
![]() Download ICS availability statistics (PDF version)
Download ICS availability statistics (PDF version)
![]() Download ICS vulnerabilities statistics (PDF version)
Download ICS vulnerabilities statistics (PDF version)
Overview
Industrial control systems (ICS) surround us: they are used in electric, water and wastewater, oil and natural gas, transportation, chemical, pharmaceutical, pulp and paper, food and beverage, and discrete manufacturing (e.g., automotive, aerospace, and durable goods). Smart cities, smart houses and cars, medical equipment – all of that is driven by ICS.
Expansion of the Internet makes ICS easier prey to attackers. The number of ICS components available over the Internet increases every year. Taking into account that initially many ICS solutions and protocols were designed for isolated environments, such availability often provides a malicious user with multiple capabilities to cause impact to the infrastructure behind the ICS due to lack of security controls. Moreover, some components are vulnerable themselves. The first available information about vulnerabilities in ICS components is related to 1997, only two vulnerabilities were published that year. Since then the number of vulnerabilities significantly increased. Over the past five years this index has increased from 19 vulnerabilities in 2010 to 189 vulnerabilities in 2015.
Sophisticated attacks on ICS systems are not somewhat new anymore. It is worth remembering an incident in 2015 in Ivano-Frankivsk, Ukraine where around a half of houses were left without electricity because of a cyber-attack against the Prykarpattyaoblenergo power company, and it was only one of multiple victims of the BlackEnergy APT campaign.
Another notable incident, happened in 2015 and described in Verizon Data Breach Digest, is an attack on Kemuri Water Company’s ICS infrastructure, when intruders infiltrated a water utility’s control system and changed the levels of chemicals being used to treat tap water. The intrusion was performed through a vulnerable externally available system, that managed programmable logic controllers (PLCs) regulating valves and ducts that controlled the flow of water and chemicals used to treat it through the system.
Also in 2015 there were other ICS-related incidents, such as attacks on a steel mill in Germany and on the Frederic Chopin Airport in Warsaw.
In this research we provide an overview of the current situation with ICS security worldwide from the point of view of vulnerabilities, and vulnerable ICS components exposed to the Internet.
Analysis Approach
The research is focused on two areas: Vulnerabilities and ICS Availability over the Internet. Vulnerabilities information gathering was carried out based on open sources, such as Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) advisories, NVD/CVE, SCADA Strangelove, Siemens Product CERT and other information available online. Severity levels for the vulnerabilities were assessed based on a Common Vulnerability Scoring System (CVSS) of the versions 2 and 3. CVSS v2 was used to compare vulnerability statistics in the years 2014 and 2015, and it was also used for any vulnerabilities that didn’t have CVSS v3 score assigned.
In the second part of research results (ICS Availability over the Internet) we used a passive approach for analysis based on information from the Shodan search engine. To identify ICS systems in Shodan search we used a fingerprint knowledgebase, containing about 2000 records and allowing to identify product vendors and versions by banners.
Main Findings
- The number of vulnerabilities in ICS components keeps growing. With increased attention to ICS security over the last several years, more and more information about vulnerabilities in these systems is becoming public. However, vulnerabilities themselves could be present in these products for years before they are revealed. In total, 189 vulnerabilities in ICS components were published in 2015, and most of them are critical (49%) or have medium severity (42%).
- Vulnerabilities are exploitable. For 26 of the vulnerabilities published in 2015, exploits are available. Besides, for many vulnerabilities (such as hard-coded credentials) an exploit code is not needed at all to obtain unauthorized access to the vulnerable system. Moreover, our ICS security assessment projects show that ICS are often considered by their owners as a “black box”, so default credentials in ICS componenets are often not changed and could be used to gain remote control over the system. The SCADAPASS project of the SCADA Strangelove team provides a representation of known default ICS credentials. Currently information on 134 ICS components of 50 vendors is available.
- ICS vulnerabilities are widely diversified. New vulnerabilities were found in 2015 in the ICS components of different vendors (55 different manufacturers) and types (HMI, electric devices, SCADA, industrial network devices, PLCs and multiple others). The largest amount of vulnerabilities were found in Siemens, Schneider Electric and Hospira devices. Vulnerabilities in ICS components have a different nature. The most widespread types are buffer overflows (9% of all detected vulnerabilities), use of hard-coded credentials (7%) and cross-site scripting (7%).
- Not all of the vulnerabilities found in 2015 are fixed. Patches and new firmware are available for 85% of the published vulnerabilities, the rest are not fixed or are only partially fixed for different reasons. Most of the unpatched vulnerabilities (14 out of 19) are of high level risk. These unpatched vulnerabilities pose significant risk to the owners of the corresponding systems, especially for those who, due to inappropriate network configuration management, have their vulnerable ICS systems exposed to the Internet. Examples include the 11,904 remotely available SMA Solar Sunny WebBox interfaces that are under risk of compromise though hard-coded passwords. Although for Sunny WebBox this number has significantly reduced since 2014 (when over 80 thousand available components were found), the amount is still high, and the unfixed hardcoded credentials issue (published in 2015) is now putting these systems under a much higher risk than was previously thought.
