
- IT threat evolution in Q1 2022
- IT threat evolution in Q1 2022. Non-mobile statistics
- IT threat evolution in Q1 2022. Mobile statistics
These statistics are based on detection verdicts of Kaspersky products received from users who consented to providing statistical data.
Quarterly figures
According to Kaspersky Security Network, in Q1 2022:
- 6,463,414 mobile malware, adware and riskware attacks were blocked.
- The largest share of all detected mobile threats accrued to RiskTool programs — 48.75%.
- 516,617 malicious installation packages were detected, of which:
- 53,947 packages were related to mobile banking trojans,
- and 1,942 packages were mobile ransomware trojans.
Quarterly highlights
In Q1 2022, the level of activity among cybercriminals remained roughly the same as it was at the end of 2021 when comparing the number of attacks on mobile devices. But in general, the number of attacks is still on a downward trend.
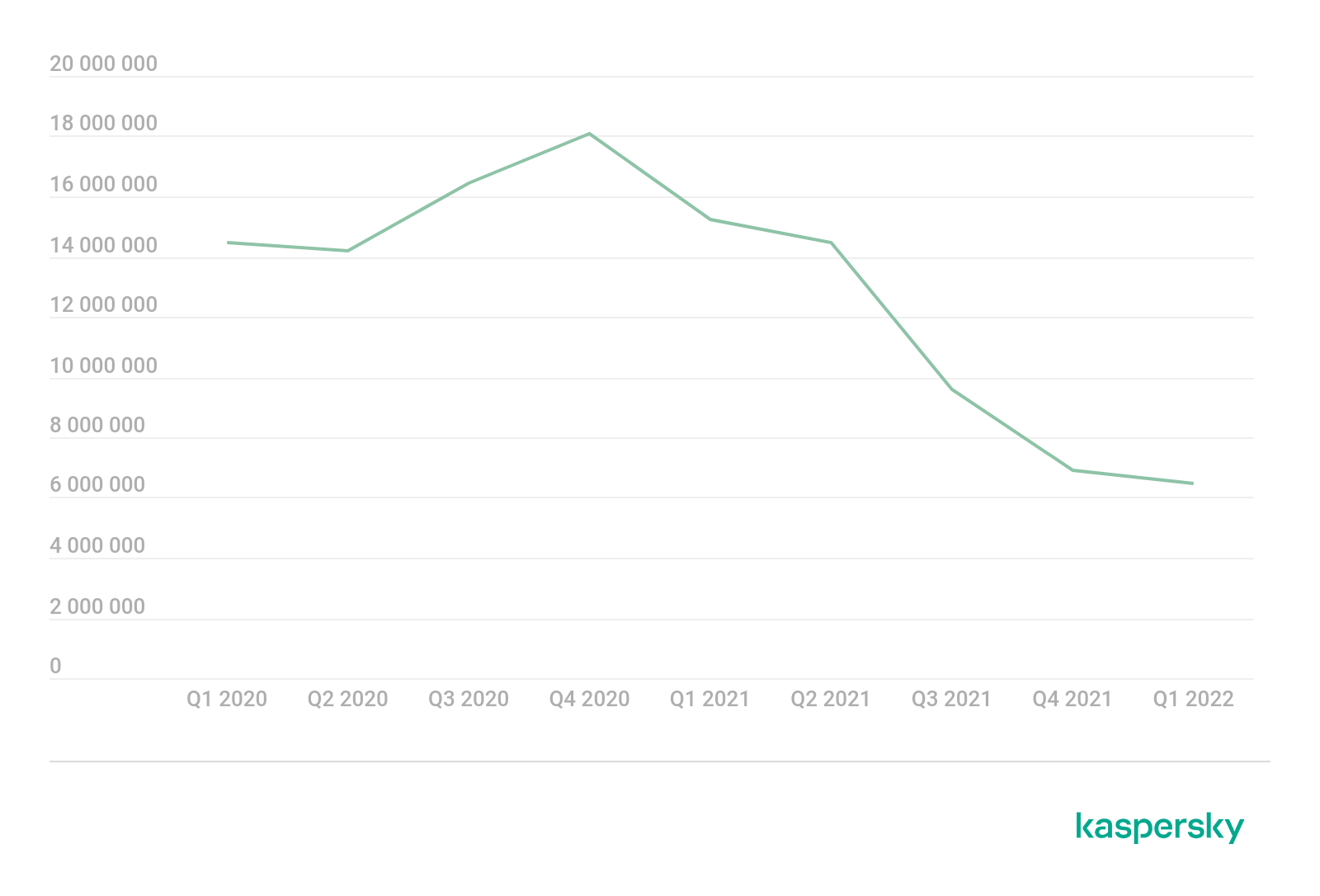
Number of attacks targeting users of Kaspersky mobile solutions, Q1 2020 — Q1 2022 (download)
One of the schemes used by scammers which has been becoming more popular since last year are scam apps for receiving social benefits. The mobile apps redirect to a webpage where users are prompted to enter personal data and shown a large sum of money they’re supposedly entitled to. In order to claim their benefits however, users are told they need to pay a commission to cover the transfer cost or legal assistance. Once the money has been transferred, the app’s objective is considered achieved, and the user receives nothing in return.
 |
 |
 |
 |
Scam apps targeting Russian-speaking users
Another common scheme deployed by scammers are fraudulent trading apps which grant access to an investment platform for certain gas stocks. The app brings the user to a fake website where you can “raise your investment capital”. Needless to say, all the money invested is sent straight to the cybercriminals.
 |
 |
 |
|
Other types of fraudulent apps begin charging a hefty weekly subscription fee a few days after the app is installed or even sign the user up for premium SMS subscriptions.
