
- IT threat evolution in Q3 2022
- IT threat evolution in Q3 2022. Non-mobile statistics
- IT threat evolution in Q3 2022. Mobile statistics
These statistics are based on detection verdicts of Kaspersky products received from users who consented to providing statistical data.
Quarterly figures
According to Kaspersky Security Network, in Q3 2022:
- A total of 5,623,670 mobile malware, adware, and riskware attacks were blocked.
- Droppers (Trojan-Dropper), accounting for 26.28% of detections, were the most common threat to mobile devices.
- 438,035 malicious installation packages were detected, of which:
- 35,060 packages were related to mobile banking Trojans,
- 2,310 packages were mobile ransomware Trojans.
Quarterly highlights
Judging by the number of attacks on mobile devices, cybercriminal activity stabilized in Q3 2022 after a gradual drop in the previous quarters. Over the three months, Kaspersky products prevented a total of 5.6 million mobile malware, adware, and riskware attacks.
Number of attacks targeting users of Kaspersky mobile solutions, Q1 2021 — Q3 2022 (download)
The new Triada Trojan, discovered inside a modified WhatsApp build, was an interesting find. It was notable for spreading via ads inside the popular Snaptube app and through the Vidmate internal store. Once on a device, the Trojan decrypts and runs a payload, which downloads and runs further malicious modules. The modules can display ads, subscribe the user to paid services, or download and run other malicious modules. Besides that, the Trojan steals various keys from the legitimate WhatsApp, potentially hijacking the account.
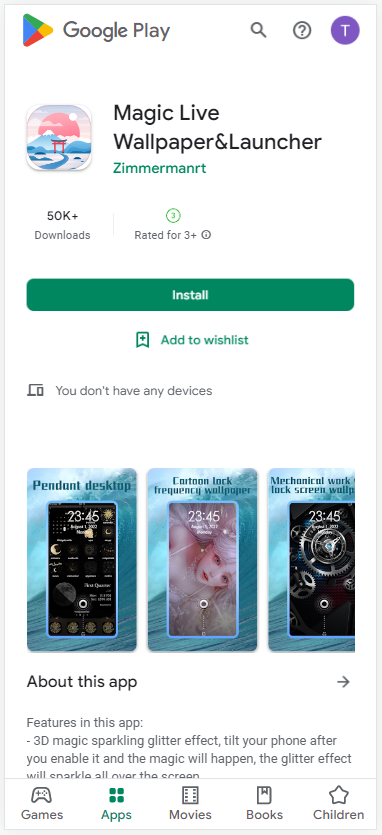
The Harly Trojan subscribers were another malware family spread via legitimate channels. These are published in Google Play under the guise of authentic apps, subscribing the unknowing user to paid services once installed. We have discovered 200 malicious applications of this type starting in 2020, and a total count of installations at the time of writing this report had exceeded 5 million.
One of the most recently detected Harly-type apps in Google Play, with more than 50,000 installations.
Google Play keeps getting new banking Trojans, such as new versions of the Trojan dropper that downloads and runs Sharkbot.
Despite a general decline in the number of mobile attacks, we can see that cybercriminals are using increasingly smarter tricks to deliver malware to user devices.
Mobile threat statistics
In Q3 2022, Kaspersky detected 438,035 malicious installation packages, which is 32,351 more than in the previous quarter and down 238,155 against Q3 2021.
Number of detected malicious installation packages, Q3 2021 — Q3 2022 (download)
Distribution of detected mobile malware by type
Distribution of newly detected mobile malware by type, Q2 and Q3 2022 (download)
Threats in the Trojan-Dropper class ranked first among all threats detected in Q3, with 26.28%, exceeding the previous quarter’s figure by 22.15 percentage points. Nearly half (45.33%) of all detected threats of that type belonged to the Ingopack family. These were followed by banking Trojan droppers from Wroba (41.24%) and Hqwar families (5.98%).
AdWare, the ex-leader, moved 2.5 percentage points down the rankings to second place with a share of 22.78%. A fourth of all detected threats of that class belonged to the Aldo family (25.64%).
