
About two weeks ago, the German Chaos Computer Club (CCC) has published an analysis report of a backdoor trojan that they claim had been used by German police during investigations in order to capture VoIP and IM communication on a suspect’s PC. Our friends over at F-Secure published a blog post last week where they wrote about another file that, according to them, seemed to be the dropper component of the trojan. They were kind enough to share the MD5 hash of the file, so we could pull it from our collection. Stefan and I took a closer look.
The dropper carries five other binaries in its resource table, so there are six components in total – each with a different purpose – all of which have been analyzed by us. Amongst the new things we found in there are two rather interesting ones: firstly, this version is not only capable of running on 32 bit systems; it also includes support for 64 bit versions of Windows. Secondly, the list of target processes to monitor is longer than the one mentioned in the CCC report. The number of applications infected by the various components is 15 in total.
Target Applications
Previous discussions of R2D2 mention Skype as a target application that is monitored by the trojan. The version analyzed by us indicates that Skype is targeted as well, but also all common web browsers, various instant messaging applications and voice-over-ip software, such as ICQ, MSN Messenger, Low-Rate Voip, paltalk, SimpPro, sipgate X-Lite, VoipBuster and Yahoo! Messenger. The list of process names is:
- explorer.exe
- firefox.exe
- icqlite.exe
- lowratevoip.exe
- msnmsgr.exe
- opera.exe
- paltalk.exe
- simplite-icq-aim.exe
- simppro.exe
- sipgatexlite.exe
- skype.exe
- skypepm.exe
- voipbuster.exe
- x-lite.exe
- yahoomessenger.exe
Code injection into target processes is carried out by the dropper, two user-mode components and also a 32 bit kernel driver with extended functionality compared to the version previously analyzed, which only provided an interface for registry and file system modifications. This new driver starts an additional thread that constantly loops over the current list of running processes and injects a DLL into each whose image name matches an entry from the following list:
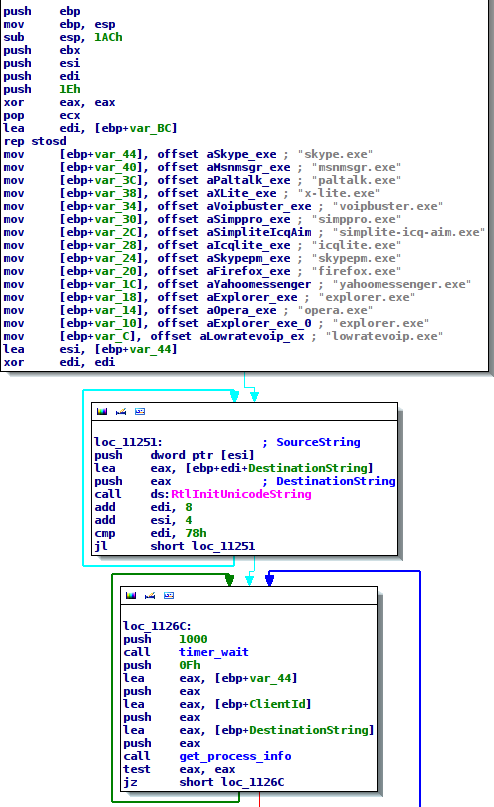
Figure 1: List of target process names in the 32 bit kernel driver
All target processes we found in the different user-mode components are also covered by the driver.
