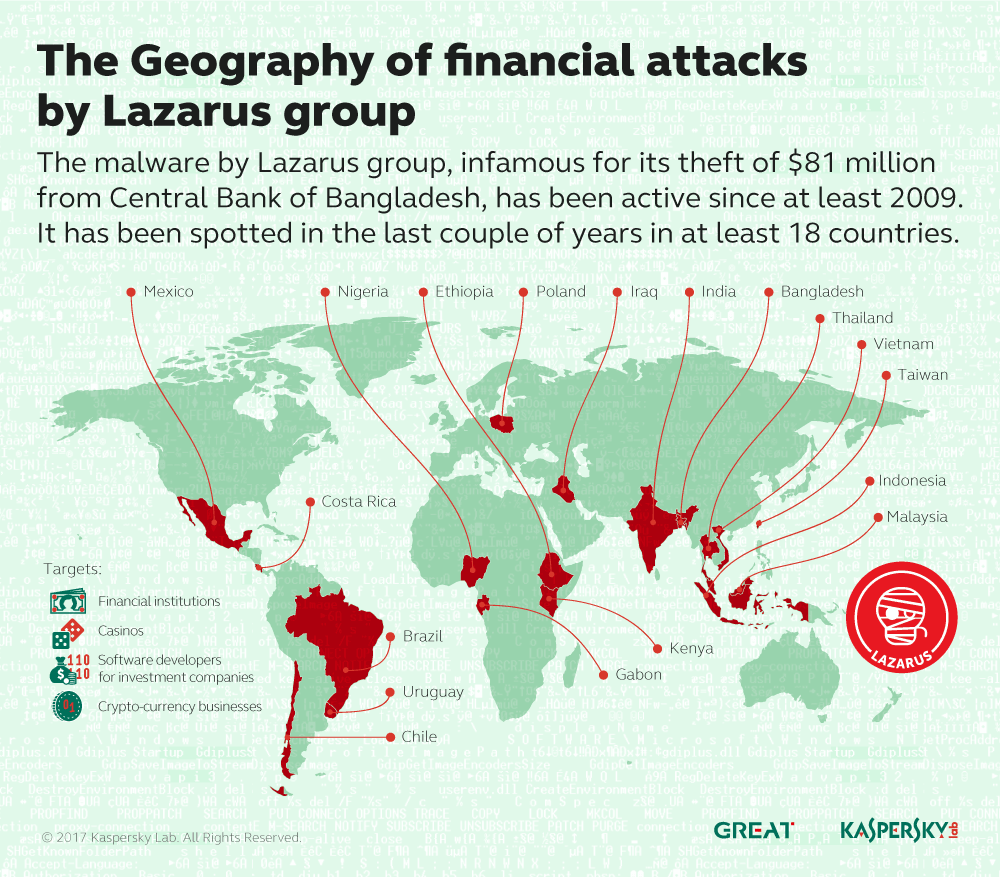
In February 2016 a group of hackers (unidentified at that time) attempted to steal $851 million – and succeeded in transferring $81 million from the Central Bank of Bangladesh – in what is considered to be the largest and most successful cyber-heist ever. Research by Kaspersky Lab and others revealed that the attacks were almost certainly conducted by Lazarus, a notorious cyber-espionage and sabotage group – responsible for the attack on Sony Pictures in 2014, as well attacks on manufacturing companies, media and financial institutions in at least 18 countries around the world since 2009.
Based on our investigations into attacks by the group on financial institutions in South East Asia and Europe, we have been able to provide an insight into the modus operandi of the Lazarus group.
Typically, the initial compromise occurs when a single system within a bank is breached, either by compromising a corporate server or by means of a watering-hole attack – that is, by placing exploit code on a legitimate web site visited by staff at the target institution. Then the attackers move to other hosts within the organisation and plant a rudimentary backdoor on infected computers. The group then spends time (days or even weeks) identifying valuable resources within the organisation. Finally the attackers deploy special malware designed to bypass internal security features and issue rogue banking transactions.
The Lazarus group operates across the globe: we have found infiltration tools used by Lazarus in multiple countries in the last year or so.
The Lazarus group is very large and has historically focused mainly on cyber-espionage and cyber-sabotage activities. The group’s interest in financial gain is relatively new and it seems as though a different team within Lazarus is responsible for the generation of illegal profits: we have dubbed this team Bluenoroff. So far, we have seen four main types of target: financial institutions, casinos, companies developing financial trade software and those in the crypto-currency business.
One of the most notable Bluenoroff campaigns was its attacks on financial institutions in Poland. The attackers were able to compromise a government web site that is frequently accessed by many financial institutions – making it a particularly powerful attack vector.
The Lazarus group goes to great lengths to cover its tracks. However, one of our research partners made an interesting discovery when completing a forensic analysis of a Command-and-Control (C2) server in Europe that was used by the group. Based on the forensic analysis report, it was apparent that the attacker connected to the server via Terminal Services and manually installed an Apache Tomcat server using a local browser, configured it with Java Server Pages and uploaded the JSP script for the C2. Once the server was ready, the attacker started testing it, first with a browser, then by running test instances of their backdoor. The operator used multiple IPs – from France to Korea, connecting via proxies and VPN servers. However, one short connection was made from a very unusual IP range, which originates in North Korea. The operator also installed off-the-shelf crypto-currency mining software that should generate Monero crypto-coins: this software consumed system resources so intensely that the system became unresponsive and froze. This could be the reason why it was not properly cleaned, and the server logs were preserved. Of course, while the link to North Korea is interesting, this doesn’t mean we can conclude that North Korea is behind all the Bluenoroff attacks: someone in North Korea could have accidentally visited the C2 server, or it could be a deliberate false flag operation.
