
For malware writers, Google Play is the promised land of sorts. Once there, a malicious application gains access to a wide audience, gains the trust of that audience and experiences a degree of leniency from the security systems built into operating systems. On mobile devices, users typically cannot install applications coming from sources other than the official store, meaning this is a serious barrier for an app with malicious intent. However, it is far from easy for the app to get into Google Play: one of the main conditions for it is to pass a rigorous check for unwanted behavior by different analysis systems, both automatic and manual.
Some malware writers have given up on their efforts to push their malicious creations past security checks, and instead learned how to use the store’s client app for their unscrupulous gains. Lately, we have seen many Trojans use the Google Play app during promotion campaigns to download, install and launch apps on smartphones without the owners’ knowledge, as well as leave comments and rate apps. The apps installed by the Trojan do not typically cause direct damage to the user, but the victim may have to pay for the created excessive traffic. In addition, the Trojans may download and install paid apps as if they were free ones, further adding to the users’ bills.
Let us look into the methods how such manipulations with Google Play happen.
Level 1. N00b
The first method is to make the official Google Play app store undertake the actions the cybercriminal wants. The idea is to use the Trojan to launch the client, open the page of the required app in it, then search for and use special code to interact with the interface elements (buttons) to cause download, installation and launch of the application. The misused interface elements are outlined with red boxes in the screenshots below:

