
- IT threat evolution in Q1 2022
- IT threat evolution in Q1 2022. Non-mobile statistics
- IT threat evolution in Q1 2022. Mobile statistics
Targeted attacks
MoonBounce: the dark side of UEFI firmware
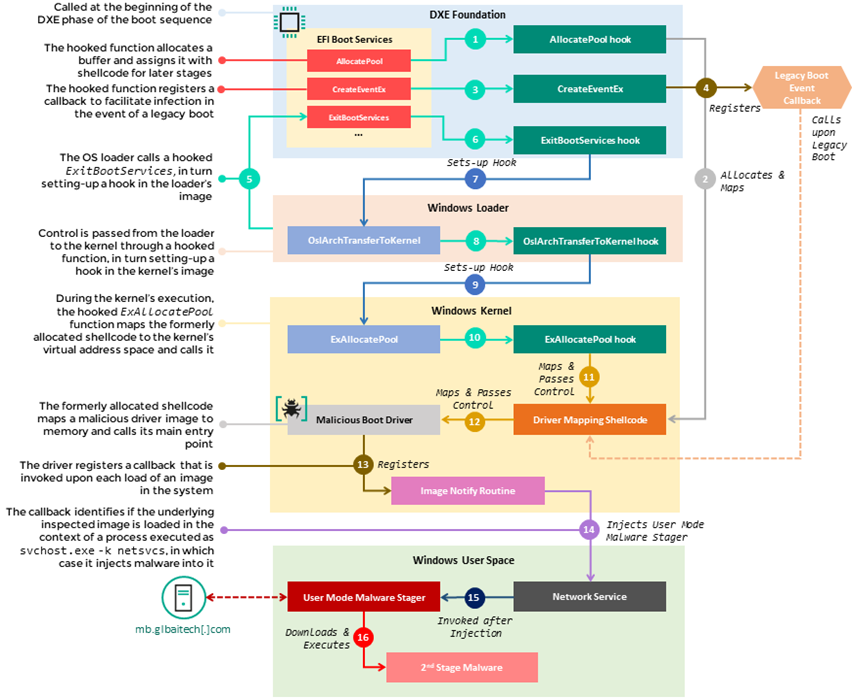
Late last year, we became aware of a UEFI firmware-level compromise through logs from our firmware scanner (integrated into Kaspersky products at the start of 2019). Further analysis revealed that the attackers had modified a single component in the firmware in a way that allowed them to intercept the original execution flow of the machine’s boot sequence and introduce a sophisticated infection chain.
Our analysis of the rogue firmware, and other malicious artefacts from the target’s network, revealed that the threat actor behind it had tampered with the firmware to embed malware that we call MoonBounce. Since the implant is located in SPI flash on the motherboard, rather than on the hard disk, it can persist even if someone formats or replaces the hard disk.
Moreover, the infection chain does not leave any traces on the hard drive, as its components operate in memory only – facilitating a fileless attack with a small footprint. We detected other non-UEFI implants in the targeted network that communicated with the same infrastructure.
We attribute this intrusion set to APT41, a threat actor widely believed to be Chinese speaking, because of the combination of the above findings with network infrastructure fingerprints and other TTPs.
Our report describes in detail how the MoonBounce implant works and what other traces of activity related to Chinese-speaking actors we were able to observe in the compromised network that could indicate a connection to APT41.
BlueNoroff continues its search for crypto-currency
In January, we reported a malicious campaign targeting companies that work with cryptocurrencies, smart contracts, decentralized finance and blockchain technology: the attackers are interested in fintech in general. We attribute the campaign, named SnatchCrypto, to the BlueNoroff APT group, the threat actor behind the 2016 attack on Bangladesh’s central bank.
The campaign has two goals: gathering information and stealing cryptocurrency. The attackers are mainly interested in collecting data on user accounts, IP addresses and session information; and they steal configuration files from programs that work directly with cryptocurrency and may contain account credentials. The attackers carefully study potential victims, sometimes monitoring them for months.