Lazarus is not just another APT group. The scale of the Lazarus group’s operations is shocking: it appears that Lazarus operates a malware factory, generating new tools as old ones are ‘burned’. The group uses various code obfuscation techniques, re-writes its own algorithms, applies commercial software protectors, and uses its own and underground packers. Typically, the group pushes rudimentary backdoors during the first stage of infection – ‘burning’ these doesn’t affect the group too much. However, if the first stage backdoor reports an interesting infection they start deploying more advanced code, carefully protecting it from accidental detection on disk: the code is wrapped into a DLL loader or stored in an encrypted container, or maybe hidden in a binary encrypted registry value. This usually comes with an installer that only the attackers can use, because they password protect it. This guarantees that automated systems – be it a public sandbox or a researcher’s environment – will never see the real payload. This level of sophistication is something that is not generally found in the cybercriminal world and requires strict organisation and control at all stages of operation. It also explains Lazarus branching out into operations to general illegal profits – operations of this kind require lots of money.
The best defence against targeted attacks is a multi-layered approach that combines traditional anti-malware technologies with patch management, host intrusion detection and a default-deny allowlisting strategy. According to a study by the Australian Signals Directorate, 85 per cent of targeted attacks analysed can be stopped by employing four simple mitigation strategies: application allowlisting, updating applications, updating operating systems and restricting administrative privileges.
You can find our report on the activities of the Lazarus group here.
Beating the bank
At this year’s Security Analyst Summit two of our researchers, Sergey Golovanov and Igor Soumenkov, discussed three cases where cybercriminals had stolen money from ATMs.
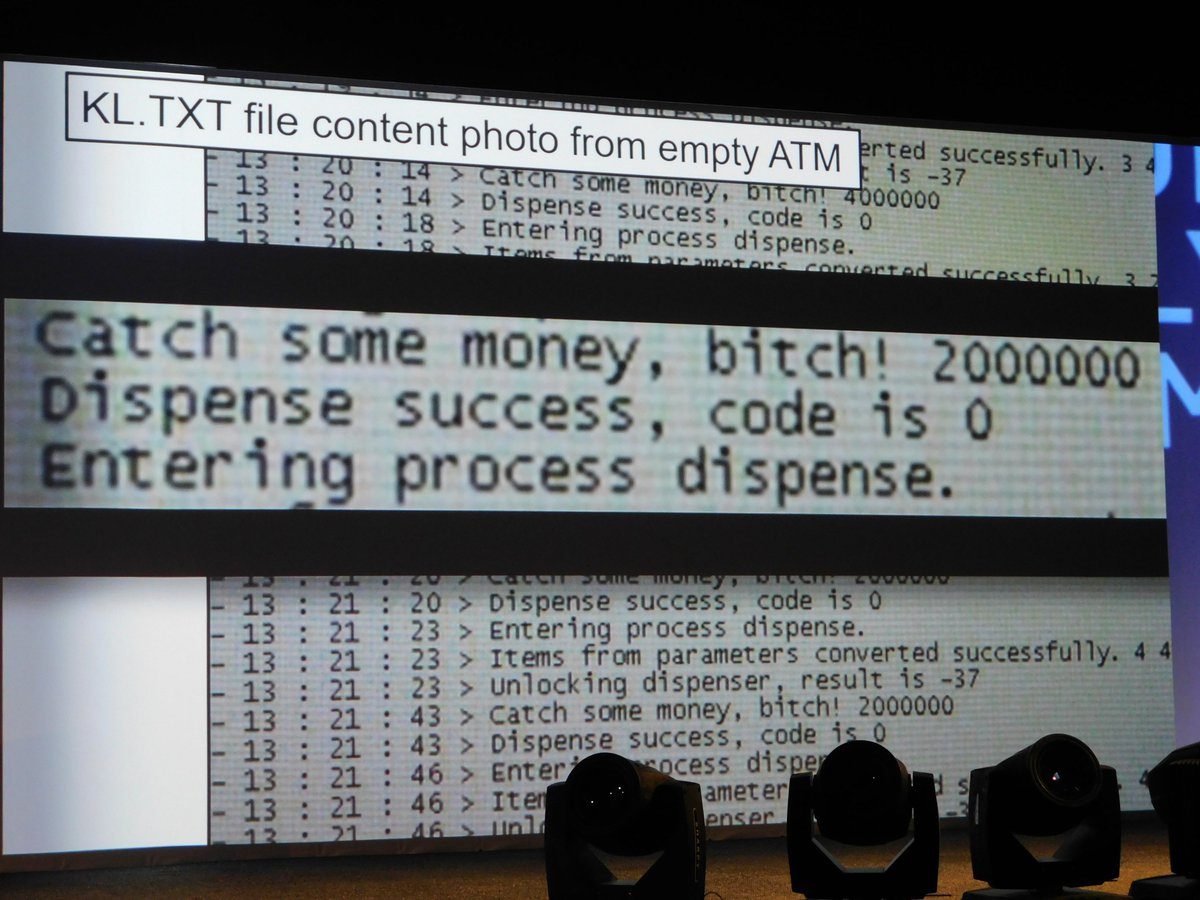
The first, ATMitch, involved compromising the bank’s infrastructure in order to controlling the operation of the ATM remotely. The attackers exploited an unpatched vulnerability to penetrate the target bank’s servers. They used open source code and publicly available tools to infect computers in the bank. However, the malware they created resided in memory only, not on the hard drives, and almost all traces of the malware were removed when the computer was re-booted. Following the infection, the attackers established a connection to their C2 server, allowing them to remotely install malware on the ATMs. Since this looked like a legitimate update, it didn’t trigger any alerts at the bank. Once installed, the malware looked for the file ‘command.txt’ – this contains the single-character commands that control the ATM. The malware first issues a command to find out how much money is in the ATM, then issues a further command to dispense money – collected by a money mule waiting at the ATM. After this, the malware writes all the information about the operation into the log file and wipes ‘command.txt’ clean.
What alerted bank staff to the malware was a single file called ‘kl.txt’. Thinking that this might have something to do with Kaspersky Lab, the bank called us and asked us to investigate. We created a YARA rule to search our systems for this file and discovered that we had been seen it twice – once in Russia and once in Kazakhstan. This enabled us to reverse engineer the malware and understand how the attack works.
One of the other bank attacks also started with a request from the bank. Money was missing, but the ATM logs were clear and the criminals had taped over the CCTV camera, so that there was no recording of the attack. The bank delivered the ATM to our office and, after disassembling it, we discovered that there was a Bluetooth adaptor connected to the ATM’s USB hub. The criminals had installed a Bluetooth adaptor on the ATM and had waited three months for the log to clear. Then they returned to the ATM, covered the security cameras and used a Bluetooth keyboard to re-boot the ATM in service mode and emptied the dispenser.