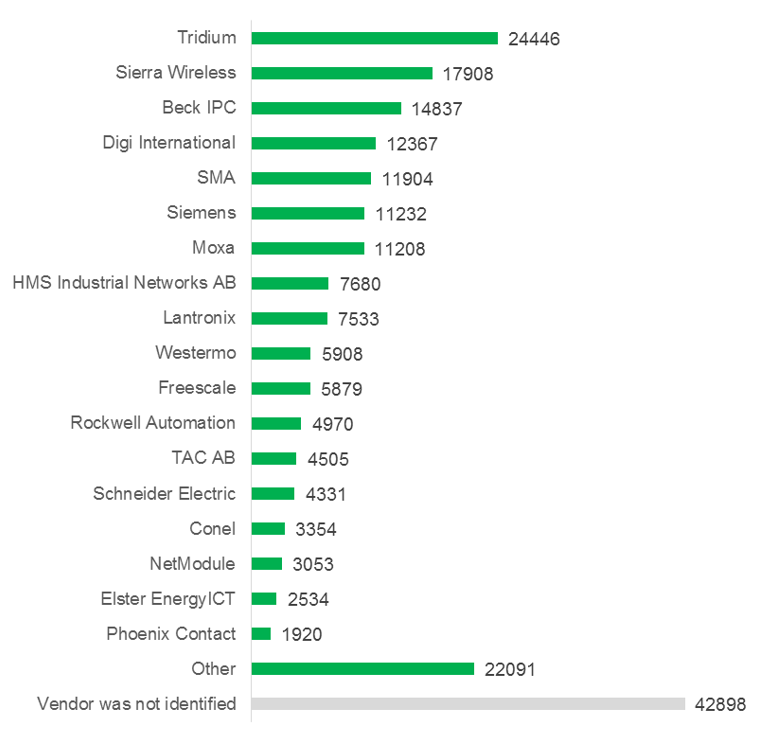
- Numerous ICS components are available via the Internet. 220,668 ICS components were discovered by the Shodan search engine. They are located on 188,019 hosts in 170 countries. Most of the remotely available hosts with ICS components are located in the United States (30.5%) and Europe. Among European countries Germany has a leading position (13.9%) followed by Spain (5.9%). The available systems are of 133 different vendors. The most widespread ones are Tridium (11.1%), Sierra Wireless (8.1%), and Beck IPC (6.7%).
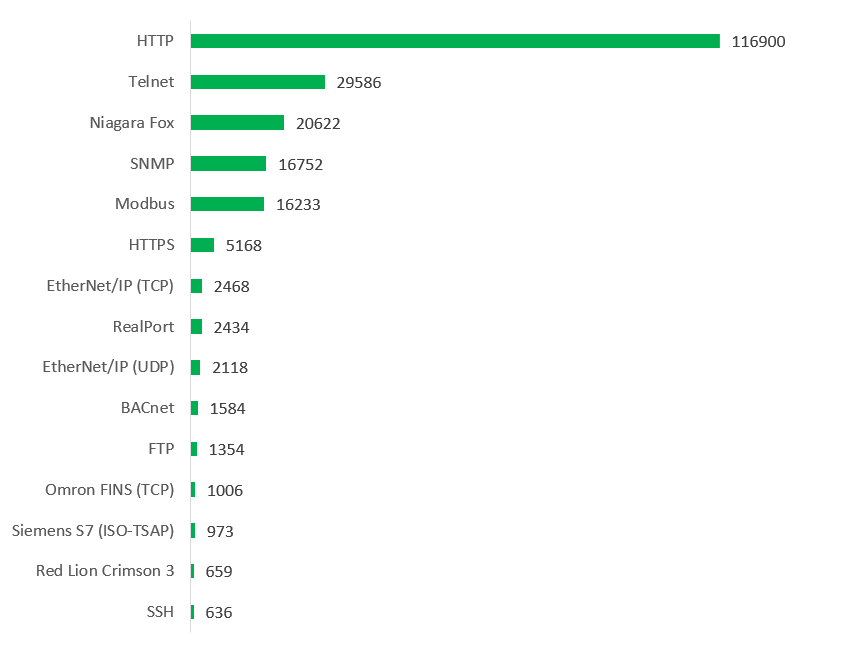
- Insecure protocols are widely used by remotely available ICS components. There is a number of protocols, which are open and insecure by design, such as HTTP, Niagara Fox, Telnet, EtherNet/IP, Modbus, BACnet, FTP, Omron FINS, Siemens S7 and many others. They are used on 172,338 different hosts, which corresponds to 91.6% of all the externally available ICS devices found. This provides an attacker with additional ways to compromise the devices by performing man-in-the-middle attacks.
