
Introduction and methodology
Financial cyberthreats are malicious programs that attack users of online banking services, electronic money, cryptocurrency and other similar services, as well as threats aimed at gaining access to financial organizations and their infrastructure. Kaspersky experts regularly analyze the statistics that the company’s products anonymously send to the cloud infrastructure of the Kaspersky Security Network (KSN) in case users agree to transfer such data. In order to study the threat landscape of the financial sector, the researchers analyzed cases of malicious activity on the devices of private users of Kaspersky’s security solutions. Statistics on corporate users were collected from corporate security solutions, after the customers agreed to share their data with Kaspersky. The information obtainedwas compared with data fromthe same period in 2018, to track the trends in the development of malware. users We looked at quarterly results in order to compare statisitics for PC users, as we were able to divide the data into two catergories – corporate and private users. Traditionally, the second and the third quarter might differ from the first and the fourth as these people often go on vaction and there less of corporate financial activity in these periods. The most active malware families were then analyzed.
Main findings:
- In the first half of 2019, more than 430,000 unique users were attacked by financial threats – seven percent more than during the same period in 2018
- The number of financial attacks in the first half of 2019 was 10,493,792 – 93% more than in the first and second quarter of 2018
- The number of malware samples from financial threats received by Kaspersky in the first half of 2019 was 5,242,462 – 74% more than the previous year
- The countries with the largest share of users attacked by financial malware were China and Belarus (2.3% each). In second and third place were Venezuela (2.2%) and South Korea (2.1%), respectively
- During the first half of 2019, Kaspersky blocked more than 339,000 attempts to switch users to phishing pages pretending to be big banks
- 438,709 unique users encountered mobile financial threats in the first half of 2019 – 23% less than in the same period in 2018
- The number of mobile financial attacks in the first half of 2019 was 3,730,378 – 107% more than in the first half of 2018
Threats to PC: banking malware and phishing
In the first half of 2019, Kaspersky experts detected 431,088 unique users[1] attacked by banking Trojans aimed at stealing funds and financial data, which was a seven percent increase compared to the same period in 2018 (400,830).
At the same time, the share of users attacked through corporate devices in the first half of 2019 reached 30.9%, while in the first half of 2018, this figure was half as much (15.3%).
Researchers also noticed an increased number of malicious files in 2019. Thus, in the first quarter, the number of samples in the Kaspersky collection more than doubled, compared to the same period in 2018, reaching 335,000. But in the second quarter, growth slowed down.
Attacks have also become more frequent: the number of attempts to infect a device detected by Kaspersky’s protective solutions in both the first and second quarter of 2019 exceeded the corresponding figures of 2018 by 51% and 27%, respectively.
For a more complete analysis of the threat landscape, experts compiled a list of the most active banking Trojans in the first and second quarters of 2019, positioning them by the number of unique users that these threats attacked. 39.50% of corporate users were attacked by the RTM Trojan, one of the most common malware samples of the past year. In second place was Emotet (14.90%), capable of loading malware onto an infected device. For example, the Trickster Trojan, which can be installed on the victim’s computer, which is in third place in our ranking (12.30%).
| Corporate users | Private users | ||
| Trojan-Banker.Win32.RTM | 39.50% | Trojan-Banker.Win32.Zbot | 25.50% |
| Trojan-Banker.Win32.Emotet | 14.90% | Trojan-Banker.Win32.RTM | 24.50% |
| Trojan-Banker.Win32.Trickster | 12.30% | Trojan-Banker.Win32.Emotet | 6.40% |
Top 3 types of financial malware found in the first half of 2019
This is different for private users: the above-mentioned RTM and Emotet occupy second and third places with 24.5% and 6.4%, respectively, and in the first place is Zbot – one of the most common Trojans of 2018. Such malware is usually spread with the help of email campaigns or through phishing sites. In the first half of 2019, Kaspersky prevented more than 339,000 attempts to switch users to phishing pages that were designed as legitimate pages of large banks.