One approach they take is to manipulate popular browser extensions for managing crypto wallets. They change an extension’s source in the browser settings so that they can install a modified version from local storage instead of the legitimate version loading from the official web store. They also use the modified Metamask extension for Chrome to replace the transaction logic, enabling them to steal funds even from those who use hardware devices to sign cryptocurrency transfers.
The attackers study their victims carefully and use the information they find to frame social engineering attacks. Typically, they construct emails that masquerade as communications from legitimate venture companies, but with an attached, macro-enabled document. When opened, this document eventually downloads a backdoor.
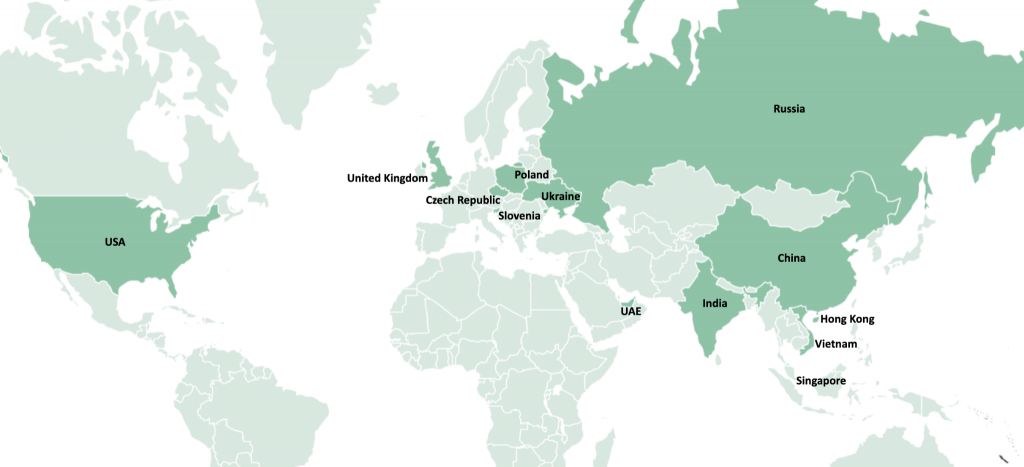
Our telemetry shows that there were victims in Russia, Poland, Slovenia, Ukraine, the Czech Republic, China, India, the US, Hong Kong, Singapore, the UAE and Vietnam. However, based on the shortened URL click history and decoy documents, we assess that there were more victims of this financially motivated attack campaign.
Roaming Mantis reaches Europe
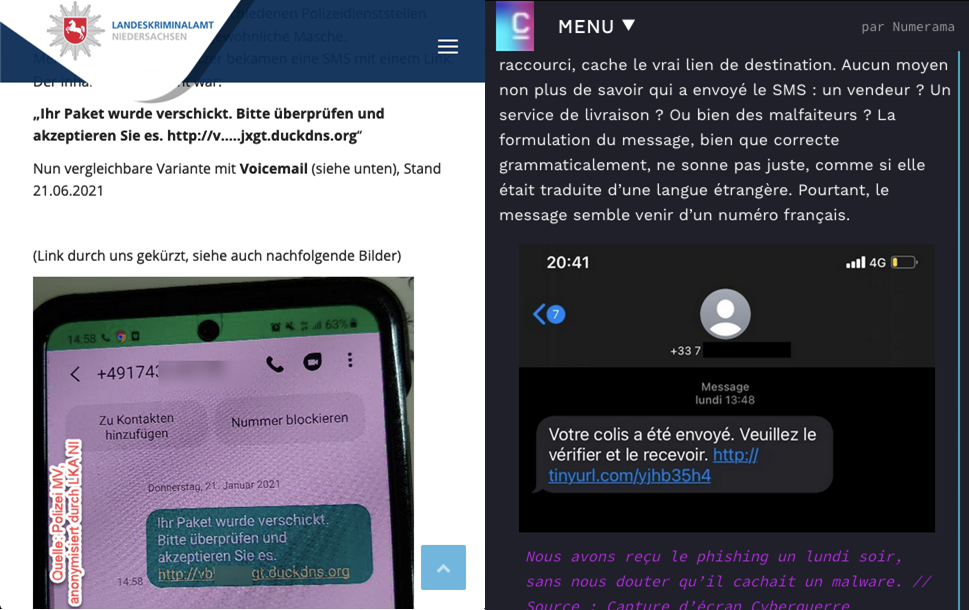
Since 2018, we have been tracking Roaming Mantis – a threat actor that targets Android devices. The group uses various malware families, including Wroba, and attack methods that include phishing, mining, smishing and DNS poisoning.