Keto diet app for meal planning which deducts money from the user’s bankcard without receiving prior consent
Other finds which stood out this quarter were various apps for taking out payday loans targeting users in Mexico and India. In our system of classification, these apps belong to a family of potentially unwanted software called RiskTool.AndroidOS.SpyLoan, which request access to user’s text messages, contacts list and photos. If a payment is late, debt collectors can begin calling people from the user’s contacts list or blackmail the user by threatening to disclose their personal information.
We observed a similar case in Brazil, where people were encouraged to install an app to take out payday loans which locks users out of their phones if they miss a payment.
Mobile threat statistics
In Q1 2022, Kaspersky detected 516,617 malicious installation packages, which is 79,448 fewer than the previous quarter and down 935,043 against Q1 2021.
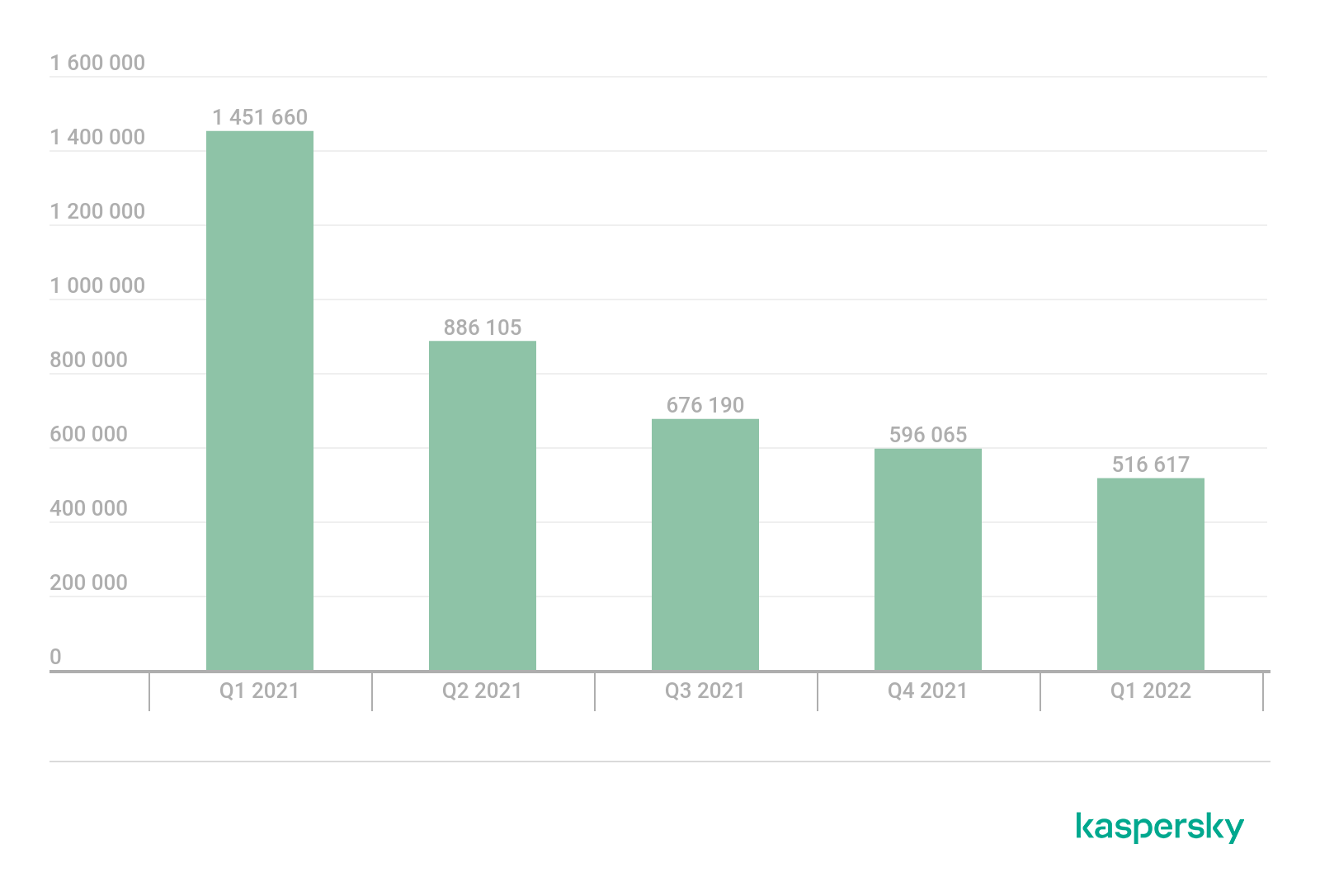
Number of detected malicious installation packages, Q1 2021 — Q1 2022 (download)
Distribution of detected mobile malware by type
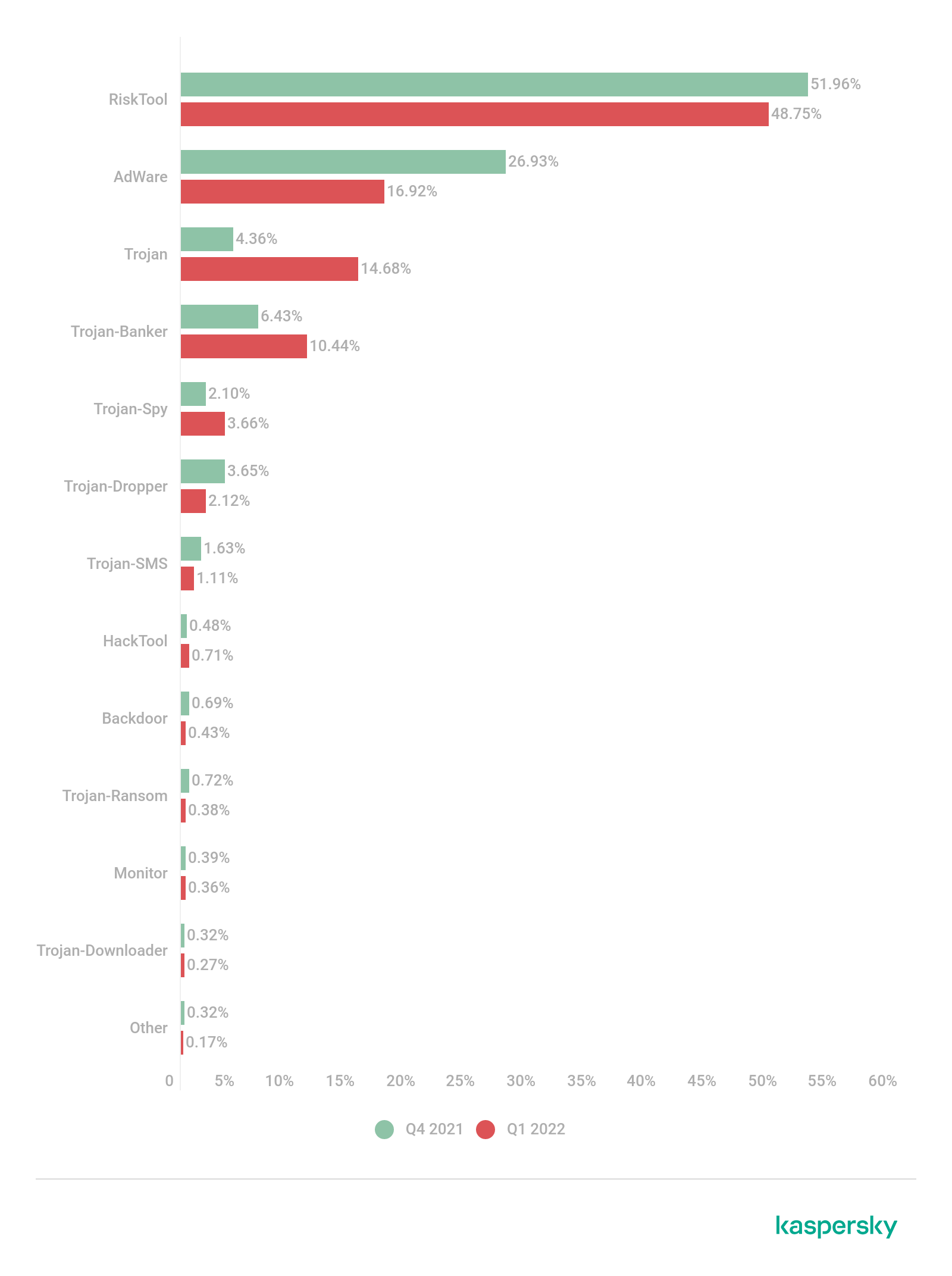
Distribution of newly detected mobile malware by type, Q4 2021 and Q1 2022 (download)
Adware apps came second (16.92%), which also saw a decrease of 10.01 p.p. The worst offenders belonged to the Ewind family (28.89%), which were encountered more frequently than any other adware we detected. It’s followed by Adlo (19.84%) and HiddenAd (12.46%) families.
Third place was taken by various trojans whose share increased by 10.32 p.p. to 14.68%. The trojan families that had the greatest impact were Mobtes (44.35%), Piom (32.61%) and Boogr (14.32%).
Top 20 mobile malware programs
Note that the malware rankings below exclude riskware or PUAs, such as RiskTool or adware.