Another attack, which, like those mentioned above, started with a bank asking us to investigate an ATM theft, turned out to be much cruder in its approach. We found a hole, approximately 4cm in diameter, drilled near the PIN pad. Not long after, we learned of similar attacks in Russia and Europe. When police caught a suspect with a laptop and some wiring, things became clearer. We disassembled the ATM to try to find out what the attacker could be trying to access from the hole. What we found was a 10-PIN header, connected to a bus that connects all of the ATMs components and weak encryption that could be broken very quickly. Any single part of the ATM could be used to control all the others; and since there was no authentication between the parts, any one of them could be replaced without the others realising. It cost us around $15 and some time to create a simple circuit board that could control the ATM once we connected it to the serial bus, including dispensing money.
Fixing the problem, as our researchers highlighted, isn’t straightforward. Patching requires a hardware update and can’t be done remotely: a technician must visit all the affected ATMs to install it.
You can read more about these incidents here.
Meet the Lamberts
In April, we published a report on an advanced threat actor that can be compared with Duqu, Equation, Regin or ProjectSauron in terms of its complexity. This group, which we call ‘The Lamberts’ (but which is also known as ‘Longhorn’) first came to the attention of the security community in 2014, when researchers from FireEye discovered an attack using a zero-day vulnerability (CVE-2014-4148). This attack used malware that we call ‘Black Lambert’ to target a high profile organisation in Europe.
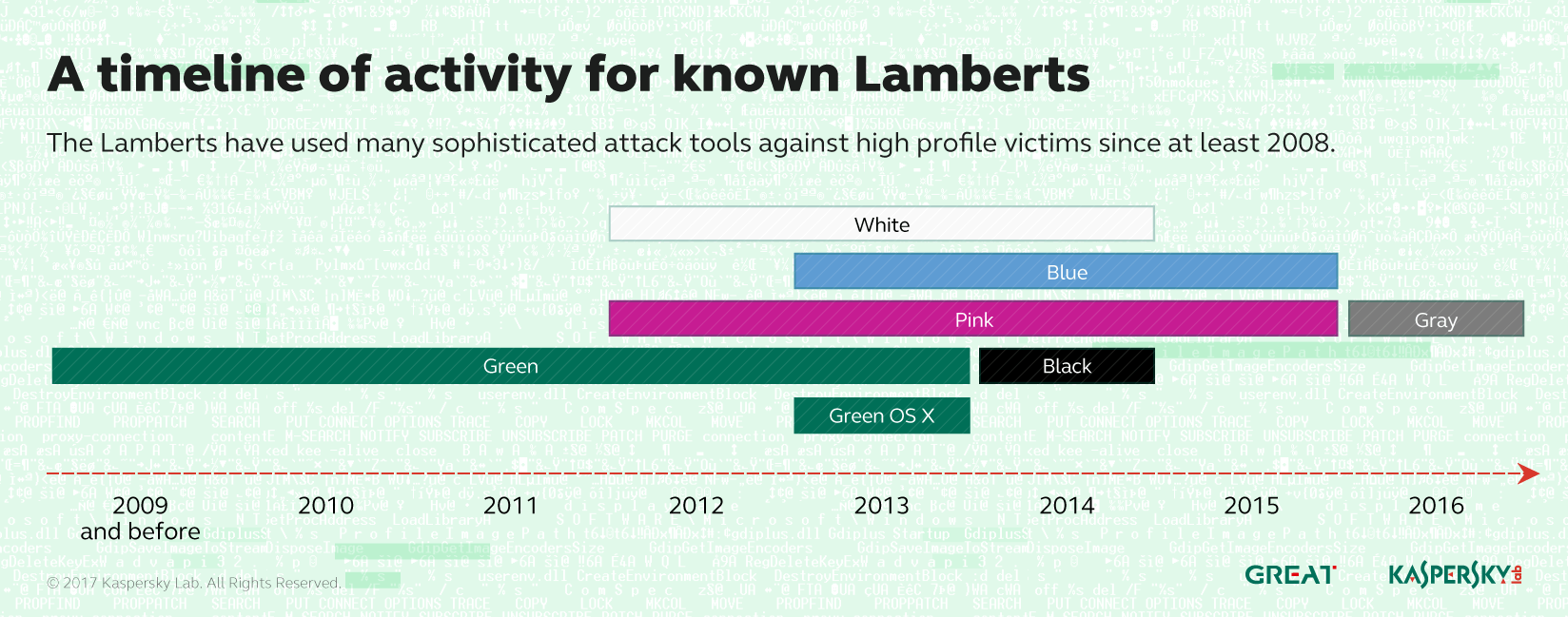
The group has developed and used sophisticated attack tools – including network-driven backdoors, several generations of modular backdoors, harvesting tools, and wipers – against its victims since at least 2008. The latest samples were created in 2016. There are currently known versions for Windows and OS X. However, given the complexity of these projects and the existence of an implant for OS X, we think that it is highly possible that other Lamberts exist for other platforms, such as Linux.
White Lambert runs in kernel mode and intercepts network traffic on infected machines. It decrypts packets crafted in a special format to extract instructions. We named these passive backdoors ‘White Lambert’ to contrast with the active ‘Black Lambert’ implants.
We subsequently came by another generation of malware that we called ‘Blue Lambert’.
One of these samples is interesting because it appears to have been used as second stage malware in a high profile attack that involved the Black Lambert malware.
The family of samples called ‘Green Lambert’ is a lighter, more reliable, but older version of Blue Lambert. Interestingly, while most Blue Lambert variants have version numbers in the range of 2.x, Green Lambert mostly includes 3.x versions. This stands in contrast to the data gathered from export timestamps and C2 domain activity that points to Green Lambert being considerably older than Blue Lambert. Perhaps both Blue and Green versions were developed in parallel by two different teams working under the same umbrella, as normal software version iterations, with one being deployed earlier than the other.