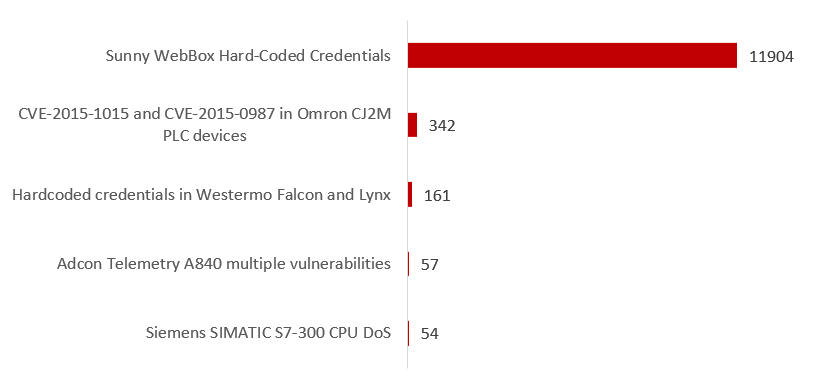
- Multiple vulnerable ICS components are externally available. We found 13,033 vulnerabilities on 11,882 hosts (6.3% of all hosts with externally available components). The most widespread revealed vulnerabilities are Sunny WebBox Hard-Coded Credentials (CVE-2015-3964), and critical vulnerabilities CVE-2015-1015 and CVE-2015-0987 in Omron CJ2M PLC. Combining these results with statistics of usage of insecure protocols, we were able to estimate the total number of vulnerable ICS hosts as 172,982 (92%).
- Multiple industries are affected. We found that at least 17,042 ICS components on 13,698 different hosts in 104 countries likely belong to large companies, and availability of these components from the Internet is likely related with significant risks. Among owners we were able to identify 1,433 large organizations, including ones belonging to the following industries: electricity, aerospace, transportation (including airports), oil and gas, metallurgy, chemical, agriculture, automotive, utilities, drinks and food manufacturing, construction, liquid storage tanks, smart cities, and ICS vendors. There are also research and education entities, government institutions (including police), medical centers, financial organizations, resorts, hotels, museums, libraries, churches and multiple small businesses among identified owners of remotely available ICS. The number of vulnerable externally available ICS hosts, which likely belong to large organizations, is 12,483 (91.1%), where 453 hosts (3.3%), including hosts belonging to energy, transportation, gas, engineering and manufacturing organizations, drink and foods manufacturing, energy and transportation organizations, contain critical vulnerabilities.
ICS vulnerabilities by year
ICS vulnerabilities in 2015 by risk level (CVSS v.2 and CVSS v.3)
ICS patching
TOP 20 countries by ICS availability
TOP 15 protocols used by externally available ICS components
TOP 5 vulnerabilities on ICS components
ICS availability by vendor
The above results are only lower bound estimations, and real number of available ICS components associated with significant risks could be much higher.
Conclusion
Where protection is concerned, the isolation of critical environments can no longer be regarded as a sufficient security control for ICS. The business requirements of the 21st century often make it necessity to integrate ICS with external systems and networks. In addition, the capabilities, motivations and number of threat actors focusing on ICS environments are increasing. From infected hard drives or USB sticks, to unauthorized connections from ICS networks to the Internet through personnel smart phones or modems, and from infected distributive kits obtained from vendors, to a hired insider – all of these methods are available to highly-skilled intruders planning an attack on a physically and logically isolated ICS network.
Nowadays, ICS owners should be aware of modern vulnerabilities and threats, and actively improve the security of their ICS environments based on this knowledge. Here, active vendor support is crucial for the prompt identification and remediation of vulnerabilities in ICS products, as well as for sharing workarounds to protect systems before patches are released.
The specifics of ICS – that its cybersecurity is closely tied with physical safety – often receives an attitude opposite to the demandable treatment in such conditions. Small and medium businesses, as well as individuals, completely rely on vendors when it comes to security of the Internet of Things. The consumers don’t go beyond simple basic steps from device manuals, thus obtaining ready-to-work and easily accessible, but also vulnerable devices. On the contrary, in the enterprise area, companies understand the high risks, which are related with incorrect configuration of ICS environment. However, because of that system owners often consider ICS devices as “black-boxes”, and have a dread to make changes in the environment, including cybersecurity enhancement.
The findings of this research are an additional reminding that the “Security through Obscurity” principle cannot serve as a good basis to achieve effective protection from modern attacks, and that industrial control systems security should not be treated superficially in favor of safety, especially because the security and safety in this area are inextricably connected.
Industrial cybersecurity threat landscape



















Tyler Bent
Love the work. Would like to invite you to present these findings to the IT-ISAC. Please check out our website http://www.it-isac.org and send me an email if interested.
Thank you!