| Verdict | %* | |
| 1 | DangerousObject.Multi.Generic | 20.45 |
| 2 | Trojan.AndroidOS.Fakemoney.d | 10.73 |
| 3 | Trojan-SMS.AndroidOS.Fakeapp.d | 7.82 |
| 4 | Trojan-SMS.AndroidOS.Fakeapp.c | 5.36 |
| 5 | Trojan-Spy.AndroidOS.Agent.aas | 4.93 |
| 6 | Trojan.AndroidOS.Fakeapp.ed | 4.45 |
| 7 | Trojan.AndroidOS.Fakemoney.g | 3.28 |
| 8 | Trojan-Dropper.AndroidOS.Agent.sl | 2.94 |
| 9 | DangerousObject.AndroidOS.GenericML | 2.55 |
| 10 | Trojan.AndroidOS.Fakeapp.dw | 2.40 |
| 11 | Trojan-Ransom.AndroidOS.Pigetrl.a | 2.14 |
| 12 | Trojan.AndroidOS.Soceng.f | 2.14 |
| 13 | Trojan.AndroidOS.Fakemoney.i | 2.13 |
| 14 | Trojan-Downloader.AndroidOS.Agent.kx | 1.63 |
| 15 | Trojan-SMS.AndroidOS.Agent.ado | 1.62 |
| 16 | Trojan.AndroidOS.Fakeapp.ea | 1.55 |
| 17 | Trojan-Downloader.AndroidOS.Necro.d | 1.47 |
| 18 | Trojan-Dropper.AndroidOS.Hqwar.gen | 1.36 |
| 19 | Trojan.AndroidOS.GriftHorse.l | 1.26 |
| 20 | SMS-Flooder.AndroidOS.Dabom.c | 1.19 |
* Unique users attacked by this malware as a percentage of all attacked users of Kaspersky mobile solutions.
The malware rating for Q1 2022 featured many new arrivals, which we discussed in the quarterly-highlights section. But let’s go back to the top of the ranking. First place was defended by the traditional title-holder DangerousObject.Multi.Generic (20.45%), which is a verdict we use to describe malware detected using cloud technology. The trojan identified as Trojan.AndroidOS.Fakemoney.d (10.73%) moved up from third to second place. Other members of this family have also occupied seventh and thirteenth place in the rating. These are fraudulent apps that invite users to fill out a fake application for social benefits. The majority of users targeted in these attacks live in Russia, Kazakhstan and Ukraine.
