
We’re raising our threat level by a notch. Not something that we do as often as we used to. There are several reasons for this decision, but one of them really stands out.
We’ve identified a worm called VBMania. This might not sound like anything much, but in contrast to most worms today, it spreads via email. Real old school. Additionally, it works on the the principle of “download and run”.
The worm spreads by sending emails from the infected computer. The messages have a subject line of “Here you have” and random text such as “This is The Free Dowload Sex Movies,you can find it Here”. Of course, the messages also include a link to a file on the Internet.
Click on the link, save and run the file and voila – your machine is infected.
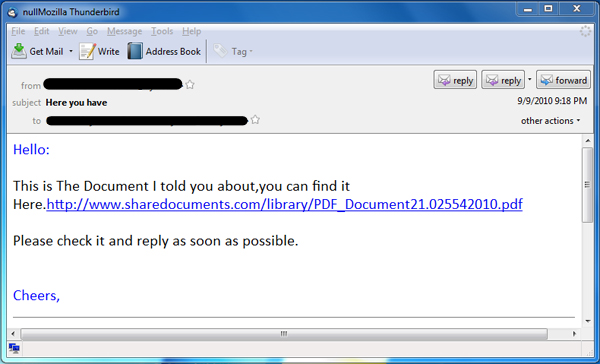
In spite of this primitive propagation routine, the worm is pretty active, and currently sending out significant amounts of mail.
Because of this, and also because there’s been a lot of news about this worm flying around, we’ve decided to raise the threat level with the aim of informing as many people as possible.
The worm’s written in Visual Basic, and our products detect it proactively using heuristics as Suspicious:HEUR:Trojan.Win32.Generic.
Last night we also added signature detection (Trojan-Win32.Swisyn) which we’re going to rename to Email-Worm.Win32.VBMania.
UPDATE:As of 1600 GMT, all the malicious worm files which were located on members.multimania.co.uk had been deleted. This means the worm won’t be able to propagate further. However, infected computers will continue to send emails until they’re disinfected.
While analysing the worm we also identified an earlier variant – Trojan.Win32.Swisyn.ajgd. It was first detected in August this year, had similar functionality, and was also spread from the member areas on members.multimania.co.uk and lycos.co.uk.


















“Here you have” – not a sex tape, but a worm