
Yesterday I came across something interesting. An email caught by some of our mailtraps, written in poor Dutch, about a site which can get you free sex.
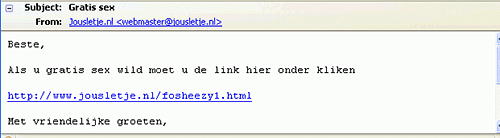
Obviously I was interested in the matter as this didn’t look like a typical spam email. These days most Dutch spam emails are about casinos. The site mentioned in the email contained a version of the popular MS XML exploit, MS06-71. We already detected this particular variant as
Trojan-Downloader.JS.Psyme.il.
The purpose of the exploit is to download and execute a backdoor, which we are now detecting as Backdoor.Win32.VB.bcv. After discovery we notified GOVCERT, the Dutch CERT, and they acted quickly to have the site taken down.
Next to this incident we’re also picking up increased activity of the gang behind the later variants of Backdoor.Win32.MSNMaker, which is mostly spreading in The Netherlands as well.
Malicious emails/messages tailored to the Dutch market have been rare, but they are on the up. People can no longer assume that emails/messages in Dutch are automatically benign and will have to start being more careful.
Free sex – Dutch email seeded

















Andreas
Thank you