The trojans in third and fourth place (7.82% and 5.36%) are members of the Trojan-SMS.AndroidOS.Fakeapp family. This type of malware is able to send text messages and call specified numbers, display ads and hide its icon on the device. Fifth place is taken by a trojan referred to as Trojan-Spy.AndroidOS.Agent.aas (4.93%), which is a modification of the popular WhatsApp Messenger containing a spy tool.
Trojan.AndroidOS.Fakeapp.ed (4.45%) took sixth place. This verdict refers to a category of fraudulent apps which target users in Russia by posing as a stock-trading platform for investing in gas.
Eighth place is occupied by Trojan-Dropper.AndroidOS.Agent.sl (2.94%), a dropper that installs and runs banking trojans on devices. The majority of users attacked by it were located in Russia, Germany and Turkey.
Ninth place was taken by the verdict DangerousObject.AndroidOS.GenericML (2.55%). These verdicts are assigned to files recognized as malicious by our machine-learning systems. The verdict in tenth place is Trojan.AndroidOS.Fakeapp.dw (2.40%), which is used to describe various scam apps, such as apps claiming to offer an additional source of income.
The trojan in eleventh place is Trojan-Ransom.AndroidOS.Pigetrl.a (2.14%), which locks the device’s screen and asks for a code to unlock it. The trojan doesn’t provide any instructions on how to obtain this code, and the code itself is embedded in the body of the malware.
The trojan which came twelfth was Trojan.AndroidOS.Soceng.f (2.14%), which sends text messages to people in your contacts list, deletes files on the SD card, and overlays the interfaces of popular apps with its own window. The trojan in fourteenth place is Trojan-Downloader.AndroidOS.Agent.kx (1.63%), which downloads adware.
A trojan known as Trojan-SMS.AndroidOS.Agent.ado (1.62%), which sends text messages to short premium-rate numbers is in fifteenth place. The next row down is occupied by Trojan.AndroidOS.Fakeapp.ea (1.55%), another fraudulent trading app for investing in gas.
The trojan in seventeenth place is Trojan-Downloader.AndroidOS.Necro.d (1.47%), which is used to download and run other forms of malware on an infected device. It is followed by Trojan-Dropper.AndroidOS.Hqwar.gen (1.36%), which is used to unpack and run various banking trojans on a device.
The trojan in nineteenth place is Trojan.AndroidOS.GriftHorse.l (1.26%) — another fraudulent app mentioned in the quarterly-highlight section. It subscribes users to premium text-messaging services. The next line is occupied by SMS-Flooder.AndroidOS.Dabom.c (1.19%), which has the main aim of bombarding people with spam text messages.
Geography of mobile threats
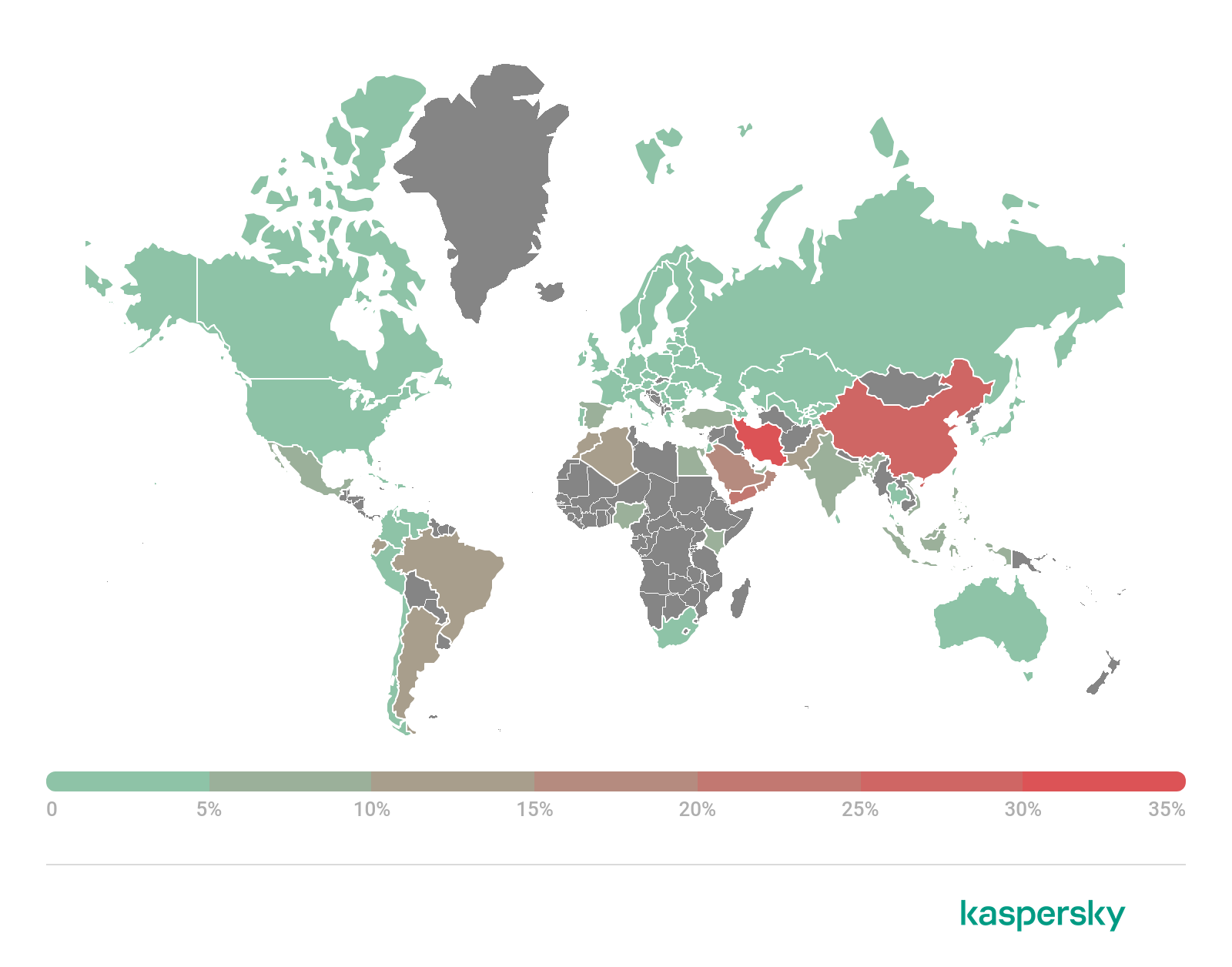
Map of attempts to infect mobiles with malware, Q1 2022 (download)
| Countries* | %** | |
| 1 | Iran | 35.25 |
| 2 | China | 26.85 |
| 3 | Yemen | 21.23 |
| 4 | Oman | 19.01 |
| 5 | Saudi Arabia | 15.81 |
| 6 | Algeria | 13.89 |
| 7 | Argentina | 13.59 |
| 8 | Brazil | 10.80 |
| 9 | Ecuador | 10.64 |
| 10 | Morocco | 10.56 |
* Countries with relatively few users of Kaspersky mobile security solutions (under 10,000) are excluded from the ranking.