Geography
The top 10 countries with the largest share of users attacked by financial malware do not have geopolitical similarities and are not situated in a specific region. In the first place were China and Belarus (2.3%), followed by Venezuela (2.2%) and South Korea (2.1%).
| Country* | %** |
| China | 2.30 |
| Belorussia | 2.30 |
| Venezuela | 2.20 |
| South Korea | 2.10 |
| Serbia | 1.80 |
| Greece | 1.70 |
| Cameroon | 1.60 |
| Indonesia | 1.50 |
| Pakistan | 1.50 |
| Russia | 1.40 |
* Countries where the number of users of Kaspersky’s security solutions is relatively small (less than 10,000) are excluded from the ranking.
** The share of unique users attacked in relation to all users of Kaspersky ‘s security solutions in the country.
Top 10 countries by the proportion of unique users attacked by financial malware
Threats to mobile platforms
In the first half of 2019, attackers actively used the names of the largest financial services and banking organizations to attack mobile platform users. Researchers found 438,709 unique users attacked by mobile Trojan bankers. For comparison, in the first half of 2018, the number of attacked users was 569,057, a decrease of 23%.
Similar cases can be seen in the table representing the total number of attacks over this period.
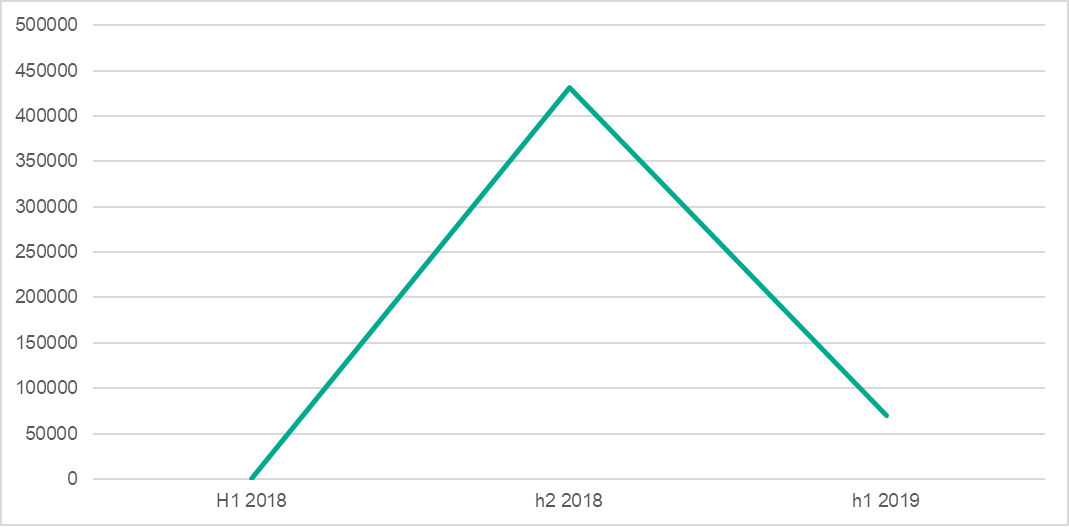
The number of attacked users and detected attacks peaked rapidly in the second half of 2018. 1,333,410 users were attacked and and there were 10,256,935 attacks. The reason behind this is the rapid growth in activity of the Asacub banker trojan and an increase in the distribution of the Svpeng banker trojan. As it can be seen from Kaspersky’s records during this period, the number of Asacub attacks peaked in in the second half of 2018, multiplying almost a thousand times, comparing to figures of H1 2018. However, the epidemics then calmed in H1 2019.
| H1 2018 | h2 2018 | h1 2019 | |
| Trojan-Banker.AndroidOS.Asacub.a | 476 | 431036 | 69704 |
| Trojan-Banker.AndroidOS.Asacub.snt | 182 | 341726 | 92483 |
| Trojan-Banker.AndroidOS.Asacub.ce | 0 | 196479 | 34211 |
| Trojan-Banker.AndroidOS.Asacub.ci | 0 | 194564 | 3101 |
| Trojan-Banker.AndroidOS.Asacub.cg | 0 | 152011 | 2893 |
| Trojan-Banker.AndroidOS.Svpeng.q | 84268 | 126316 | 35400 |
The influence of Asacub on the overall statistics can be clearly seen in the graph below.