Signatures created for Green Lambert (Windows) have also triggered on an OS X variant of Green Lambert, with a very low version number: 1.2.0. This was uploaded to a multi-scanner service in September 2014. The OS X variant of Green Lambert is in many regards functionally identical to the Windows version, but it’s missing certain functionality – such as running plugins directly in memory.
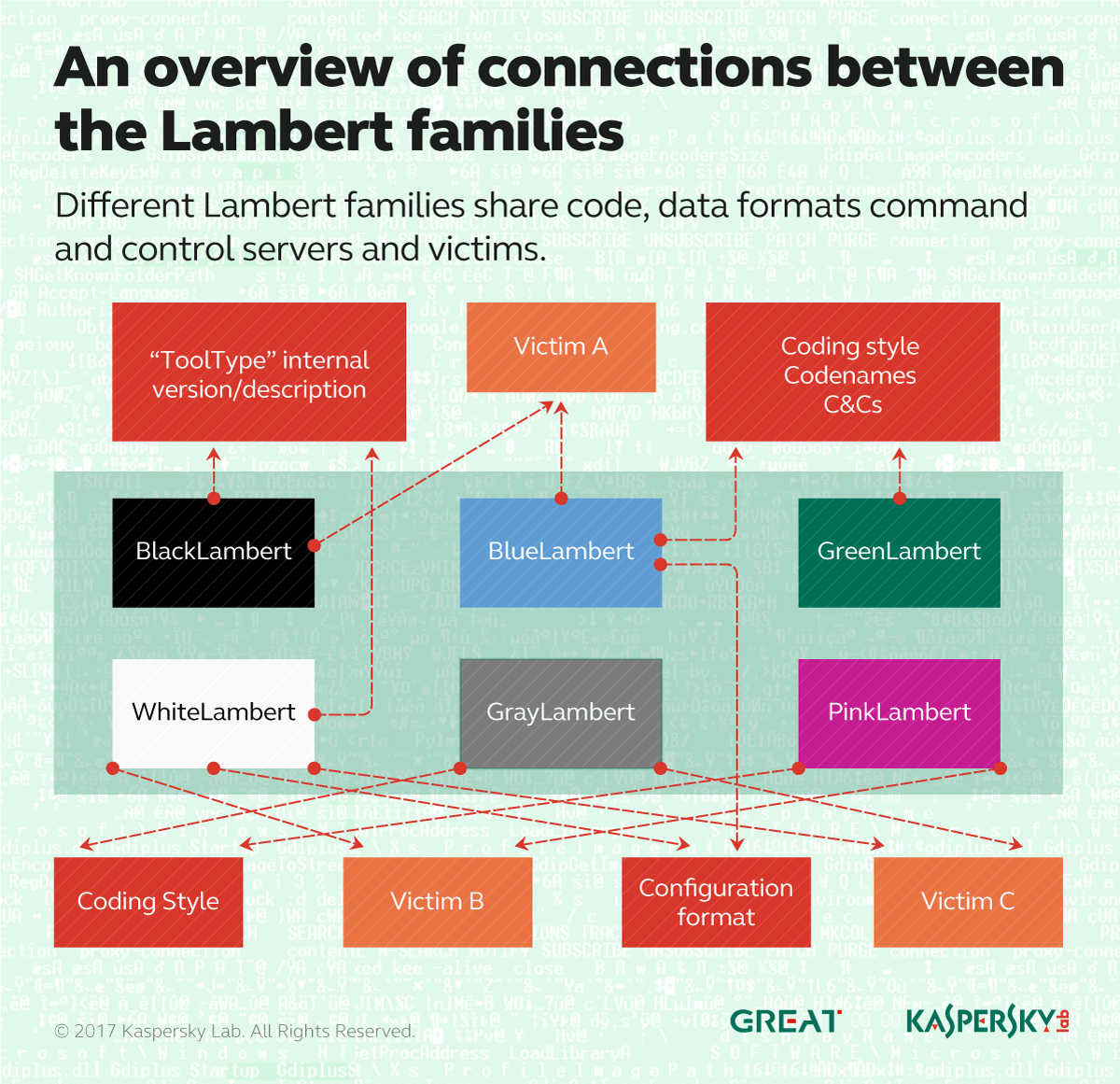
Kaspersky Lab detections for Blue, Black, and Green Lamberts have been triggered by a relatively small set of victims from around the world. While investigating one of these infections involving White Lambert (network-driven implant) and Blue Lambert (active implant), we found yet another family of tools that appear to be related. We called this new family ‘Pink Lambert’.
The Pink Lambert toolset includes a beaconing implant, a USB-harvesting module and a multi-platform orchestrator framework that can be used to create OS-independent malware. Versions of this particular orchestrator were found on other victims, together with White Lambert samples, indicating a close relationship between the White and Pink Lambert families.
By looking further for other undetected malware on victims of White Lambert, we found yet another, apparently related, family. The new family, which we called ‘Gray Lambert’, is the latest iteration of passive network tools from the Lamberts’ arsenal. The coding style of Gray Lambert is similar to the Pink Lambert USB-harvesting module. However, the functionality mirrors that of White Lambert. Compared to White Lambert, Gray Lambert runs in user mode, without the need for exploiting a vulnerable signed driver to load arbitrary code on 64-bit Windows systems.
Connecting all these different families by shared code, data formats, C2 server, and victims, we have arrived at the following overarching picture:
Development of The Lamberts toolkit spans several years, with most activity occurring in 2013 and 2014.
Overall, the toolkit includes highly sophisticated malware that relies on high-level techniques to sniff network traffic, run plugins in memory without touching the disk and making use of exploits against signed drivers to run unsigned code on 64-bit Windows systems.
To further exemplify the proficiency of the attackers behind The Lamberts’ toolkit, deployment of Black Lambert included a rather sophisticated TTF zero-day exploit, CVE-2014-4148. Taking this into account, we classify The Lamberts as the same level of complexity as Duqu, Equation, Regin or ProjectSauron – that is, one of the most sophisticated cyber-espionage toolkits we have ever analysed.
In the vast majority of cases, the infection method is unknown, so there are still a lot of unknown details about these attacks and the group(s) using them.
You can read more about The Lamberts here.