** Share of unique users attacked as a percentage of all users of Kaspersky mobile security solutions in the country.
In the rating for Q1 2022, Iran (35.25%) is still the country with the most infected devices. The most frequently encountered threat in this country was annoying adware from the Notifyer and Fyben families. China came second (26.85%), where the most frequently encountered threats were Trojan.AndroidOS.Boogr.gsh and Trojan.AndroidOS.Najin.a. Third place was taken by Yemen (21.23%), where the most widespread mobile threat was Trojan-Spy.AndroidOS.Agent.aas spyware.
Mobile banking trojans
The number of installation packages for mobile banking trojans, which dipped in the first three quarters of 2021, continued to grow: we detected 53,947 of these packages in the reporting period, which is 15,594 up on Q4 2021 and a year-on-year increase of 28,633 against Q1 2021. The increase in the number of packages is largely due to the Trojan-Banker.AndroidOS.Bray family — its share accounted for 80.89% of all mobile banking trojans detected. The second most frequently detected package was Trojan-Banker.AndroidOS.Fakecalls (8.75%), followed by Trojan-Banker.AndroidOS.Cebruser (2.52%) in third place.
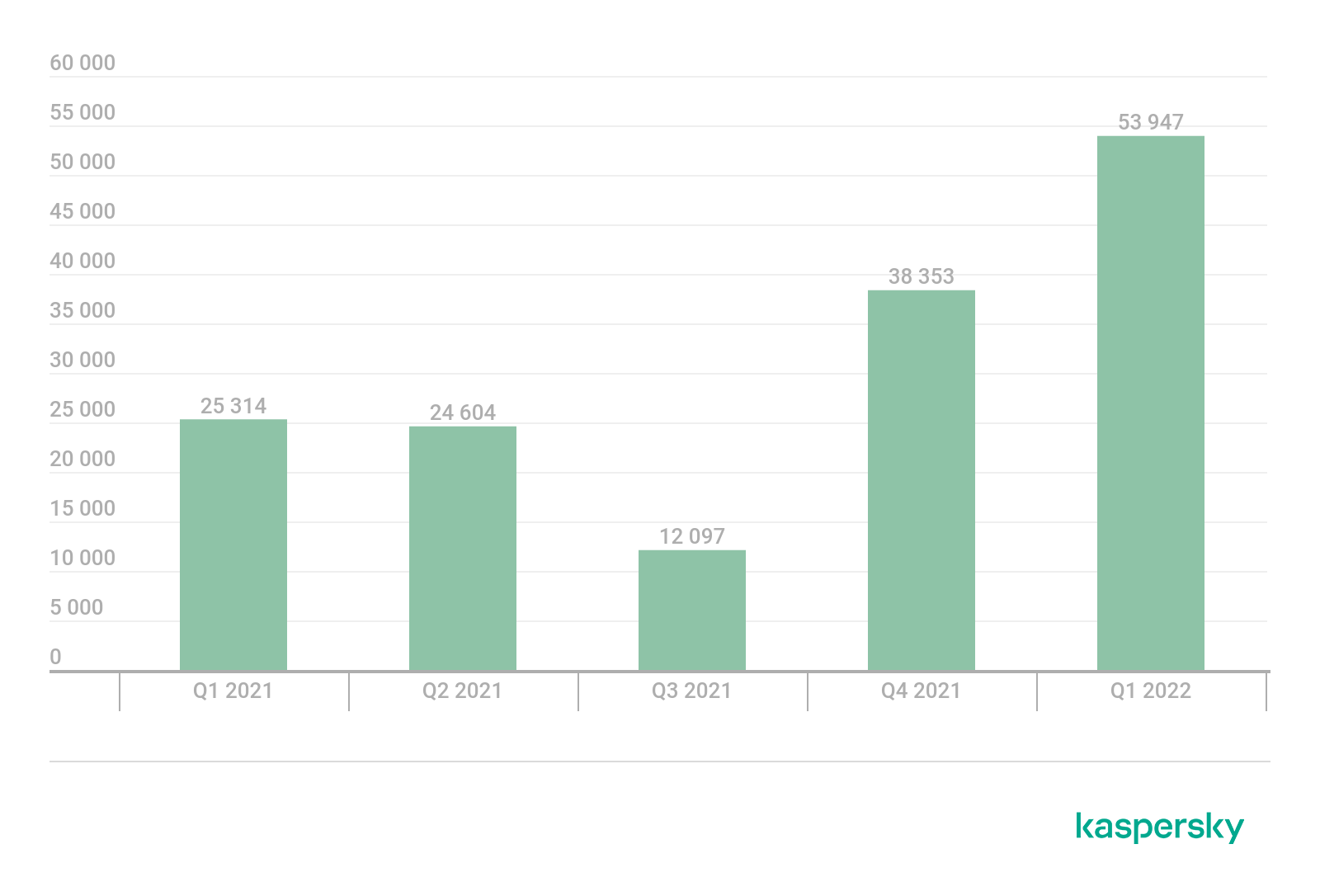
Number of installation packages for mobile banking trojans detected by Kaspersky, Q1 2021 — Q1 2022 (download)
| Verdict | %* | |
| 1 | Trojan-Banker.AndroidOS.Bian.h | 18.68 |
| 2 | Trojan-Banker.AndroidOS.Anubis.t | 12.52 |
| 3 | Trojan-Banker.AndroidOS.Svpeng.q | 8.63 |
| 4 | Trojan-Banker.AndroidOS.Agent.ep | 8.24 |
| 5 | Trojan-Banker.AndroidOS.Asacub.ce | 4.98 |
| 6 | Trojan-Banker.AndroidOS.Agent.eq | 4.56 |
| 7 | Trojan-Banker.AndroidOS.Sova.g | 2.75 |
| 8 | Trojan-Banker.AndroidOS.Gustuff.d | 2.62 |
| 9 | Trojan-Banker.AndroidOS.Agent.cf | 2.39 |
| 10 | Trojan-Banker.AndroidOS.Hqwar.t | 2.32 |
* Unique users attacked by this malware as a percentage of all Kaspersky mobile security solution users who encountered banking threats.