The overall number of detected malicious files (installation packages) has decreased since the first half of 2018: in the first half of 2019, there were 43% fewer. At the same time, researchers recorded an increase in the number of attacks, rising by 107%.
The top-five malware families for mobile platforms in the first half of 2019 is almost identical to the overall rating for 2018.
More than half (51),39% of users faced representatives of the Asacub malware, which recorded powerful growth last year. At the peak of its “popularity” this malicious software attacked up to 40,000 users per day. isThe was partly due to the Trojan distribution method; when it reached the victim’s phone, it sent messages to all its contacts with links to download the installation file.
The Asacub family is followed by the Agent family (16.75%). This is the general verdict for banking trojans that cannot be classified into particular families or are represented by only one sample.
14.91% were attacked by the Svpeng Trojan. Like most banking Trojans, Svpeng slips a false login page to the user, and then intercepts the data entered in the login and password fields.
| Family | %* |
| Trojan-Banker.AndroidOS.Asacub | 51.39 |
| Trojan-Banker.AndroidOS.Agent | 16.75 |
| Trojan-Banker.AndroidOS.Svpeng | 14.91 |
| Trojan-Banker.AndroidOS.Faketoken | 7.56 |
| Trojan-Banker.AndroidOS.Hqwar | 2.56 |
* The share of users attacked by a certain family of malicious programs from all users attacked by financial threats
TOP 5 financial malware families, H1 2019
The Anubis Trojan is particularly interesting: it intercepts data for access to services of large financial organizations and two-factor authentication data (scode from SMS), which encrypts the data in order to extort money. It is one of the few banking Trojans that spreads via instant e messaging apps, such as WhatsApp, and sends a link to the victim’s contact list. Anubis is known to be one of the first threats in which comments on the YouTube platform were used as a command centre – a platform from which attackers manage malware. This usually works in the following way: malware writers create a video on Youtube and write a description or comment containing a command. Malware then connects to this video page, reads the description or comment and executes the command.
This happened in this way because Youtube is a public resource, so when one analyzes an infected user’s traffic, and sees a YouTube link in the list of accessed pages, even a cybersecurity expert may not consider it suspicious. They could even be unaware that those requests were not sent by the user but instead by malware. Moreover, such communication can not be blocked as there the user could be blocked from accessing the entire YouTube website.
Conclusion and recommendations
In the first half of 2019, researchers recorded an increase in the number of users attacked by financial malware for personal computers compared to the same period in 2018, and a decrease in the activity of cybercriminals targeting mobile platforms.
The main families of malware that attacked users in 2019 remained the same: for mobile platforms, the leaders turned out to be the Asacub family, and for PC RTM (for corporate users) and Zbot (for private users) trojans were the most prolific.
It was not possible to single out specific geographic locations where financial threats are most active, since they turned out to be approximately equal for users in all regions.
To protect against financial threats, Kaspersky recommends that users:
- Install applications only from trusted sources – such as official stores;
- Check what access rights and permissions the application requests – if they do not correspond to what the program is designed to do then it should be questioned;
- Do not follow links in spam messages and do not open documents attached to them;
- Use a reliable security solution, including on mobile devices.
To protect your business from financial malware, Kaspersky security specialists advise:
- Introducing cybersecurity awareness training for your employees, particularly those who are responsible for accounting, to teach them how to distinguish phishing attacks: do not open attachments or click on links from unknown or suspicious addresses
- Installing the latest updates and patches for all of the software you use
- Forbidding the installation of programs from unknown sources
- For endpoint level detection, investigation and timely remediation of incidents, implement an EDR solution such as Kaspersky Endpoint Detection and Response. It can even catch unknown banking malware
- Integrating Threat Intelligence into your SIEM and security controls in order to access the most relevant and up-to-date threat data





























Financial threats in H1 2019