The only effective way to withstand such threats is to deploy multiple layers of security, with sensors to monitor for even the slightest anomaly in organisational workflow, combined with threat intelligence and forensic analysis.
We will continue to monitor the activities of The Lamberts, as well as other targeted attack groups. By subscribing to our APT intelligence reports, you can get access to our investigations and discoveries as they happen, including comprehensive technical data.
Malware stories
More vulnerable Internet of Things things
Hackers are targeting devices that make up the Internet of Things (IoT) more and more. One of the most dramatic examples is the Mirai botnet, which took down a portion of the Internet in October 2016 by hijacking connected home devices (such as DVRs, CCTV cameras and printers).
In our predictions for 2017 we suggested that vigilante hackers might also target IoT devices, to draw attention to the woeful lack of security in some connected devices – perhaps even going so far as to create an ‘Internet of bricks’. In addition, there have been recent reports (here and here) of IoT malware designed to just that.
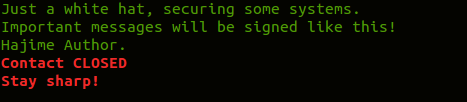
In April, we published an analysis of the Hajime botnet. This malware, first reported in October 2016 by Rapidity Networks, infects insecure IoT devices with open Telnet ports and default passwords. Hajime is a huge peer-to-peer botnet which, at the time of our report (25 April) comprised around 300,000 devices. The malware is continually evolving, adding and removing functionality. The most intriguing aspect of Hajime is its purpose. The botnet is growing, partly due to new exploitation modules, but its purpose remains unknown. So far, it hasn’t been used for malicious activity. It’s possible that this will never happen, because every time a new configuration file is downloaded, a piece of text is displayed while the new configuration is being processed:
On the other hand, even if it’s not used for deliberate harm, it’s possible that it might adversely affect the normal operation of an infected device.
Hajime, like other malware designed to compromised IoT devices, exploits the fact that many people don’t change the manufacturer’s default credentials when they buy a smart device. This makes it easy for attackers to access the device – they simply have to try the known default password. In addition, there are no firmware updates for many devices. IoT devices are also an attractive target for cybercriminals because they often have 24/7 connectivity.
These days we’re surrounded by smart devices. This includes everyday household objects such as telephones, televisions, thermostats, refrigerators, baby monitors, fitness bracelets and even children’s toys. However, it also includes cars, medical devices, CCTV cameras and parking meters. Now we can add drones to the list.
At the Security Analyst Summit, security expert Jonathan Andersson showed how a skilled attacker could create a device to hijack a drone in seconds. He used a software-defined radio (SDR), a drone’s control unit, a microcomputer and some other electronic equipment to create such a device, which he called ‘Icarus’. He used the device to tune to the frequency a drone uses to communicate with its controller and then experimented until he learned how exactly the signals were transmitted between the devices.
Andersson explained that this threat can potentially influence the whole drone industry — from cheap toys to expensive, professional craft — because drones and controller units use data transfer protocols that are vulnerable to the same type of attack. While stronger encryption could fix the problem, it’s not that easy because many controllers do not support software updates. Strong encryption also requires substantial computation capacity, which leads to additional energy consumption by the controller and the drone.
Hacking drones might seem a bit far-fetched, but the use of drones is no longer just a niche activity. Last December, Amazon tested the use of drones to deliver parcels.
You can find our overview of the growing threat to IoT devices, plus advice on protecting yourself from IoT malware here.
From extortion to ExPetr
The threat from ransomware continues to grow. Between April 2016 and March 2017, we blocked ransomware on the computers of 2,581,026 Kaspersky Lab customers. This is an increase of 11.4 per cent on the previous 12 months. You can read our full report on ransomware developments in 2016-17 here, but here are some of the key trends.
- The extortion model is here to say and we’re seeing growing competition between ransomware gangs. They’re also targeting countries that had previously been unaffected – where people are less well-prepared to deal with the threat.
- We’re seeing increasingly targeted ransomware attacks – quite simply because attacks on businesses are more profitable.
- Ransomware is growing in sophistication and diversity, offering many ready-to-go solutions to those with fewer skills, resources or time – through a growing and increasingly efficient underground eco-system.
- The establishment of a criminal-to-criminal infrastructure that is fuelling the development of easy-to-go, ad hoc tools to perform targeted attacks and extort money, making attacks more dispersed.
- Global initiatives to protect people from crypto-ransomware, such as No More Ransom, will continue to gain momentum.