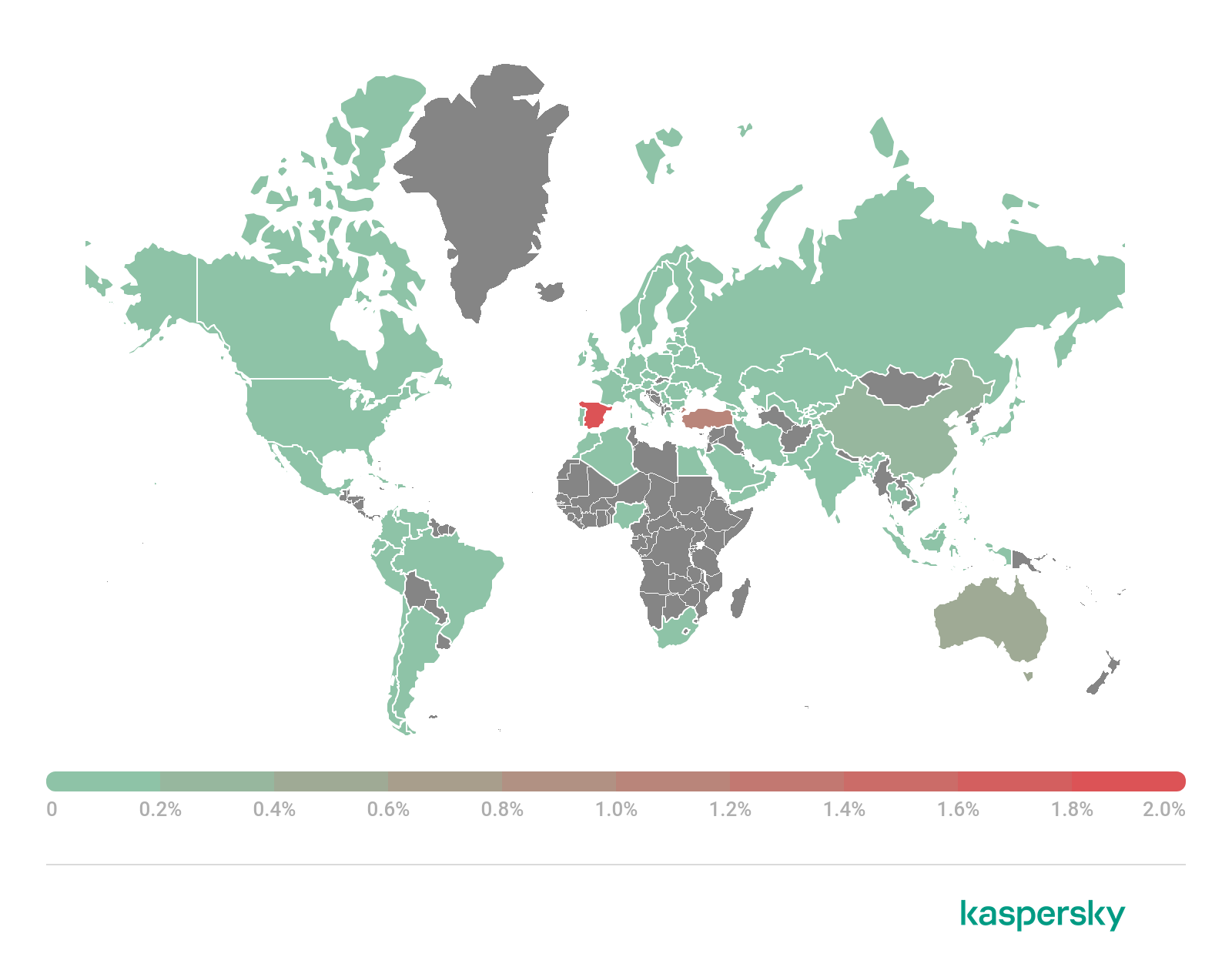
Geography of mobile banking threats, Q1 2022 (download)
| Countries* | %** | |
| 1 | Spain | 1.80 |
| 2 | Turkey | 1.07 |
| 3 | Australia | 0.54 |
| 4 | China | 0.35 |
| 5 | Italy | 0.17 |
| 6 | Japan | 0.15 |
| 7 | Colombia | 0.13 |
| 8 | Yemen | 0.09 |
| 9 | South Korea | 0.08 |
| 10 | Malaysia | 0.07 |
* Countries with relatively few users of Kaspersky mobile security solutions (under 10,000) have been excluded from the ranking.