Third place was taken by various Trojans with a cumulative share of 16.01%, which was 4.48 percentage points lower than in the previous quarter. Half of all detected threats of that class were objects from the Boogr family (50.16%).
Top 20 mobile malware programs
Note that the malware rankings below exclude riskware or PUAs, such as RiskTool or adware.
| Verdict | %* | |
| 1 | DangerousObject.Multi.Generic | 22.58 |
| 2 | Trojan.AndroidOS.Generic | 14.59 |
| 3 | Trojan-Spy.AndroidOS.Agent.aas | 8.51 |
| 4 | Trojan-SMS.AndroidOS.Fakeapp.d | 6.95 |
| 5 | Trojan.AndroidOS.GriftHorse.l | 5.57 |
| 6 | Trojan-Dropper.AndroidOS.Hqwar.hd | 2.94 |
| 7 | DangerousObject.AndroidOS.GenericML | 2.90 |
| 8 | Trojan-Dropper.AndroidOS.Wroba.o | 2.46 |
| 9 | Trojan-Dropper.AndroidOS.Agent.sl | 2.21 |
| 10 | Trojan-Downloader.AndroidOS.Necro.d | 1.93 |
| 11 | Trojan-Dropper.AndroidOS.Agent.rv | 1.84 |
| 12 | Trojan-Banker.AndroidOS.Bian.h | 1.71 |
| 13 | Trojan-Downloader.AndroidOS.Agent.kx | 1.69 |
| 14 | Trojan-Dropper.AndroidOS.Hqwar.hc | 1.66 |
| 15 | Trojan.AndroidOS.Hiddad.hh | 1.52 |
| 16 | Trojan.AndroidOS.GriftHorse.ah | 1.45 |
| 17 | Trojan-SMS.AndroidOS.Agent.ado | 1.41 |
| 18 | Trojan-Dropper.AndroidOS.Hqwar.gen | 1.39 |
| 19 | Trojan-Dropper.AndroidOS.Triada.az | 1.35 |
| 20 | Trojan.AndroidOS.Soceng.f | 1.33 |
* Unique users attacked by this malware as a percentage of all attacked users of Kaspersky mobile solutions.
First and second places went to DangerousObject.Multi.Generic (22.58%) and Trojan.AndroidOS.Generic (14.59%), respectively, which are verdicts we use for malware detected with cloud technology. Cloud technologies are used when the antivirus databases lack data for detecting a piece of malware, but the company’s cloud already contains information about the object. This is essentially how the latest malware types are detected.
Trojan-Spy.AndroidOS.Agent.aas (8.51%), an evil twin of WhatsApp with a spy module built in, rose to third position. Trojan-SMS.AndroidOS.Fakeapp.d slid from second to fourth place with 6.95%. This malware is capable of sending text messages and calling predefined numbers, displaying ads and hiding its icon. Members of the Trojan.AndroidOS.GriftHorse family, which subscribe the user to premium SMS services, took fifth and sixteenth places.
Malware from the Trojan-Dropper.AndroidOS.Hqwar family, used for unpacking and running various banking Trojans, occupied sixth, fourteenth, and eighteenth places. These attacked a combined 6% of all users who encountered malware.
The verdict of DangerousObject.AndroidOS.GenericML came seventh with 2.90%. This verdict is assigned to files recognized as malicious by our machine-learning systems. Eighth place was occupied by Trojan-Dropper.AndroidOS.Agent.sl (2.46%), a dropper that unpacks and runs the banking Trojan from the Roaming Mantis campaign. Roaming Mantis mainly attacks users in Japan and France. Another banking Trojan dropper, Trojan-Dropper.AndroidOS.Agent.sl, sunk to ninth place with 2.21%.
Trojan-Downloader.AndroidOS.Necro.d, used for downloading and running other forms of malware on infected devices, jumped from sixteenth to tenth place with 1.93%. Trojan-Dropper.AndroidOS.Agent.rv, a dropper that unpacks and runs various types of malware, took eleventh place with 1.84%.