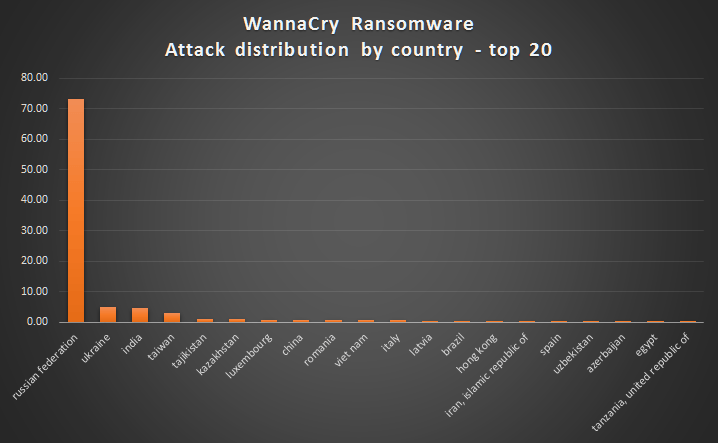
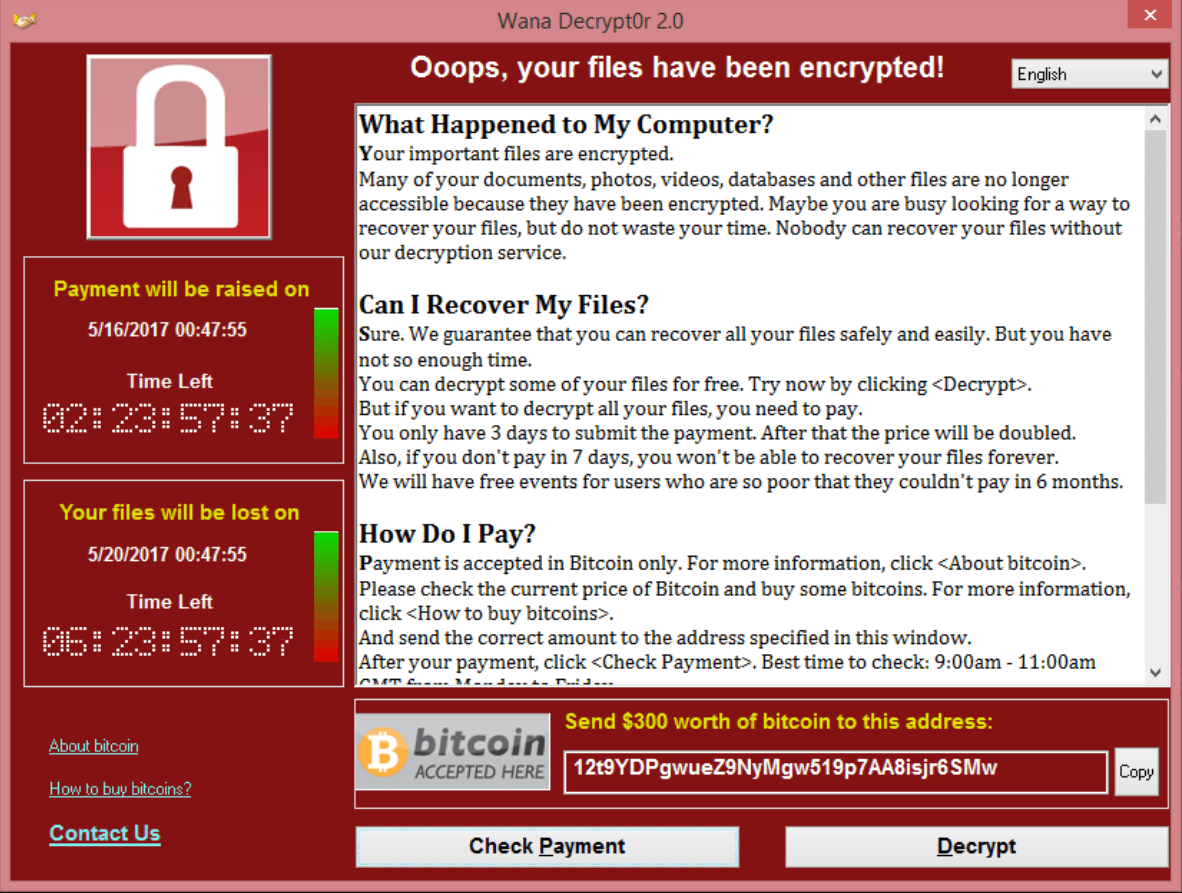
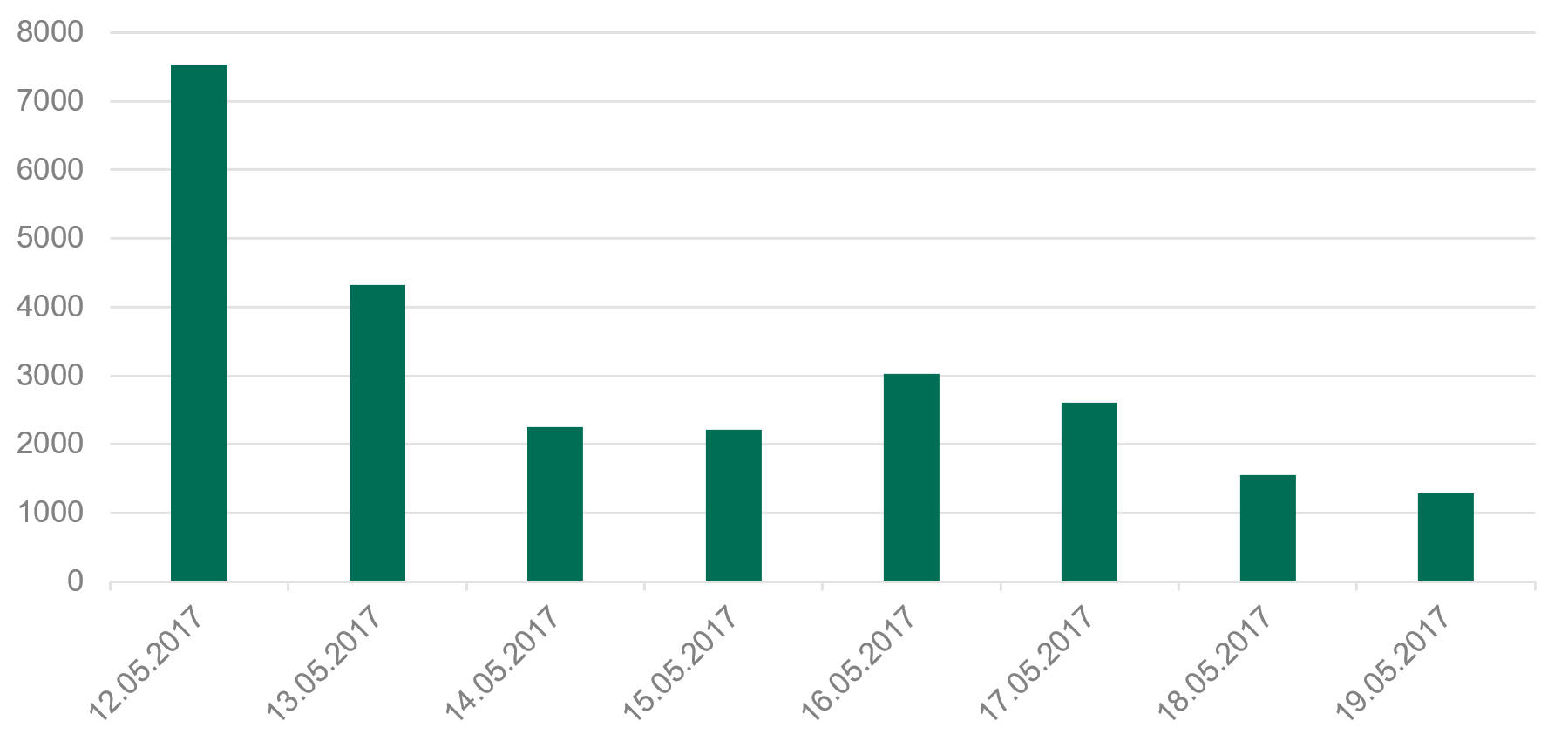
In May, we saw the biggest ransomware epidemic in history, called WannaCry. The largest number of attacks occurred in Russia, but there were also victims in Ukraine, India, Taiwan and many other countries – in total, 74 countries were affected. The malware spread very quickly – in just one day we saw more than 45,000 infections (Europol later estimated that upwards of 200,000 people had fallen victim to WannaCry).