** Unique users attacked by mobile banking trojans as a percentage of all Kaspersky mobile security solution users in the country.
Spain (1.80%) was where the most unique users were attacked by mobile financial threats in Q1 2022. The trojan behind almost three quarters of attacks (74,58%) in this country was the TOP 10 leader Trojan-Banker.AndroidOS.Bian.h. Turkey (1.07%) came second, where Trojan-Banker.AndroidOS.Bian.h (42.69%) was also encountered more frequently than any other threat. Australia (0.54%) took third place, where one trojan was more active than all the rest: Trojan-Banker.AndroidOS.Gustuff.d (95.14%).
Mobile ransomware trojans
In Q1 2022, we detected 1,942 installation packages for mobile ransomware trojans, which is 2,371 fewer than the figure recorded in the previous quarter and a year-on-year decrease of 1,654 against Q1 2021.
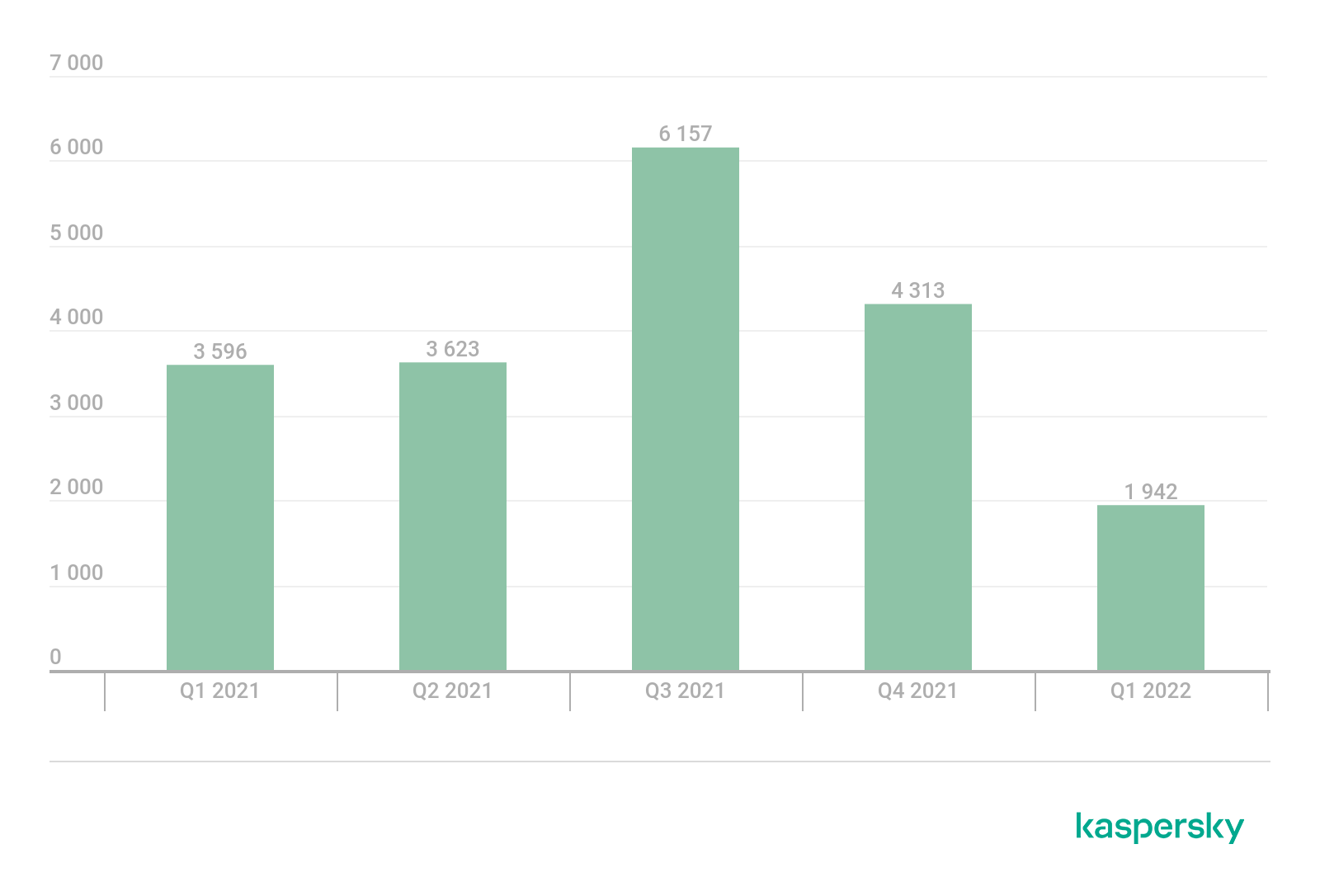
Number of installation packages for mobile ransomware trojans detected by Kaspersky, Q1 2021 and Q1 2022 (download)
| Verdict | %* | |
| 1 | Trojan-Ransom.AndroidOS.Pigetrl.a | 78.77 |
| 2 | Trojan-Ransom.AndroidOS.Rkor.br | 5.68 |
| 3 | Trojan-Ransom.AndroidOS.Rkor.bs | 1.99 |
| 4 | Trojan-Ransom.AndroidOS.Small.as | 1.89 |
| 5 | Trojan-Ransom.AndroidOS.Rkor.bi | 1.59 |
| 6 | Trojan-Ransom.AndroidOS.Rkor.bt | 1.58 |
| 7 | Trojan-Ransom.AndroidOS.Rkor.bp | 1.41 |
| 8 | Trojan-Ransom.AndroidOS.Rkor.bh | 0.93 |
| 9 | Trojan-Ransom.AndroidOS.Rkor.bn | 0.88 |
| 10 | Trojan-Ransom.AndroidOS.Rkor.bl | 0.76 |
* Unique users attacked by the malware as a percentage of all Kaspersky mobile security solution users attacked by ransomware trojans.
