
We’ve detected a new variant of Gpcode – a dangerous file-encryptor. It encrypts a whole variety of user files, targeting files with extensions such as DOC, TXT, PDF, XLS, JPG, PNG, CPP, H etc. If you’re a regular visitor to Viruslist, you might remember reading about Gpcode a couple of years ago.
We recently started getting reports from infected victims, analysed a sample, and added detection for Gpcode.ak to our antivirus databases yesterday, on June 4th. However, although we detect the virus itself, we can’t currently decrypt files encrypted by Gpcode.ak – the RSA encryption implemented in the malware uses a very strong, 1024 bit key.
The RSA encryption algorithm uses two keys: a public key and a private key. Messages can be encrypted using the public key, but can only be decrypted using the private key. And this is how Gpcode works: it encrypts files on victim machines using the public key which is coded into its body. Once encrypted, files can only be decrypted by someone who has the private key – in this case, the author or the owner of the malicious program. As I’ve said above, we’ve come across Gpcode before (see Blackmailer for the full story). Two years ago we were able to get the private key by detailed analysis of the data at our disposal. However, the maximum RSA key length we’ve been able to ‘crack’ to date is 660 bits. We were able to do this as the author had made some mistakes when implementing the encryption algorithm.
The author has bided his time, waiting almost two years before creating a new, improved variant of this file encryptor. Gpcode.ak doesn’t not repeat the errors found in previous versions of the virus. Back in 2006 when we detected the first versions of Gpcode to use RSA, this sounded an alarm: we warned that we wouldn’t be able to help decrypt encrypted files if the virus writer implemented the RSA encryption algorithm correctly. It would be a case for law enforcement; encrypting files in this way is tantamount to a cybercriminal copying user files to his own machine, and deleting them from the user’s infected machine without consent – an illegal action.
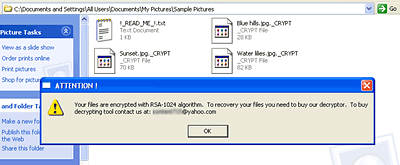
Once the virus has encrypted a user’s files, it leaves the following text message along with the files it has encrypted:
To recovery your files you need to buy our decryptor.
To buy decrypting tool contact us at: ********@yahoo.com»
Unfortunately, at the time of writing it’s still not clear how the virus spreads. To protect your machine, you should enable all components of whatever anti-malware protection that you have installed.
ATTENTION! If you see the following message on your computer:
…Then, in all probability, you have been attacked by Gpcode.ak. In this case, try to contact us using another computer connected to the Internet. DO NOT RESTART or POWER DOWN the potentially infected machine.
Contact us by email stopgpcode@kaspersky.com and tell us the exact date and time of infection, as well everything you did on the computer in the 5 minutes before the machine was infected:
• which programs you have executed,
• which websites you have visited, etc.
We’ll try and help you recover any data that has been encrypted.
Our analysts are continuing to analyze the virus code in search of a way of decrypting files without having the private key. In the meantime, do take extra care as you surf and read email. And if you see the above messages…do follow our instructions.
We’ll be posting updates here when we have more news.




















Gpcode: the return of the file encryptor