Typically, the smishing messages contain a very short description and a URL to a landing page. If someone clicks on the link and opens the landing page, there are two scenarios: the attackers redirect people using iOS to a phishing page imitating the official Apple website; on Android devices, they install the Wroba malware.
Our latest research indicates that Roaming Mantis has extended its geographic reach to include Europe. In the second half of 2021, the most affected countries were France, Japan, India, China, Germany and South Korea.

Territories affected by Roaming Mantis activity (download)
Cyberattacks related to the crisis in Ukraine
On January 14, attackers defaced 70 Ukrainian websites and posted the message “be afraid and expect the worst”. The defacement message on the Ministry of Foreign Affairs website, written in Ukrainian, Russian and Polish, suggested that personal data uploaded to the site had been destroyed. Subsequently, DDoS attacks hit some government websites. The following day, Microsoft reported that it had found destructive malware, dubbed WhisperGate, on the systems of government bodies and agencies that work closely with the Ukrainian government. It was not clear who was behind the attack, although the deputy secretary of Ukraine’s National Security and Defence Council stated that it was the work of UNC1151, a threat actor thought to be linked to Belarus.
WhisperKill, the wiper used during the WhisperGate campaign, wasn’t the only wiper to target organizations in Ukraine. On February 23, ESET published a tweet announcing new wiper malware targeting Ukraine. This wiper, named HermeticWiper by the research community, abuses legitimate drivers from the EaseUS Partition Master to corrupt the drivers of the compromised system. The compilation date of one of the identified samples was December 28 last year, suggesting that this destructive campaign had been planned for months.
The following day, Avast Threat Research announced the discovery of new Golang ransomware in Ukraine, which they dubbed HermeticRansom and which we call ElectionsGoRansom. This malware was discovered at around the same time as HermeticWiper; and publicly available information from the security community indicated that it was used in recent cyberattacks in Ukraine. The unsophisticated style and poor implementation suggest that attackers probably used this new ransomware as a smokescreen for the HermeticWiper attack.
On March 1, ESET published a blog post related to wipers used in Ukraine and to the ongoing conflict: in addition to HermeticWiper, this post introduced IsaacWiper, used to target specific computers previously compromised with another remote administration tool named RemCom, commonly used by attackers for lateral movement within compromised networks.
On March 22, the Ukraine CERT published a new alert about the DoubleZero wiper targeting the country. This is a new wiper, written in .NET, with no similarity to previously discovered wipers targeting Ukrainian entities. According to the CERT public statement, the campaign took place on March 17, when several targets in Ukraine received a ZIP archive with the filename “Вирус… крайне опасно!!!.zip” (translation: “Virus… extremely dangerous!!!.zip”).
On March 10, researchers from the Global Research and Analysis Team shared their insights into past and present cyberattacks in Ukraine. You can find the recording of the webinar here and a summary/Q&A here.
Lazarus uses Trojanized DeFi app to deliver malware
Earlier this year, we discovered a Trojanized DeFi app, compiled in November last year. The app contains a legitimate program, called DeFi Wallet, which saves and manages a cryptocurrency wallet, but it also implants a malicious file when executed. The malware is a fully featured backdoor designed to control compromised computers.
While it’s not clear how the threat actor tricked the victims into executing the Trojanized app, we suspect they sent a spear-phishing email or contacted them via social media.
We attribute the attacks, with high confidence, to the Lazarus group. We discovered numerous overlaps with other tools used by the same threat actor. The malware operator exclusively used compromised web servers located in South Korea for this attack. To take over the servers, we worked closely with a local CERT; as a result of this effort, we had the opportunity to investigate a Lazarus group C2 server.