The top ransomware trojan held onto its title in the ranking for Q1 2022: Trojan-Ransom.AndroidOS.Pigetrl.a (78.77%). It’s worth noting that 94% of all attacks involving this trojan targeted Russia. The next runners-up trailing far behind the leader are two members of the Trojan-Ransom.AndroidOS.Rkor family: Rkor.br (5.68%) and Rkor.bs (1.99%).
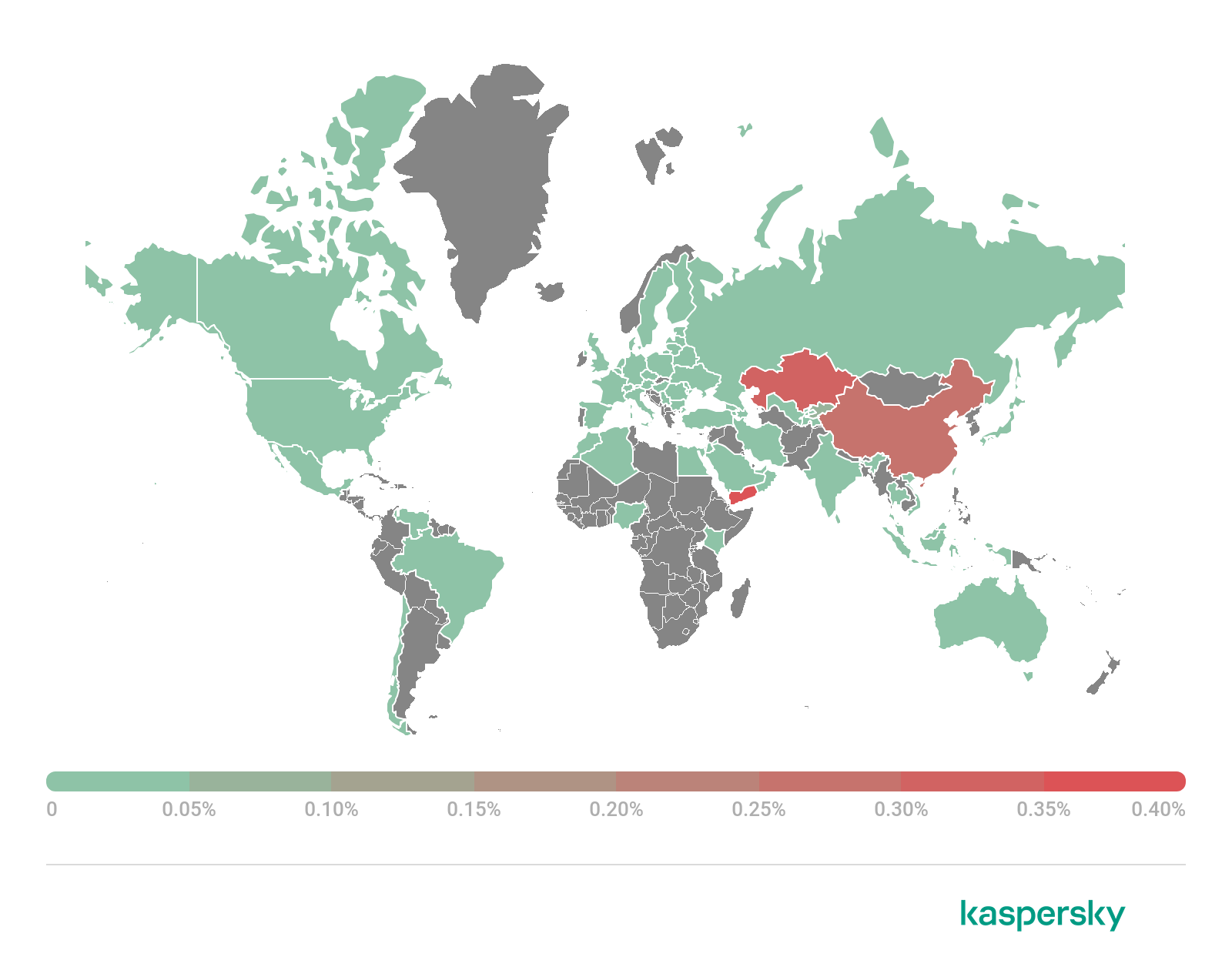
Geography of mobile ransomware trojans, Q1 2022 (download)
| Countries* | %** | |
| 1 | Yemen | 0.43 |
| 2 | Kazakhstan | 0.34 |
| 3 | China | 0.28 |
| 4 | Kyrgyzstan | 0.08 |
| 5 | Moldova | 0.03 |
| 6 | Saudi Arabia | 0.02 |
| 7 | Russian Federation | 0.02 |
| 8 | Egypt | 0.02 |
| 9 | Ukraine | 0.02 |
| 10 | Lithuania | 0.02 |
* Countries with relatively few users of Kaspersky mobile security solutions (under 10,000) have been excluded from the ranking.
** Unique users attacked by ransomware trojans as a percentage of all Kaspersky mobile security solution users in the country.
Yemen (0.43%) tops the list of countries where the greatest number of users were attacked by mobile ransomware trojans. It’s followed by Kazakhstan (0.34%) with China (0.28%) rounding out the top three. The trojan which users in Yemen encountered most frequently was Trojan-Ransom.AndroidOS.Pigetrl.a, while users in Kazakhstan and China encountered members of the Trojan-Ransom.AndroidOS.Rkor family.





















IT threat evolution in Q1 2022. Mobile statistics