There are two different DLL injection methods implemented. One works by registering the user-mode library in the Windows registry as an AppInit DLL so that it gets loaded during process creation. The second creates a remote thread in already running processes and injects a piece of position-independent code that maps the mfc42ul.dll file, one of the user-mode modules, into the target process memory. The following screen shot depicts the first couple of instructions of the injection code:
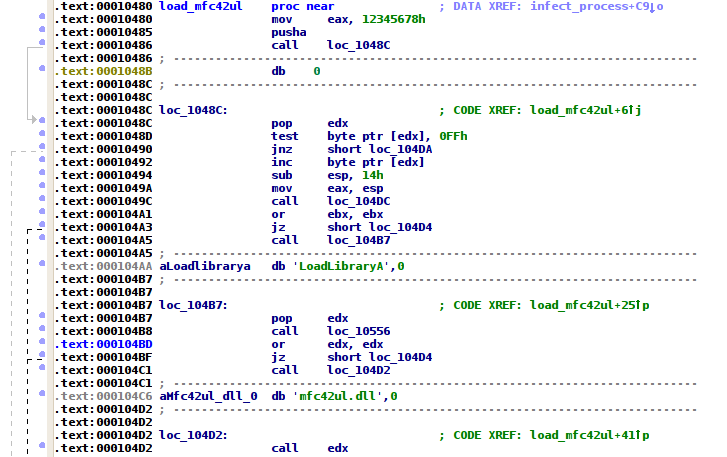
Figure 2: Position-independent code to load a DLL into a target process
64 bit Kernel Driver
When the dropper installs the kernel-mode component, it derives the resource name from the architecture (either 32 or 64 bit) and installs an appropriate driver:
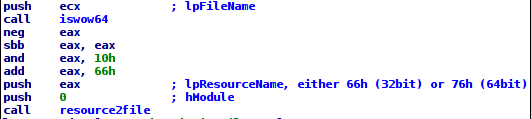
Figure 3: Code to determine and load the appropriate kernel driver for the architecture
Contrary to the 32 bit version, the 64 bit driver does not contain any process infection functionality but only provides a rudimentary privilege escalation interface through file system and registry access. Similar to its brother, it creates a device and implements a basic protocol for communicating with user-mode applications.
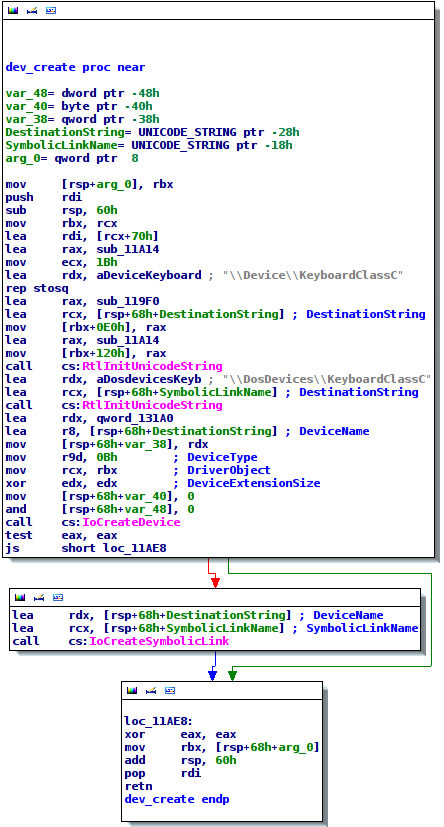
Figure 4: Device creation routine in the 64 bit driver
It is well known that 64 bit kernel modules must carry a valid digital signature that can be checked by the operating system, or loading the driver fails. The driver that comes with the rootkit comes with a 1024 bit RSA certificate (fingerprint e5445e4a 9c7d24c8 43f0c669 e2a8d3a1 78cf7fa8), issued by Goose Cert on April 11, 2010. However, the certificate must be installed and the trustworthiness must be confirmed in order to make the driver load.
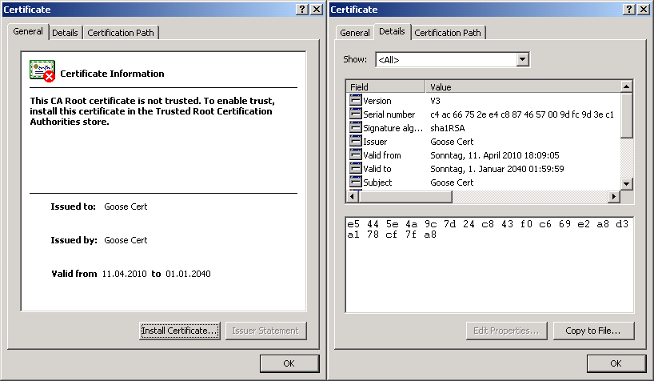
Figure 5: Certificate from the 64 bit driver
All components are detected by Kaspersky as variants of the R2D2 trojan/rootkit. The dropper was previously heuristically detected and blocked by us as an invasive program.






















Federal Trojan’s got a “Big Brother”