Twelfth place saw the arrival of the banking Trojan, Trojan-Banker.AndroidOS.Bian.h, with 1.71%. Trojan-Downloader.AndroidOS.Agent.kx, an adware dropper, accounted for 1.69%, climbed from twentieth to thirteenth place. Trojan.AndroidOS.Hiddad.hh, an adware Trojan that mostly attacks users in Russia, Kazakhstan, and Ukraine, was fifteenth with 1.52%.
Trojan-SMS.AndroidOS.Agent.ado, known for sending text messages to premium-rate shortcodes, remained seventeenth with 1.41%. Nineteenth place, with 1.35%, was occupied by Trojan-Dropper.AndroidOS.Triada.az, a type of malware that decrypts and runs a payload capable of displaying ads on the lock screen, opening new browser tabs, gathering device information, and dropping other malicious code.
The last in the rankings (previously thirteenth) is Trojan.AndroidOS.Soceng.f with 1,33%. It sends text messages to the user’s contacts, deletes files on the memory card, and overlays the interfaces of popular apps with its own window.
Geography of mobile threats
TOP 10 countries and territories by share of users attacked by mobile malware
| Countries and territories* | %** | |
| 1 | Iran | 81.37 |
| 2 | Yemen | 18.91 |
| 3 | Saudi Arabia | 12.68 |
| 4 | Oman | 11.99 |
| 5 | Algeria | 11.93 |
| 6 | Kenya | 11.42 |
| 7 | Nigeria | 10.72 |
| 8 | India | 10.65 |
| 9 | Egypt | 9.39 |
| 10 | Ecuador | 8.66 |
* Countries and territories with relatively few users of Kaspersky mobile security solutions (under 10,000) have been excluded from the rankings.
** Unique users attacked as a percentage of all users of Kaspersky mobile security solutions in the country.
The countries with the largest shares of attacked users and the most widespread threats in these regions remained unchanged in Q3 2022.
Iran came first with a record 81.37%, still plagued by the annoying adware modules from the AdWare.AndroidOS.Notifyer and AdWare.AndroidOS.Fyben families. Yemen, where users were attacked mostly by Trojan-Spy.AndroidOS.Agent.aas, stayed at second place with 18,91%. In Saudi Arabia, which came third with 12.68%, users most commonly encountered adware from the AdWare.AndroidOS.Adlo and AdWare.AndroidOS.Fyben families.
Mobile banking Trojans
The number of detected installation packages for mobile banking Trojans dropped to 35,060. This figure represents a decrease of 20,554 from Q2 2022, but a decrease of 22,963 from Q3 2021.
Two-thirds (66.20%) of the detected banking Trojan installation packages belonged to the Trojan-Banker.AndroidOS.Bray family. These were followed by Trojan-Banker.AndroidOS.Bian with 5,46% and Trojan-Banker.AndroidOS.Fakecalls with 4,59%.
Number of installation packages for mobile banking Trojans detected by Kaspersky, Q3 2021 — Q3 2022 (download)
Top 10 most common mobile bankers
| Verdict | %* | |
| 1 | Trojan-Banker.AndroidOS.Bian.h | 29.61 |
| 2 | Trojan-Banker.AndroidOS.Anubis.t | 10.67 |
| 3 | Trojan-Banker.AndroidOS.Svpeng.q | 7.72 |
| 4 | Trojan-Banker.AndroidOS.Gustuff.d | 5.35 |
| 5 | Trojan-Banker.AndroidOS.Asacub.ce | 4.18 |
| 6 | Trojan-Banker.AndroidOS.Agent.eq | 3.94 |
| 7 | Trojan-Banker.AndroidOS.Agent.ep | 3.21 |
| 8 | Trojan-Banker.AndroidOS.Agent.cf | 2.51 |
| 9 | Trojan-Banker.AndroidOS.Faketoken.z | 2.12 |
| 10 | Trojan-Banker.AndroidOS.Hqwar.t | 2.08 |
* Unique users attacked by this malware as a percentage of all Kaspersky mobile security solution users who encountered banking threats.