WannaCry spread by taking advantage of a Windows exploit named ‘EternalBlue’ that relies on a vulnerability that Microsoft had patched in security update MS17-010. The Microsoft update had been released on 14 March, one month before EternalBlue exploit was made available in the ‘Shadow Brokers’ dump. However, many organisations hadn’t patched their systems, allowing the attackers to gain remote access to corporate systems. It then spread to other un-patched computers on the network.
Like other cryptors, WannaCry encrypts files on an infected computer and demands a ransom to decrypt them.
The attackers initially demanded $300, but this increased top $600 as the outbreak unfolded.
To ensure that the victims didn’t miss the warning, the malware changed the wallpaper and included instructions on how to locate the decryptor tool dropped by the malware.
It’s clear from our research that the quality of the WannaCry code is poor and the developers made many mistakes, enabling many of those infected to recover encrypted data. The way the attackers handled ransom payments limited their ability to capitalise on the spread of the worm. Multiple attempts were made to track transactions to the bitcoin wallets used by the attackers. Although estimates of how much money the attackers made vary, they run into tens of thousands, rather than hundreds
The timeline for attacks in the first week shows the impact of cyber-security efforts in combating the threat.
Not least among them was the discovery of a kill-switch. There’s a special check at the start of the code. It tries to connect to a hard-coded web site: if the connection fails the attack continues, if the connection is made, the code exits. By registering this domain and pointing it to a sinkhole server, a UK researcher was able to slow the infection of the worm.
A few days into the outbreak, Neel Mehta, a researcher at Google, posted a mysterious tweet using the #WannaCryptAttribution hashtag referring to a similarity between two code samples. One was a WannaCry sample from February 2017 that looked like an early variant of the worm. The other was a Lazarus sample from February 2017. Kaspersky Lab and others confirmed the similarity. It’s too early to say for sure if WannaCry was the work of the Lazarus group – more research is required to see if the dots join up.
You can find our original blog post here, our FAQ here and our comparison of the WannaCry and Lazarus samples here.
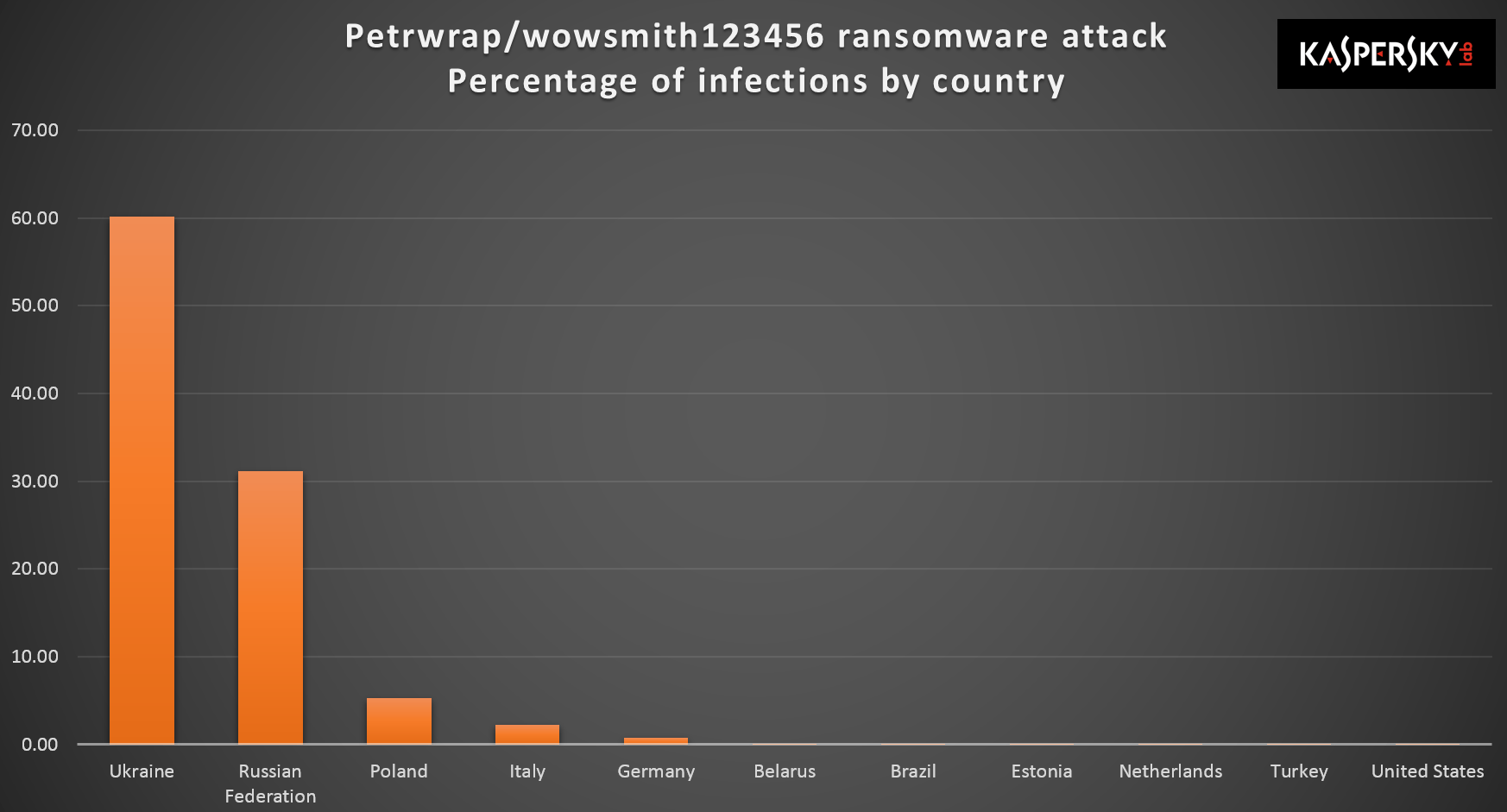
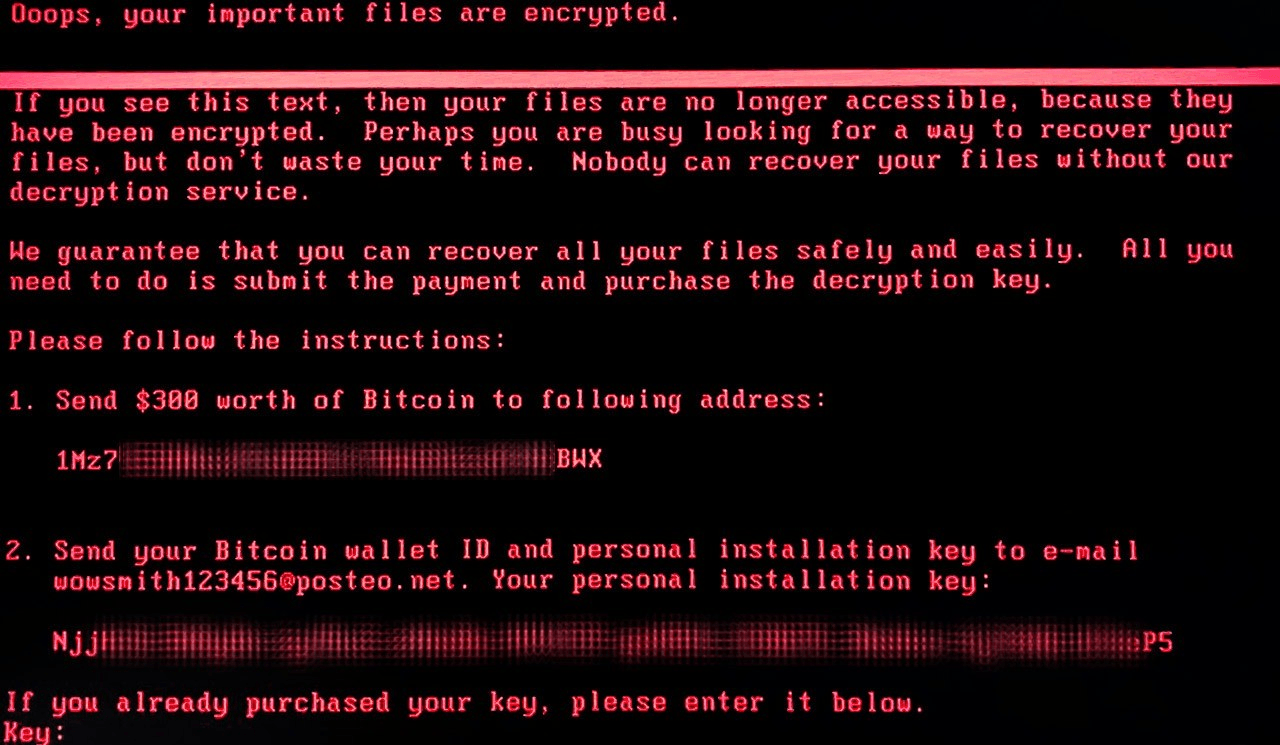
Towards the end of June, we saw reports of a new wave of ransomware attacks. The malware, which we called ExPetr (but known variously as Petya, Petrwrap and NotPetya) primarily targeted businesses in Ukraine, Russia and Europe – around 2,000 in total.
