
A few days ago the Inquirer published a interesting little article talking about how Google hadn’t returned the search results he wanted, but instead told him his computer might be infected with a malicious program. And today one of our clients got caught the same way – the ubiquitous search engine was displaying the same error message to lots of the company’s staff.
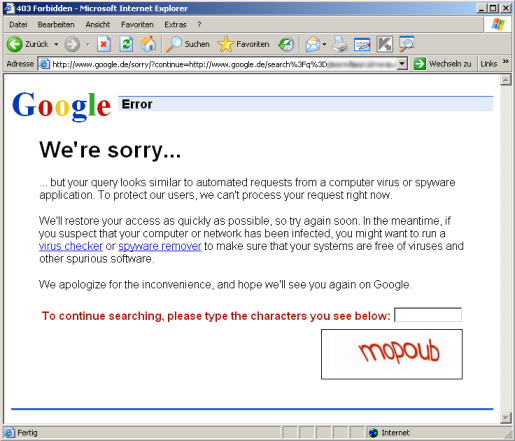
I’m interested in why this happened. It’s not very difficult to find a possible answer: a lot of spammers use Google to find the emails of potential victims and automate this task by using little scripts which may be run from infected machines. So Google can implement a temporary block which is lifted when the user correctly responds to Google’s captcha by entering the letters and numbers shown, proving that s/he is not a spambot.
We’ve managed to reproduce the suspicious behaviour that can get a human user getting locked out of Google. And once the user’s been locked out, his/ her IP address get’s denylisted. This can be a problem if the user is coming in via a proxy server – it will be the proxy that will be seen as the attacker, and the proxy that gets blocked. Which means that all the users coming in via the same proxy will also be subject to the same restrictions, until someone correctly solves the captcha. It would of course be helpful if the Google warning clearly stated that it could be the proxy, rather than the user’s computer, which is suspected of being a bot. We’ve suggested this to Google, and we’ll let you know their response.
Of course, it might not be a false alarm at all – there might be an infected computer on your network, and Google raising the red flag could be the first sign of infection. But even though Google’s search capability may be awesome, a dedicated antivirus program is still going to be the most reliable way of catching malicious programs.






















GoogleBlock