The three most-attacked countries in terms of affected users remained the same as in Q2 2022.
Geography of mobile bankers
TOP 10 countries and territories by shares of users attacked by mobile banking Trojans
| Countries and territories* | %** | |
| 1 | Saudi Arabia | 1.36 |
| 2 | Spain | 1.05 |
| 3 | Australia | 0.79 |
| 4 | Turkey | 0.41 |
| 5 | Switzerland | 0.20 |
| 6 | Japan | 0.11 |
| 7 | France | 0.08 |
| 8 | Colombia | 0.08 |
| 9 | South Korea | 0.07 |
| 10 | Italy | 0.04 |
* Countries and territories with relatively few users of Kaspersky mobile security solutions (under 10,000) have been excluded from the rankings.
** Unique users attacked by mobile banking Trojans as a percentage of all Kaspersky mobile security solution users in the country.
Saudi Arabia had the largest share (1.36%) of unique users who came across mobile financial threats in Q3 2022. Trojan-Banker.AndroidOS.Bian.h accounted for more than 99% of attacks in that country. Spain, formerly the hardest-hit country, had the second largest share (1.05%), with 93.46% of attacks linked to the same malware type. Australia again had the third-largest (0.79%) share, with 98.27% of attacks there involving Trojan-Banker.AndroidOS.Gustuff.d.
Mobile ransomware Trojans
We detected 2,310 mobile Trojan ransomware installers in Q3 2022, a decrease of 1,511 from Q2 2022 and a decrease of 3,847 year on year.
Number of installation packages for mobile ransomware Trojans detected by Kaspersky, Q3 2021 — Q3 2022 (download)
Top 10 most common mobile ransomware
| Verdict | %* | |
| 1 | Trojan-Ransom.AndroidOS.Pigetrl.a | 58.73 |
| 2 | Trojan-Ransom.AndroidOS.Small.as | 4.52 |
| 3 | Trojan-Ransom.AndroidOS.Rkor.cw | 4.17 |
| 4 | Trojan-Ransom.AndroidOS.Rkor.cl | 1.92 |
| 5 | Trojan-Ransom.AndroidOS.Fusob.h | 1.92 |
| 6 | Trojan-Ransom.AndroidOS.Rkor.cm | 1.60 |
| 7 | Trojan-Ransom.AndroidOS.Rkor.da | 1.60 |
| 8 | Trojan-Ransom.AndroidOS.Rkor.bi | 1.60 |
| 9 | Trojan-Ransom.AndroidOS.Rkor.cx | 1.57 |
| 10 | Trojan-Ransom.AndroidOS.Small.ce | 1.32 |
* Unique users attacked by the malware as a percentage of all Kaspersky mobile security solution users attacked by ransomware Trojans.
Geography of mobile ransomware
TOP 10 countries and territories by share of users attacked by mobile ransomware Trojans
| Countries and territories* | %** | |
| 1 | Yemen | 0.28 |
| 2 | Kazakhstan | 0.15 |
| 3 | Saudi Arabia | 0.02 |
| 4 | Jordan | 0.02 |
| 5 | Switzerland | 0.02 |
| 6 | Azerbaijan | 0.01 |
| 7 | Kyrgyzstan | 0.01 |
| 8 | Egypt | 0.01 |
| 9 | Iran | 0.01 |
| 10 | Algeria | 0.01 |
* Excluded from the rankings are countries and territories with relatively few (under 10,000) Kaspersky mobile security users.
** Unique users attacked by ransomware Trojans as a percentage of all Kaspersky mobile security solution users in the country or territory.
Yemen (0.28%), Kazakhstan (0.15%) and Saudi Arabia (0.02%) had the largest shares of users attacked by mobile ransomware Trojans. Users in Yemen and Saudi Arabia most often encountered Trojan-Ransom.AndroidOS.Pigetrl.a, while users in Kazakhstan were attacked mainly by members of the Trojan-Ransom.AndroidOS.Rkor family.


















IT threat evolution in Q3 2022. Mobile statistics