|

|

|
The exact methods of interaction with the interface vary. In general, the following techniques may be identified:
- Use of the Accessibility services of the operating system (used by modules in Trojan.AndroidOS.Ztorg).
- Imitation of user input (used by Trojan-Clicker.AndroidOS.Gopl.c).
- Code injection into the process of Google Play client to modify its operation (used by Trojan.AndroidOS.Iop).
To see how such Trojans operate. Let us look at the example of Trojan.AndroidOS.Ztorg.n. This malicious program uses Accessibility services originally intended to create applications to help people with disabilities, such as GUI voice control apps. The Trojan receives a job from the command and control server (C&C) which contains a link to the required application, opens it in Google Play, and then launches the following code:
This code is needed to detect when the required interface element appears on the screen, and to emulate the click on it. This way, the following buttons are clicked in a sequence: “BUY” (the price is shown in the button), “ACCEPT” and “CONTINUE”. This is sufficient to purchase the app, if the user has a credit card with sufficient balance connected to his/her Google account.
Level 2. Pro
Some malware writers take roads less traveled. Instead of using the easy and reliable way described above, they create their own client for the app store using HTTPS API.
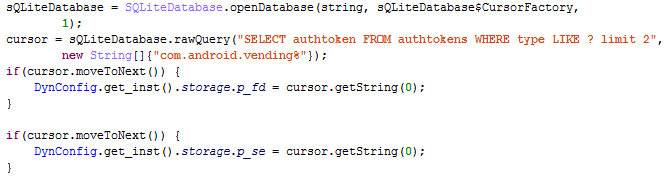
The difficult part about this approach is that the operation of the self-made client requires information (e.g. user credentials and authentication tokens) which is not available to a regular app. However, the cybercriminals are very fortunate that all required data are stored on the device in clear text, in the convenient SQLite format. Access to the data is limited by the Android security model, however apps may abuse it e.g. by rooting the device and thus gaining unlimited access.
For example, some versions of the Trojan.AndroidOS.Guerrilla.a have their own client for Google Play, which is distributed with the help of the rooter Leech. This client successfully fulfils the task of downloading and installing free and paid apps, and is capable of rating apps and leaving comments in the Google store.
After launch, Guerrilla starts to collect the following required information:
-
The credentials to the user’s Google Play account.
Activities in Google Play require special tokens that are generated when the user logs in. When the user is already logged in to Google Play, the Trojan can use the locally cached tokens. They can be located through a simple search through the database located at /data/system/users/0/accounts.db:
With the help of the code below, the Trojan checks if there are ready tokens on the infected device, i.e. if the user has logged on and can do activities in Google Play:
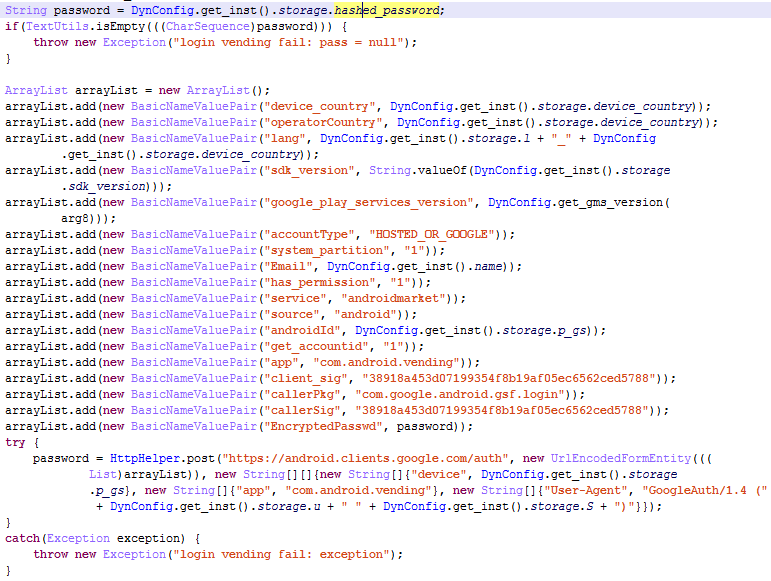
If no such tokens are available, the Trojan obtains the user’s username and hashed password, and authenticates via OAuth:
- Android_id is the device’s unique ID.
-
Google Service Framework ID is the device’s identifier across Google services.
First, the Trojans attempts to obtain this ID using regular methods. If these fail for whatever reason, it executes the following code:
-
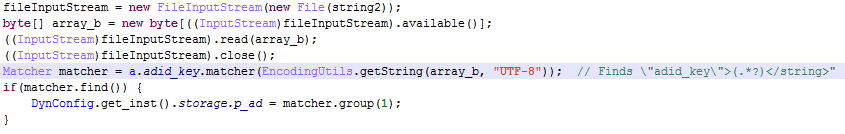
Google Advertising ID is the unique advertising ID provided by Google Play services.
Guerrilla obtains it as follows:
-
In a similar way, the Trojan obtains hashed data about the device from the file “/data/data/com.google.android.gms/shared_prefs/Checkin.xml“.
When the Trojan has collected the above data, it begins to receive tasks to download and install apps. Below is the structure of one such task:
The Trojan downloads the application by sending POST requests using the links below:
- https://android.clients.google.com/fdfe/search: a search is undertaken for the request sent by the cybercriminals. This request is needed to simulate the user’s interaction with the Google Play client. (The main scenario of installing apps from the official client presupposes that the user first does the search request and only then visits the app’s page).
- https://android.clients.google.com/fdfe/details: with this request, additional information needed to download the app is collected.
- https://android.clients.google.com/fdfe/purchase: the token and purchase details are downloaded, used in the next request.
- https://android.clients.google.com/fdfe/delivery: the Trojan receives the URL and the cookie-files required to download the Android application package (APK) file.
- https://android.clients.google.com/fdfe/log: the download is confirmed (so the download counter is incremented.)
- https://android.clients.google.com/fdfe/addReview: the app is rated and a comment is added.
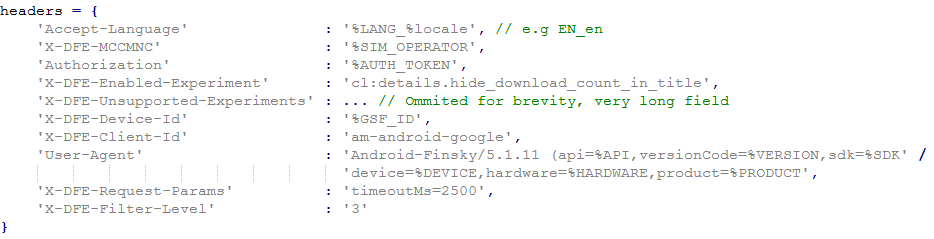
When creating the requests, the cybercriminals attempted to simulate most accurately the equivalent requests sent by the official client. For example, the below set of HTTP headers is used in each request:
After the request is executed, the app may (optionally) get downloaded, installed (using the command ‘pm install -r’ which allows for installation of applications without the user’s consent) and launched.
Conclusion
The Trojans that use the Google Play app to download, install and launch apps from the store to a smartphone without the device owner’s consent are typically distributed by rooters – malicious programs which have already gained the highest possible privileges on the device. It is this particular fact that allows them to launch such attacks on the Google Play client app.
This type of malicious program pose a serious threat: in Q2 2016, different rooters occupied more than a half of the Top 20 of mobile malware. All the more so, rooters can download not only malicious programs that compromise the Android ecosystem and spend the user’s money on purchasing unnecessary paid apps, but other malware as well.
How Trojans manipulate Google Play



























Antonella Mastroianni
Thanks for all the explanation. But.. how can I remove the Trojans from my android??