The threat actor configured this infrastructure with servers set up as multiple stages. The first stage is the source for the backdoor, while the purpose of the second stage servers is to communicate with the implants. This represents a common scheme for Lazarus infrastructure.
We weren’t able to confirm the exact victims of this campaign, but the attack targets entities and/or individuals at a global level.
Other malware
Noreboot: faking an iPhone restart
One of the things you can do to protect yourself from advanced mobile spyware is to reboot your device on a daily basis. Typically, such programs do not have a permanent foothold in the system and will survive only until the device is next restarted – the vulnerabilities that allow an attacker to obtain such persistence are rare and very expensive.
However, researchers have recently found a way to fake a restart. Their technique, which they call Noreboot, is only a proof-of-concept, but if implemented by an attacker, it would allow them to achieve persistence on a target device.
For their lab demonstration, the researchers use an iPhone they had already infected (although they did not share the details of how they did this). When they shut down the device, using the power and volume buttons, the spyware displays an image of the iOS shutdown screen, faking the shutdown. After the user drags the power-off slider, the screen goes dark and the phone no longer responds to any of the user’s actions. When they press the power button again, the malware displays a perfect replica of the iOS boot animation.
Most people, of course, are not in the firing line of advanced threat actors; and a few simple precautions can help to keep you safe.
- Don’t jailbreak or root your device.
- Use a unique, complex passcode; and don’t leave your device unlocked when it’s unattended.
- Only download apps from the App Store or Google Play.
- Review app permissions and remove apps you no longer use.
- If you use Android, protect your device with a robust security solution.
For those who think they could be a potential target for advanced threat actors, Costin Raiu, director of the Global Research and Analysis Team at Kaspersky, has outlined some steps you can take to reduce and mitigate the risks.
Hunting for corporate credentials on ICS networks
In 2021, Kaspersky ICS CERT experts noticed a growing number of anomalous spyware attacks infecting ICS computers across the globe. Although the malware used in these attacks belongs to well-known commodity spyware families, the attacks stand out from the mainstream due to the very limited number of targets in each attack and the very short lifetime of each malicious sample.
By the time we detected this anomaly, it had become a trend: around 21.2 percent of all spyware samples blocked on ICS computers worldwide in the second half of 2021 were part of this new limited-scope, short-lifetime attack series. At the same time, depending on the region, up to one-sixth of all computers attacked with spyware had been attacked using this tactic.
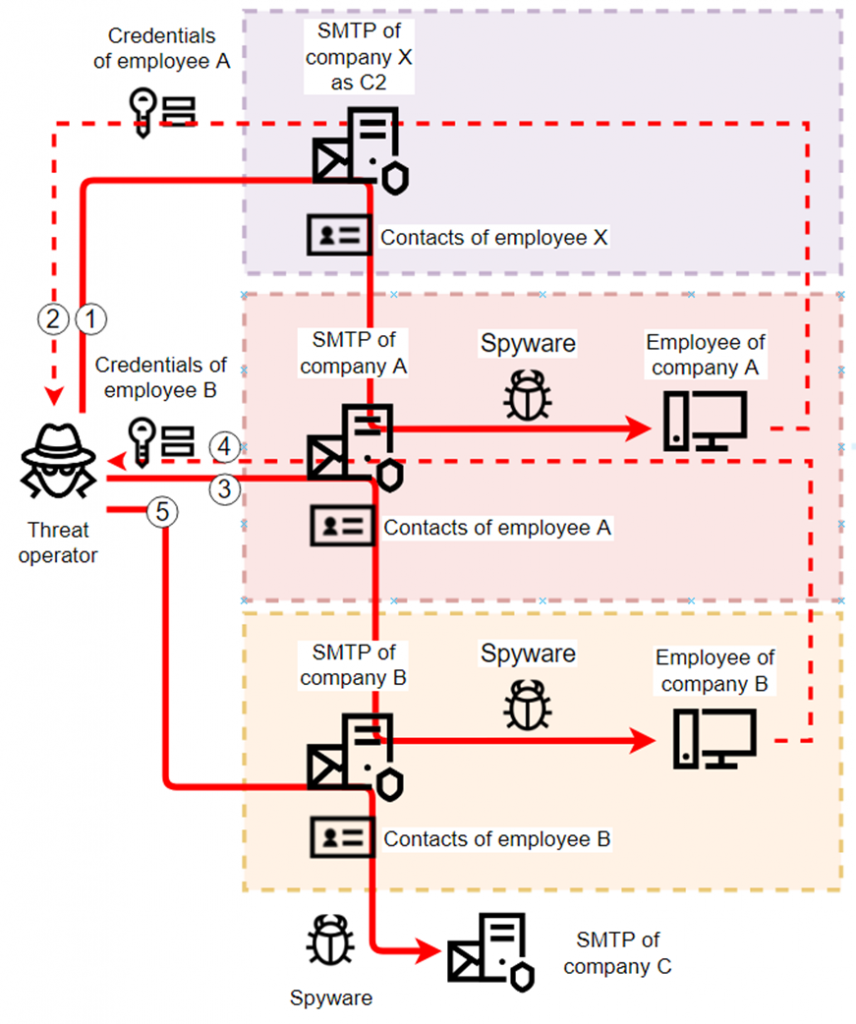
In the process of researching the anomaly, we noticed a large set of campaigns that spread from one industrial enterprise to another via hard-to-detect phishing emails disguised as correspondence from the victim organizations and abusing their corporate email systems to attack through the contact lists of compromised mailboxes.
