
Infected websites appear on the Internet literally every day. They include personal blogs on WordPress that become infected during mass, automated attacks, and the websites of major media outlets, each of which malicious users infect manually after some preparatory steps. All of these resources replenish the arsenal of so-called “traffic traders” – cybercriminals who redirect visitors to infected websites to the online resources of their malware-writing clients. In the end a user, suspecting nothing, can become the victim of a drive-by attack and, if the user’s browser or the browser’s plug-ins have the necessary vulnerabilities, malware will be downloaded to and installed on the victim’s computer.
Kaspersky Lab has a system that automatically detects and visits infected websites in order to collect a malicious sample and send it to our virus lab for research. To ensure this system is as effective as possible when it comes to detecting online threats, infected websites are studied by virus analysts. With the precision and attentiveness of a forensics examiner, they are able to determine how attacks are launched when a user visits a website.
One time, that forensics examiner was me. I was assigned a website that was causing victim computers to download malicious software, and I used the free HTTP debugging service Fiddler and set about examining its contents. First of all, I took a look at the website’s pages, looking for any of the standard signs of web infection, such as <script> and <iframe> tags that would redirect visitors to malicious web resources. I didn’t find anything in the tags, and that came as no surprise, since website hackers rarely leave links to malware out in the open. I carefully examined all of the JavaScript files on the website – but I didn’t find anything there, either. There were several Flash clips on the website, which I knew could also be used to download malware. I broke them down and looked at each one. Unfortunately, there was no trace of malicious code there, either. So what exactly was going on here? I checked and re-checked these elements, but could find nothing.
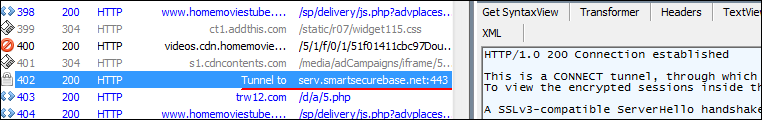
My attention then turned to an unassuming string in Fiddler, which indicated that part of the site’s content is downloaded through an encrypted channel via HTTPS.
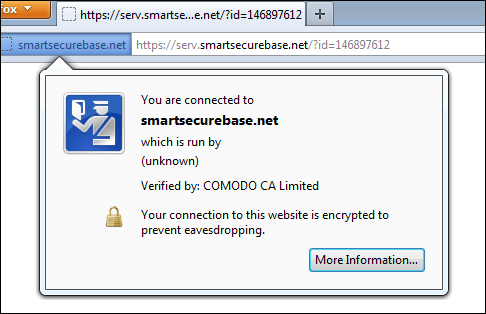
It was hard to believe that malicious users went through the costly procedure of obtaining an SSL certificate for the website in order to spread malicious programs, since these websites are put onto denylists by antivirus companies and lose their value very quickly. But as Sherlock Holmes says, “Eliminate all other factors, and the one which remains must be the truth.”
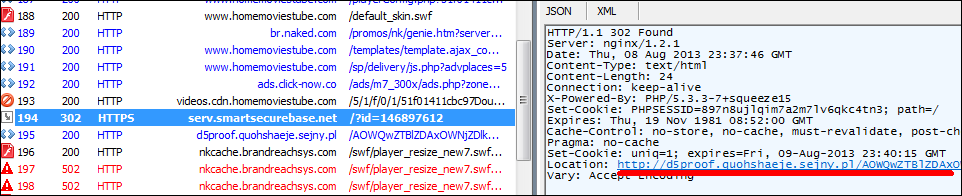
I wasn’t feeling overly confident when I switched on Fiddler’s option to decipher HTTPS traffic. But as it turned out, what had originally seemed like an altogether ordinary string was in fact concealing a redirect to a malicious website.
The site that served as the source of malicious software, just like the website that served as the redirect intermediary with the SSL certificate, were both added to our database of malicious resources right then and there. All of the malware that they had been spreading had already previously been detected and identified by Kaspersky Lab.
But my curiosity was piqued: are malicious users really purchasing SSL certificates for the secure transmission of malicious code, or had they somehow figured out a way to get past browser verification using fake SSL certificates? Surprising as it was, the certificate was the real deal.
Quite often, we see malicious users preying on the trust of their victims – they hack accounts on social networks in order to send links to that person’s friends under the guise of yet another cute cat video (but with an .exe extension, and not everyone will fall for that), and they recreate the logos of law enforcement agencies seeded with a blackmailer Trojan, and persuade users to enter their cell phone numbers “to fight botnets”. But what’s more, malicious users also expend no small effort to fool antivirus companies and independent researchers. What may seem like a harmless grey string in an HTTPS connection is just one example of these types of tactics, vying for experts’ trust in these technologies that were designed with the intention of protecting users against online sabotage.

















HTTPS Working for Malicious Users