
During routine malware analysis we sometimes find new techniques which are being used by Brazilian cybercriminals to remove security protection. Now it’s Brazilian banking Trojans are using Gmer, a well known standalone anti-rootkit tool to remove GBPlugin, a very popular security mechanism used by the four largest Brazilian banks. There are around 15 million Brazilian computers running GBPlugin which is designed to prevent the theft of personal banking data.
It’s common behavior for malware developers to use legitimate software to remove antivirus and other security solutions. We saw it with PSEXEC of Sysinternals. In Brazil this is the second time we know of that local malware has used a legitimate tool; the first was when Avenger, another anti-rootkit tool, was used to remove the same GBPlugin files.
The malware which we’ve just looked at downloads an old version of Gmer (1.014) from a legitimate, but compromised, Chinese server. Its saves it as System%logsvc.exe and once it’s installed, the malware registers a special service to remove GBPlugin using rootkit technology.
A bat file is created on the system and inside the file you can see the commands designed to kill all running files of GBPlugin, using the
–killfile parameter.
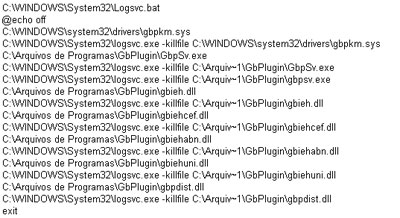
Another driver with commands to delete the GBPlugin files is installed to ensure that all the files will be removed:
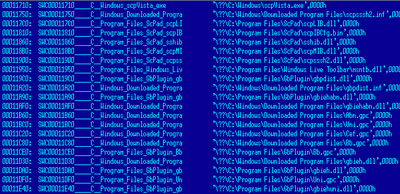
This Trojan is already detected by our products as Trojan-Downloader.Win32.Homa.yw, and the driver is detected as Rootkit.Win32.Agent.neg.






















Friendly fire