ExPetr uses a modified version of the EternalBlue exploit, as well as another exploit made public by the Shadow Brokers, called ‘EternalRomance’. The malware spread as an update to MeDoc – a Ukrainian accounting application – and through watering-hole attacks. Once inside the target organisation, the ransomware uses custom tools to extract credentials from the ‘lsass.exe’ process and passes them to PsExec or WMIC tools for further distribution within the network.
The malware waits for 10 minutes to an hour before re-booting the computer and then encrypts the MFT in NTFS partitions, overwriting the MBR with a customised loader containing a ransom demand.
ExPetr encrypts files as well as encrypting the MFT. The attackers demanded $300 in Bitcoins for the key to decrypt ransomed data, payable to a unified Bitcoin account. In principle – and unlike WannaCry – this technique could have worked because the attackers asked the victims to send their wallet numbers by e-mail to ‘wowsmith123456@posteo.net’, thus confirming the transactions. However, this e-mail account was quickly shut down, limiting the scope of the attackers to make money.
Following further analysis of the encryption routine, we concluded, as did some other researchers, that it isn’t possible for the attackers to decrypt the victims’ disks, even if payment is made. This suggests that ExPetr was a wiper masquerading as ransomware. There is even a suggestion that there might be a connection between ExPetr and the BlackEnergy KillDisk ransomware from 2015 and 2016.
ExPetr wasn’t the only ransomware that was distributed via MeDoc updates on 27 June 27. Another ransomware program, which we called FakeCry, was distributed to MeDoc customers at the same time. Our data indicate that 90 organisations received this malware, nearly all of them in Ukraine.
While the interface and messages closely resemble WannaCry, it is an entirely different malware family. We believe that FakeCry was designed with false flags in mind. One of the most interesting questions is whether FakeCry and ExPetr are related – as is suggested by the fact that both were distributed at the same time through MeDoc updates.
Here are our recommendations on how to protect against ransomware attacks.
- Run a robust anti-malware suite with embedded anti-ransomware protection (such as Kaspersky Lab’s System Watcher).
- Apply security updates for your operating system and applications as soon as they become available.
- Do not open attachments, or click on links, from untrusted sources.
- Backup sensitive data to external storage and keep it offline.
- Never pay the ransom. Not only does this fuel the next wave of ransomware attacks, but also there is no guarantee that the criminals will restore your data.

















IT threat evolution Q2 2017