Overall, we identified more than 2,000 corporate email accounts belonging to industrial companies that the attackers abused as next-attack C2 servers because of successful malicious operations of this type. They stole, or abused in other ways, many more (over 7,000 according to our estimates).
Lapsus$ group hacks Okta
In March, the Lapsus$ cybercrime group claimed that it had obtained “superuser/admin” access to internal systems at Okta. The dates of the screenshots posted by the group suggest that it had had access to Okta’s systems since January. Lapsus$ was previously responsible for a number of high-profile hacks, including the Brazil Ministry of Health, Impresa, Nvidia, Samsung and Ubisoft.
Okta develops and maintains identity and access management systems; in particular, it provides a single sign-on solution that is used by a large number of companies. Okta confirmed the breach and stated that 2.5 percent of its customers (amounting to 366 customers) were potentially affected; and said that it had contacted the affected customers.
A few days later, Lapsus$ mocked Okta’s response to the breach.
The phishing kit market
Phishing remains one of the key methods used by attackers to compromise their targets – both individuals and organizations. One of the most common tricks the phishers use is to create a fake page that mimics the legitimate site of a famous brand. They copy design elements from the real website, making it hard for people to distinguish fake pages from the real ones.
Such websites can be easily blocked or added to anti-phishing databases, so cybercriminals need to generate these pages quickly and in large numbers. Since it is time-consuming to create them from scratch each time, and not all cybercriminals have the necessary skills, they tend to use phishing kits. These are like model aircraft or vehicle assembly kits – ready-made templates and scripts that others can use to create phishing pages quickly and at scale. They are quite easy to use, so even inexperienced attackers without technical skills can make use of them.
Cybercriminals typically get phishing kits from dark web forums or from closed Telegram channels. Scammers working on a tight budget can find some basic open-source tools online. Those who are better off can commission Phishing-as-a-Service, which often includes various phishing kits.
Cybercriminals tend to use hacked official websites to host pages generated using the phishing kits, or rely on companies that offer free web hosting providers. The latter are constantly working to combat phishing and block fake pages, although phishing websites often only require a short period of activity to achieve their intended purpose, which is to collect the personal data of victims and send it to the criminals.

Number of unique domains using the TOP 10 phishing kits, August 2021 — January 2022 (download)
Last year alone, Kaspersky detected 469 individual phishing kits, enabling us to block around 1.2 million phishing pages. The chart shows the dynamics of the TOP 10 phishing kits we detected between August 2021 and January 2022, along with the number of unique domains where each phishing kit was encountered.
IT threat evolution Q1 2022





















Diego
Muito obrigado pela informação. Essencial e grande utilidade. Deus abençoe voces!!