
Quite recently, we (and hence our security solutions) started to designate an entire class of sites — gift card generators — as fraudulent, despite their not stealing any money or personal data from visitors. Why? Let’s try to unpick these sites and see how they work.
How it works
Ads for all kinds of generators can be seen in spam emails and the banners of dubious advertiser networks. The quality of such sites can range from professional to shoddy, but the essence is always the same: the visitor is offered a freely generated gift card code for iTunes, Google Play, Amazon, Steam, and the like. A single site can offer cards of any value for almost every service out there.
As usual with phishing sites, there is no word about why the creators are so charitable, yet plenty of reviews from grateful customers who report that the “generated” code did the trick (if not the first, then the tenth or the hundredth).
It should be noted that the code generation algorithms of major firms like Apple or Google are well shielded against attack. And according to cybersecurity experts, the only high-profile case of this kind — when the iTunes code generation algorithm was allegedly compromised by Chinese hackers back in 2009 — actually was more akin to a money laundering scheme. Gift cards supplied by smaller stores are less well protected, but also of little interest to scammers.
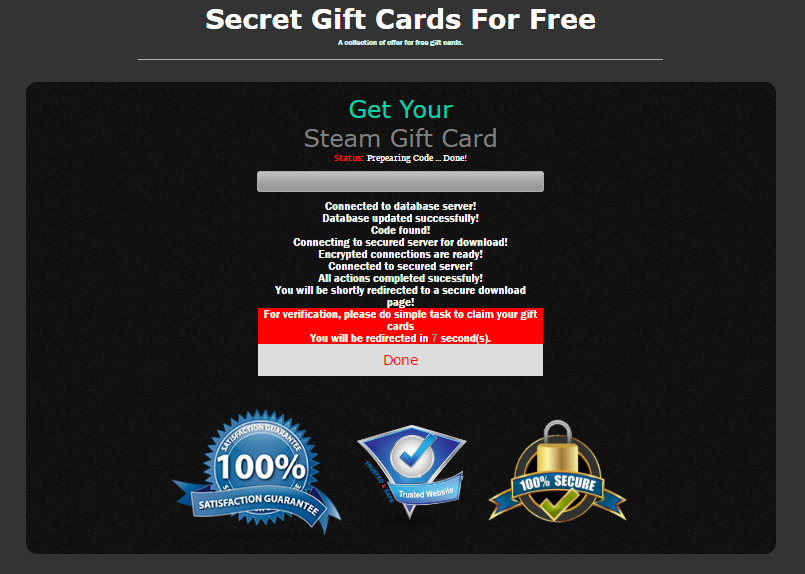
To get a code, the user first selects a gift card on the site, whereupon the system begins the “code generation” (or “hacking”) process. To make everything more believable, as in hacker movies, there are plenty of on-screen messages about server connections and other seemingly important operations.
The user does not get to see the generated code in its entirety until confirmation is given that they are human, not a robot. This requires clicking a link and completing a task.
Depending on their country of residence, the user might be asked to take a survey, play a lottery, provide details (phone number, postal address), subscribe to a paid SMS service, install adware (which redirects all user searches, harvests information about online activity, and resists deletion), or do something else. The nature of the task is determined by the partner network owning the site that the user is redirected to. The network, in turn, is selected based on the country of residence: each domain zone has partner networks catering to the laws and languages of various countries.

Download a paid ringtone, play a lottery, share personal data — basically, do something risky to prove you’re not a robot
The upshot is unpleasant, but predictable: the victim is either led around various partner sites until they tire of filling out forms and playing lotteries, or they are rewarded with a random set of symbols that has nothing to do with a real code and only mimics the format.
Note that owners of code generator sites try to avoid outright fraud or phishing. They are more than happy with the funds they get from “selling user actions” on partner sites: revenue can range from a few cents for a click on a link to tens of dollars for a filled-out form or a subscription to a paid service. Scrupulous advertisers (they do exist!) of the partner network assume that they are getting data from users genuinely interested in their particular product or service. But the unscrupulous ones don’t really care, as far as they can use this data for spam or similar purposes. This deception of users (and sometimes advertisers too) is the reason why we started to classify generator sites as fraudulent. But the topic of honest and dishonest partners is a discussion for another day.
Exceptions
There are legitimate sites and services that give users discounts and gift cards as part of a loyalty program (for example, in exchange for points earned or purchases made in partner stores). TokenFire and Swagbucks are examples of legitimate apps. Their gift card codes are purchased from the vendor openly and honestly, and issued to clients who have done enough to cover the company’s expenses and deliver a profit. In other words, to receive a gift, the user has to spend a sizable amount of money and/or time. By contrast, generator sites look far more appealing, since they require very little. But as our research shows, that is because they give even less in return — nothing in fact, besides dashed expectations.
Online generators… of dashed expectations



















Liam Donn
No valid cards